- Networking Interview Questions: Basics
- Networking Interview Questions: Intermediate
- Networking Interview Questions: Advanced
- Conclusion
Top 100 Networking Interview Questions & Answers - For All Levels

When preparing for a networking interview, it's essential to be well-versed in both theoretical concepts and practical applications of networking protocols, tools, and technologies. Networking plays a crucial role in today's digital world, enabling communication between devices, systems, and applications. This article will guide you through key networking interview questions, covering foundational topics such as the OSI model, IP addressing, subnetting, and network security, ensuring you're ready to tackle common and complex queries with confidence.
Networking Interview Questions: Basics
1. What is a network?
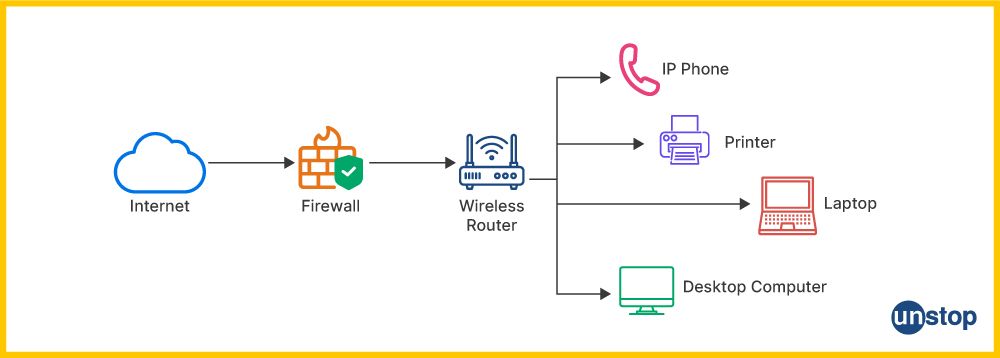
A network is a collection of interconnected devices (like computers, servers, switches, routers) that communicate with each other to share resources, data, and services. Networks can range in scale from a small Local Area Network (LAN) to vast Wide Area Networks (WAN), such as the internet.
2. What are the different types of networks (LAN, WAN, MAN)?
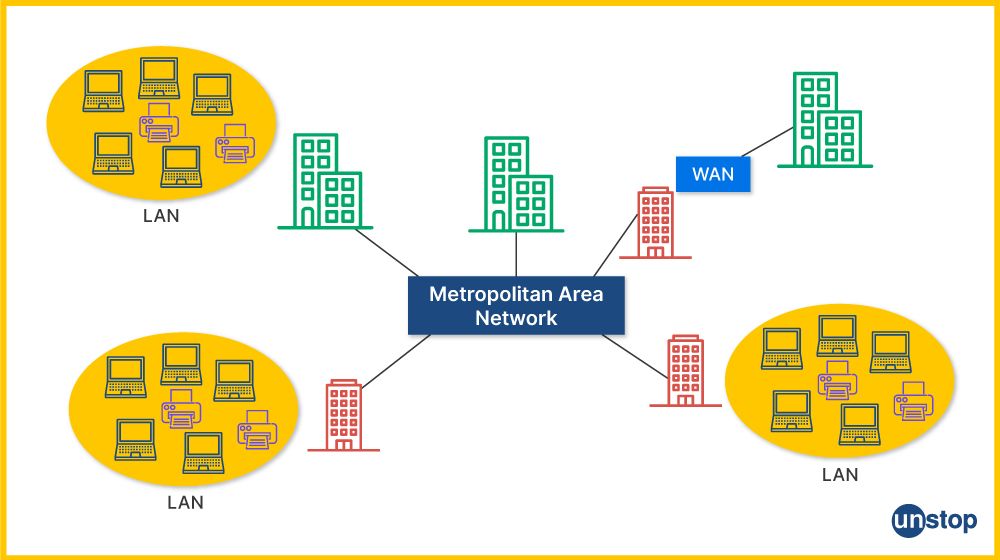
The key distinction between LAN, MAN and WAN are as follows:
- LAN (Local Area Network): A network that covers a small geographical area like a home, school, or office. It enables devices within close proximity to share resources.
- WAN (Wide Area Network): A large network that spans over a broad area, like cities, countries, or even globally. The internet is the most prominent example of a WAN.
- MAN (Metropolitan Area Network): This network covers a city or large campus. It is larger than a LAN but smaller than a WAN, used for connecting users within a specific geographic area, like a city.
3. What is the OSI Model? Name its layers.
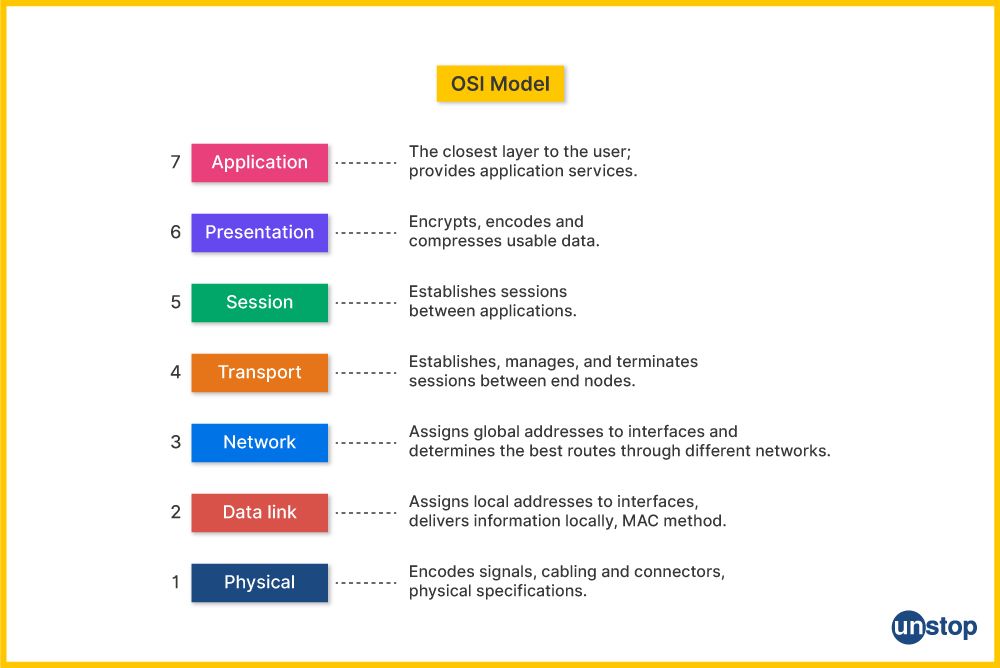
The OSI (Open Systems Interconnection) Model is a conceptual framework used to understand how different network protocols interact in layers. It has 7 layers:
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
4. What is TCP/IP?
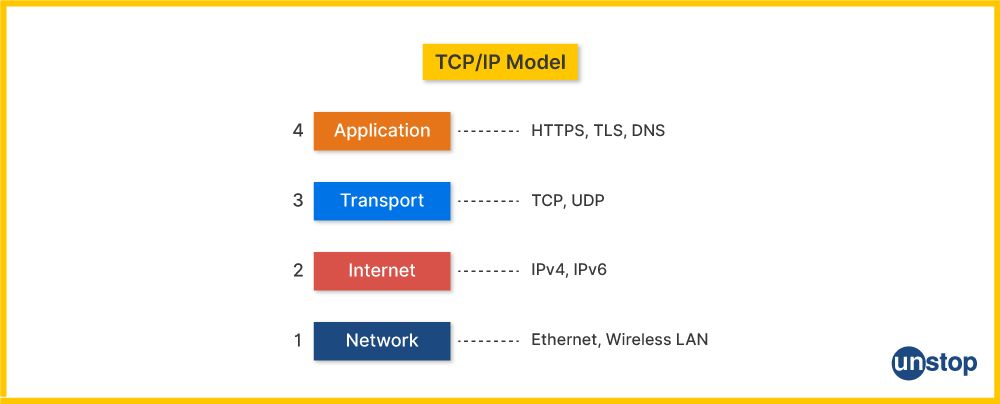
TCP/IP (Transmission Control Protocol/Internet Protocol) is a suite of communication protocols used to connect devices on the internet and other networks. It defines how data is transmitted and ensures that it reaches its destination accurately.
- TCP is responsible for breaking data into packets, ensuring reliable delivery, and reassembling the data in the correct order.
- IP handles the addressing and routing of these packets across networks to their destination.
- Together, TCP/IP forms the backbone of internet communication, enabling devices to interact across vast networks, from small local networks to the global internet. It is the standard protocol suite for most modern networks.
5. What is the difference between TCP and UDP?
Here's are the key differences between TCP and UDP:
| Aspect | TCP (Transmission Control Protocol) | UDP (User Datagram Protocol) |
|---|---|---|
| Connection Type | Connection-oriented (establishes a connection before data transfer) | Connectionless (sends data without setting up a connection) |
| Reliability | Reliable (data delivery is guaranteed, with acknowledgment) | Unreliable (no guarantee of data delivery, no acknowledgment) |
| Data Transfer | Ensures ordered and accurate data delivery | Data may be lost, arrive out of order, or be duplicated |
| Error Checking | Yes, includes error-checking, retransmission, and acknowledgment | Yes, but without retransmission or acknowledgment mechanisms |
| Speed | Slower due to connection setup, error handling, and flow control | Faster due to minimal overhead and no connection setup |
| Use Case | Suitable for applications where data accuracy is crucial (e.g., file transfer, web browsing) | Suitable for applications that need speed and can tolerate some data loss (e.g., live streaming, online gaming) |
| Header Size | Larger (20-60 bytes) | Smaller (8 bytes) |
| Flow Control | Yes, flow control using window size | No flow control |
| Congestion Control | Yes, adjusts transmission rate based on network conditions | No congestion control |
| Transmission Method | Segments are sent in a sequence and acknowledged | Packets (datagrams) are sent independently, without tracking |
6. What is an IP address?
An IP address (Internet Protocol address) is a unique identifier assigned to each device on a network. It allows devices to locate and communicate with each other over the internet. There are two main versions: IPv4 (e.g., 192.168.0.1) and IPv6 (e.g., 2001:0db8:85a3::8a2e:0370:7334).
7. What are public and private IP addresses?
- Public IP Address: Used to identify devices on the global internet. It is unique across the entire web and assigned by your ISP (Internet Service Provider).
- Private IP Address: Used within local networks (e.g., in a home or office LAN). Devices within the same private network can communicate using private IPs, but to access the internet, they need a public IP.
8. What is subnetting?
Subnetting is the process of dividing a network into smaller sub-networks or subnets. This helps improve network management and efficiency by organizing IP addresses logically. Subnets allow for better routing, minimize network congestion, and enhance security.
9. What is a default gateway?
A default gateway is the device that routes traffic from a local network to external networks. In most home networks, the router acts as the default gateway, forwarding data from devices on the local network to the internet.
10. What is DNS? How does it work?
DNS (Domain Name System) is a system that translates domain names (like www.example.com) into IP addresses (like 192.0.2.1), which computers use to identify each other on the network. When you type a domain name into a browser, the DNS resolves it to the corresponding IP address, allowing your device to connect to the website’s server.
11. What is DHCP and why is it used?
DHCP (Dynamic Host Configuration Protocol) is a network protocol used to automatically assign IP addresses and other network configuration details (like the subnet mask and default gateway) to devices in a network. This eliminates the need for manual configuration and ensures that each device gets a unique IP physical address, making network management more efficient.
12. What is a MAC address?
A MAC (Media Access Control) address is a unique identifier assigned to a network interface card (NIC) for communication on the physical network layer. It is a hardware address that remains fixed for each device, unlike an IP address, and it helps in identifying devices within a local network.
13. What is ARP? How does it work?
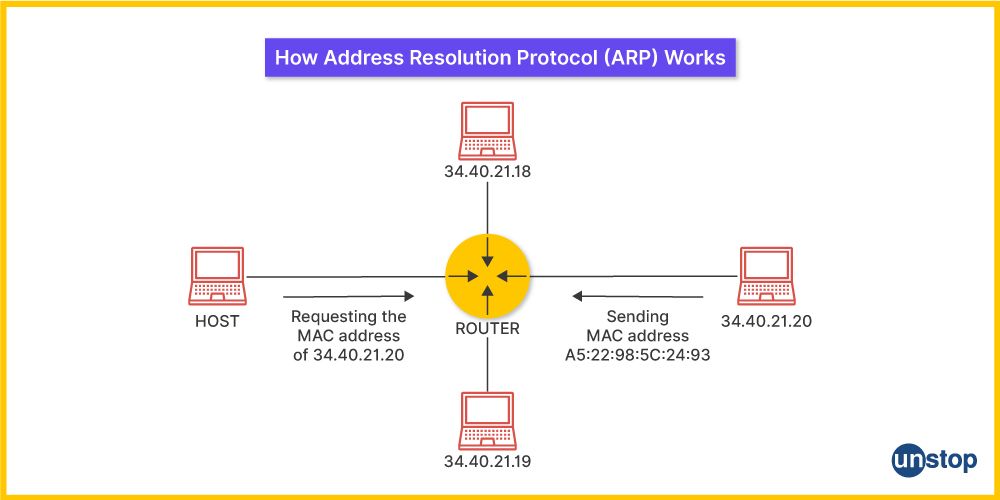
ARP (Address Resolution Protocol) is a protocol used to map an IP address to a MAC address in a local network. When a device wants to communicate with another device, it sends an ARP request asking "Who has this IP address?" The device with the corresponding IP replies with its MAC address, enabling the communication.
14. What is NAT?
NAT (Network Address Translation) is a method used in routers to modify the IP address information in packet headers while they are in transit. NAT allows multiple devices on a local network to share a single public IP address for accessing the internet, providing privacy and conserving the number of public IP addresses used.
15. What is a firewall and what are its types?
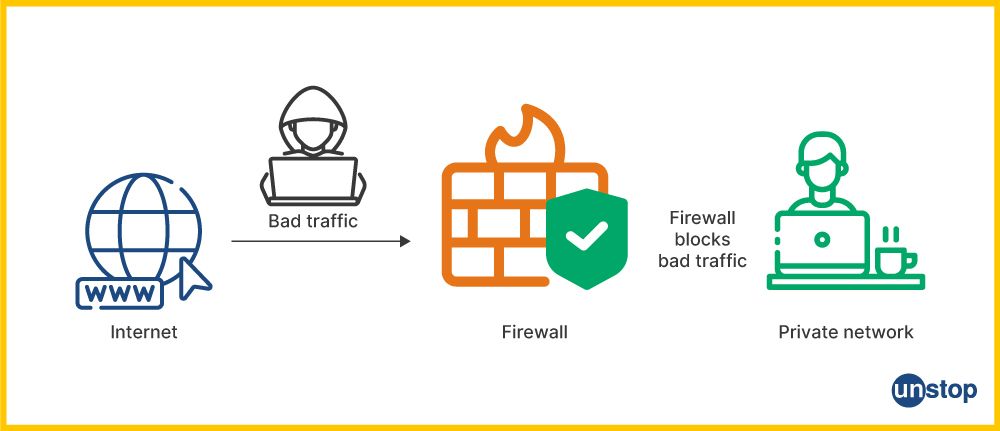
A firewall is a security device that monitors and controls incoming and outgoing network traffic based on predefined security rules. It acts as a barrier between a trusted internal network and an untrusted external network.
Types of Firewalls:
- Packet-Filtering Firewall: Inspects individual packets and blocks or allows them based on source and destination IPs, ports, or protocols.
- Stateful Inspection Firewall: Tracks the state of active connections and makes decisions based on the context of traffic.
- Proxy Firewall: Intercepts traffic between the network and the destination to prevent direct connections.
- Next-Generation Firewall (NGFW): Offers deeper packet inspection, including application-level filtering and intrusion prevention.
16. What is a VPN and how does it work?
A VPN (Virtual Private Network) is a service that creates a secure, encrypted connection (or tunnel) over a public network (like the internet). It allows users to safely send and receive data as if their devices were directly connected to a private network. VPNs are commonly used to protect privacy, hide online activity, or securely access remote networks.
17. What are different types of network topologies?
- Bus Topology: All devices are connected to a single communication line.
- Star Topology: Devices are connected to a central hub or switch.
- Ring Topology: Devices are connected in a circular manner, with data traveling in one or both directions.
- Mesh Topology: Every device is connected to every other device, offering high redundancy.
- Tree Topology: A hybrid topology combining characteristics of star and bus topologies.
- Hybrid Topology: A combination of two or more different types of topologies.
18. What is a VLAN?
A VLAN (Virtual Local Area Network) is a logical segmentation of a physical network into multiple, isolated networks. VLANs allow devices to be grouped together virtually, even if they are not on the same physical LAN. This improves security, reduces network congestion, and makes network management easier.
19. Explain the difference between an intranet and an extranet.
- Intranet: A private network used within an organization for internal communication and data sharing. It is restricted to employees or authorized users.
- Extranet: An extension of an intranet that allows external users (such as partners, vendors, or customers) to access certain internal resources in a controlled manner.
20. What is bandwidth?
Bandwidth refers to the maximum amount of data that can be transmitted over a network connection in a given amount of time, usually measured in bits per second (bps). Higher bandwidth allows more data to be transferred quickly, improving network performance.
21. What is the difference between a router and a switch?
The difference between a router and a switch lies in their function and the network layers they operate on:
| Aspect | Router | Switch |
|---|---|---|
| Primary Function | Routes data between different networks (e.g., connects a LAN to the internet) | Connects devices within the same network (e.g., within a LAN) |
| Layer in OSI Model | Operates at Layer 3 (Network Layer) | Operates at Layer 2 (Data Link Layer) |
| Data Forwarding | Forwards data based on IP addresses | Forwards data based on MAC addresses |
| Purpose | Connects multiple networks and directs data between them (e.g., home network to the internet) | Connects multiple devices within the same network, allowing them to communicate |
| Network Address | Uses IP addresses to route data | Uses MAC addresses to forward frames |
| Routing Capability | Can route data between different networks, including different IP subnets | Does not route between different networks; only forwards data within the same network |
| Traffic Management | Can handle traffic between various networks, provide NAT, and assign IPs | Improves efficiency within the network by reducing data collisions |
| Device Communication | Enables communication between different networks (like LANs and WANs) | Enables communication within the same local network |
| Typical Use | Used to connect home/office networks to the internet or link different subnets | Used to link multiple devices (PCs, printers, etc.) within a local area network |
22. What is the purpose of network protocols?
Network protocols are a set of rules and standards that define how data is transmitted and received across a network. They ensure that devices can communicate efficiently and securely, enabling the seamless exchange of information. Examples include TCP/IP, HTTP, and DNS.
23. What is a load balancer?
A load balancer is a device or software that distributes incoming network traffic across multiple servers to ensure no single server is overwhelmed. It enhances availability, improves performance, and prevents server overload.
24. What is MTU (Maximum Transmission Unit)?
MTU (Maximum Transmission Unit) is the largest size of a packet that can be transmitted over a network in one go. If a packet exceeds the MTU size, it is fragmented into smaller packets, which can affect performance.
25. What is the role of a switch in networking?
A switch connects devices within a local network and forwards data based on MAC addresses. It improves the efficiency of data transfer by reducing collisions and ensuring that data is only sent to the intended recipient, rather than broadcasting it to all devices.
26. What is a socket in networking?
A socket is an endpoint for sending and receiving data across a network connection. It consists of an IP address and a port number and is used in network programming for communication between devices.
Master Computer Networks! Register on this course and begin your learning journey!
27. What is a static IP address?
A static IP address is a fixed, manually assigned IP address that does not change over time. It is often used for devices that require consistent access, like servers and printers.
28. What is a dynamic IP address?
A dynamic IP address is assigned automatically by a DHCP server and may change over time. It is commonly used for most personal devices, like laptops and smartphones, because it allows for flexible IP management.
29. What is a ping command and its usage?
The ping command is used to test the connectivity between two devices over a network. It sends ICMP echo request packets to a target IP address and waits for a reply, helping to measure latency and detect network issues.
30. What is a traceroute command?
The traceroute command traces the path that data takes to reach a destination. It shows each hop (router) along the route and measures the delay at each hop, helping to diagnose network slowdowns or routing issues.
31. Explain the term "network latency."
Network latency refers to the time delay that occurs when data is transmitted from a source to a destination. It is often measured as the round-trip time (RTT) it takes for a packet to travel to the destination and back. Low latency is crucial for real-time applications, while high latency can cause noticeable delays.
32. What is HTTP and HTTPS? Explain the difference.
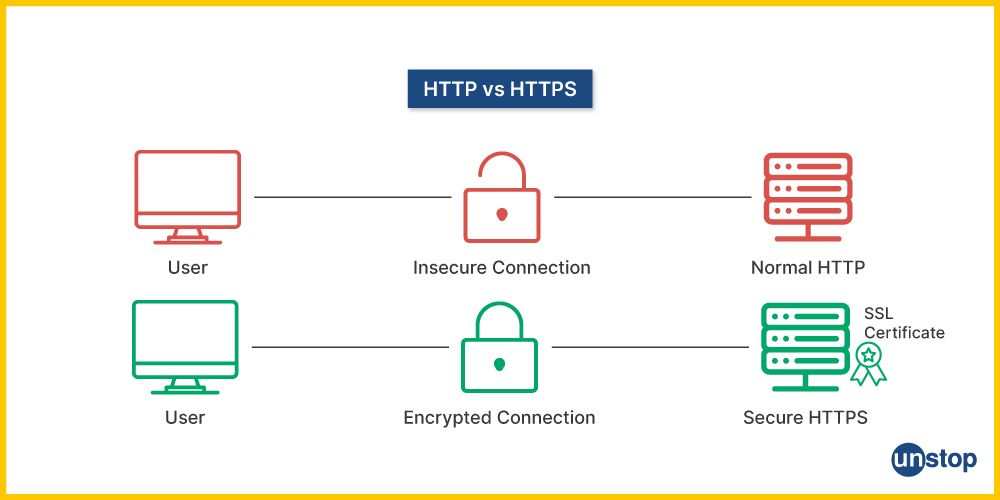
HTTP (HyperText Transfer Protocol) and HTTPS (HyperText Transfer Protocol Secure) are both protocols used for transmitting data over the web, but they differ in terms of security:
| Aspect | HTTP | HTTPS |
|---|---|---|
| Security | Unencrypted, vulnerable to attacks | Encrypted with SSL/TLS, ensuring secure communication |
| Port | Uses port 80 | Uses port 443 |
| Data Integrity | No guarantee of data integrity | Guarantees data integrity and protection from tampering |
| Use Case | Suitable for non-sensitive data transmission | Essential for sensitive data like online banking, payments, and personal information |
| Performance | Slightly faster (no encryption overhead) | Slightly slower due to encryption but more secure |
In short, HTTPS is an enhanced, secure version of HTTP, and it's widely used to protect sensitive data like login credentials and personal information while browsing or making transactions online.
33. Explain half-duplex and full-duplex communication.
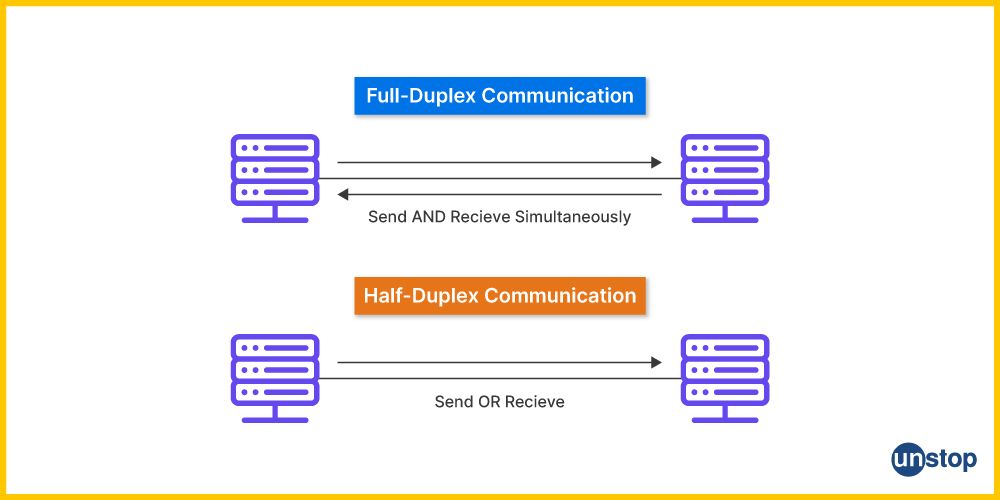
Half-duplex and full-duplex are modes of data transmission that describe how data can be sent and received between devices on a network.
Half-Duplex Communication:
- Definition: Half-duplex communication allows data transmission in both directions, but not simultaneously. A device can either send or receive data at any given time, but not both.
- How It Works: When one device is transmitting data, the other must wait until the transmission is complete before sending data. This mode is like a two-way radio, where one person speaks while the other listens, and then they switch roles.
- Example: Traditional walkie-talkies and some network technologies like Ethernet (in older versions) use half-duplex communication.
Full-Duplex Communication:
- Definition: Full-duplex communication allows data transmission in both directions simultaneously. Devices can send and receive data at the same time without interference.
- How It Works: Both devices can communicate simultaneously, similar to a telephone conversation where both parties can talk and listen at the same time.
- Example: Modern Ethernet networks, telephones, and most contemporary communication systems use full-duplex communication.
34. What is latency in networking?
Latency refers to the delay in data transmission over a network. It is the time it takes for a packet of data to travel from the source to the destination and back, measured in milliseconds. High latency results in slower network performance, especially noticeable in real-time applications like video calls and gaming.
35. What is a proxy server?
A proxy server acts as an intermediary between a client and the internet. It forwards client requests to the destination server, receives responses, and then sends them back to the client. Proxies are used for improving security, caching web pages, and bypassing content restrictions.
36. What is port forwarding?
Port forwarding is a networking technique used to direct external traffic to a specific internal IP address and port on a private network. It allows remote devices to connect to services within a private network, such as hosting a website or game server.
37. What is the difference between unicast, multicast, and broadcast?
- Unicast: Data is sent from one source to one specific destination (one-to-one communication).
- Multicast: Data is sent from one source to multiple specific destinations in a group (one-to-many).
- Broadcast: Data is sent from one source to all devices on the network (one-to-all).
38. What is the role of ICMP in networking?
ICMP (Internet Control Message Protocol) is used for network diagnostics and error reporting. It helps in troubleshooting by sending messages like ping or traceroute to detect network issues, report unreachable hosts, and measure latency.
39. What is a network interface card (NIC)?
A NIC (Network Interface Card) is a hardware component that allows a device (like a computer or server) to connect to a network. It provides the physical interface for both wired and wireless network connections and has a unique MAC address for identification.
40. What are collision domains and broadcast domains?
Collision domains and broadcast domains are concepts used to describe different aspects of network segmentation and traffic management. Understanding these domains is essential for efficient network design and troubleshooting:
| Aspect | Collision Domain | Broadcast Domain |
|---|---|---|
| Definition | Segment where data packets can collide | Segment where broadcast frames are propagated |
| Controlled By | Managed by network devices like switches or hubs | Managed by routers or VLANs |
| Impact of Collisions | Leads to packet loss and retransmission | Excessive broadcast traffic can reduce performance |
| Example | Devices connected to a hub or a single switch port | Devices within the same VLAN or subnet |
In summary, a collision domain deals with data packet collisions in half-duplex communications, while a broadcast domain handles the distribution of broadcast messages across network segments.

Networking Interview Questions: Intermediate
41. How does routing work in a network?
Routing is the process of determining the best path for data packets to travel from the source to the destination across a network. Routers are devices that manage this process by examining the destination IP address of incoming packets and using routing tables to forward them to the appropriate next hop or destination network. The routing process involves:
- Path Selection: Choosing the most efficient route based on metrics like distance, cost, or network conditions.
- Forwarding: Sending packets to the next router or destination network based on the selected path.
- Routing Protocols: Using protocols like BGP, OSPF, or RIP to dynamically update and maintain routing tables.
42. What is BGP (Border Gateway Protocol)?
BGP (Border Gateway Protocol) is an exterior gateway protocol used to exchange routing information between different autonomous systems (ASes) on the internet. BGP is crucial for making routing decisions based on network policies and path attributes. It helps ensure data packets find the best route across the diverse and complex web of interconnected networks that make up the internet.
43. What is the difference between a layer 2 switch and a layer 3 switch?
- Layer 2 Switch: Operates at the Data Link Layer (Layer 2) of the OSI model. It uses MAC addresses to forward frames within the same VLAN or network segment. Layer 2 switches are used primarily for internal network segmentation and traffic management.
- Layer 3 Switch: Operates at the Network Layer (Layer 3) of the OSI model. It can perform routing functions in addition to switching, using IP addresses to forward packets between different VLANs or subnets. Layer 3 switches are used for inter-VLAN routing and managing traffic between different network segments.
| Aspect | Layer 2 Switch | Layer 3 Switch |
|---|---|---|
| OSI Layer | Data Link Layer (Layer 2) | Network Layer (Layer 3) |
| Addressing | MAC addresses | IP addresses |
| Traffic Management | Manages traffic within the same VLAN or broadcast domain | Routes traffic between different VLANs or subnets |
| Functionality | Switches Ethernet frames based on MAC addresses | Routes packets and switches frames based on IP addresses |
| Routing Capabilities | None | Supports routing between different IP networks |
| Typical Use | Connecting devices within a LAN | Integrating routing and switching functions, managing multiple VLANs |
44. What is a subnet mask? How does it work?
A subnet mask is a 32-bit number used to divide an IP address into network and host portions. It helps routers and switches determine which part of an IP address identifies the network and which part identifies the device (host). By applying the subnet mask to an IP address, we can:
- Identify the Network Portion: Determine the range of IP addresses within the same subnet.
- Separate Networks: Facilitate the creation of multiple subnets within a larger network, improving organization and management.
45. Explain CIDR (Classless Inter-Domain Routing).
CIDR (Classless Inter-Domain Routing) is a method for allocating IP addresses and routing IP packets more efficiently than the older class-based system. It uses variable-length subnet masking (VLSM) to allow for more flexible and efficient IP address allocation by specifying IP addresses and their associated prefix lengths (e.g., 192.168.0.0/24). CIDR helps to:
- Reduce IP Address Wastage: By allowing for subnet sizes tailored to actual needs.
- Improve Routing Efficiency: By aggregating multiple IP address ranges into a single routing table entry.
46. What is QoS (Quality of Service)?
QoS (Quality of Service) is a set of techniques used to manage network traffic and ensure the performance of high-priority applications. QoS helps prioritize certain types of traffic (e.g., voice, video) over others (e.g., file downloads) to meet performance requirements. It involves:
- Traffic Classification: Categorizing traffic into different classes or priority levels.
- Traffic Shaping: Controlling the flow of traffic to prevent congestion.
- Bandwidth Allocation: Ensuring that critical applications receive the necessary bandwidth.
47. What is OSPF (Open Shortest Path First)?
OSPF (Open Shortest Path First) is an interior gateway routing protocol used within an autonomous system to find the best path for data packets based on the shortest path algorithm. It is a link-state protocol that creates a topology map of the network, allowing routers to calculate the shortest path to each network destination. OSPF is efficient, scalable, and supports large networks with complex topologies.
48. What is RIP (Routing Information Protocol)?
RIP (Routing Information Protocol) is a distance-vector routing protocol used to manage routing within an autonomous system. It uses hop count as its metric to determine the best path for data packets. RIP has limitations, such as a maximum hop count of 15, which can restrict its use in large networks. It is relatively simple to configure and is best suited for smaller or less complex networks.
49. What is STP (Spanning Tree Protocol)?
STP (Spanning Tree Protocol) is a network protocol designed to prevent loops in Ethernet networks by creating a loop-free logical topology. It works by:
- Identifying Redundant Paths: Detecting and blocking redundant paths that could cause network loops.
- Maintaining a Tree Structure: Ensuring a single active path between network switches, while backup paths remain in standby mode.
- Reconfiguring Paths: Automatically reactivating backup paths if the active path fails.
50. What is MPLS (Multiprotocol Label Switching)?
MPLS (Multiprotocol Label Switching) is a data-carrying technique that uses labels to direct data packets along predefined paths through a network, rather than using traditional IP routing. MPLS provides:
- Efficient Traffic Management: By using labels to forward packets based on predetermined paths.
- Improved Performance: Through faster packet forwarding and reduced latency.
- Support for Multiple Protocols: MPLS can carry various types of traffic, including IP, ATM, and frame relay, making it versatile and scalable for different network environments.
51. Explain the term "network redundancy."
Network redundancy refers to the practice of providing multiple pathways for data traffic to travel in a network, ensuring that if one link or device fails, an alternative route or device can take over without disrupting service. Redundancy enhances network reliability, minimizes downtime, and provides fault tolerance. Common redundancy techniques include using backup routers, switches, and alternative physical links.
52. What is HSRP (Hot Standby Router Protocol)?
HSRP (Hot Standby Router Protocol) is a Cisco proprietary protocol that provides network redundancy for IP networks. It allows multiple routers to work together as a group, sharing a virtual IP address. One router is designated as the active router and handles traffic, while the others are in standby mode. If the active router fails, one of the standby routers takes over, ensuring uninterrupted network connectivity.
53. What is Link Aggregation?
Link Aggregation is a technique used to combine multiple physical network links into a single logical link. This increases bandwidth, improves performance, and provides redundancy in case one of the physical links fails. It is commonly used in switch-to-switch or switch-to-server connections to enhance network throughput and reliability.
54. What is LACP (Link Aggregation Control Protocol)?
LACP (Link Aggregation Control Protocol) is a protocol used to dynamically manage link aggregation. It allows devices (like switches or servers) to automatically negotiate the aggregation of multiple physical links into a single logical connection. LACP ensures that link aggregation is set up properly and can adjust dynamically if one or more links fail or recover.
55. What is a DMZ (Demilitarized Zone)?
A DMZ (Demilitarized Zone) is a physical or logical subnet that separates an internal network from external networks (usually the internet). It is commonly used to host public-facing services like web, email, or DNS servers while protecting the internal network from potential security threats. The DMZ serves as a buffer zone, allowing external users access to certain services without granting them access to the internal network.
56. What are the different types of NAT? (Static, Dynamic, PAT)
NAT (Network Address Translation) is used to map private IP addresses within a local network to public IP addresses for communication with external networks. Types of NAT include:
- Static NAT: Maps one private IP address to a single public IP address. It is used for devices that need consistent, unchanging IP mappings.
- Dynamic NAT: Maps a private IP address to one of a pool of available public IP addresses. The mapping is temporary and may change.
- PAT (Port Address Translation): A variation of dynamic NAT where multiple private IP addresses share a single public IP address, differentiated by port numbers. It is commonly used in home and small office networks.
57. What is a broadcast storm?
A broadcast storm occurs when there is excessive broadcast traffic on a network, often due to a loop or misconfigured network devices. This can overwhelm network resources, degrade performance, and potentially bring the network to a halt. Broadcast storms can be mitigated using protocols like Spanning Tree Protocol (STP) to prevent loops.
58. What is the role of DNS caching?
DNS caching involves storing the results of DNS lookups (mapping domain names to IP addresses) temporarily on a local device or server. This reduces the time needed to resolve frequently accessed domain names, speeds up web browsing, and reduces the load on DNS servers. Cached records are retained until their TTL (Time-to-Live) expires.
59. Explain port numbers and their significance in networking.
Port numbers are numerical identifiers used in networking to distinguish between different types of services and applications running on a device. For example, HTTP traffic typically uses port 80, and HTTPS uses port 443. Port numbers ensure that incoming and outgoing traffic is directed to the correct application or service. There are two types:
- Well-Known Ports: Ranging from 0 to 1023, used by standard protocols (e.g., FTP, HTTP).
- Dynamic or Ephemeral Ports: Ranging from 1024 to 65535, used for temporary or client-side communication.
60. What are ephemeral ports?
Ephemeral ports are temporary port numbers automatically assigned by the operating system for client-server communications. When a client initiates a connection to a server, it uses an ephemeral port (typically in the range of 1024 to 65535) as its source port for the duration of the session. After the session ends, the ephemeral port is released and can be reused for future connections.
61. What is a floating static route?
A floating static route is a backup route in a network, designed to take over if the primary route fails. It is configured with a higher administrative distance than the primary route, meaning it will only be used when the primary route becomes unavailable. This helps maintain network connectivity during link or device failures by ensuring traffic can still be routed through an alternate path.
62. How does VLAN tagging work?
VLAN tagging allows multiple VLANs (Virtual Local Area Networks) to exist on the same physical network by marking Ethernet frames with a unique identifier (VLAN ID). Using the IEEE 802.1Q standard, a 4-byte tag is inserted into the Ethernet frame header, which includes the VLAN ID and priority information. This tag helps switches identify which VLAN a frame belongs to, ensuring proper routing across a shared network infrastructure. Once the frame reaches its destination, the tag is removed.
63. What is the difference between VLAN and VXLAN?
The primary difference between VLAN (Virtual Local Area Network) and VXLAN (Virtual Extensible LAN) lies in their purpose, scalability, and the environments where they are typically used:
| Aspect | VLAN (Virtual Local Area Network) | VXLAN (Virtual Extensible LAN) |
|---|---|---|
| Purpose | Segments a physical network into multiple logical networks. | Extends VLANs across a larger Layer 2 network, typically used in data centers for multi-tenant environments. |
| Layer | Operates at Layer 2 of the OSI model. | Operates at Layer 2 over Layer 3, enabling communication across different IP networks. |
| Scalability | Supports up to 4096 VLANs (due to 12-bit VLAN ID limitation). | Supports up to 16 million VXLANs (due to 24-bit VXLAN ID), allowing for much greater scalability. |
| Encapsulation | Frames are tagged with a VLAN ID using 802.1Q tagging. | VXLAN uses encapsulation over UDP to transport Layer 2 frames over Layer 3 networks. |
| Use Case | Commonly used in smaller, localized networks (e.g., within an office or campus network). | Primarily used in large-scale data centers and cloud environments to support multi-tenant architectures and virtualized environments. |
| Broadcast Domain | Provides isolation of broadcast domains within a LAN. | Extends broadcast domains over IP networks, enabling Layer 2 adjacency across geographically separate physical locations. |
| Configuration | Easier to configure and manage in smaller environments. | More complex to configure and manage, requiring additional technologies like VTEP (VXLAN Tunnel Endpoints). |
| Overhead | Minimal overhead with VLAN tags (4 bytes added to the frame). | Higher overhead due to VXLAN encapsulation (adds around 50 bytes per packet). |
| Protocol Dependency | Direct Ethernet frames; no tunneling or encapsulation. | Encapsulates Layer 2 Ethernet frames within Layer 3 IP/UDP packets. |
64. Explain 802.1Q encapsulation.
802.1Q encapsulation is a standard for VLAN tagging. It adds a 4-byte tag into the Ethernet frame's header, which includes:
- A VLAN identifier (12 bits): Specifies the VLAN to which the frame belongs.
- A Priority field (3 bits): Allows for Quality of Service (QoS) differentiation. This encapsulation allows frames to be routed properly between VLANs, maintaining network segmentation even when multiple VLANs share the same physical network.
65. What is MAC flooding?
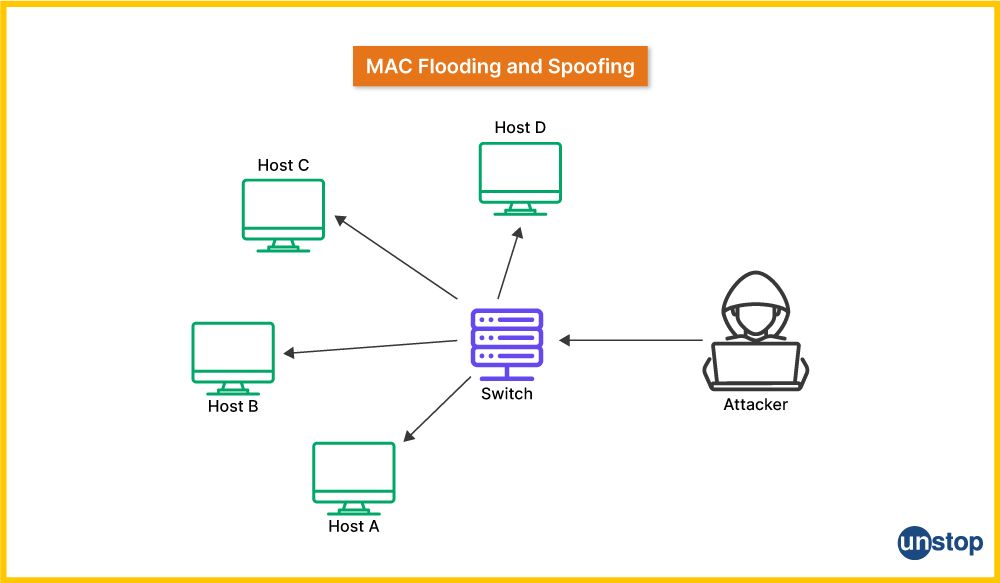
MAC flooding is a type of network attack that overwhelms a switch’s MAC address table by sending a flood of frames with different fake MAC addresses. When the table is full, the switch can't map incoming frames to their correct destination and starts forwarding them to all ports. This exposes sensitive data to all devices on the network and can lead to security breaches. MAC flooding exploits switches that don't have enough capacity to handle large numbers of addresses.
66. What is split-horizon in networking?
Split-horizon is a routing technique used to prevent routing loops in distance-vector routing protocols like RIP. The idea is simple: a router does not advertise a route back out of the interface from which it was learned. This prevents incorrect routing information from being propagated, reducing the chances of a loop forming and ensuring more stable network routing.
67. What are ACLs (Access Control Lists)?
Access Control Lists (ACLs) are rules applied to routers or switches that determine whether network traffic is permitted or denied based on predefined criteria. ACLs can be used to:
- Control access to network resources.
- Filter traffic based on IP addresses, port numbers, or protocols.
- Enhance security by blocking unauthorized users or restricting certain types of network traffic. ACLs play a crucial role in network security by enforcing policies that control which devices or users can access certain parts of the network.
68. What is a routing table?
A routing table is a database used by routers to determine the best path for forwarding packets across a network. It contains information about:
- Destination IP addresses or subnets.
- Next hop addresses (the next router or interface to send the packet to).
- Metrics (used to decide the best path if multiple routes exist). Routing tables are either built manually (static routing) or dynamically (dynamic routing) and are essential for guiding traffic through interconnected networks.
69. Explain the difference between interior and exterior gateway protocols.
The difference between Interior Gateway Protocols (IGPs) and Exterior Gateway Protocols (EGPs) lies in where they are used and how they manage routing information:
| Aspect | Interior Gateway Protocols (IGPs) | Exterior Gateway Protocols (EGPs) |
|---|---|---|
| Usage Scope | Within a single autonomous system (e.g., a company’s internal network). | Between different autonomous systems (e.g., ISP networks). |
| Examples | RIP, OSPF, EIGRP | BGP |
| Focus | Optimized for fast routing within a controlled environment. | Optimized for large-scale routing between multiple, independent networks. |
| Administration | Managed by a single entity (organization or network). | Involves coordination between different entities (ISPs, organizations). |
| Routing Decisions | Based on metrics like hop count or cost (link-state or distance-vector methods). | Based on policies, AS paths, and administrative preferences. |
70. How does dynamic routing differ from static routing?
Here are the key differences between dynamic routing and static routing in networking:
| Feature | Static Routing | Dynamic Routing |
|---|---|---|
| Configuration | Manually configured by the network administrator. | Automatically configured using routing protocols. |
| Adaptability | Does not adapt to network changes; requires manual updates. | Automatically adapts to changes like link failures or topology updates. |
| Scalability | Less scalable for large networks; more effort required to manage. | Highly scalable; suitable for large, complex networks. |
| Complexity | Simple to implement in small networks. | More complex due to the need for routing protocols and algorithms. |
| Resource Usage | Minimal resource usage (CPU, memory). | Consumes more resources (CPU, memory) to run protocols and process updates. |
| Routing Decisions | Predefined by the administrator; routes are fixed. | Routing decisions are dynamic and based on real-time network conditions. |
| Best Path Selection | Static, based on manual configuration (no path recalculation). | Dynamic, calculated based on metrics such as cost, distance, or bandwidth. |
| Convergence | No convergence mechanism (doesn't detect link failures). | Supports fast convergence; routes are recalculated automatically. |
| Maintenance | Requires frequent manual intervention for changes. | Self-maintaining; routers automatically update each other. |
| Use Case | Best for small, stable networks with few changes. | Ideal for larger, more dynamic networks where paths may change often. |
71. What is DNS forwarding?
DNS forwarding is a method used by DNS servers to pass on DNS queries to another server when the requested domain name is not found in the local cache. Typically, an internal DNS server forwards the request to a public DNS server (e.g., Google DNS or an ISP’s DNS server), which then resolves the query. This optimizes DNS resolution, reduces latency, and improves network efficiency by relying on external resources when needed.
72. What is GRE (Generic Routing Encapsulation)?
GRE (Generic Routing Encapsulation) is a tunneling protocol developed by Cisco that encapsulates a variety of network layer protocols inside virtual point-to-point links. GRE allows for the transport of traffic across IP networks by creating a tunnel between two endpoints. It is often used in VPNs to transport traffic between remote networks or between a client and a server, and can encapsulate Layer 3 packets over IP networks.
73. Explain how NAT traversal works.
NAT traversal is a technique used to allow traffic to pass through a router or firewall that uses Network Address Translation (NAT). Since NAT modifies IP address information in packet headers, it can interfere with protocols like IPsec or applications that require end-to-end connectivity. NAT traversal methods, such as using UDP encapsulation or technologies like STUN (Session Traversal Utilities for NAT), help ensure that the connections can bypass or navigate through NAT devices, enabling proper communication between endpoints.
74. What are IPsec protocols?
IPsec (Internet Protocol Security) is a suite of protocols used to secure IP communications by authenticating and encrypting each IP packet in a communication session. It consists of several components:
- AH (Authentication Header): Provides data integrity and authenticity without encryption.
- ESP (Encapsulating Security Payload): Provides encryption, integrity, and authentication for the IP packet payload.
- IKE (Internet Key Exchange): Negotiates and establishes security associations and keys between the two communicating devices. IPsec is widely used for securing VPN connections.
75. What is the significance of the TTL (Time to Live) field in an IP packet?
The TTL (Time to Live) field in an IP packet specifies the maximum number of hops (routers or switches) the packet can pass through before being discarded. Each router that forwards the packet decreases the TTL by 1, and when it reaches 0, the packet is dropped. TTL prevents infinite loops in routing and helps identify unreachable routes, ensuring that packets do not circulate endlessly in the network.
76. What is port security in switches?
Port security is a feature on network switches that restricts access to specific ports by controlling which devices can connect. It allows the switch to limit the number of MAC addresses allowed on a particular port and can prevent unauthorized devices from gaining network access. If an unknown device tries to connect, the switch can either block the port or generate an alert, enhancing network security.
77. Explain the purpose of ARP spoofing.
ARP spoofing is a malicious attack where an attacker sends falsified ARP (Address Resolution Protocol) messages to associate their MAC address with the IP address of a legitimate device on the network. This allows the attacker to intercept, modify, or even block data intended for that legitimate device. ARP spoofing is commonly used in man-in-the-middle (MITM) attacks to compromise network security.
78. What is DHCP snooping?
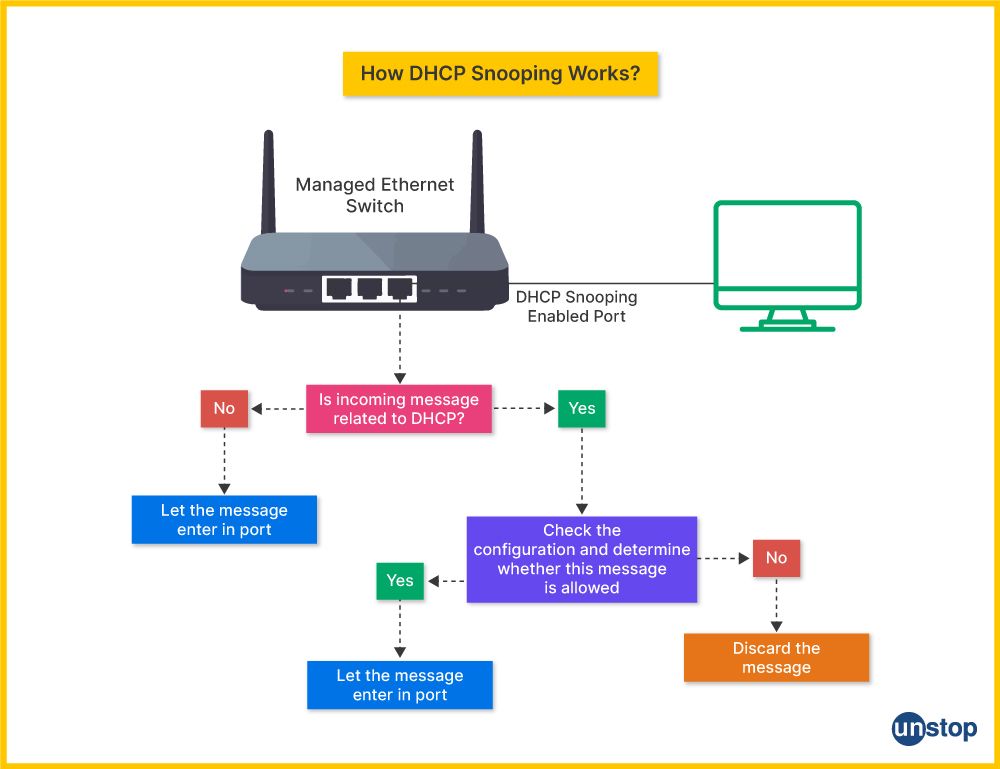
DHCP snooping is a security feature implemented on switches that monitors and controls DHCP traffic. It prevents rogue DHCP servers from assigning malicious or incorrect IP addresses to clients. The switch inspects DHCP messages and allows only trusted ports to act as DHCP servers, ensuring that only valid DHCP responses reach clients. This helps protect the network from attacks like DHCP spoofing.
79. How does proxy ARP work?
Proxy ARP is a technique where a router or network device responds to ARP requests on behalf of another device that resides on a different network. When a device sends an ARP request for an IP address that is not on its local subnet, the proxy ARP-capable router replies with its own MAC address. This allows devices on different subnets to communicate as if they were on the same network, without needing explicit routing configuration.
80. Explain the concept of route summarization.
Route summarization, also known as route aggregation, is the process of consolidating multiple IP routes into a single, summarized route. By combining several smaller subnets into one larger network address, routers can reduce the size of their routing tables, improving efficiency and performance. Route summarization is commonly used in large networks to simplify routing updates and reduce the amount of memory and processing power required for routing decisions.
Networking Interview Questions: Advanced
81. What is SDN (Software-Defined Networking)? How does it work?
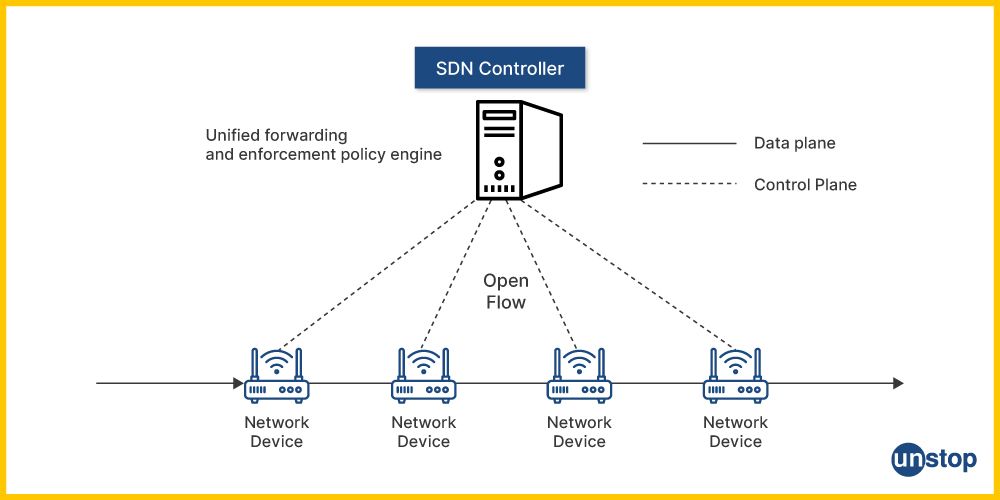
Software-Defined Networking (SDN) is a network architecture approach that allows for centralized control and programmability of the network. Instead of relying on hardware-based configurations, SDN decouples the control plane (network decision-making) from the data plane (packet forwarding), enabling administrators to manage network services through software-based controllers. This centralized control allows for more flexibility, automation, and efficient network management, making it easier to optimize traffic flow, enhance security, and deploy new applications quickly.
82. What is the purpose of IPv6, and how does it differ from IPv4?
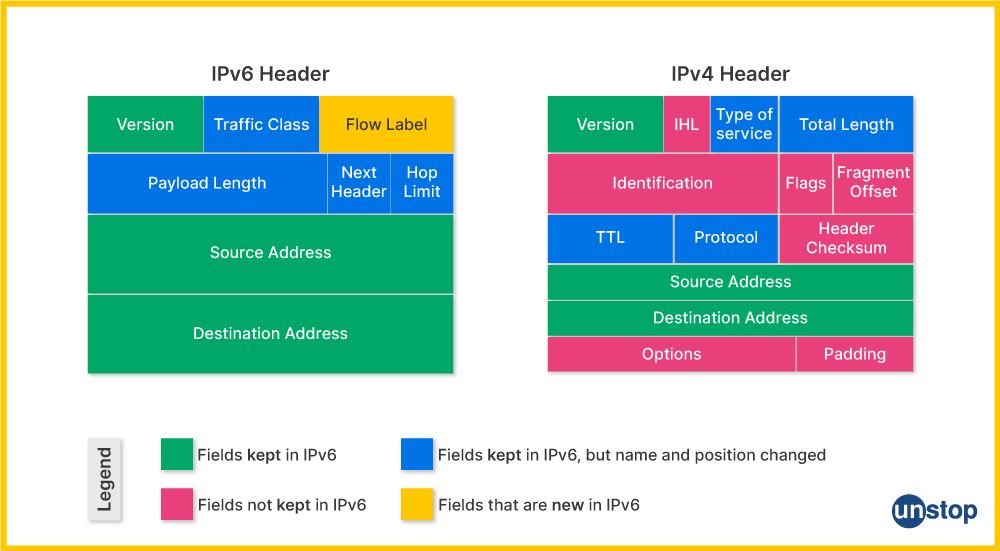
IPv6 was developed to address the exhaustion of IPv4 addresses. While IPv4 uses a 32-bit address format, allowing for about 4.3 billion unique addresses, IPv6 uses a 128-bit address format, allowing for 340 undecillion (3.4×10^38) unique addresses. This immense address space solves the problem of address depletion and supports the growing number of devices connecting to the internet. In addition to the expanded address space, IPv6 also introduces improvements in areas like routing efficiency, auto-configuration, and security (IPsec is built-in).
83. How does BGP prevent routing loops?
BGP (Border Gateway Protocol) prevents routing loops through the use of an AS_PATH attribute. When a BGP router advertises a route, it appends its Autonomous System (AS) number to the AS_PATH. If a router receives a route advertisement with its own AS number already in the AS_PATH, it knows that the route has already passed through its AS and will reject the route to prevent a loop. This ensures that traffic does not keep circulating between ASes in a loop.
84. Explain MPLS Traffic Engineering.
MPLS Traffic Engineering (TE) allows network operators to optimize traffic flow through their network by directing traffic across specific paths, based on resource availability and performance requirements, rather than relying solely on shortest-path routing. By establishing Label-Switched Paths (LSPs) and using resource-based constraints (such as bandwidth or latency), MPLS TE ensures that critical traffic takes the most efficient path, avoiding congestion and ensuring better quality of service for certain applications.
85. What is a BGP peer?
A BGP peer (or BGP neighbor) is a router that establishes a direct connection with another router using BGP to exchange routing information. These peers communicate to share routes across autonomous systems (for external BGP) or within the same AS (for internal BGP). Peers are typically established manually, and they maintain a session to continuously exchange updates about reachable networks.
86. How does Anycast routing work?
Anycast routing is a network addressing and routing method where multiple devices (usually servers) share the same IP address. The network directs traffic to the nearest or best-performing device based on the router's distance metrics, load, or network conditions. Anycast is commonly used in DNS servers and content delivery networks (CDNs), ensuring faster response times by routing users to the closest server.
87. Explain what EIGRP (Enhanced Interior Gateway Routing Protocol) is.
EIGRP is a distance-vector routing protocol developed by Cisco, which combines features of both link-state and distance-vector protocols. It uses the Diffusing Update Algorithm (DUAL) to calculate the shortest path to a destination and supports features like fast convergence, unequal-cost load balancing, and reduced bandwidth usage. EIGRP is efficient for routing within a single autonomous system and is widely used in enterprise networks.
88. What is the significance of MPLS VPNs?
MPLS VPNs (Multiprotocol Label Switching Virtual Private Networks) provide secure and isolated virtual networks over a shared MPLS infrastructure. MPLS VPNs enable service providers to offer private, segmented networks to multiple customers using the same backbone, without compromising on security or performance. This allows businesses to connect different branches securely over a service provider's network, with the added benefit of QoS (Quality of Service) for traffic prioritization.
89. What are route reflectors in BGP?
In BGP, a route reflector (RR) is a router that allows for efficient distribution of BGP routes within an autonomous system (AS). Normally, BGP requires a full mesh of iBGP peers, meaning each router must maintain a session with every other router, which can be impractical in large networks. A route reflector reduces this requirement by allowing one router to "reflect" routes to its clients, thus reducing the number of BGP connections needed and simplifying management.
90. Explain how a distributed denial-of-service (DDoS) attack works and how to mitigate it.
A DDoS (Distributed Denial-of-Service) attack involves overwhelming a target server, network, or service with a massive volume of traffic, making it unavailable to legitimate users. The attack is launched from multiple compromised devices (botnets) that simultaneously flood the target, causing resource exhaustion or bandwidth congestion.
Mitigation strategies:
- Traffic filtering: Identify and block malicious traffic based on known signatures or IP addresses.
- Rate limiting: Limit the number of requests a server can handle from a single IP in a set period.
- DDoS protection services: Use services like Cloudflare or Akamai that can absorb and deflect the attack.
- Load balancing: Distribute incoming traffic across multiple servers to prevent a single point of failure.
- Anycast routing: Spread incoming traffic to multiple geographically distributed servers to prevent overload.
91. What are overlay networks?
An overlay network is a virtual network built on top of an existing physical network infrastructure. It allows devices in the virtual network to communicate as if they are directly connected, regardless of the underlying physical topology. Overlay networks abstract the complexity of the physical network and allow more flexibility in managing resources, traffic, and security policies.
Overlay networks are commonly used in scenarios like:
- Virtual Private Networks (VPNs): Enabling secure communication over public networks.
- Software-Defined Networking (SDN): Abstracting the physical layer to create programmable network topologies.
- Data centers: Facilitating communication across multiple locations or for load balancing.
92. What is VXLAN (Virtual Extensible LAN)?
VXLAN (Virtual Extensible LAN) is a tunneling protocol used to extend Layer 2 networks over Layer 3 infrastructure. It solves the scalability issues of traditional VLANs by using a 24-bit segment ID, allowing for up to 16 million isolated network segments (versus the 4,096 limit in traditional VLANs). VXLAN encapsulates Layer 2 frames within Layer 3 packets, enabling the creation of virtualized networks across data centers.
VXLAN is crucial for modern cloud and data center environments because:
- It supports virtual machine mobility (VLANs have limitations on scalability).
- It works across IP networks, allowing Layer 2 traffic to traverse Layer 3 networks seamlessly.
93. Explain the concept of network automation.
Network automation refers to using software and scripts to automate the configuration, management, testing, deployment, and operation of physical and virtual network devices. Automation reduces manual intervention, speeds up network operations, and decreases the chance of human errors.
Common use cases include:
- Automating device configurations across large networks.
- Provisioning services quickly in response to demand.
- Monitoring and troubleshooting network performance with minimal manual input.
Tools like Ansible, Puppet, and Cisco’s DNA Center enable network administrators to automate repetitive tasks, making networks more scalable and adaptive.
94. What is OpenFlow in SDN?
OpenFlow is a communication protocol that enables the SDN controller to interact with network devices (like switches and routers) in a software-defined network. OpenFlow separates the control plane (where decisions are made) from the data plane (where traffic forwarding occurs), enabling centralized management of network traffic.
How it works:
- OpenFlow defines flow tables on switches.
- The SDN controller dynamically programs flow entries based on traffic patterns.
- The switches then forward packets based on these flow entries, allowing for greater flexibility and programmability in traffic management.
OpenFlow enables dynamic control over network traffic, making SDN efficient for dynamic and large-scale networks.
95. How does a zero-trust security model apply to networking?
The zero-trust security model operates under the principle that no user or device, whether inside or outside the network, should be trusted by default. Instead, every access request must be authenticated, authorized, and continuously validated before granting access.
In networking, zero-trust involves:
- Segmenting networks: Minimizing the lateral movement of threats by enforcing strict access controls at every layer.
- Multi-factor authentication (MFA): Verifying user identities rigorously.
- Continuous monitoring: Observing network traffic and user behavior to detect anomalies.
Zero-trust networking ensures that even if an attacker breaches the perimeter, they will be met with multiple layers of security, reducing the potential impact.
96. What are route dampening and its use in BGP?
Route dampening is a mechanism in BGP (Border Gateway Protocol) used to reduce the propagation of unstable routes (flapping routes). Flapping occurs when a route continually goes up and down, causing excessive churn and instability in BGP routing tables.
Route dampening works by assigning a penalty score to routes that flap. When the penalty score exceeds a predefined threshold, the route is "suppressed" and not advertised to other routers. After the route stabilizes and the penalty decays below a certain level, it is re-advertised.
Route dampening helps:
- Stabilize large networks by reducing unnecessary route updates.
- Minimize the impact of unreliable routes on the overall network.
97. Explain how BGP convergence works.
BGP convergence is the process where all BGP routers in a network have consistent and stable routing tables after a change occurs (e.g., a link failure or route addition). When a topology change happens, BGP routers exchange updated route information to compute the best path to reach each destination.
Steps in BGP convergence:
- Route changes: A topology change triggers BGP updates.
- Route propagation: BGP routers exchange these updates with their peers.
- Best path selection: Routers select the best route based on BGP attributes like AS_PATH and MED.
- Routing table updates: Once all routers agree on the best paths, convergence is complete.
BGP convergence can be slow, especially in large networks, but optimizations like route reflectors and confederations can speed it up.
98. What is EVPN (Ethernet VPN)?
EVPN (Ethernet Virtual Private Network) is a modern, scalable VPN technology that extends Layer 2 Ethernet services across a Layer 3 network, allowing for multi-site Layer 2 connectivity. EVPN is used primarily in data centers and service provider networks to support multi-tenant environments.
Key features:
- MAC address learning via BGP, providing more scalability and reducing flooding.
- Support for Layer 2 and Layer 3 VPNs over MPLS or VXLAN.
- Seamless VM mobility, making it ideal for data centers with high virtual machine migration requirements.
99. How does VPC (Virtual Private Cloud) work in cloud networking?
A VPC (Virtual Private Cloud) is a logically isolated section of a public cloud (like AWS, Azure, or GCP) where users can launch cloud resources in a virtual network they control. VPC allows users to define their own subnets, routing tables, security policies, and VPNs to connect securely with their on-premises network.
VPC features include:
- Subnetting: Users can create isolated or shared subnets for different workloads.
- Security groups: To control inbound and outbound traffic for cloud instances.
- VPN gateways: To securely connect the VPC to an on-premises network.
VPCs offer a flexible, secure environment for hosting applications in the cloud while maintaining control over networking configurations.
100. What are Service Function Chaining (SFC) and its application in SDN?
Service Function Chaining (SFC) is the process of creating a logical sequence (or "chain") of network services (such as firewalls, load balancers, or deep packet inspection) that traffic must pass through before reaching its destination. In SDN, this can be implemented programmatically, making it easier to customize and manage network services based on application needs.
Applications of SFC in SDN:
- Security: Directing traffic through a firewall and an IDS before routing it to its final destination.
- Traffic optimization: Sending traffic through load balancers or WAN optimizers to enhance performance.
- Network flexibility: Reconfiguring service chains dynamically based on network conditions or specific application requirements.
SFC is essential for modern, cloud-native architectures where traffic flows need dynamic control and adaptability across different service components.
Conclusion
Preparing for networking interview questions requires a solid understanding of both foundational concepts and advanced networking technologies. By mastering topics such as the OSI model, IP addressing, routing protocols, and modern innovations like SDN and network automation, you can approach interviews with confidence. The key is to stay updated with industry trends and continue building hands-on experience. Whether you're tackling basic or advanced questions, a clear grasp of networking principles will position you for success in your interview journey.
You might be interested in reading the following:
I’m a Computer Science graduate with a knack for creative ventures. Through content at Unstop, I am trying to simplify complex tech concepts and make them fun. When I’m not decoding tech jargon, you’ll find me indulging in great food and then burning it out at the gym.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter
Blogs you need to hog!

How To Write Finance Cover Letter For Morgan Stanley (+Free Sample!)

55+ Data Structure Interview Questions For 2026 (Detailed Answers)

How To Negotiate Salary With HR: Tips And Insider Advice










Comments
Add comment