- Most popular Linux applications
- Basic Linux Interview Questions
- Advanced Interview questions
- Preparing for Linux interview questions
50 Most-Asked Linux Interview Questions (Basic & Advanced)

Linux has been a part of many operating system distributions since the 1990s. Linus Torvalds originally authored it, and it was later adopted as a kernel for the GNU operating system. Today, Linus kernel is a free and open-source multi-tasking operating system kernel. It is provided under the GNU General Public License version 2.
Linux is used on a wide variety of computing systems, such as PCs, servers, mobile phones, supercomputers, etc. An important advantage of the Linux kernel is that it can be adapted for specific architectures as well as for several tasks using simple commands. Hence, there is no need to manually edit its source code before compilation.
Linux is an important topic for job interviews for system administrators, security engineers, kernel developers, etc. In this article, we will cover some important Linux interview questions that will help step up your interview prep. But before we get to the questions, let us go through some popular Linux applications.
Basic Linux Interview Questions
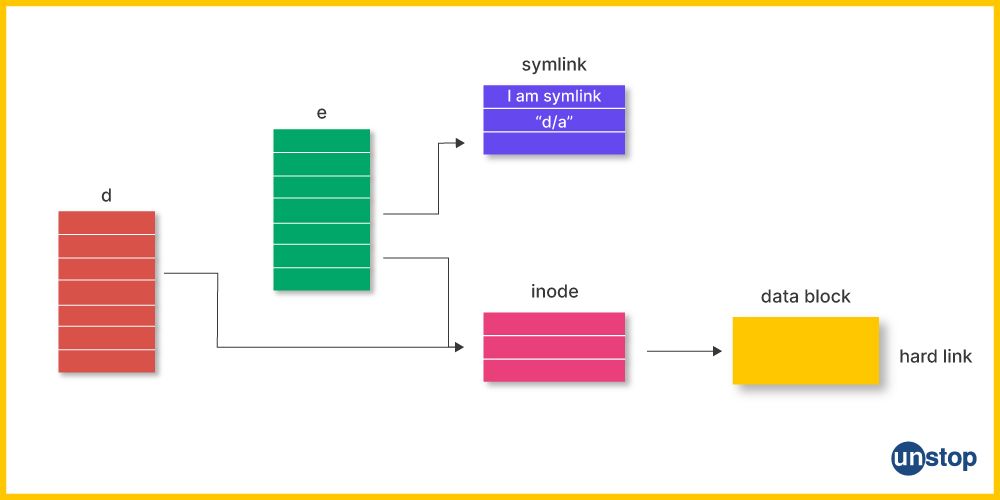
1. What is a symbolic link?
Symlink is another file that references another file or folder within a file system. There are many similarities between this and the Windows shortcut. Symbolic links come in handy in linking to various files or directories distributed across the file structure and on other drives. In addition, they provide a means of creating a backup for files or directories.
2. What are configuration files?
The configuration file contains the application's settings and parameters and those of the operating system. They define how the system or applications behave. The configuration files are typically kept in plain text format, which may be amended using any text editor.
3. What is a parent process?
A parent process is the process that produces the other one. The child process is started in the main control of the parent process. During the creation of the child process, it acquires the parent process's environment.
4. What is the Bourne Again Shell (BASH)?
BASH is an acronym for Bourne Again Shell, which refers to the fact that it is a modern version of the old Bourne shell. It is the default shell and scripting language under Linux and other Unix-based operating systems. For most Linux distributions, it is the default shell. BASH is a very versatile shell with many functionalities and abilities in working with command prompts.
5. What are application programs?
Application programs serve particular purposes or functions on a computer. These are used for word processing, spreadsheet calculations, and surfing. Operating systems are also layered with application programs installed on top of it.
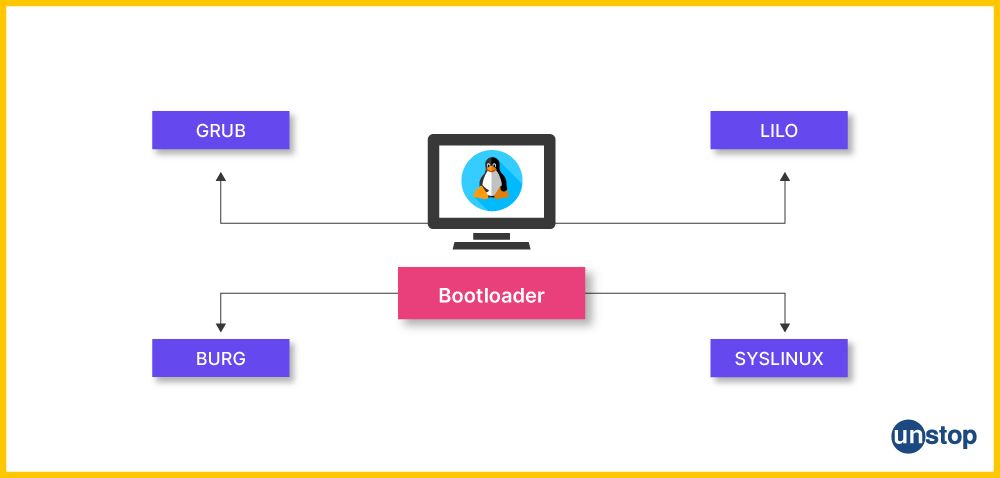
6. What are boot loaders?
The boot loader is a special program that loads an operating system to memory whenever the computer starts. They boot the hardware and load the OS kernel into memory. Examples of famous Linux boot loaders include GRUB and LILO.
7. What is the current directory?
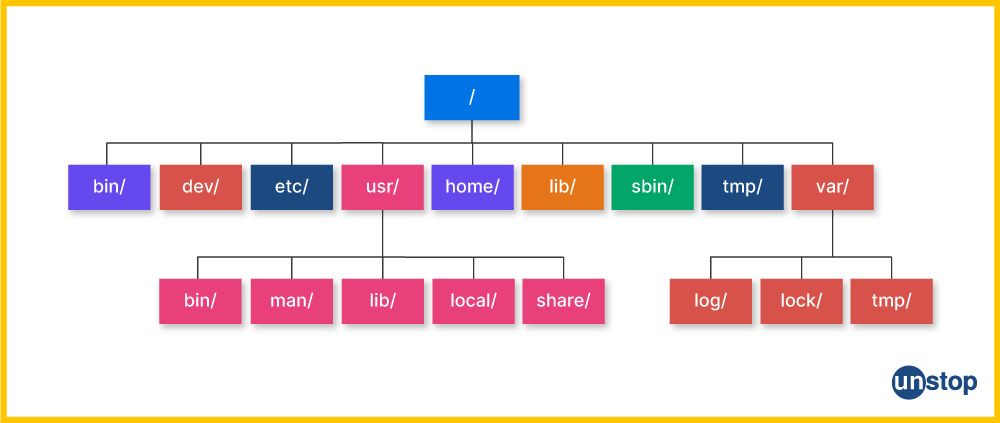
A current directory is a directory where a user is working now. The `pwd` command will display it. The `pwd` means “Print Working Directory,” which shows the present directory's whole path. One may use “pwd” command as an example, which, when used in a situation whereby the user is presently working in the home directory, will result in the output “/home/user”.
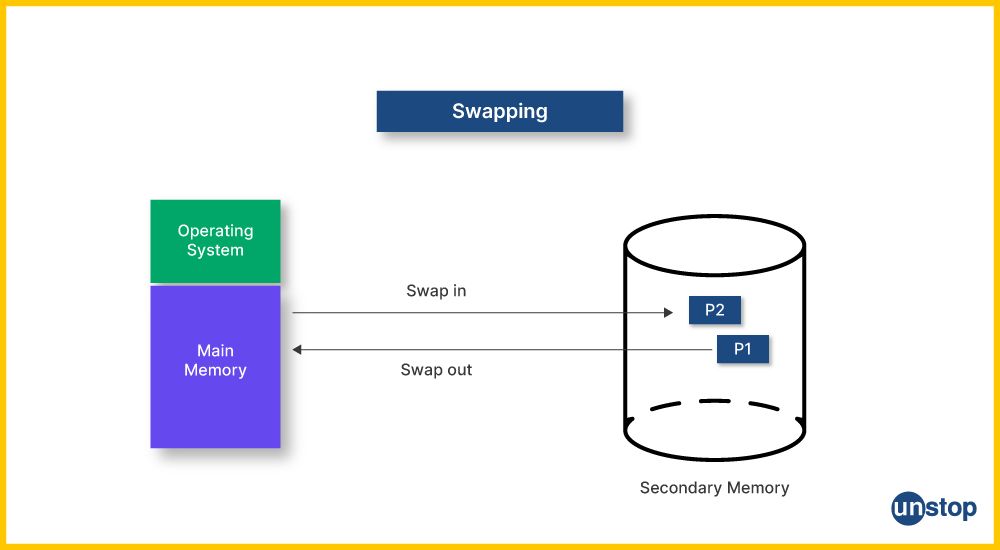
8. What is swap space?
One of the places where a hard disk is used temporarily for storing data that can’t fit into RAM is swap space. This type of memory is also referred to as the virtual memory. The operating system uses the least frequently accessed data in the RAM to create a swap space. A swap partition differs entirely in the hard drive or a swap file.
9. What is an original file?
The term “original file means a file that is untouched and has not been copied. It is the master of others, and other products are its copies. As an illustration, when one makes a document he calls example.txt, that is the original one. The original file can be copied but cannot be the same copy.
10. What is physical memory?
The physical memory is called RAM, and the CPU has direct access. This data stores information that the computer is processing at the moment. As programs are invoked, they are loaded into the real RAM, where the CPU can access them fast. Physical memory availability influences the performance of a computer.
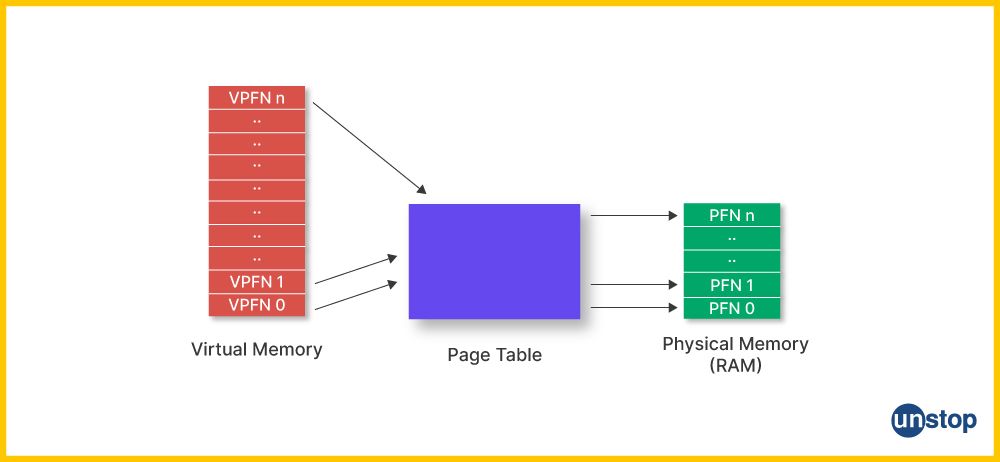
11. What are the different types of shells?
There are several types of shells, including:
- Bourne shell (sh)
- C shell (csh)
- Korn shell (ksh)
- Bourne-Again shell (bash)
- Z shell (zsh)
The first Unix shell is the Bourne shell (sh), which is still used. The csh (known as the C shell) was produced at Berkeley University and recognized for being similar to the C language.
A popular interactive command language for communication with the Unix system is Korn shell - ksh. Developed by David Korn of Bells Lab, it can be used as a programming language.
Bash is a free Unix shell software compatible with the Bourne shell and has incorporated aspects of the shell. Z shell (zsh) is a Unis shell with multiple upgrades over the traditional Bourne shell.
12. What is the process table?
A Unix system has a particular table called the “process table,” which stores information related to all the running processes at any moment. The OS keeps the information on the processes it handles at the moment in the RAM as a data structure known as a process table.
The information pertaining to this information covers general knowledge regarding each process, which includes process ID, owner, priority, environment variables for each process, parent process and the pointer to the machine code of an executive module. Also, in the process tab lies, among other things, information about the condition state of every process so that OS can manage process execution.
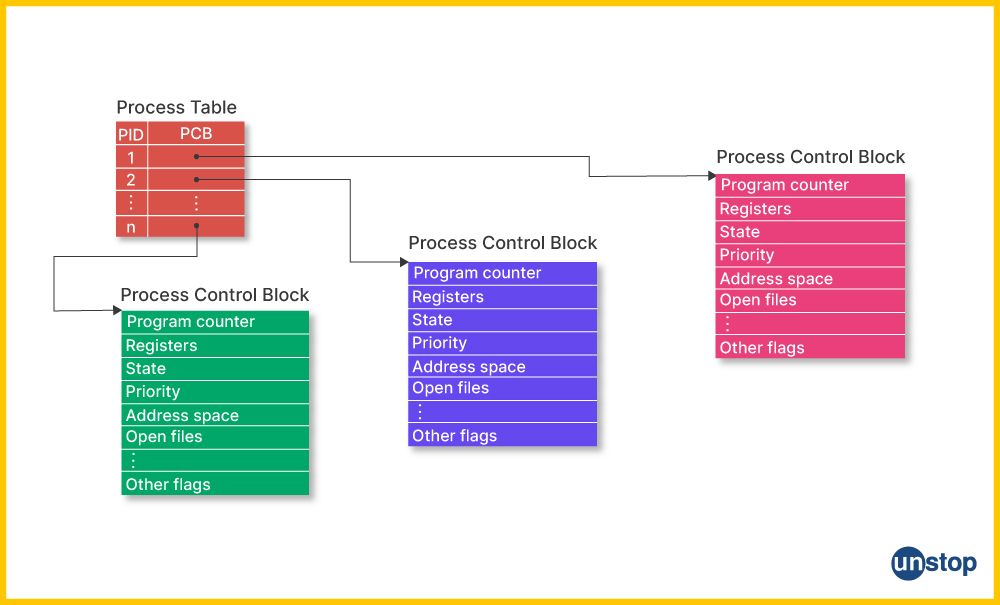
13. What is the current working directory?
The user’s current working directory is where he or she is currently active. One can view their pwd using this command. Pwd is an abbreviation that means print working directory, which shows a complete path of the current directory. For instance, if a user is active in the home directory, then the results of the pwd command would be /home/user.
14. From the File System types, explain the difference between ext3 and ext4 file systems in Linux.
|
Features |
Ext3 |
Ext4 |
|
Extent support |
No |
Yes |
|
Maximum file size |
2 TB |
16 TB |
|
Maximum file system size |
16 TB |
1 EB |
|
Journaling |
Yes |
Yes |
|
Multiple block allocation |
No |
Yes |
15. What is the default run level in a Linux system, and how does it impact the system's behavior during startup?
The default run level on a Linux system determines the run level at which the system registers itself at startup. The most common run level in most Linux distributions is run level 3, a multi-user mode with networking. The Run level determines which process starts at startup time.
Another example includes run level 0 (used to shut down the system) and run level 6 (used to reboot). Most Linux operating systems specify the default run level in the /etc/inittab file.
16. Differentiate between a hard link and a soft link. When would you prefer to use a soft link?
|
Features |
Hard Link |
Soft Link |
|
Inode number |
Hard-linked files take the same inode number. |
soft-linked file accepts a unique inode number. |
|
Directories |
Hard links to directories are not allowed. |
Soft links can be used to connect directories. |
|
File system |
It cannot be used on file systems. |
It can be used on file systems. |
|
Data |
Data in the original file will still be available in the hard links. |
only point to the file name; they do not retain data of the file. |
|
Original file’s deletion |
If the original file has been removed, the link will still work because it accesses the original data in the path. |
If you remove the original file, the link will not work because it does not retrieve the data from the original file. |
|
Speed |
Hard links are faster. |
Soft links are slower. |
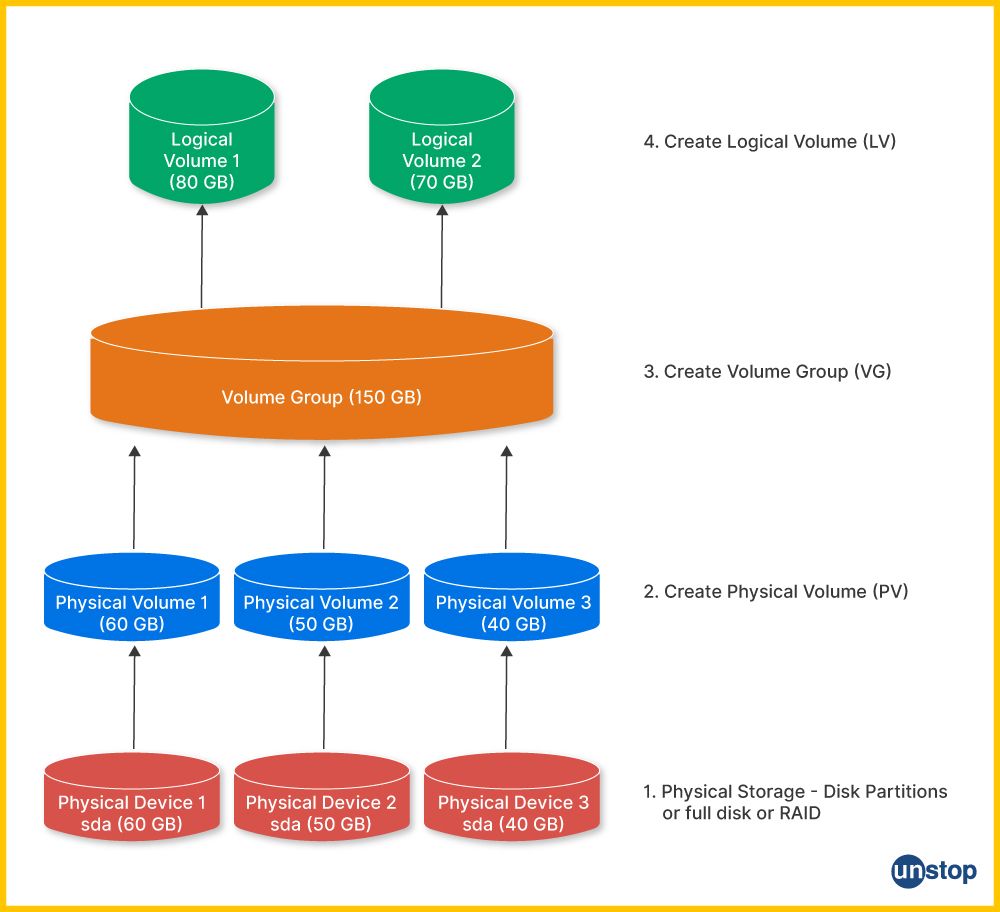
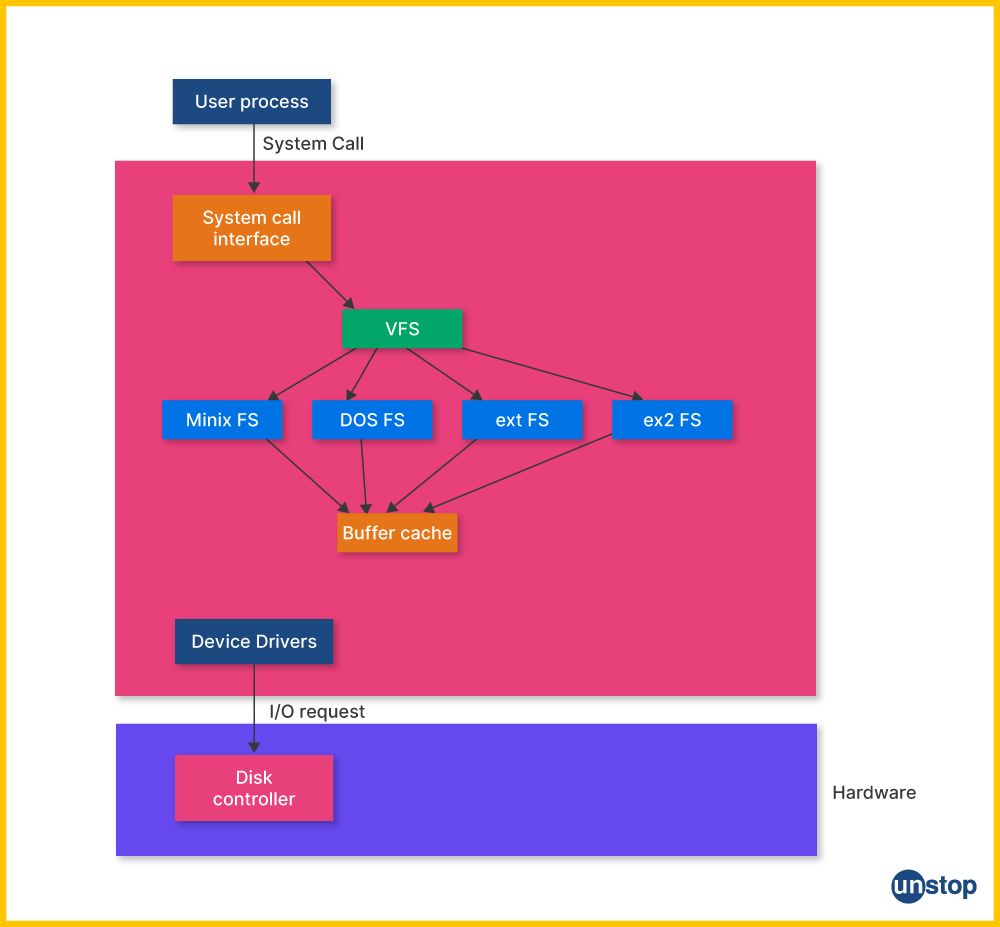
17. Explain what logical volume management (LVM) is in Linux and how it helps in managing disk space.
LVM is a storage management facility on Linux for hard drives and other storage media. LVM can handle virtual partitions that will propagate across physical disks. Logical Volumes refer to these virtual partitions. Using LVM has some advantages over traditional partitions. Such benefits include:
- Extending or pressing volume components online.
- Block-based image capture rather than files.
- Moving from one physical frame to another without any time.
18. How would you change the permissions of a file using the chmod command? Provide an example.
The command chmod is used to change the permissions of a file. Chmod, which stands for 'change mode,' means modifying the license of files and directories. The permissions are presented in the form of three digits, each representing the permission's owner, the group or others.
For example, to give the owner of a file read, write, and execute permissions and to give the group and everyone else read and execute permissions, the following command: "chmod 755 filename." This will create the permissions for the filename file as rwxr-xr-x.
19. Explain the purpose of the /etc/fstab file in Linux. How does it contribute to the system's boot process?
A configuration file called “/etc/fstab” in Linux lists available disk drives and partitions. It identifies the way disk parts are mounted into a file system tree. This file is read during boot-up so that the OS knows which file systems need mounting and the corresponding mount points. The /etc/fstab file contains information on the device to mount, mount point, file system type, and mount options. It is significant as it enhances the ease of auto-mount and starts the system with needed file systems.
20. Explain the purpose of the tail command in Linux and provide a practical scenario where you might use it.
Tail is one of the Linux commands meant to retrieve the last lines of a text document. Initially, it was designed to let users see the end or tail part of files, making it ideal for log files and live tracking.
The syntax of the tail command is: tail [options] filename
Practical Scenario:
For example, you monitor a system log file that is updated in real-time, like '/var/log/syslog'. The tail command lets one see new log entries added to the file consecutively.
For example: tail -f /var/log/syslog
The -f option lets you track the file in real-time, and you will see log entry new lines when they occur. This can be critical during troubleshooting, debugging, and monitoring of system activities.
21. Name two commonly used default ports in Linux networking and describe their respective purposes.
- SSH (Secure Shell) - Port 22: Secure shell (SSH) is a protocol to access the system remotely. The default port for SSH (port 22) enables a user to access a distant device safely and enter commands therein.
- HTTP (Hypertext Transfer Protocol) - Port 80: The basic building block for data communication on the World Wide Web is HTTP. The unencrypted web is transmitted over port 80, used when navigating websites with a browser.
22. What are kernel parameters in Linux, and how can you pass them during the boot process?
Boot time Linux kernel parameters are settings that dictate the behaviour of the kernels during the boot process. These include several items that can be employed to define memory allocation, system parameters, hardware settings and debugging. These are usually stipulated in the bootloader settings.
To pass kernel parameters during the boot process:
- GRUB: Open the GRUB configuration file located at '/etc/default/grub', and append the required values in the 'GRUB_CMDLINE_LINUX' field. Then, run 'update-grub' to put the change into practice.
- LILO: Open up the LILO configuration file, usually at "/etc/lilo.conf ", and then add the details in the 'append; line. Finally, after editing, run 'LILO' to update the bootloader.
23. Compare GRUB and LILO as Linux loaders. What is the role of a bootloader in the Linux startup sequence?
|
Features |
GRUB |
LILO |
|
Supported file systems |
Supports various file systems, including ext2, ext3, ext4, NTFS, and FAT. |
Supports a limited number of file systems, including ext2, ext3, and FAT. |
|
Configuration file |
Uses a configuration file called grub.cfg. |
Uses a configuration file called lilo.conf. |
|
Boot menu |
Supports a graphical boot menu with mouse support. |
Supports a text-based boot menu. |
|
Installation |
Can be installed on a partition or the MBR. |
Must be installed on the MBR. |
|
Flexibility |
More flexible and customizable. |
Less flexible and customizable. |
24. How can you securely connect to a remote server in Linux, and which protocols or tools would you use?
The SSH or Secure Shell is one option to log into remote servers under Linux safely. The most popular SSH connection tool is the ssh command (SSH stands for Secure Shell).
Here's a basic example:
ssh username@remote_server_ip
- Replace 'username' instead with your actual username.
- Replace 'remote_server_ip' with IP address or hostname of the remote server.
SSH encryption enables logging in, execution of commands, and transfer of files between the client and the server into an encrypted channel. SSH also makes other secure file transfer mechanisms like SCP (Secure Copy) and SFTP (secure file transfer protocol) possible.
25. Explain the significance of the key combination Ctrl + Alt + Del in Linux. How does it differ from its usage in other operating systems, and what does it trigger?
The key combination Ctrl + Alt + Del has a different meaning under the Linux operating system as compared to other OS like Windows.
Linux does not normally have Ctrl + Alt + Del to start a direct system reboot. It can call on Task Manager or a similar system monitor where one can see all running processes, system performance, etc., and possibly stop unresponsive programs.
Conversely, this deviates from its usual use on Windows, known as Ctrl + Alt + Del, which serves as an iconic shortcut that allows users to lock the computer, switch users, log out, or gain access to the Task Manager.
The functionality of Ctrl + Alt + Del is configurable based on the specific desktop environment or system setup in Linux. This makes it an adaptable shortcut, catering to unique end-user needs and configurations.
Advanced Interview questions
1. Explain the significance of the "tar" command in Linux. How does it contribute to managing disk space usage? Provide an example of archiving and extracting files using tar.
Significance of the "tar" Command:
Efficient file management can be achieved using Linux's "tar" command. In essence, it is a program that aims to produce zip archives, usually employed in the backup processes, transmission of several files, and software distribution. Tar command plays an important role in managing the disk space since it reduces the size of files stored together as archives.
Example of Archiving and Extracting Files
tar -czvf archive.tar.gz source_directory
tar -xzvf archive.tar.gz -C destination_directory
Explanation:
- -c: Create a new archive.
- -z: Compress the archive using gzip.
- -v: Verbosely list the files processed.
- -f: Specify the archive file name.
The "tar" utility shows this process by compressing source_directory into an archive and then uncompressing it directly in destination_directory, saving disk space.
2. Describe the different types of resource usage monitoring commands in Linux. How would you use tools like "top" and "htop" to analyze CPU usage, memory usage, and running processes?
Resource Usage Monitoring Commands
"Top" and "top" are commonly used monitoring commands in Linux that provide a simple overview of resource consumption.
Using "top" and "htop" for Resource Analysis:
Top:
- Type top on a shell prompt to launch "top."
- Real-time analysis of CPU, memory usage, and running processes.
- To sort by CPU, use Shift+P; to sort by memory, use Shift+M.
htop:
- Htp is needed only in case of absence.
- Write "htop" into an open command line or a terminal to launch "htop."
- Displays interactive, graphical mapping of the system resource usage.
- Enables user-friendly navigation and tailoring of the interface.
Both utilities offer information on each process, its memory footprint, and system-wide statistics. This helps identify resource-hungry processes that consume more resources, improving system performance.
System administrators need these commands to oversee and control system resources promptly.
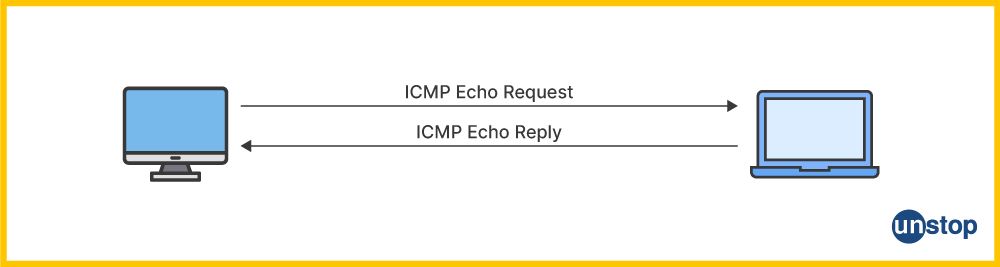
3. In Linux, discuss the role of the "ping" command in troubleshooting network interfaces and determining connectivity issues.
Role of the "ping" Command in Troubleshooting Network Interfaces:
An essential aid in troubleshooting network connections in Linux is the ping command. It mainly sends ICMP echo request messages into a target network node and waits for ICMP echo reply messages. The key aspects of its role in network troubleshooting are:
- Checking Connectivity: You can check whether a remote host is contactable on the network through a string of ping queries. The fact that the system works means that the network path is good.
- Latency Measurement: Ping gives the packet round-trip time traveling from the source to the destination and back. High latency could imply that the network is clogged or some other problems.
- Packet Loss Detection: Packets may be lost during the communication and can point, for example, to network problems." Persistent packet loss can affect the integrity of the connection between the two networks.
Example of Using "ping": ping example.com
It helps resolve connection problems by showing round-trip times and packets lost when ICMP Echo Requests are sent to "example.com."
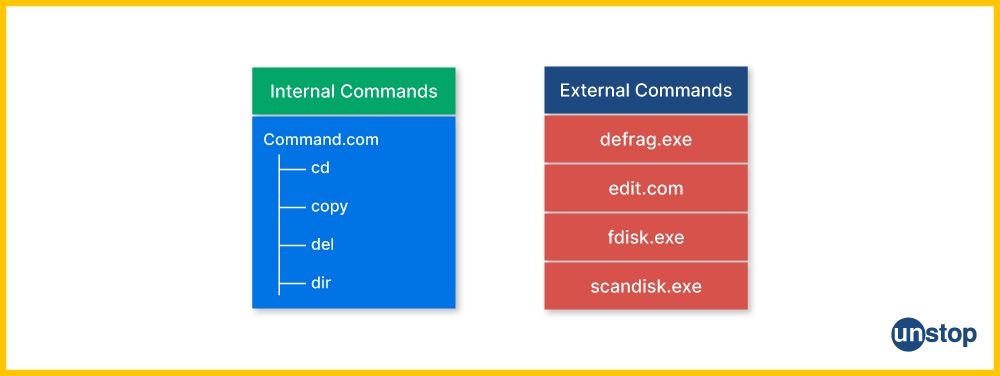
4. Differentiate between external commands and internal commands in the context of the Linux command-line interface. How can one create a custom command or script to automate a series of tasks?
In Linux, commands can be divided into external and internal, depending on where they run.
|
Feature |
External Commands |
Internal Commands |
|
Execution Location |
Stored in separate executable files |
Built into the shell |
|
Execution Method |
Executed using the command's path or full path |
Executed directly within the shell process |
|
Path Configuration
|
Requires the path to be included in the system's PATH variable |
No need for additional path configuration |
|
Shell Dependency
|
Not dependent on the shell |
Part of the shell's functionality |
|
Access and Permissions |
Executable files with associated permissions |
Integrated with the shell, inherits shell permissions |
|
Customization |
Customizable, additional commands can be added |
Limited to the built-in functionality of the shell |
|
Examples |
‘ls’, ‘ cp’, ‘grep’ |
‘cd’ , ‘ echo’, ‘pwd’ |
Creating a Custom Command or Script:
You can do a number of tasks automatically by creating a new command or a script which can be created in a standard text editor like nano or vim. Follow these steps:
- Write the Script: echo "Hello, this is a custom script!"
- Save the Script: Save the script with a ".sh" extension, e.g., "myscript.sh."
- Make it Executable: "chmod +x myscript.sh"
- Run the Script: "./myscript.sh"
A simple example of a script that echoes a message is shown below. You can extend the script to encompass any number of command sequences, creating a convenient method for automating jobs.
5. Explain the significance of user accounts in Linux and how they contribute to the security of the system. Discuss the role of environmental variables in user-specific configurations.
Significance of User Accounts and Environmental Variables:
User Accounts in Linux:
User accounts form a critical component of Linux system security and organizing systems. They have an individual account for each user and are recognized as their username. The significance of user accounts includes:
- Access Control: User accounts enable restrictions on accessing files, directories, and system resources. Individual users can be allowed to perform limited or restricted tasks through permission assignment.
- Isolation: User space ensures that each user works independently to avoid accidentally interfering with any system files and configurations. It provides system stability and security because, in this way, it further isolates the communication network.
- Account Management: Administrators can follow and control different user actions using user accounts. Additionally, it enables security policy implementation and audit.
Environmental Variables in User-Specific Configurations:
These are settings in the environment that affect the behaviors of processes and applications. In user-specific configurations, these variables are significant because:
- Customization: People can personalize their workspace through the setting of path, home, and PS1. Users may thus specify their preferred shell environment.
- Configuration Persistence: The environmental variables remain unchanged through sessions, thus allowing specific settings for every user in every session. It makes things simple for the user and facilitates application settings.
- Scripting and Automation: Scripting and Automation usually use environmental variables to exchange data and customize the activities performed by scripts to change the conditions under which they execute. It involves the automation of duties and other tasks as well.
6. Discuss the concept of background processes in Linux. How can a background process be initiated, monitored, and managed? Explain the relevance of the "cron" command in scheduling recurring tasks.
Background Processes in Linux:
Tasks after background processes do not depend on the foreground at the time. This is very important regarding multitasking and overall system performance. Key aspects include:
- Initiation: Appending an ampersand (&) initiates a process that will run as a background. For example: 'command &'.
- Monitoring: The 'jobs' command will allow you to list down background processes, and the 'bg' and 'fg' commands will make you move them from backward to forward.
- Management: Signals such as 'kill' to manage background processes to terminate it.
"cron" Command for Scheduling Recurring Tasks:
A task scheduler known as the cron command is used to run recurring jobs in Linux. This enables users to schedule scripting of commands or processes for running at particular periods. Key points include:
- Scheduling Format: The crontab, or "Cron table", schedules tasks according to a time-based format. The format includes minutes, hours, days, months, and dates.
- Editing Crontab: The users may change their crontab via the 'crontab -e' instruction. A scheduled task is represented in each line of the crontab file.
Examples:
Every day script to run at 3:30 AM: 30 3 * * * /path/to/script.sh.
To schedule a command every hour: 0 * * * * /path/to/command.
Cron command ensures that users can perform recurring activities and make regular backups or system maintenance as required.
7. How can you determine the disk usage of a directory in Linux? Provide a command and explain its output.
The command 'du' (disk usage) is used to determine a directory's disk usage. Here's an example:
du -h /path/to/directory
Explanation:
- du: Stands for disk usage.
- h: The human-readable format of sizes to avoid awkwardness (for instance, KB, MB, GB).
- /path/to/directory: Indicates the target directory on which you would like disk usage to be calculated.
This will give us the aggregate disk use of the designated folder and all its subfolders, shown understandably.
8. What is the default mode for creating files and directories in Linux? How can you modify the default permissions?
Default Mode for Creating Files and Directories in Linux:
By default, the 'unmask' (UMask) value specifies how Linux creates new files and directories. Umask stands for the permissions that must not be assigned in the case of the creation of new files or directories.
To check the current umask value, you can use the following command:
umask
You can also change the default mask to be used to create a new file or directory by setting a new umask value. For example:
umask022
Therefore, umask will be set as 022, making the permissions default for new files to 644 (rw-r--r--) and directories to 755 (rwxr-xr-x).
9. Explain the significance of a "target file" when using commands like 'ln' or 'cp' in Linux.
Significance of a "Target File" in Linux Commands:
In Linux, a command such as "ln" or "cp" considers the target file as its destination, pointing towards the source or directory.
- In the 'ln' command: ln source_file target_link
In this case, 'source_file' is the actual file, while 'target_link' will be created.
- In the 'cp' command: cp source_file target_directory
'Source_file' refers to the file to be copied, while 'target_directory' refers to the destination directory for these files.
It is important to understand the target file as it identifies the location of the creation of a symbolic link or any other operation.
10. What is the role of the directory separator in Linux file paths? Provide an example.
Role of the Directory Separator in Linux File Paths:
The forward-slash ("") in Linux file paths is a directory separator. It separates pathnames into parts or directories and file names, resulting in a hierarchical representation of directory pathnames.
Example: '/home/user/documents/example.txt'
In this example, '/home/user/documents/' denotes the directory path and 'example.txt' represents the document under this Directory. At this juncture, the forward slash assists in navigating and organizing the file system.
11. Name a basic Linux command that is frequently used for file and directory operations. Provide an example of its usage.
The 'cp' (copy) command is a popular and fundamental command applied to files and directories in Linux-related operations.
Example: cp file.txt /path/to/destination/
Copies "file.txt" to the destination directory. 'Cp' is comprehensive enough and may aid in copying files and folders while preserving their properties.
- 'mv' (Move): the command is used to relocte or change the name of a file or folder.
Example: mv oldname.txt newname.txt
It changes the name of "oldname.txt" into "newname.txt." - 'ls' (List): the command shows all the files and content of a directory
Example: ls
This command shows all the files and directories in your current working directory.
12. List three essential commands for working with directories in Linux. Provide a brief explanation of each.
Three Essential Commands for Working with Directories in Linux:
'cd' (Change Directory):
- Usage: 'cd /path/to/directory'
- Explanation: It simply changes the current working Directory to the specified path.
'ls' (List):
- Usage: 'ls -l /path/to/directory'
- Explanation: Shows what is in a directory. A detailed, long-form listing is provided through the use of the '-l'
'mkdir' (Make Directory):
- Usage: 'mkdir new_directory'
- Explanation: This creates a new directory named as specified.
These commands are indispensable in facilitating movement through the file system, viewing a subdirectory's contents, and making new subdirectories. These constitute the core of file and directory administration under the Linux operating system.
13. What is a "virtual file" in the context of Linux file systems? Provide an example.
A "virtual file" in the Linux filesystem denotes an interface that mimics interaction at the machine's level with the system's info and setup. These are procfs or sysfs files that belong to the virtual filesystem, not the real ones stored on disk.
Example: /proc/cpuinfo
This is a specific case where a virtual file '/proc/cpuinfo' gives more information about the type of CPU the computer uses and even the model it uses. Such a virtual file lets users and applications receive real-time information as regards the system CPU directly bypassing concrete files.
14. How do virtual desktops contribute to the user experience in Linux environments?
Workspaces or virtual desktops greatly impact the user experience of Linux-based environments. They provide the following benefits:
- Multitasking: This enables users to allocate different tasks or applications on distinct virtual desktops, facilitating the process of doing several things simultaneously.
- Workspace Customization: The wallpaper, icons, and open applications in each virtual desktop are customized to help users create unique environments depending on their work.
- Enhanced Productivity: Switching through several virtual desktops allows organizing various application projects, thus increasing productivity.
- Reduced Clutter: The use of virtual desktops enables a reduction in the amount of desktop mess as a result of organizing similar jobs or apps in distinct workspaces.
The virtual desktops are helpful for Linux users so that they can organize their space and improve efficiency concerning the organization of tasks.
15. Explain the role of process management in Linux. How can you view and control running processes?
Linux process manages the running of programs or applications. These are some of the roles it entails, like commencement-termination and prioritization. The key aspects include:
Viewing Processes:
'Ps' represents a command which enables us to look at a snapshot of running processes.
Example: ps aux
Controlling Processes:
'Kill' is a signal that users can use to tell the processes what they should do.
Example: kill -9 PID
Monitoring Processes:
'top' and 'htop' tools report on system processes in real-time, including metrics such as CPU usage and memory.
Background Processes:
After a command, the ampersand '&' signifies that processes can initiate and run concurrently in the background. For instance: command &. System administrators are responsible for process management to optimize resources for efficient system performance.
16. Who is Brian Fox, and what is his significance in the context of Linux?
Brian Fox developed the bash shell. He is the original writer of the Bash shell, contributing largely to its development. One of the common command-line shells in Unix is called Bash. Bash is an acronym for Bourne Again Shell and is common in Linux. Brian Fox's contributions in his bash work have changed the shell field in the context of UNIX-like system called Linux, offering users a dynamic shell for operating systems communication.
The work done by Brian Fox points to the nature of open source as a cooperative and community-based undertaking, where many people, including such persons, affect the means of existence necessary for running Linux, such as Bash.
17. Describe what is meant by "command mode" in Linux. Provide an example of a command that operates in this mode.
"Command mode" is the typical name for the function of a text editor in Linux. Vim remains one of the most prominent command-style user text editors at present. Navigating a document in command mode is more like giving commands than entering text directly. Switch to the insert mode by the key to enter the text.q
Example of a Command in Vim's Command Mode:
- Open a file in Vim: Vim filename
- In Vim, you start in command mode.
- To switch to insert mode and start typing text, Press 'i'.
- To save changes and exit, switch back to command mode by pressing 'Esc' and then type ': wq.'
This example is made of a command mode through which you can view documents, make edits, and perform many other operations.
18. Differentiate between physical files and virtual files in Linux. Provide examples of each.
|
Features |
Physical Files |
Virtual Files |
|
Definition |
Tangible data stored on persistent storage devices |
Entries in virtual filesystems representing information and configurations |
|
Location |
Stored on hard drives, SSDs, external storage media |
Part of virtual filesystems like ‘/proc’ or ‘/sys’ |
|
Nature |
Contains actual data that persists on disk |
Represents dynamic information, not stored on disk |
|
Modification by Users |
Users can create, modify, and delete physical files |
Users typically cannot modify virtual files directly |
|
Examples |
‘file.txt’ (text document), ‘image.jpg’ (image file) |
‘/proc/cpuinfo’ (provides CPU information), ‘/sys/class/net’ (network device information) |
|
Example Commands for Operations |
Creating a directory: ‘mkdir newdirectory’ |
Viewing network devices: ‘ls /sys/class/net’ |
|
|
Creating a file: ‘touch newfile.txt’ |
Reading CPU information: ‘cat /proc/cpuinfo’ |
19. How can you identify the resource usage of a running process in Linux? Name a command for this purpose.
Identifying Resource Usage of a Running Process in Linux:
You can use the 'top' command to identify the resource usage of a running process in Linux. What makes 'top' unique is that it gives users real-time snapshots of processes in a system and shows how much each process is consuming dynamically.
Usage:
- The cmd command invokes a display window that exhibits details related to CPU load, memory utilization, active processes, etc. The processes are then lined up in decreasing order depending on CPU utilization.
- You must use the key 'q' to quit the 'top' command.
- In this regard, 'htop' is an alternative command that can interactively monitor and manage system resources.
- The 'top' and 'htop' providing real-time information on each process's performance, the user can spot a particular process using lots of CPU or memory space.
20. Differentiate between 'rm' commands and explain the potential risks associated with them. How can accidental deletions be prevented?
Differentiating 'rm' Commands and Risks Associated:
Linx contains the 'rm' command for deleting files or folders. There are two main variants of the 'rm' command:
'rm' (Remove):
- Usage: Remove files.
- Example: rm filename.txt
- Remove the specified file using this command.
'rm -r' (Recursive Remove):
- Usage: Recursive removal of directories with all its contents.
- Example: rm -r directory/
- This command deletes a specific directory with all its contents.
Risks Associated:
- No Trash Bin: Unlike many graphical interfaces, the 'rm' does not delete any file to the bin and erases them entirely.
- No Confirmation: No pop-up confirmation means more chances for accidental removal.
Preventing Accidental Deletions:
- Use '-i' Option: By including '– i', a removal confirmation dialogue will come up.
Example: rm -i filename.txt
- Create Aliases: To make it the default behavior, create an alias for rm with the -i option.
Example: alias rm='rm -i'
21. What is the default route in a Linux network configuration? How can you view and modify it?
Default Route in Linux Network Configuration:
In the case of Linux network configuration, there is a default route through which packets travel, provided that they do not coincide with any particular route in a routing table. It will usually act as a passage for sending traffic toward remote sites on other networks.
- Viewing the Default Route: 'ip route show'
- Modifying the Default Route: 'sudo ip route add default via new_gateway_ip'
Explanation:
- The command' ip route show' shows the current and default routing table.
- The command' ip route add default via new_gateway_ip' is the specified gateway for the default route modification or addition using the' ip route add default via' command
Note: The 'route' command can replace the' ip route' to view and modify the routing table.
22. Explain the concept of multi-user mode in Linux. How does it impact system resources and user interactions?
The multi-user mode in Linux denotes a situation when many users can log on and connect with the system simultaneously. Linux enables a variety of virtual consoles or terminal sessions. Consequently, people can be logged in locally or remotely. Among the multi-user modes are the various run levels that define different operational states, starting with the single-user mode (run level 1) and ending with the multi-user mode (run levels 2 to 5).
Impact on System Resources and User Interactions:
- Resource Sharing: Efficient resource sharing allows several users to carry out processes and execute instructions simultaneously in multi-user mode.
- Simultaneous Logins: The users can log in through the terminal, ssh, etc, thereby promoting teamwork and synchronization of operations within the system.
- System Services: The vital systems which support users' interaction, networking, and other essential services are started in multi-user mode.
To change the run level and enter multi-user mode, the 'init' command can be used. You may note that many Linux distributions have now transitioned to using 'systemd' as the default init system.
23. How do you identify and mount a storage device in Linux? Provide a command for each.
1. Identifying a Storage Device:
To list accessible storage devices, run 'lsblk' or 'fdisk -l'.
Example: lsblk
2. Mounting a Storage Device:
- The 'mount' function should be used to mount on a specific mount-point, a storage device.
Example: sudo mount /dev/sdX1 /mnt/mount_point
- In this case, '/dev/sdX1' stands for device partition, while '/mnt/mount_point' will represent the directory where the device will be mounted.
- Permanently mount the drive by editing the '/etc/fstab' file.
Note: Instead, use a real device (/dev/sdX1) and mount point.
24. Discuss how Linux provides a wide range of commands and utilities for system administration. Name three commands that showcase this diversity.
Linux's Wide Range of Commands and Utilities for System Administration:
The operating system, Linux, has numerous commands and utilities for system administration. Here are three commands that showcase this diversity:
1. 'ps' (Process Status):
- Usage: Display information about processes.
- Example: ps aux
- The listing of all processes running in the system is offered with this Command.
2. 'df' (Disk Free):
- Usage: Show how much disk space is being used.
- Example: df -h
- Mounted filesystems containing free and occupied space are displayed under this Command.
3. 'iptables' (IP Tables):
- Usage: Configure rules for packet filtering.
- Example: df -h
- This means it shows the existing firewall rules.
The various commands used show the wide array of capabilities of the system for controlling processes, disk space management, and network security arrangement.
25. What is the purpose of the 'locate' command in Linux? How does it differ from the 'find' command?
In a Linux-based operating system, a 'locate' command quickly establishes where such files or directories are located in a system. It is based on the predefined file system index, and thus, finds are more expeditious than the 'find' Command.
Differences from the 'find' Command:
- Speed: 'locate' is usually quicker than "find" since it accesses a pre-composed registry.
- Usage: 'locate' works fast with finding files, as 'find' is stronger with more search options considering multiple categories.
- Indexing: the command 'locate' relies on a pre-built index, and to ensure it's up-to-date, the 'updatedb' command is used periodically.
Usage
It searches for the given file name in the index and shows all the match paths.
However, it should be noted that the 'locate' may not depict the latest data due to the fact that the 'updatedb' Command issues an update for its index periodically. Example: locate filename
Most popular Linux applications
Because of its stability, performance, and flexibility, the Linux kernel is used in many applications. Following are a few examples:
1. Mozilla Firefox
Firefox is the fastest web browsing application for Linux. It is user-friendly and supports many extensions and add-ons that provide a customizable experience to the users. Pitched as the biggest competitor to Google Chrome, its auto-update feature and tracker blocking mechanism, Mozilla Firefox provides users with minimum browsing interruptions.
2. VLC Media Player
VLC is one of the popular media players. It supports all kinds of audio or video files without any need to download additional codecs. VLC Media Player can be used for converting files from one format to another, clipping videos, creating playlists, etc. An interesting feature of this application is that it can be integrated with other streaming software and services as well.
3. Thunderbird
Thunderbird helps to conveniently manage emails. It is a free and powerful wizard that acts as an assistant to manage an unlimited number of accounts. One of the most useful features of Thunderbird is the backup storage for all the messages. So, if one happens to delete any important message, the same can be easily retrieved. Apart from this, Thunderbird has multiple calendars and RSS reader to help the user look at the headlines in one glance.
4. LibreOffice
LibreOffice is considered one of the best office suites that consist of basic as well as advanced features. Its components are equipped to handle any kind of operation, such as word processing, presentations, spreadsheets, vector graphics, mathematical calculations, etc.
5. Timeshift
Timeshift is a useful application that helps to keep a backup of driver updates and configuration changes. It is similar to the system restore feature in Windows. It helps to protect the system by creating snapshots of the system. These can then be re-established whenever needed, and all the changes in the system can be reversed.
6. Shortcut
Shortcut is a video editing software available for Linux. It can be used in macOS and Windows as well. The software supports all kinds of audio and video formats and is free to use. Shortcut has various audio and video filters such as 360-degree video filters, chroma-key, peak meter, spectrum analyzer, etc. Acting as a full-fledged package for video editing, Shortcut also makes the process of cutting, pasting, adding text, trimming, or rotating videos easy and convenient.
Linux skills are highly in demand. Hence, considering the massive importance of Linux, it is recommended to prepare Linux interview questions for any job interview that requires you to have such software skills. One can brush up on the basic concepts of Linux through short tutorials to prepare well for the Linux interview questions. Solving Linux quizzes can be a good way to get a grasp of the fundamental concepts of Linux.
More Reads:
As a biotechnologist-turned-writer, I love turning complex ideas into meaningful stories that inform and inspire. Outside of writing, I enjoy cooking, reading, and travelling, each giving me fresh perspectives and inspiration for my work.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter
Blogs you need to hog!

This Is My First Hackathon, How Should I Prepare? (Tips & Hackathon Questions Inside)

10 Best C++ IDEs That Developers Mention The Most!

Advantages and Disadvantages of Cloud Computing That You Should Know!









Comments
Add comment