- What is the difference between hashing and encryption?
- Hashing vs Encryption: Similarities
- What is Hashing?
- What is Encryption?
- Frequently Asked Questions (FAQs)
Difference Between Hashing And Encryption Decoded
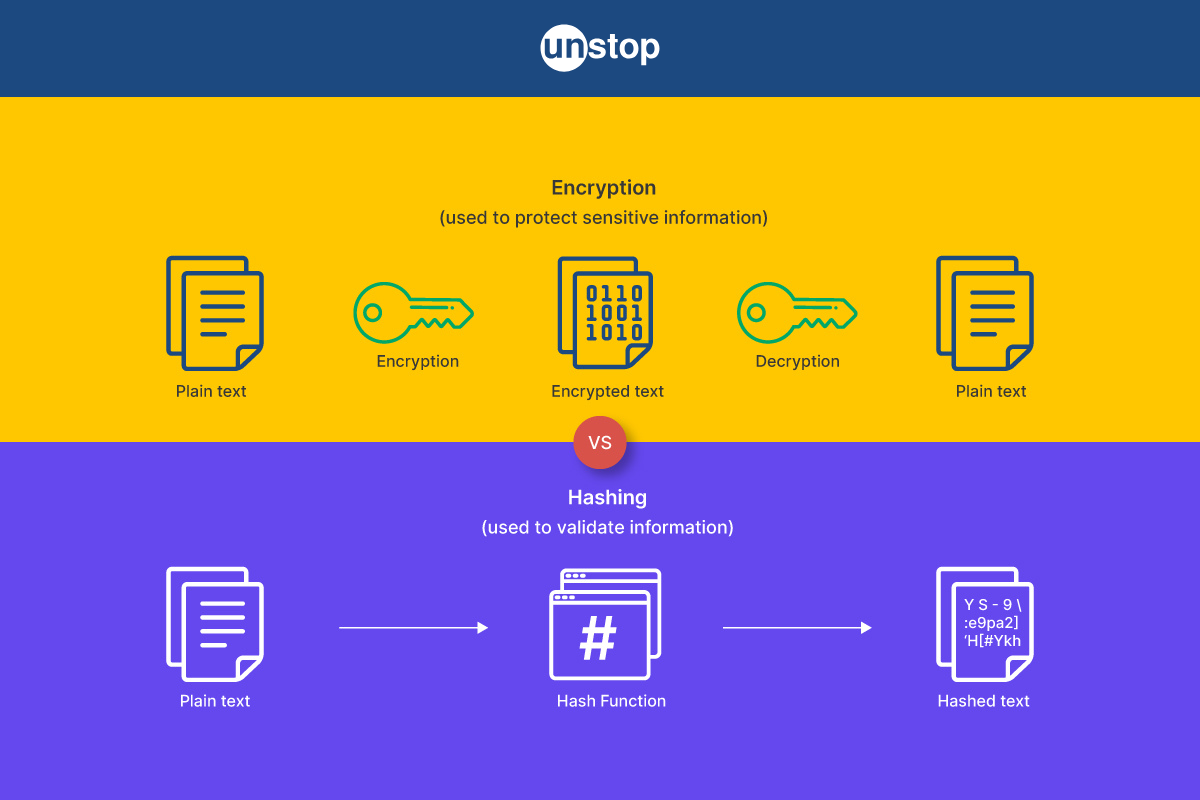
The terms hashing and encryption are commonly used in the world of data security. The main purpose of these techniques is to change the raw data into a different format to secure information. However, there is a substantial difference between hashing and encryption.
Hashing is done using a hash function and its objective is to ensure data or file integrity. On the other hand, encryption uses keys to make sure of data confidentiality. Read ahead to find the major differences between hashing and encryption, their similarities as well as their types and characteristics.
What is the difference between hashing and encryption?
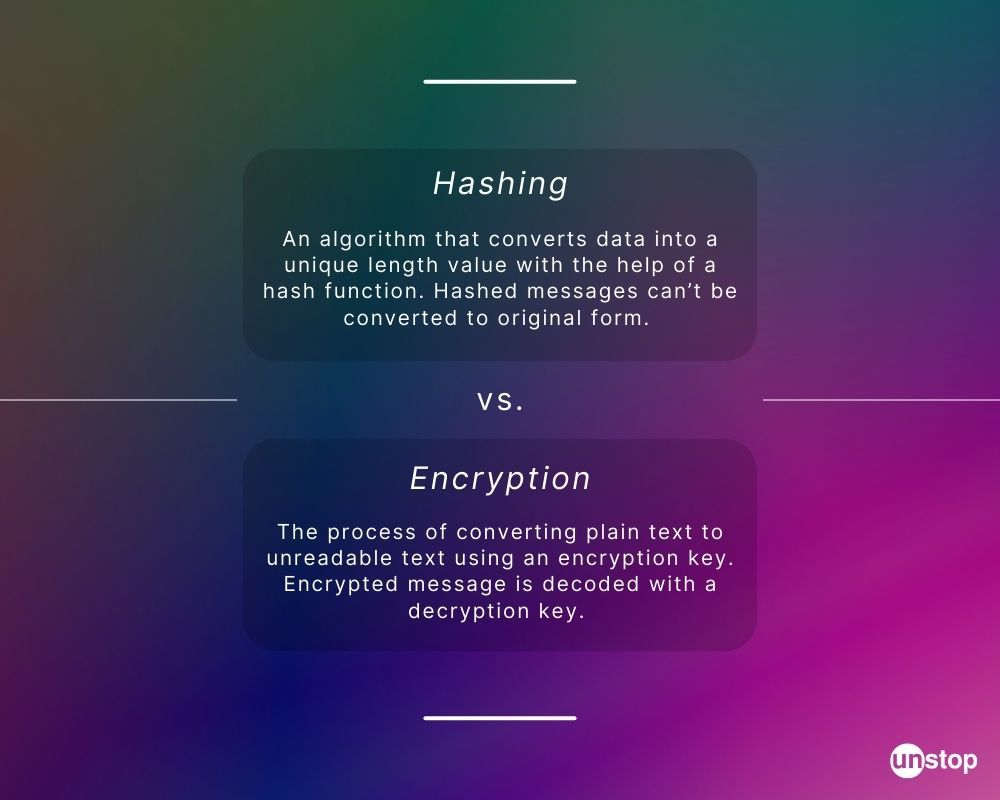
Hashing and encryption are both cryptographic techniques used to secure data, but they serve different purposes and have distinct characteristics. The major differences between hashing and encryption can be summarized as follows
Hashing vs Encryption
| Criteria | Hashing | Encryption |
| Reversibility | It is a one-way function i.e. original message cannot be retrieved back. | It is a two-way function i.e. original message can be obtained back by the decryption process. |
| Purpose | The purpose of hashing is data integrity. | The purpose of encryption is data confidentiality. |
| Output length | Fixed-length output is produced, regardless of the size of the input data. | Typically, the output produced is the same length as the input data. |
| Types | Types of Hashing Algorithms - MD5, RIPEMD, SHA, etc. | Types of Encryption Algorithms- RSA, AES (Advanced Encryption Standard), IDEA, Twofish, etc. |
| Applications | Applications include digital signature, storage of personal information such as bank details, etc. | Applications include messaging platforms, data exchange between servers, etc. |
Thus, the key difference between hashing and encryption is that hash codes cannot be decrypted to obtain the original text or file, whereas the encryption process can be decrypted.
Let’s study the difference between hashing and encryption in detail:
-
Purpose: The primary purpose of hashing is data integrity and verification. It takes input data and produces a fixed-size output called a hash value or hash code. In contrast, encryption is used to protect the confidentiality of data by transforming it into an unreadable format.
-
Reversibility: Hashing is a one-way process, meaning that it is not possible to retrieve the original input data from the hash value. It is designed to be irreversible to ensure data integrity. On the other hand, encryption is a reversible process, allowing the encrypted data to be decrypted back to its original form using a decryption key.
-
Length of Output: Hash functions produce a fixed-length output, regardless of the size of the input data. For example, the SHA-256 hash function always produces a 256-bit hash value. In contrast, encryption algorithms typically produce an output that is the same length as the input data. For instance, encrypting a 1 KB file would result in an encrypted file of approximately 1 KB.
-
Collision Possibility: Hash functions can have collisions, which occur when different input data produces the same hash value. However, a good hash function minimizes the chances of collisions. Encryption algorithms, on the other hand, aim to avoid collisions altogether, as it would compromise the security of the encrypted data.
Note: Collision in computer science is when two pieces of data in a hash table share the same hash value. So, the same slot might be allocated to 2 different keys.
Examples:
-
Hashing: The MD5 hash function is commonly used to verify the integrity of files. For example, when downloading a large file, the MD5 hash value provided by the source can be compared with the calculated MD5 hash value of the downloaded file to ensure that it has not been tampered with during transmission.
-
Encryption: The Advanced Encryption Standard (AES) is widely used to encrypt sensitive data, such as passwords or credit card information. For example, when transmitting credit card information over the internet, the data can be encrypted using AES before being sent. The recipient, who possesses the decryption key, can then decrypt the data and retrieve the original credit card information. This ensures that the sensitive information remains confidential and secure during transmission.
Let’s understand more about hashing and encryption and know how they are different from each other, as well as the similarities between the two.
Hashing vs Encryption: Similarities
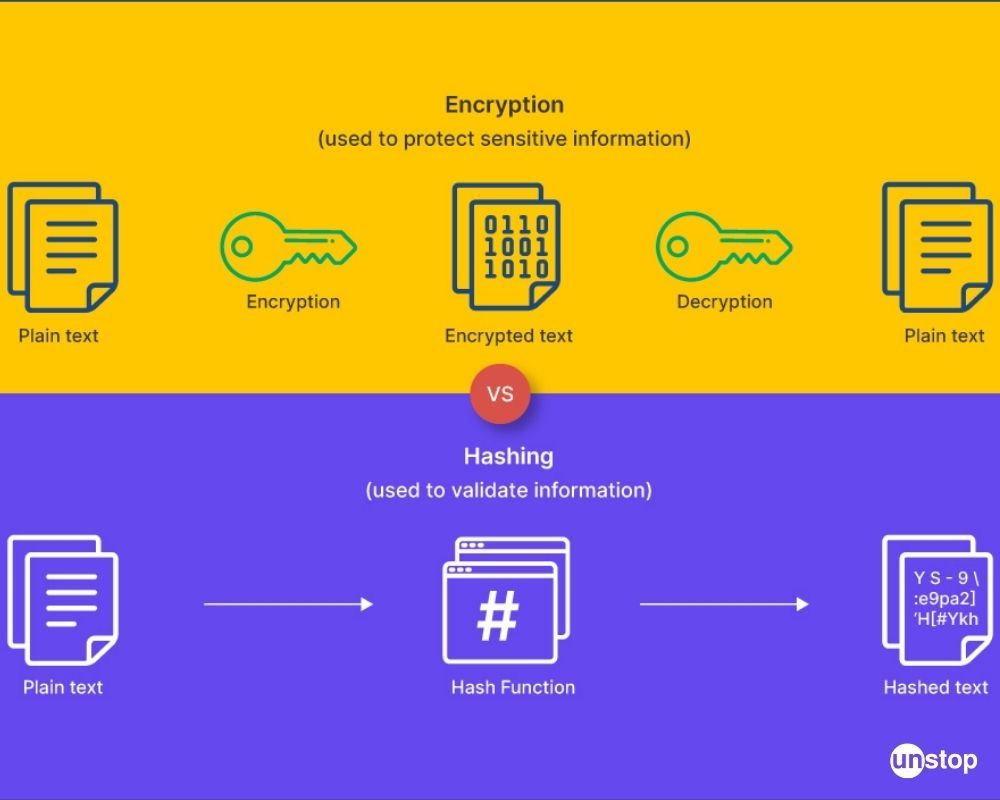
The difference between hashing and encryption is clear but since both are cryptographic techniques commonly used to protect data, there are some similarities between them as well.
Here are three key similarities between hashing and encryption:
-
Using algorithms to transform data
-
Difficult to reverse hashed or encrypted data
-
Both provide assurance that data can’t be altered
Let’s study the similarities between hashing and encryption in detail:
The first similarity between hashing and encryption is that both techniques involve the use of algorithms to transform data. In hashing, a specific algorithm is applied to a piece of data to generate a unique fixed-length string of characters, known as a hash value. Similarly, in encryption, an algorithm is used to transform plaintext data into ciphertext, making it unreadable to unauthorized parties.
Another similarity is that once data is hashed or encrypted, it cannot be easily reversed or decrypted without the corresponding key or hash function. In the case of hashing, it is computationally infeasible to reconstruct the original data from its hash value. Similarly, encryption ensures that only authorized parties with the correct decryption key can access the original plaintext from the ciphertext.
Furthermore, both hashing and encryption provide a level of data integrity and authentication. In hashing, the generated hash value acts as a unique identifier for the original data. Even a small change in the input data will result in a significantly different hash value. This property allows for the detection of data tampering or corruption. Encryption, on the other hand, ensures that the data remains confidential and cannot be modified without the decryption key. This provides assurance that the data has not been altered during transmission or storage.
What is Hashing?
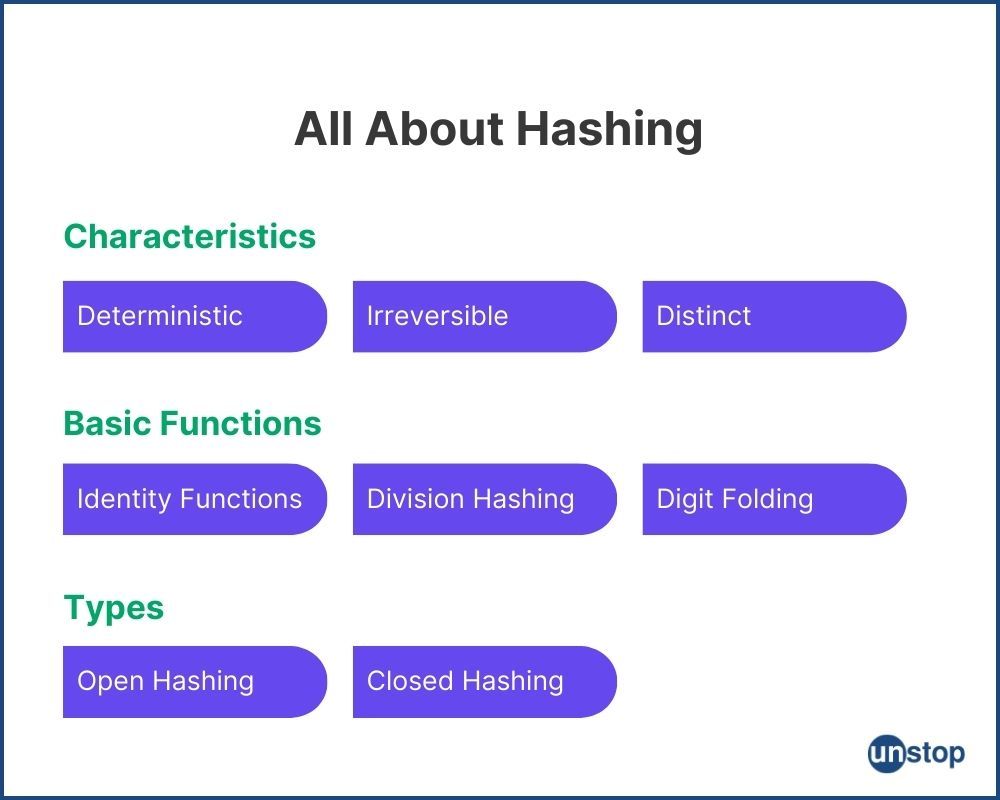
Hashing is an algorithm that takes in any size of data and converts it into a unique length value with the help of a hash function. In simple words, hashing is the use of a formula on data that results in what is called a hash. The hashes generated by the formula are always of the same length irrespective of the length of the data fed initially.
The hashing process is a one-way process, i.e., once hashing is done it cannot be converted back to the original input. Usually, the size of input strings is greater than the strings we get after using the hashing functions. We often use hashing in data structures and also in password verification.
It is interesting to note that hashing is an example of a space-time trade-off in computer science which is a case where a program trades an increased space or data storage with decreased time (time taken to do a specific given task).
Simplifying hashing through a real-life example: Let's assume you have taken up a stall in an exhibition and your sole purpose is to make money out of the things you have. And all you have is water, lemon, sugar, tea powder, glasses, and a stove. You decide to make some drinks using these ingredients. You can make 4 drinks out of the 7 ingredients you have - lemonade, black tea, lemon tea, and sugar water.
So now, your ingredients are your input, the procedure to make the drinks is hashing and the final output is the hashed value or the string.
Characteristics of a good hash function
-
Deterministic: A good hash function is always deterministic. Taking the help of the above example, if you add the same inputs (sugar+water) your output should be the same (sugar water).
-
Distinct: It should produce distinctive hash outputs for similar inputs. The only difference between lemonade and sugar water is lemons but still, they form 2 different dishes.
-
Irreversible: Hash digest (or Hashed output) cannot be reversed to the original strings (input). Just like how it is not possible to get back the lemons from the lemonade, it is not possible to reverse engineer any hash values.
Basic hash functions
1. Identity Hash Function: This is used when the data is small (like integer values). The key itself is the hashed value. The cost of computing the hash value is effectively zero as the value itself is the hash value and there is no computation. There are no collisions as every key is distinct and so is the hash value.
2. Division Hashing: In this hashing algorithm, we map the key into one of the slots by dividing the remainder of the key by the table size. This is written as h(k) = k mod m, in mathematical logic where m is a number that allows it to generate distinctive hash values. The table size is usually a power of two, resulting in a distribution ranging from 0 to m-1. There are chances of collisions.
3. Digit Folding: In this method, the number is split into several parts, and all parts are added up to get a new number. This method can give rise to fewer collisions, as the sum is mostly different.
Types of Hashing
Hashing can be divided into the following two types:
1. Open Hashing (Chaining): Data is not stored in Hashtable's hash key but another data structure is used i.e. linked list. If 2 or more hash codes point to the same index in a hash table, data is stored in linear form.
2. Closed Hashing: This is another technique in which there is no additional data structure. When a collision occurs the newly added hashcode is stored in the next possible empty cell. We can find the next possible cell in 3 different ways - Linear probing, Quadratic Probing, and Double Hashing.
What is Encryption?
Encryption is a process of converting plain text (Original text) to unreadable (gibberish) text, also called ciphertext, using an encryption key. The encryption key can be decoded later using a decryption key.
The objective of encryption is to protect the data from unauthorized parties. It is the most advanced method to ensure data security in modern communication systems.
Types of Encryption
There are two different types of encryption which are as follows:
1. Symmetric Encryption Algorithm: It is as simple as having 2 keys for one lock and only the people who have access to that key can open it. In symmetric encryption, we have one security key that both sender and receiver have and that key is used to encrypt and decrypt the message. Hence, it is called a public key. The sender encrypts the message using the public key and the receiver uses the same public key to decrypt the message.
2. Asymmetric Encryption Algorithm: Unlike symmetric encryption, here we have 2 different keys - Public key and Private Key. A public key is available for everyone and is used to encrypt the message whereas a Private key is available only at the receiver's end and is used for decrypting the message. It is slower compared to symmetric encryption and requires more processing power for computation as there is an extra key.
To sum up, both hashing and encryption have their own applications and methodologies. With the increase in the need for cybersecurity, more hashing and encryption algorithms are being created to protect data. In case of any data theft or leak, hashing and encryption help to secure critical as no one can understand the text and it is not easy to break it either.
Hashing vs Encryption: Frequently Asked Questions (FAQs)
1. What is hashing?
Hashing is a process used to transform data into a fixed-size string of characters, known as a hash value or hash code. It is commonly used in computer science and cryptography to verify data integrity and quickly retrieve data from large databases.
2. What is encryption?
Encryption is a method of converting data into a form that is unreadable to unauthorized individuals. It is used to protect sensitive information and ensure its confidentiality. Encryption algorithms use keys to encrypt and decrypt data, making it secure during transmission or storage.
3. What is the main difference between hashing and encryption?
The main difference between hashing and encryption is their purpose and functionality. Hashing is a one-way process, meaning that it cannot be reversed to obtain the original data. It is primarily used for data integrity checks and password storage. Encryption, on the other hand, is a two-way process that can be reversed using the appropriate key. It is used to protect data confidentiality.
4. Can hashed data be decrypted?
No, hashed data cannot be decrypted. Hashing is a one-way process, which means that the original data cannot be obtained from the hash value. It is designed to be irreversible, making it suitable for storing passwords and verifying data integrity.
5. Can encrypted data be decrypted?
Yes, encrypted data can be decrypted using the appropriate decryption key. Encryption algorithms use keys to transform the data into an unreadable form, and the same key is used to reverse the process and obtain the original data. Without the correct key, it is extremely difficult to decrypt the data.
6. Which one is more secure, hashing or encryption?
Both hashing and encryption serve different purposes and provide different levels of security. Hashing is primarily used for data integrity checks and password storage, while encryption is used for data confidentiality. In terms of security, encryption is generally considered more secure as it can be reversed with the correct key, whereas hashing is designed to be irreversible.
7. Can hashing and encryption be used together?
Yes, hashing and encryption can be used together. In fact, it is common to use both hashing and encryption in combination to enhance data security. This approach is often referred to as "hashing with salt" or "salted hashing."
In this process, the data is first hashed using a secure hashing algorithm. The resulting hash value is then encrypted using an encryption algorithm and a unique encryption key. This adds an extra layer of security to the hashed data, making it even more difficult for unauthorized individuals to access or manipulate.
Hashing provides a way to verify the integrity of the data, while encryption protects the data from unauthorized access. This dual approach is especially important when dealing with sensitive information, such as passwords or financial data.
Understanding the similarities and differences between hashing and encryption is essential for implementing effective data protection strategies.
You might also be interested in reading:
As a biotechnologist-turned-writer, I love turning complex ideas into meaningful stories that inform and inspire. Outside of writing, I enjoy cooking, reading, and travelling, each giving me fresh perspectives and inspiration for my work.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter
Blogs you need to hog!

This Is My First Hackathon, How Should I Prepare? (Tips & Hackathon Questions Inside)

10 Best C++ IDEs That Developers Mention The Most!

Advantages and Disadvantages of Cloud Computing That You Should Know!










Comments
Add comment