- Basic UNIX interview questions and answers
- Intermediate UNIX interview questions and answers
- Advanced UNIX interview questions and answers
100 Of The Most Asked UNIX Interview Questions And Answers
UNIX is a computer operating system that was initially developed in 1969 and has been continuously updated since then. It's a multi-user, multi-tasking system that's suitable for servers, desktops, and laptops. UNIX systems include a graphical user interface (GUI) comparable to Microsoft Windows that makes it simple to use.
However, knowledge of UNIX is essential for activities that are not covered by graphical software or when a Windows interface is not accessible, such as in a telnet session. On the market, there are several Unix variations. A few examples are Solaris Unix, AIX, HP Unix, and BSD. Linux is a free version of Unix.
If you are planning to sit for a UNIX interview, you must have a thorough knowledge of the entire concept as your interviewer will test your technical expertise. We have created a list of handpicked UNIX interview questions and answers that will increase your chances of getting hired by your dream company.
Basic UNIX interview questions and answers
1. What do you mean by UNIX?
It's a lightweight operating system that's optimized for multitasking and multi-user functionality. Because of its mobility, it can operate on a variety of hardware systems. It was created in C and allows users to manipulate and process data from within a shell.
2. Explain kernel.
The kernel is the main software that manages the computer's resources. This component is in charge of allocating resources to various users and tasks. When a user logs in to the system, the kernel does not interface directly with the user; instead, it launches a separate interactive program termed shell for each user.
3. What is the definition of a single-user system?
Single-user systems have an operating system that can only serve one user at a time. A single-user system is a computer with an operating system that can only be used by one person at a time. Because of the low cost of hardware and the availability of a large selection of software to accomplish various functions, single user systems are becoming increasingly popular.
4. What do you mean by shell?
A shell is software that allows you to access the Unix operating system. It gathers information from you and executes programs based on that information. Once a program has completed its execution, the output is shown. Shell is a command-line interface that lets us run commands, programs, and shell scripts from the command line. Shells are available in a range of flavors, similar to how operating systems are available in a variety of flavors. Common shells have a collection of well-known commands and features.
5. What are a shell’s responsibilities?
A shell's responsibilities are as follows:
- Execution of the Program
- Redirection of input and output
- Variable substitution and filename
- Connection to a pipeline
- Controlling the environment
- Integrated programming language
6. When sending commands in the shell, what is the common syntax used?
The following is a typical command syntax in the UNIX shell:
Command [-argument] [-argument] [–argument] [file]
7. Describe a UNIX link.
The term "link" is used to refer to a file that has more than one name. It's similar to a file pointer, except that one file might have several pointers. There are two sorts of links: internal and external.
Hard link- These hard-linked files have the same node value as the original and hence relate to the same physical file location. The link will also function if the file is relocated to a different directory.
ln [name of the original file] [name of the link]
Soft link- A soft link is similar to a file shortcut, except it has a different node than the original. If the original file is relocated, the link may not operate, but it can still refer to other files.
ln -s [original filename] [link name]
8. What does the term directory mean in UNIX?
A directory is a particular type of file that keeps track of all the files it contains. A directory is allotted to each file. Both ordinary and special files and folders are stored in this file type.
9. What are the shell types in UNIX?
Shells are divided into two categories in Unix:
- Bourne Shell - The $ character is the default prompt if you're using a Bourne shell.
- C-Shell - If you're using a C-shell, the % character serves as the default prompt.
10. Describe the Bourne Shell and C-Shell categories.
The Bourne Shell and C Shell (csh) are two of the most well-known Unix shells, each with its own set of categories for Unix commands and utilities. These categories aid in the organization and classification of the numerous commands and programs accessible in the Unix ecosystem.
The different subcategories are:
- Bourne Shell:
- Bourne shell (sh)
- Korn shell (ksh)
- Bourne Again shell (bash)
- POSIX shell (sh)
- C-shell:
- C shell (csh)
- TENEX/TOPS C shell (tcsh)
11. Explain the fork() system call.
The command fork used to generate a new process from an existing one is called fork(). The parent process is the primary process, while the child process is the new process id. The child process id is given to the parent process, while the child is given 0. The values returned are used to verify the process and the code that was performed.
The fork() system call takes no arguments and returns an integer. 0 signifies that the child process is created successfully, and it refers to the child process within the parent process.–1 means that the system failed to create another process.
12. What is command substitution and how does it work?
Every time instructions are handled by the shell, one of the steps is command substitution. Only instructions placed in backquotes are executed by the shell. This will then take the place of the command's usual output and be shown on the command line.
13. What do the commands chmod, chown, and chgrp do?
These are commands for managing files. These are utilized for the following purposes:
-
chmod - This command modifies a file's permissions.
It modifies a user group's ability to write.$ chmod g+w textfile -
chown - This command changes the file's ownership.
$ chown scoy3421 textfileIt makes scoy3421 the owner of textfile.
-
chgrp - The group of the file is changed using this command.
$ chgrp moderators textfileIt elevates a set of text files to the status of moderators.
14. What precisely is a daemon?
A daemon is a job or process that runs in the background and is responsible for a certain task or group of activities. This is a key idea in the Unix operating system. Memory management, file system administration, printer jobs, network connections, and a variety of other services are all handled by the Unix kernel's system daemons.
15. What is the Unix process model?
A priority-based preemptive round-robin scheduling technique is used to schedule processes. There will be no CPU starvation or saturation as a result of this. Processes can be preempted from the run queue and shifted to the sleep queue based on the completion of the time slice or wait by any I/O. Because we may encounter stalemate on any resource when scheduling, user applications must offer deadlock detection to guarantee that user processes do not become stuck.
16. What is the procedure for modifying file access permissions?
When adding or updating file access permissions, there are three sections to consider:
- File owner’s user ID
- File owner’s group ID
- File access mode to define
The following is how these three pieces are organized:
(User permission) – (Group permission) – (other permission)
There are three forms of authorization:
- r - denotes permission to read.
- w - denotes permission to write.
- x - denotes permission to execute.
17. How much do you know about shell variables?
The shell features a few preset internal variables, as well as the ability to create new ones. Some of them are variables that affect the environment, while others affect the local environment. These can be accessed through a variety of methods. A variable's name can only contain letters (A-z), digits (0-9), or the underscore character (_).
NAME="Sachin Tendulkar" $ echo $NAME $ unset NAME
18. Compile a list of regularly used network commands in UNIX.
The following are some of the most widely used networking commands in Unix:
- telnet: This is used to log in from a remote location and communicate with another hostname.
- ping: This command is used to test the network connectivity.
- hostname: This contains the IP address as well as the domain name.
- nslookup: Performs a DNS lookup.
- xtraceroute: This is used to figure out how many hops and how long it takes to go to the network host.
- netstat: This command displays information about the system and ports, as well as routing tables and interface statistics.
- tcpdump: This command displays information on both incoming and outgoing network traffic.
19. What is an inode?
An inode is a file system entry that is generated on a part of the disc dedicated to the file system. The inode stores almost all of a file's information. It contains information such as the file's initial position on the disc, its size, when it was last used, when it was last altered, the file's read, write, and execute rights, who owns the file, and other details.
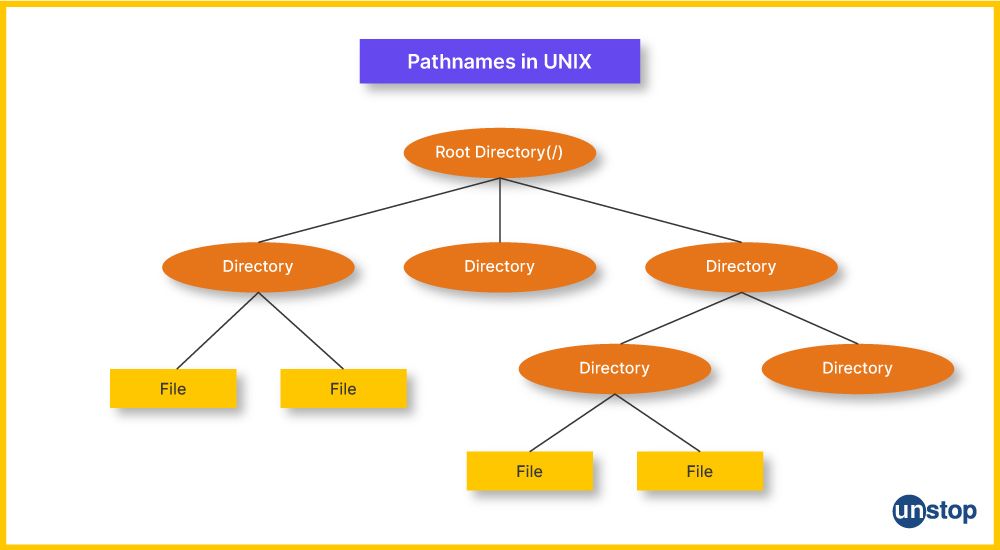
20. Explain the many types of pathnames and how to create them in UNIX.
A path is the unique location of a file or directory, as well as a mechanism to access it inside a directory hierarchy. In Unix, pathnames are divided into two categories:
- Absolute Pathname: The whole path from the beginning of the file system to the location of a file or directory (root directory).
/usr/local/Cellar/mysql/binis an example. - Relative Pathname: This is the path from the user's current working directory, i.e. the current working directory (pwd). The relative path for the bin is
./mysql/binif the current directory is/usr/local/Cellar.

21. Describe the functionality of the 'find' command in UNIX.
The 'find' command is used to search for files and directories within a specified directory hierarchy. It is often used with various options to locate and perform actions on files that match specific criteria.
22. How do you determine the process ID (PID) of a running process in UNIX?
You can use the 'ps' command to list running processes and their PIDs. For example: ps aux | grep processname.
23. What does the UNIX architecture look like?
The Unix architecture consists of the following main components:
-
Hardware Layer: The physical computer components.
-
Kernel: The core of the operating system, managing processes, memory, and devices.
-
Shell: The user interface for interacting with Unix, often through a command-line interface.
These components work together to enable the Unix operating system to function.
24. Explain the role of the 'history' command in UNIX.
The 'history' command displays a list of previously executed commands, allowing users to recall and re-run commands from their command history.
25. In which year was UNIX founded?
UNIX was founded in the year 1969 by Ken Thompson and Dennis Ritchie.
Intermediate UNIX interview questions and answers
26. In UNIX, explain Superblock.
A SuperBlock is software that stores information on a certain file system, such as the block size, the number of vacant and full blocks, the size of block groups, the disc block map, the size and placement of inode tables, and use statistics.
Superblocks are divided into two categories:
- Default Superblock: The default superblock is a predetermined offset from the system's disc partition's start.
- Redundant Superblock: Multiple copies of a default superblock exist and are accessed when the default superblock is impacted by a system crash or problems.
27. Enlist some of the certain UNIX file manipulation commands.
Here are a few commands for manipulating files:
- cat filename - This shows the contents of the specified file.
- cp source destination - This command copies the source file to the destination folder.
- mv old_name new_name - Rename/move files.
- rm filename - Deletes/removes a file.
- touch filename - time of creation/modification.
- In [-s] old_name new_name - Generating a soft link on an old name.
- Is –F - Shows details about the file type.
- ls -ltr - This displays the list in long format, arranged by modification time from oldest to newest.
28. In terms of Unix commands, what are system calls and library functions?
- System calls: System calls are an interface to the kernel that allows user applications to ask the operating system to do activities on their behalf. The application software switches from user space to kernel space whenever a system call is made within the operating system. These aren't easily transportable.
- Library functions: Library functions are non-kernel functions that are utilized by various application programs. It takes less time to execute than a system call, is portable, and can only conduct specified activities in “kernel mode”.
29. What is meant by virtual memory?
Virtual Memory is a method or system for accessing more memory than is physically available. The model is made up of a series of memory pages, each of which is typically 4 KB in size. Between virtual memory addresses and physical memory addresses, there is a translation layer. This translation layer is part of the kernel, and it's commonly written in machine language (Assembly) to get the best results when translating and mapping addresses. The kernel employs the address translation layer to transform the virtual memory address into a physical memory address whenever a user process accesses memory. Virtual Addressing allows you to address more memory than is physically available.
30. Distinguish between a relative and an absolute path.
The path relative to the present path is referred to as a relative path. On the other hand, an absolute path refers to the exact path as referenced from the root directory (the first directory is called the root directory).
| Relative Path | Absolute Path |
|---|---|
| A relative path specifies a location based on the current working directory. | An absolute path specifies a location from the root directory of the file system. |
| It is relative to the current working directory. | It starts from the root directory (/) or another fixed location. |
If the current directory is /home/user/docs/, a relative path to file.txt might be ../../data/file.txt. |
An absolute path to the same file would be /data/file.txt. |
Relative paths can use notations like . (current directory) and .. (parent directory). |
Absolute paths do not use . or .. because they start from a known fixed point. |
| Relative paths can be shorter, but they are context-dependent. | Absolute paths are longer but explicitly specify the location or exact path. |
| Often used when navigating within the same directory or to nearby directories. | Useful for accessing files or directories regardless of the current working directory. |
31. What's the difference between a UNIX command, a library function, and a system call?
A system call is an element of the kernel's programming. A library function is a program that isn't part of the kernel but is accessible to system users. UNIX commands, on the other hand, are standalone programs that can include both system calls and library functions.
32. What does the kill() system call do and what do the return values mean?
The kill() system function delivers signals to any running process, which then takes appropriate action in response to the signal. It accepts two arguments: the first is the PID of the device to which you want to send a signal, and the second is the signal you wish to send.
The following values are returned by this method:
- 0 - indicates that the process with the supplied PID exists and that the system enables signals to be sent to it.
- -1 and errno==ESRCH - indicates that the process/process group given by the PID does not exist.
- 1 and errno==EPERM - The sender does not have the authorization to transmit a signal to the destination process.
- EINVAL - indicates that an invalid signal has been supplied.
33. What exactly is UNIX's Zombie process? How is the Zombie procedure found by you?
Child processes that finish before the parent process is known as zombie processes. So, once the process is over, the process structure and address space are withdrawn from the system and freed up, but the process table entry remains. In the process table, one can easily locate the process ID of the same despite it remaining non-functional. The parent must call and wait, in order to obtain the status of the child's procedure (). The kid is considered to be a 'zombie' during the time between the child's termination and the parent's call to wait().
34. Explain how to boot a UNIX system.
There are five phases to it:
- Hardware - BIOS starts up and scans for a hardware connection.
- Operating System loader - The OS loader is found in the MBR, which is the first 512-byte block of the boot device.
- Kernel - It initializes different components of the computer, operating system, and each section of software responsible for a job, which is commonly considered a driver root user.
- root user-space process (init and inittab) - This specifies what should be done when the /sbin/init program is told to enter a certain run-level, making it simple for the administrator to set up a specific environment.
- Boot scripts - There is a single startup script for each managed service (mail, nfs server, cron, and so on) located in a specific directory.
35. Distinguish between the cmp and diff commands.
The cmp command is primarily used to compare two files byte by byte, with the first mismatch shown. The diff command, on the other hand, is used to identify the changes that need to be done to make the two files identical.
36. State the differences between Linux and Unix.
Differences between Linux and Unix are:
| Aspect | Linux | Unix |
|---|---|---|
| Origin & License | Open-source with GNU/GPL license | Mixed, both proprietary and open-source |
| Kernel | Linux kernel | Various Unix kernels |
| Package Management | APT, Yum, Pacman, etc. | Varies or none for some Unix systems |
| Hardware Support | Versatile hardware compatibility | Often tied to specific architectures |
| System Tools | User-friendly administration tools | May require more manual configuration |
| Community & Support | Active open-source community | Limited community for some Unix variants |
| Cost | Often free with optional support | Licensing fees for some Unix variants |
37. What are the I/O calls in the Unix System?
A system call is a method for applications to communicate with the operating system. For file management, process control, device administration, information management, and communication, Unix System calls are utilized.
The following are some of the most regularly used I/O System calls:
- open(pathname, flag, mode) - a command that opens a file.
- close(filedes) - closes a file that is currently open.
- create(pathname, mode) is a command that creates a file.
- write(filedes,buffer,bytes) - writes data to a currently open file.
- read(filedes, buffer, bytes) - read data from a file that is currently open.
- lseek(filedes, offset, from) - position an open file using.
- dup(filedes) - duplicates a file descriptor that already exists.
- dup2(oldfd, newfd) - replace the old file descriptor with the appropriate file descriptor.
- ioctl(filedes, request, arg) - Change the behavior of an open file.
- fcntl(filedes,cmd,arg) - Change the attributes of an open file.
38. In Unix, what exactly is a process?
A process is a set of instructions or a specific instance of a program that is running. Any application that is run generates a process. Processes can be manipulated in the same way that files may. Various qualities are connected with a process:
- PID stands for Process-ID.
- PPID stands for Parent Process ID.
- TTY (Teletypewriter) is the terminal with which the process is attached.
- UID refers to User Identification.
39. What method do you use to obtain the current date? Is it possible to change the way the date is printed?
The current date may be obtained by entering the 'date' command. If we want the format to be the day, month, date, year, and time, we'll use the following sequence:
set ‘date’
echo $4 $2 $5 $2 $6 $4
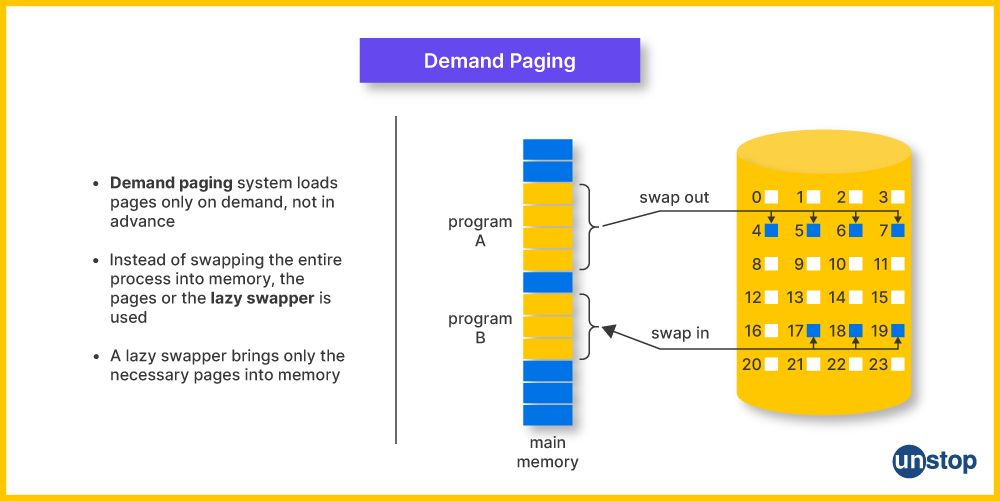
40. For Demand paging, what data structures are used?
In operating systems, demand paging is a memory management strategy used to optimize memory utilization and system performance. It enables programs to load data into memory only when needed rather than putting the complete program into memory all at once. This reduces memory waste and boosts overall system responsiveness.
Several data structures are used in demand paging to control the movement of pages between main memory (RAM) and secondary storage (often a hard disc). These data structures are:
- Page Table: Maps virtual memory addresses to physical memory locations.
- Page Table Entry (PTE): Contains information about each page, including its state and location.
- Page Frame Data Table: Tracks the state of page frames in physical memory.
- Backing Store or Swap Space: Secondary storage where pages are stored when not in memory.
- Swap Use Table: Monitors the usage of swap space to manage allocation and deallocation.
41. State the difference between shell & environment variables.
Environment variables are accessible to all processes in the current session and are often used for system-wide configuration. Shell variables are specific to the current shell session. The variables are lost when you quit the shell.
They are different in terms of scope and accessibility. Here are other differences between the two:
| Aspect | Shell Variables | Environment Variables |
|---|---|---|
| Scope | Local to session/script | Global, inherited |
| Inheritance | Not inherited | Inherited by children |
| Lifetime | While session/script | Beyond current session |
| Common Use | Temporary data/config | System-wide settings |
42. What exactly is swapping? Describe how a swapper operates.
Swapping is the process of moving a full process to the main memory to be performed. The capacity of the main memory must be more than the process size.
The swapper operates on a high-priority scheduling system. It looks for processes that are sleeping. If none are available, ready-to-run processes are used instead. To be swapped, the process must spend at least 2 seconds in the swapper. If no processes are available, the swapper enters a wait state and waits for the Kernel to call it (every second).
43. In UNIX, what are hidden files?
In UNIX, hidden files are those with a. (dot) before the file name. The standard file manager does not recognize these files.
The following are some instances of hidden files:
- .profile
- .kshrc
- .rhosts
- .cshrc
44. How to log out of UNIX?
To log out of UNIX type the logout command in the command prompt. Here's the command:
$ logout
45. How would you reverse a string in UNIX?
To reverse a string in Unix we use the rev command.
$> echo "String" | rev gnirtS
46. How do you define an array in UNIX Shell?
Following is the way to create an array in Shell:
NAME1="Vuitton" NAME2="Chanel" NAME3="Gucci" NAME4="Prada" NAME5="AlexanderMcQueen"
Declaring an array variable in Unix is as follows:
array_name[index]=value
The name of the array is array_name, the index of the item in the array that you want to set is the index, and the value is the value you want to set for that item is value.
47. How do you set up an environment in UNIX?
The shell goes through an initialization process when you log in to the system to set up the environment. This is normally a two-step procedure that begins with the shell reading the files listed below:
- /etc/profile
- profile
The steps are as follows:
The shell checks for the existence of the file /etc/profile.
The shell reads it if it exists. If not, this file will be skipped. There is no error message displayed.
The shell looks in your home directory to determine if the file .profile exists. Your home directory is the first directory you see when you log in.
The shell reads it if it exists; else, it skips it. There is no error message displayed.
When both of these files have been read, the shell shows a prompt: $
When this command shows, you can enter commands.
48. How can you send an email using UNIX?
An email can be sent using the following commands using the UNIX shell.
$mail [-s subject] [-c cc-addr] [-b bcc-addr] to-addr
49. Define piping in Unix.
You can chain two instructions together such that one program's output becomes the input for the next. A pipe is formed when two or more instructions are joined in this manner. To build a pipe, place a vertical bar (|) between two instructions on the command line.
50. What precisely are foreground and background processes in Unix?
Foreground Process:
Every one of the processes you launch by default runs in the forefront. It takes input from the keyboard and displays the results on the screen.
With the ls command, you can observe what's going on. You may use the following command to get a list of all the files in your current directory:
$ls ch*.doc
You can also use ls-lrta command to display hidden files in the current directory.
The process runs in the foreground, the output is sent to my screen, and the ls command waits for input from the keyboard if it needs it (which it doesn't).
Because the prompt will not be available until the program finishes processing and exits, no other commands can be performed (no other processes can be started) while it is running in the foreground.
Background Process:
Without being linked to your keyboard, a background process operates. It waits for any keyboard input if the background operation demands it.
You may run additional commands while a process is running in the background; you don't have to wait for it to finish before starting another!
Adding an ampersand (&) to the end of a command is the easiest method to start a background process.
$ls ch*.doc &
51. What is the definition of a shebang line?
In Unix-like operating systems, a shebang line, sometimes known as a "hashbang" or "pound-bang" line, is a specific comment at the beginning of a script or executable file. It is composed of the characters #! followed by the path to the interpreter to be used to execute the script or program.
For example, in a Python script, the shebang line might look like this:
#!/usr/bin/python3
52. What is the function of the telnet command?
The telnet command is used to establish a connection with a distant Unix/Linux computer.
53. What is the function of the book block?
It includes software called MBR (Master boot record) that loads the kernel on system booting.
54. Explain the significance of the '/etc/passwd' file in UNIX.
The '/etc/passwd' file stores user account information, including usernames, user IDs, group IDs, home directories, and shell information. It is essential for user authentication and system administration.
55. How do you change the ownership of a file in UNIX using the 'chown' command?
You can change the ownership of a file with the 'chown' command by specifying the new owner and, optionally, the new group.
For example: chown newuser:newgroup filename.
56. What is the 'ulimit' command in UNIX used for?
The 'ulimit' command is used to set or display user-level resource limits in UNIX. It allows controlling resource consumption, such as maximum file size, CPU time, and open file descriptors.
57. What is the 'umask' command in UNIX, and how is it used to set file permissions?
'umask' sets the default file permissions for newly created files. It subtracts the specified permission bits from the maximum permission value (usually 666 for files and 777 for directories) to determine the default permissions.
58. Explain the purpose of the 'script' command in UNIX.
The 'script' command is used to record the input and output of a terminal session into a file. It is often used for creating session logs and documenting terminal interactions.
Advanced UNIX interview questions and answers
59. Show how to create functions on Unix with an example.
Simply use the following syntax to declare a function:
func_name () { list of commands }
Your function's name is func_name, and you'll refer to it by that name throughout your scripts. After the function name, there must be a parenthesis, then a list of commands contained in braces.
For example:
#!/bin/sh # Define your function here Hello () { echo "Hello World from my Unix" } # Invoke your function
You will get the following output after running the command:
$ksh main.ksh Hello World from my Unix
60. What is the use of the tee command?
The tee command helps in two things. Firstly, it is used to get data from the standard input and send it to the standard output. Secondly, it redirects a copy of that input data into a file that was specified.
61. What is the 'nohup'?
"nohup" is a special command to run a process in the background even when a user logs off from the system.
62. What is the 'gzip' command used for?
The gzip command in Unix is used to compress files, reducing their size.
The basic usage is: gzip file
63. What are Symbolic links?
They are files that only contain the name of another file. The operations on the symbolic link get directed to the file pointed by it. The limitations of connections are eliminated in symbolic links.
64. How many types of job classes are provided by UNIX? Explain them all.
Unix-like operating systems do not have predefined "job classes." Instead, they offer mechanisms like foreground and background jobs, process states, job control, process priorities, and shell scripting, allowing users to manage and categorize tasks and processes based on their specific requirements and characteristics. Users have the flexibility to use these mechanisms to organize and control their jobs and processes effectively.
65. How do you delete a file?
To delete a file, you can use an 'rm command'. The syntax for the rm command is:
$ rm <filename>
You can also use -r with the rm command to delete all the sub-directories recursively.
66. What is a wild-card interpretation?
When a command line contains a wild-card character(s) such as ‘*’ or ‘?’, they are replaced by the shell with a sorted list of files whose patterns match the input command. Wild-card characters are used to set up a list of files for processing, instead of having it specified one at a time.
67. Describe the main features of UNIX.
The main features of UNIX are listed below:
-
-
Portability: UNIX applications and scripts can be easily transferred between UNIX systems, ensuring seamless integration.
- Machine Independence: UNIX is adaptable to different hardware types, ensuring flexibility and cross-platform compatibility.
-
Multi-User Support: UNIX facilitates concurrent use by multiple users, each with personalized settings and files.
-
Command Shells: UNIX provides a variety of command-line interfaces (shells) with scripting capabilities for user interactions.
-
Hierarchical File System: UNIX uses a tree-like structure for organizing files and directories, simplifying file management.
-
Pipes and Filters: UNIX allows the creation of efficient data processing pipelines through command chaining.
-
Background Processing: UNIX enables tasks to run in the background independently, freeing up the terminal for other activities.
-
Utilities: UNIX offers an extensive set of built-in tools and commands for tasks ranging from file management to system administration.
-
Development Tools: UNIX provides a comprehensive suite of development tools, including compilers, debuggers, and scripting languages, making it a preferred platform for software development.
-
68. What does Relative pathname signify?
Relative pathname signifies the current directory and parent directory. It also refers to files that are either inconvenient or impossible to access.
69. What's the purpose of the 'gunzip' command?
The gunzip command in Unix is used to decompress gzip-compressed files. It takes a compressed file (with a .gz extension) and restores it to its original, uncompressed state.
The basic usage is: gunzip file.gz
70. Which command is used to find the maximum memory-taking process on the server?
The top command is used to find the maximum memory-taking process on the server. It displays the CPU usage, process ID, and a few other details. The syntax for the command is sh-4.3$ top.
71. Why is it not advisable to use root as the default login?
One needs to keep in mind the concept of Privilege escalation. If any security vulnerability is exploited (for instance, your web browser), not running your programs as root will limit the damage. If your web browser is running as root, any security failures will have access to your entire system.
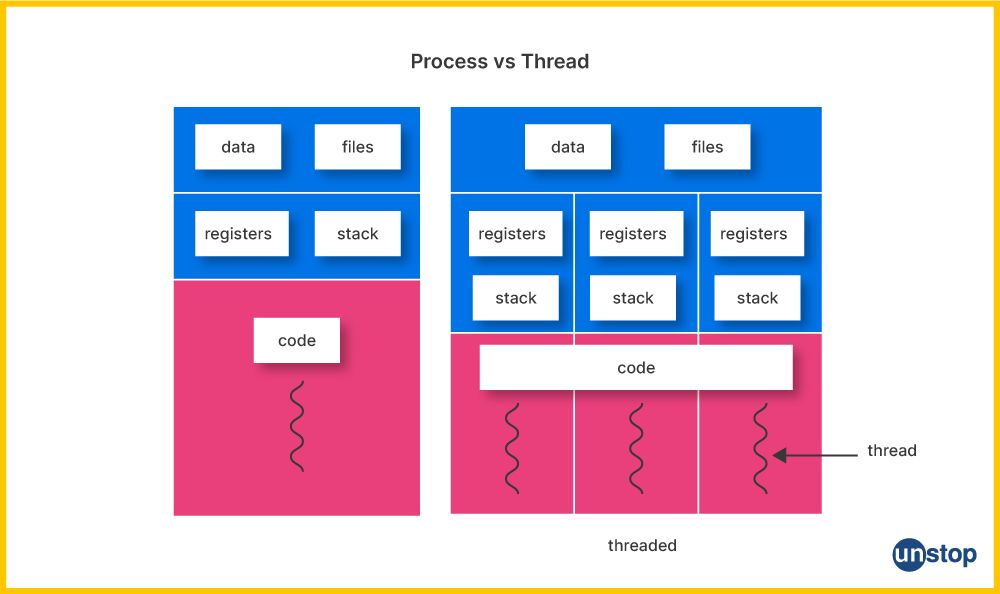
72. Explain the difference between a process and a thread in Unix.
In a nutshell:
- Process: Independent program with its own memory and resources.
- Thread: Lightweight unit within a process that shares the same memory and resources with other threads in that process.
73. What is the difference between swapping and paging?
| Criteria | Swapping | Paging |
|---|---|---|
| Fundamental Concept |
The complete process is moved to the main memory for execution. |
Processes are divided into fixed-sized pages, and only the necessary pages are loaded into main memory. |
| Process Size Limitation | Process size must be smaller than the available main memory. | Process size can be larger than the available main memory as only necessary pages are loaded. |
| Memory Utilization | May lead to inefficient memory use as entire processes are swapped. | More efficient use of memory, as only the required pages are loaded. |
| Granularity | Coarse-grained, dealing with entire processes. | Fine-grained, dealing with smaller, fixed-sized pages. |
| Flexibility | Less flexible in managing available memory. | More flexible and efficient in managing memory resources. |
| Number of Processes | Usually limited to one or a few processes in main memory. | Can accommodate multiple processes in main memory simultaneously. |
74. What is FIFO?
In Unix, FIFO stands for "First-In, First-Out." It's a named pipe that allows processes to communicate by reading and writing to a shared file-like resource in the sequence in which they were received. It is a unique file format that allows data to be shared between processes in the order it was written. If there is no data to read or the FIFO is full, the process will be blocked. Though it's a special file, it has the same permissions and ownership as ordinary files and is widely used for process communication.
75. What is the purpose of the 'cron' utility in UNIX?
The 'cron' utility is used for job scheduling and automation in UNIX. It allows users to schedule tasks and scripts to run at specified times or intervals.
76. Explain the concept of a Super User.
In Unix, the Super User, also known as "root," is the user with the most privileges who is in charge of important system administrative responsibilities. The root user has the ability to perform any operation on the system, but this power comes with the requirement to exercise prudence in order to avoid security concerns and system instability. To safeguard the root account and the broader system, security techniques such as restricted access and "sudo" are in place.
77. How can you create a symbolic link (symlink) in UNIX?
To create a symbolic link, you can use the 'ln' command with the '-s' option.
For example: ln -s sourcefile linkname.
This creates a symlink named 'linkname' that points to 'sourcefile.'
78. What is the purpose of the 'chroot' command in UNIX?
The 'chroot' command is used to change the root directory for a process, limiting the access of that process to a specific directory and its subdirectories. It is often used for security and isolation purposes.
79. Describe the role of the 'at' and 'batch' commands in UNIX.
The 'at' and 'batch' commands are used to schedule one-time tasks in UNIX. 'at' allows you to schedule a command to run at a specific time, while 'batch' schedules a task to run when the system load is low.
80. What are hard links and how do they differ from symbolic links?
Hard links are multiple directory entries (filenames) that point to the same inode, representing the same file on disk. They essentially create multiple directory entries for a single file. In contrast, symbolic links (symlinks) are separate files that point to another file or directory by its path. Hard links can only point to files on the same filesystem, while symlinks can point to files on different filesystems.
81. How do you change the permissions of a file in UNIX?
You can change file permissions with the 'chmod' command by specifying the desired permissions using symbolic or octal notation. For example, to give read and write permissions to the owner of a file: chmod u+rw filename. Octal notation can be used as well, like: chmod 644 filename for the same permissions.
82. What is the purpose of the 'grep' command in UNIX?
The 'grep' command is used for searching and matching patterns within text files. It is particularly useful for extracting lines or data that match specific criteria using regular expressions.
83. What's the default network stacking protocol for UNIX?
The Internet Protocol (IP) is often the default network stacking protocol in Unix-like operating systems. IP is a basic protocol that allows data to be sent over networks such as the Internet. It implements the addressing and routing mechanisms required for data packets to reach their destinations. Unix systems, such as Linux, rely significantly on IP for network communication. While IP is the most often used network protocol, Unix systems also offer a variety of other network protocols and services to meet a variety of networking requirements.
84. How do you archive and compress files in UNIX using the 'tar' and 'gzip' commands?
To archive files using 'tar': tar -cvf archive.tar files. To compress the archive using 'gzip': gzip archive.tar. To extract: tar -xvf archive.tar.gz.
85. What is the purpose of the 'awk' command in UNIX?
'awk' is a versatile text processing tool used for data manipulation, reporting, and extraction. It allows users to define patterns and actions to process structured data.
86. How do you set environment variables in UNIX, and what is their significance?
Environment variables are set using the 'export' command.
For example: export MY_VARIABLE=myvalue.
Environment variables store configuration information and are accessible to all processes in the current session.
87. How do you send signals to processes in UNIX using the 'kill' command?
The 'kill' command is used to send signals to processes. For example, to terminate a process, you can use kill <PID> or kill -9 <PID> to forcefully terminate it.
88. What is the purpose of the 'ifconfig' command in UNIX?
'ifconfig' is used to configure and display network interfaces, including assigning IP addresses, enabling or disabling network interfaces, and obtaining network-related information.
89. What is the alias mechanism?
The alias mechanism in Unix allows users to create custom shortcuts for frequently used or lengthy commands. The alias command is used to define these shortcuts. For example, you can create an alias like ll for ls -l, making it easier to run commonly used commands.
90. Explain the purpose of the 'ssh' command in UNIX.
The 'ssh' command is used to securely connect to remote systems over a network. It provides encrypted communication and authentication for secure access to remote servers.
91. How do you archive and compress files in UNIX using the 'zip' command?
To create a zip archive: zip archive.zip files.
To extract: unzip archive.zip.
92. What is the purpose of the 'tee' command in UNIX?
The 'tee' command is used to read from standard input and write to standard output and files simultaneously. It is often used to capture and view output while saving it to a file.
93. How can you check available disk space in UNIX using the 'df' command?
The 'df' command is used to display information about available disk space on filesystems. Running 'df' without options will list space usage on all mounted filesystems.
94. How can you view and manipulate the process table in UNIX using the 'ps' command?
The 'ps' command is used to list and manage running processes. You can display a list of processes using various options like 'ps aux,' and use options like 'kill' or 'nice' to manage processes.
95. What is the purpose of the 'lsof' command in UNIX?
The 'lsof' (list open files) command is used to display information about files and network connections opened by processes. It is useful for troubleshooting and identifying which processes have specific files or sockets open.
96. Explain the concept of 'stdin,' 'stdout,' and 'stderr' in UNIX.
'stdin' (standard input), 'stdout' (standard output), and 'stderr' (standard error) are the default data streams for processes. 'stdin' is where a process reads input, 'stdout' is where it writes normal output, and 'stderr' is where it writes error messages.
97. What is the 'chmod' command?
The chmod command in Unix is used to change file and directory permissions. It can be used to grant or restrict read, write, and execute permissions to users, groups, and others.
Basic usage: chmod [options] mode file
98. What is the CAT command?
The cat command in Unix is used to display the file contents. It's short for "concatenate" and is often used to view the contents of a single file.
For example: cat filename
99. What is the tar command?
The tar command in Unix is used to archive and compress files and directories into a single file. It stands for "tape archive" and is often used for creating backups or bundling multiple files together.
Basic usage:
tar [options] archive_file files/directories
100. What's the role of mount and unmount commands?
The "mount" command attaches file systems to the operating system, making them accessible, while the "umount" (or "unmount") command detaches or unmounts them, ensuring data integrity and safe removal.
Summing up...
Unix specialists are in high demand in the software technology area. Unix allows you to advance in your career by allowing you to pick from a range of job titles such as Unix Engineer, Administrator, Systems Engineer, and Analyst Engineer.
Make sure you practice these interview questions and answers so you're able to showcase your knowledge.
You might also be interested in reading:
- Difference Between Retesting And Regression Testing Explained (With Examples)
- Difference Between Scripting And Programming Language | Why Scripting Language Is Considered A Programming Language But Not Vice-Versa?
- Top 50+ Java Collections Interview Questions
- What Is Scalability Testing? How Do You Test Application Scalability?
I’m a reader first and a writer second, constantly diving into the world of content. If I’m not writing or reading, I like watching movies and dreaming of a life by the beach.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter
Blogs you need to hog!

This Is My First Hackathon, How Should I Prepare? (Tips & Hackathon Questions Inside)

10 Best C++ IDEs That Developers Mention The Most!

Advantages and Disadvantages of Cloud Computing That You Should Know!









Comments
Add comment