Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Don't have an account? Sign up
Blogs you need to hog!

Organize Hackathons: The Ultimate Playbook With Past Case Studies
Shivani Goyal


What is Campus Recruitment? How To Tap The Untapped Talent?
Shivangi Vatsal

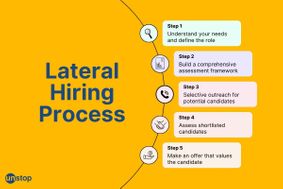
Lateral Hiring: A Complete Guide To The Process, Its Benefits, Challenges & Best Practices
Srishti Magan

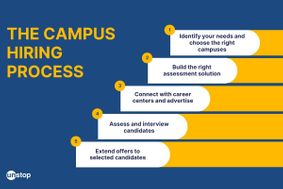
Step-By-Step Approach To Building A Winning Campus Recruitment Strategy
Srishti Magan



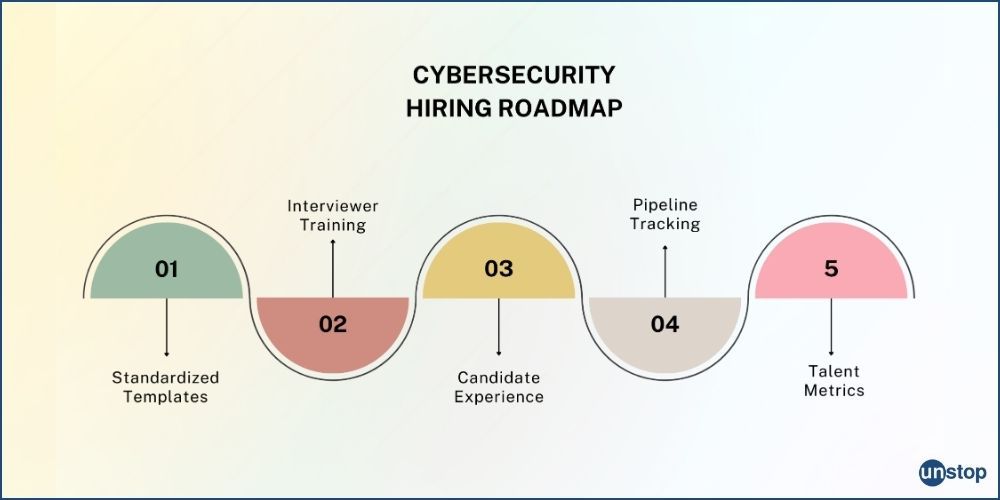
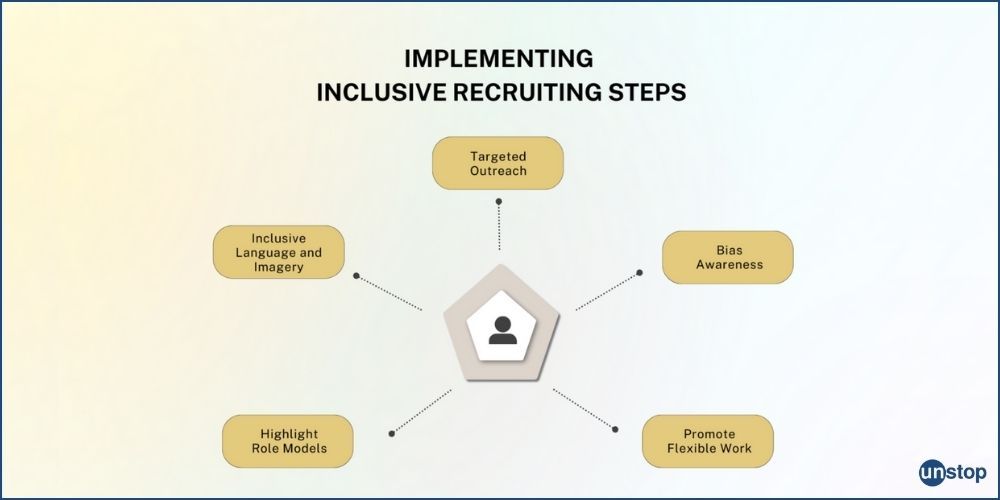








Comments
Add comment