- What is Encryption?
- What is Decryption?
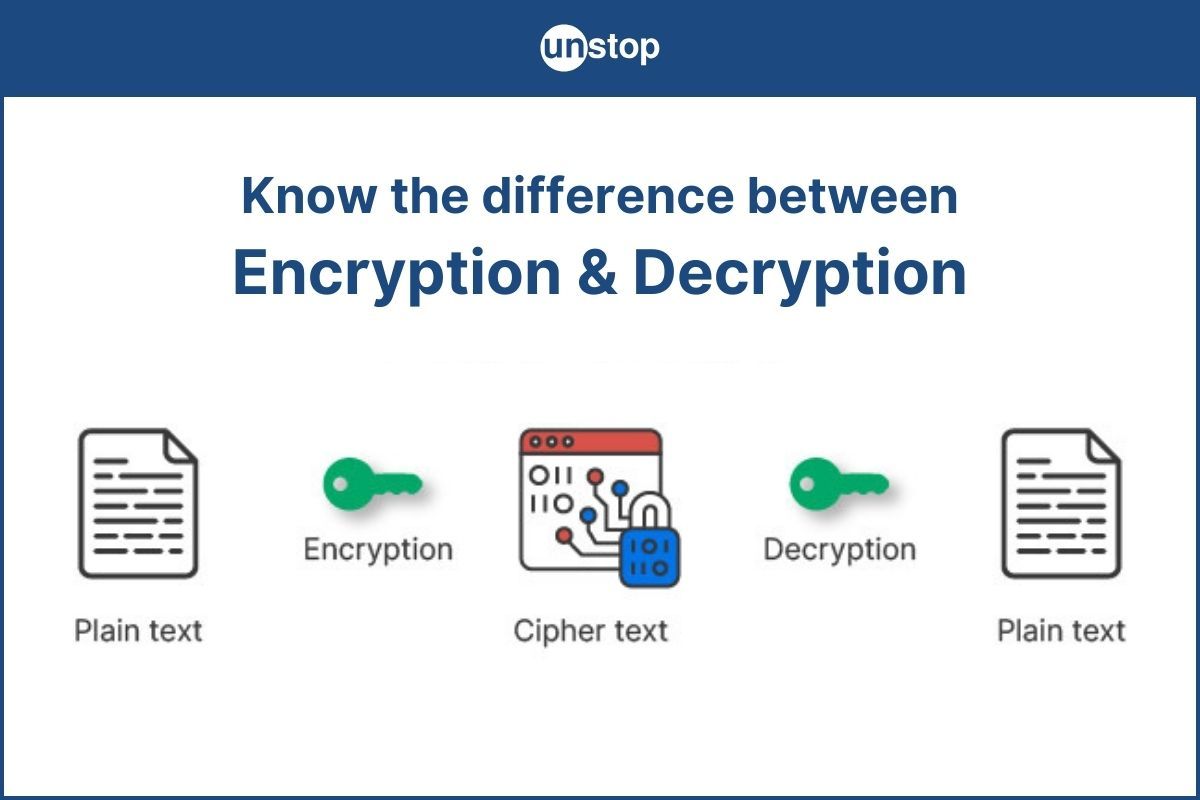
- Differences between Encryption and Decryption
- How do Encryption and Decryption work?
- Why use Encryption and Decryption?
- Encryption and Decryption Tools
- Benefits of Encryption and Decryption
- Real-life Examples of Encryption and Decryption
- Frequently Asked Questions
Encryption And Decryption 101: Know How Your Data Is Protected On Internet
Have you ever wondered how messages zip across the internet without anyone eavesdropping? The answer lies in the fascinating world of encryption and decryption! These two processes act like a digital lock and key, scrambling information to keep it confidential and then transforming it back into its original form for authorized users.
In this article, we'll delve into the intricacies of encryption and decryption, exploring how they work, the tools that make it happen, and the real-world applications that keep our digital lives secure. So, buckle up and get ready to unlock the mysteries of cryptography!
What is Encryption?
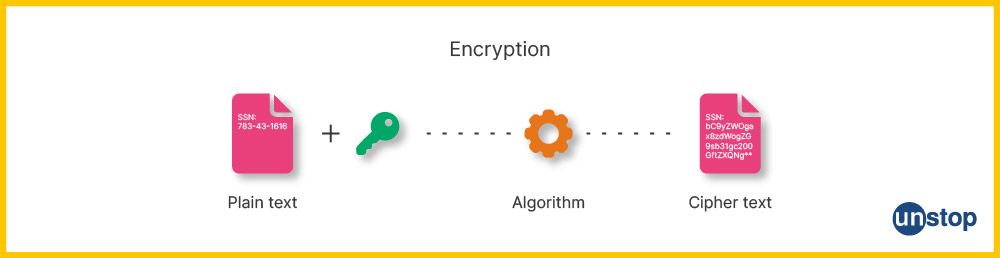
Encryption is the process of encoding a message or file to make it unreadable by anyone except an authorized recipient. The original form of the data, known as plain text, can be encrypted using various encryption algorithms and techniques.
It works by transforming plaintext letters into cipher texts (encrypted letters) through mathematical functions that use complex numbers and keys to scramble them up to an unrecognizable form, altered from their original format.
This prevents unauthorized access to sensitive information stored on digital media such as computers, laptops, smartphones, etc. This protects the integrity of the sensitive information from malicious actors aiming to modify or extract valuable data without permission. Encryption also provides authenticity for sent messages with digital signatures, allowing recipients who have received encrypted documents to know if they come from a trusted source.
What is Decryption?
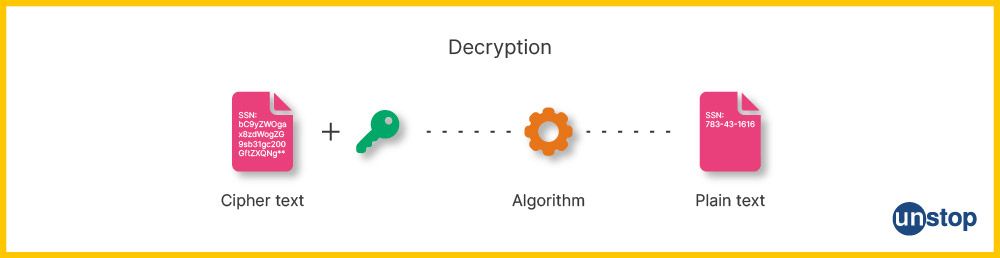
Decryption is the opposite process of encryption. It is taking encrypted data, such as text or an image, and restoring it to its original state so anyone can read it without requiring a password or other authorization. This process involves using decryption algorithms to break down the encrypted code into plain text to make sense of what was once scrambled information.
Decrypting secured files has become increasingly important for businesses that must protect confidential data from unauthorized access. Such encryption schemes are designed with highly advanced techniques requiring powerful computing resources and specialized software programs for successful decryptions. The effective security methods associated with these protections determine the type and strength of the decryption algorithm used. Thus, if someone attempts to gain access without proper authentication procedures, they will likely fail due to relying on ineffective methods.
Differences between Encryption and Decryption
Here are the major differences between encryption and decryption:
|
Aspect |
Encryption |
Decryption |
|
Purpose |
Converts data into an unreadable form to protect it from unauthorized access. |
Converts encrypted data back into its original, readable form. |
|
Method |
Uses an encryption method (e.g., AES, RSA) to transform plaintext into ciphertext. |
Reverses the process using decryption methods that are compatible with the encryption technique. |
|
Output |
Produces ciphertext, which is gibberish and unintelligible without the decryption key. |
Yields the original plaintext when provided with the correct decryption key. |
|
Security |
Enhances data security by making it difficult for unauthorized parties to understand the content. |
Restores data to its original form for authorized users or systems. |
|
Applications |
Applications of encryption: Widely used in data transmission, storage, and communication to protect sensitive information, such as financial data, personal records, and passwords. |
Decryption is necessary for authorized parties to be able to access encrypted data and for secure communication between parties. |
|
Key Management |
Requires secure management of correct encryption keys, which should be kept secret to maintain extra security. |
Also necessitates secure key management, with decryption keys being securely stored and controlled. |
|
Use cases |
It is commonly used in online banking, e-commerce, email services, and VPNs, among others. |
Utilized in scenarios like accessing secure documents, opening encrypted messages, and authenticating users. |
|
Reversibility |
Generally irreversible - without the appropriate decryption key, ciphertext is hard to revert to plaintext without it. |
Reversible - Applying the appropriate decryption key converts ciphertext back to plaintext. |
|
Algorithms |
Utilizes various encryption algorithms like AES, DES, RSA, and others. |
Requires corresponding decryption algorithms that match the encryption method used. |
How do Encryption and Decryption work?
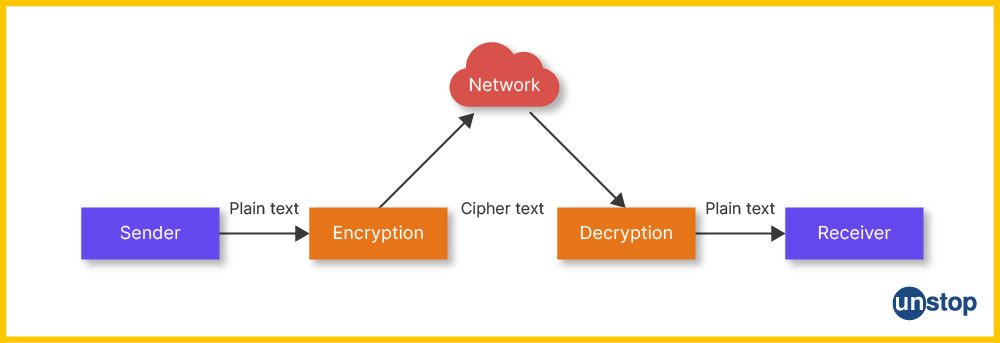
Encryption and decryption help encrypt data so that only authorized parties can read it. Thus, secret information is protected.
Encryption is a technique that uses an algorithm, or block cipher, to scramble plaintext into unintelligible text (ciphertext). Decryption is used to reverse the ciphertext to its original form.
Decrypting the ciphertext involves using a key usually shared between sender and receiver before encryption instructing how to unscramble the scrambled message back into its original readable format.
How to encrypt data?
When encrypting data, users must decide on several components:
- What kind of encryption algorithm will they use?
- Whether they want symmetric-key or asymmetric-key algorithms?
- If any additional authentication methods are required before access is granted.
For instance, with symmetric-key cryptography like AES or DES (Data Encryption Standard), one secret key is used both for scrambling and unscrambling messages
In asymmetrical systems, two keys are used - public ones for broadcasting messages outwards securely from one source, and private ones that remain within your possession are required for secure communication between multiple devices or networks. For example, fraudulent websites hosting financial services requiring extra layers of verification protection.
Once the encryption method is agreed upon, data can be encrypted by encrypting files in bulk (whole-disk encryption) or message-specific contents such as emails and chats that require end-to-end protection across devices.
During this process, the plaintext input of characters is run through an algorithm with the key which may include salt, nonce and other extra components that create ciphertext output strings. These strings are impossible to decrypt without possessing their corresponding symmetric/asymmetric key pair(s).
For example, when sending sensitive information via email, you would use the TLS (Transport Layer Security) protocol, which allows communications over networks like Facebook Messenger, etc., to become secure against third parties from accessing messages between sender and receiver.
Each time someone logs into their account, these services automatically generate new temporary access tokens for each session, making sure all communication remains confidential if intercepted during transit.
How to decrypt data?
When appropriate credentials are presented, it begins by reversing cryptographic operations to retrieve the original elements stored before encryption (e.g., the key or access token). Depending on your chosen system, decryption may involve multiple steps -such as authenticating user credentials with 2FA– to provide secure access and unscramble ciphertext back into its original format before it can be read by the intended recipient(s).
When decrypting data, users must use the same algorithm used for encrypting it along with a valid symmetric/asymmetric key pair corresponding to one used during encryption so they can decode the scrambled message back into readable form. If the correct algorithm and key are used, users can decrypt ciphertext into plaintext so they can read or access whatever information was securely transmitted.
Types of Keys
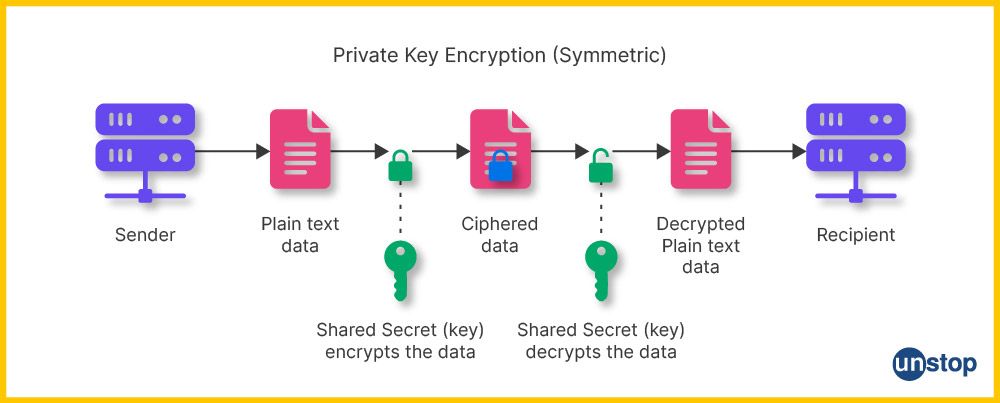
1. Symmetric Keys: This type of key uses the same encryption and decryption keys, meaning that any information encrypted with one key can only be decrypted with the same key. These are often shared secret algorithms because both parties must know the same key to work correctly.
Examples include Data Encryption Standard (DES) and Advanced Encryption Standard (AES).
2. Asymmetric Keys: This type of cryptography is based on public-key or two-key cryptosystems and requires two connected but distinct cryptographic keys – a public and private pair instead of just one symmetrical single ‘shared’ secret key like symmetric cryptography does. These also correspondingly generate digital signatures used in authentication processes such as banking over networks or electronic document signing systems.
Examples include the RSA algorithm and elliptic Curve Cryptography(ECC).
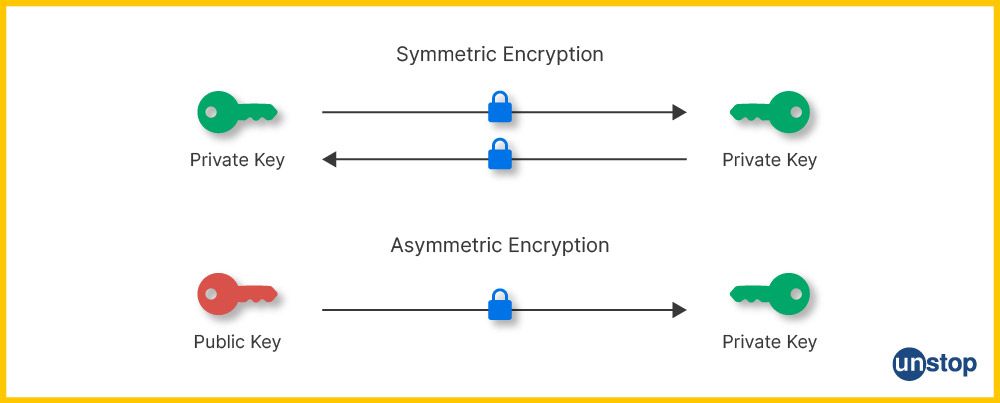
3. Public Key: It refers to a type of asymmetrically encrypted security technology where two different related yet mathematically disparate elements are combined into an incredibly secure form by using clever mathematics. A system protected this way proves to be quite a difficult beast for hackers who try merely to guess your credentials without knowing all the parts that are necessary to attempt to access the system.
The most common use case for public keys is in asymmetric encryption systems, where the public-key cryptography is used to encrypt data, and the private one is used to decrypt.
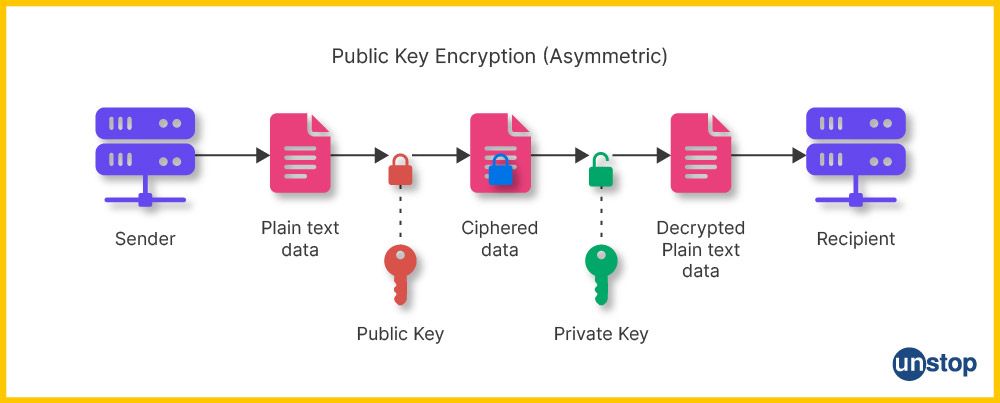
4. Private Key: A private key is an encryption key used in cryptography and contains a secret password for decrypting information encrypted with public key cryptosystems. The user typically generates private keys and then shares them via secure channels, only with those who need to know them. The data encryption can be done using the private key, and data decryption can be done using only its corresponding public key; this ensures that no one else can decrypt or read your sensitive information without having access to your specific private key.
The most common use case for private keys is in digital signatures designed specifically so that someone can prove they own something (such as documents) without having direct control over them but also work when it comes to authentication and decryption tasks such as email encryption, email conversation or securing online banking sessions.
Why use Encryption and Decryption?
The ability to securely communicate, store, and transmit data makes encryption and decryption crucial. Encrypted data can be accessed by authorized users with the correct key encryptions or accurate passwords. This ensures that only those supposed to access sensitive information can see it, protecting companies from malicious attacks, by confusing hackers who may try to steal confidential data.
- Encryption and decryption are important to protect data sent or received over a network so it remains private between the sender and receiver.
- It helps prevent unauthorized access to confidential information such as credit card numbers, social security numbers, critical passwords, etc., by providing strong encryption techniques that make the data unreadable unless it’s decrypted using the correct key encryptions or code.
- Encryption protects against viruses and malicious software from stealing personal information, possibly leading to identity theft or financial losses if left unchecked.
- Additionally, encryption ensures that even if an intruder gains access to your computer systems, they cannot read any of your sensitive documents without having the correct password for decrypting them, which would take too long for them, thus making hacking difficult.
- Encryption also provides authentication methods like digital signatures, which allow only authorized people to view certain files. Unauthorized users are blocked out completely due to additional privacy protection provided on web applications or online transactions. This builds trust with the stakeholders.
- Decryption can also prevent data tampering and corruption during transmission over networks or the Internet by verifying the integrity of files being sent from one place to another with added features such as error checking for assurance that no changes have been made in transit.
- Lastly, encryption is necessary for any communication system, like satellite television, wireless communications, etc., which transmits signals through airwaves. These need the protection of their signal messages from interception so they remain secure between the two parties involved.
Encryption and Decryption Tools
Here are some tools used to encrypt and decrypt information:
- The encryption process involves encoding data with a secure algorithm so that only those with the correct key can read it. Encryption tools are available in software and hardware form, relying on algorithms such as AES, RSA, Blowfish, DES and Triple DES to protect sensitive information from unauthorized viewers.
- The other features offered by many encryption tools include password protection and digital signatures to provide an extra level of security required when dealing with important documents.
- Decryption is the reverse process of encryption unscrambling data into its original form with a Bit-key Security or passphrase to (obscure form) view content like reading your bank account PIN on your phone after unlocking it.
- Decryption tools are necessary to unscramble data from its encrypted form and restore it to a readable state. By employing private-key cryptography, only parties with access to the same key can successfully decrypt information; without this shared secret, any decryption attempts will give meaningless characters known as ciphertext.
- Similar to encryption, multiple types of decryption tools are available depending on what type of authentication scheme you decide, whether symmetric or asymmetric, where shared secrets between trusted entities protect the transmission stream from prying eyes or manipulation attempts.
Benefits of Encryption and Decryption
- Security: The main purpose of encryption and decryption is to secure data as it travels across networks or gets stored in databases, ensuring only authorized persons can access information. By using a key to encrypt sensitive information, the original plaintext (or raw) form of the message changes into ciphertext, which can only be understood by someone with knowledge of that specific encryption key used for the conversion process.
- Privacy: Encryption helps to protect user’s privacy when sending messages over public networks such as the Internet and Wi-Fi hotspots, etc. This way, even if someone manages to intercept the transmission, they will not understand what was sent unless they have access to decrypting software/key used while encrypting transmission in the first place.
- Authentication: Decrypting encrypted communications also has the added benefit of authentication since only people who hold the correct keys associated with those messages should ever be able to decrypt them correctly.
- Integrity Protection: Cryptographic algorithms may include some integrity protection mechanisms within their specifications, so once any tampering occurs during the communication process, its effects are immediately visible after applying cryptographic checksums. This means that data transferred between two points is not corrupted in any way.
- Non-repudiation: With encryption and decryption, digital signatures are used to guarantee the authenticity (or non-repudiation) of a message by verifying the identity of the sender/creator. This also prevents forgeries or impersonations as it requires a private key holder’s approval before they can encrypt their sensitive data.
- Increased Reliability & Integrity Of Corporate Communications: Encrypted communication provides companies with more reliable methods of transferring valuable internal information without worrying about interception or tampering. This helps to ensure that the integrity of the data is maintained even during transit.
Real-life Examples of Encryption and Decryption
1. Online Shopping Platforms: When you shop online, your debit or credit card details will likely need to be inputted into an e-commerce platform for payment processing purposes. Again, encryption technology comes into play here, with servers scrambling the numbers associated with this type of transaction via specially designed algorithms. Encryption turns this sensitive information into a meaningless message for any unauthorized user. Thus, it provides customers greater peace of mind when shopping off virtual shelves without worrying about potential security breaches, especially while dealing with large sums of money or confidential personal details such as addresses, etc.
2. Secure Email Communication: Email communication is another form of data that uses encryption to help secure communications between two parties by scrambling messages sent via email, such as emails containing financial or health-related information, which are both extremely sensitive pieces of personal details requiring encryption protocols when transmitted electronically outside or within a corporate network environment. Emails are encoded on one end before reaching out into networks. Thus, they need decoding at their delivery point for effective user engagement tasks.
3. Online Banking Transactions: Banks use strong forms of encryption technology whenever customers log in for online banking sessions – this helps ensure customer security while transacting business over the Internet for transfer of funds, etc., and protects against cyber criminals who try gaining unauthorized access to confidential accounts held by individuals or businesses alike; retrieval requires authentication through passwords/codes making it hard for intruders to get their hands on customer data.
4. Private Messages: Instant messaging applications use encryption to protect the content being exchanged between two or more users, as these platforms are often used to communicate private and sensitive information that needs to be secure from third-party access. End-to-end encryption is a prime example that scrambles messages, so even if someone intercepts them, they won't be able to understand what's inside - to them, it's a meaningless message. This is because it requires authentication from both sender and receiver before any deciphering can happen to convert the message into a readable format at either end of this digital conversation.
Conclusion: Encryption and Decryption - Guardians of Our Digital Age
Encryption and decryption have become the cornerstones of our digital world, safeguarding our information and ensuring secure communication. From the messages we send to the financial transactions we conduct online, these processes operate seamlessly behind the scenes, protecting our privacy and fostering trust in the digital landscape.
As technology continues to evolve, so will the encryption and decryption methods. So, the next time you send a message or make an online purchase, take a moment to appreciate the silent guardians – encryption and decryption – working tirelessly to keep your digital world safe.
Frequently Asked Questions
1. What is encryption and decryption in the context of cybersecurity?
The encryption-decryption process takes data, such as plain text or digital files, and uses algorithms to make it incomprehensible so that only authorized users can access the content. This helps protect data from unauthorized users while maintaining its integrity if it is intercepted in transit through secure networks.
2. How does encryption protect data from unauthorized users?
Encryption scrambles the ordinary message into an unreadable or meaningless message form (message into ciphertext). Both sides involved in communication require a key that unlocks this ciphertext back into understandable messages (plaintext) readable to intended recipients. Unauthorized users without this knowledge would be unable to unlock these messages due to their encryption protection capabilities, which prevents them from tampering with sensitive information during transfer between separate machines over shared networks like the internet.
3. What types of encryption are most commonly used today?
Commonly used types of encryption today include symmetric encryption algorithms, asymmetric encryption algorithms, and pre-shared keys. Additionally, there are other basic techniques such as single algorithm processes for safely transferring funds electronically between two parties via wireless networks without risk of interception by malicious third parties interested in profiting off stolen goods.
4. How do pre-shared keys work to secure transmissions of funds electronically?
Pre-shared keys work by having two parties set up a predetermined password before transmission, thus creating additional digital security measures. Should someone attempt intercepting online transmission content, they still wouldn't be able to decrypt any of the data as they would not be in possession of this key.
5. Is there an optimal approach for securing networks with wireless technology through complex encryption methods such as symmetric or asymmetric algorithms?
To secure networks with wireless technology through complex encryption methods, it is important to evaluate all possible encryption solutions and strategies for each scenario while taking into account multiple levels of security requirements. The level of security requirement will depend on the level of danger associated and a variety of types of threats posed against connected devices either directly or indirectly, such as malware virus infection spread from an external network source, potential eavesdropping activities by unauthorized parties, etc. Additionally, regular security audits are essential when maintaining network integrity stability to ensure compliance with current standards and regulations. This is necessary to protect sensitive information stored on-premises.
6. Which techniques should be applied when using basic encryption and decryption processes to maintain security over online communications?
When using basic forms of encryption and decryption processes, it's important to consider both sides involved in the conversation. This ensures that correct technologies are applied to safeguard confidential communications across ordinary text medium formats like email, chat messages, etc. Message authentication codes (MAC) can help increase confidence in transmitted messages that are readable and understood by the sender and recipient correctly, without manipulation.
7. How do homomorphic encryptions add value to how information is protected while still allowing it to remain accessible by authorized parties despite intermediate protocols?
Homomorphic encryption is a technique of cryptographic that allows users to maintain full access to encrypted data without deciphering it. This security approach works by allowing certain computations to be calculated within the encrypted state, thus making it completely readable during process operation. This means only people with powerful computing resources would try to break into otherwise secure communication channels.
8. What key algorithms should be employed to ensure the data is encrypted at a level that can withstand brute-force attacks?
To ensure the data is adequately protected against brute-force attacks, key algorithms should be employed depending on the desired level of complexity required. Some stronger options require additional time and effort to crack and process correctly, given the amount of information available from public sources. In addition, safety measures such as double-factor authentications could further improve the reliability of end-to-end encryption, providing both parties involved to receive and send messages safely and securely. This includes interactions involving financial transactions or online purchases of goods and services where sensitive details are exchanged regularly via formats like credit card banking applications, etc.
9. How do security experts assess the requirements for encryption and decryption when setting up secure networks while combating malicious activities on the internet?
Security experts assess requirements for encryption and decryption when setting up secure networks by first evaluating all potential threats posed against connected devices and various forms of digital platforms they utilize and establishing any patterns of malicious activity that arise. Thereafter, they accordingly suggest appropriate countermeasures to be implemented based on the findings. Their recommendations mitigate risk and minimize the impact caused by malicious attempts to access private, confidential user content, loss of monetary value, personal gain, connection events, and particular individual groups that may have been affected adversely or directly tied to related cybercrimes carried out recently in the past.
You may also like to read the following:
I’m a reader first and a writer second, constantly diving into the world of content. If I’m not writing or reading, I like watching movies and dreaming of a life by the beach.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter
Blogs you need to hog!

This Is My First Hackathon, How Should I Prepare? (Tips & Hackathon Questions Inside)

10 Best C++ IDEs That Developers Mention The Most!

Advantages and Disadvantages of Cloud Computing That You Should Know!









Comments
Add comment