- Microservices Interview Questions: Basics
- Microservices Interview Questions And Answers: Intermediate To Advanced
- Spring/ Spring Boot Microservices Interview Questions
55+ Microservices Interview Questions That You Shouldn't Miss!

Microservices is an architectural and organizational model/ approach made up of small and autonomous services. The said services communicate over well-defined APIs and are used in software development. Microservices enable autonomous scaling of each service to match the demand for the application functionality it offers. In other words, microservices are a collection of functional modules that simplify the management of complex applications and replace monolithic architecture. Companies like Twitter, amazon, etc., have replaced monolithic architecture with microservices architecture. The microservices interview questions and answers listed in this will help you prepare for the job interview for such roles and make your dreams come true!
Microservices Interview Questions: Basics
Let's look at some interview questions that will test your basic and fundamental knowledge of microservices and their components.
Q1. What DBMS is suggested for use with microservices architectures?
There is no universally applicable solution to this problem because the selection of a database management system (DBMS) for a microservices architecture will be influenced by several use-case-specific factors, such as the type of data being stored, the size and complexity of the system, and the requirements for scalability, availability, and consistency. Some of the most frequently used DBMS voices for microservices architectures are:
- NoSQL databases
- Relational databases
- NewSQL databases
Q2. What exactly do you mean by 'REST' and 'microservices'?
REST, short for Representational State Transfer, is an architectural design for creating web services. It is a collection of guidelines, procedures, instructions, and protocols that specify how web services should connect online.
On the other hand, Microservices, the architectural approach arranges an application as a collection of little autonomous services based on a business domain. Every microservice implements a single business capability and is independent of one another.
Q3. What does a microservice accomplish for a monolithic application?
A monolithic application is divided into smaller, independently deployable services by using a microservice design, which increases the application's flexibility, scalability, and robustness. Microservices enable shorter development cycles and simpler application management because they may be created, tested, and deployed independently from one another.
Q4. What exactly is Idempotence and its use?
Idempotence in the context of microservices refers to a microservice's ability to provide the same output when given the same inputs. A microservice that is idempotent can handle duplicate requests accurately and avoid any unintended consequences. Idempotence is needed to make that the system responds appropriately in the case of network outages, retries, or other unforeseen circumstances. It is used for remote service.
The primary use of Idempotence is that it guarantees that each request will only be processed once, even when a remote service or information provider receives instructions more than once.
Q5. What is a contract, and how is it implemented?
Contracts are agreements that outline the anticipated input and output of the service between the microservice and its customers. Contracts typically include a schema that outlines the data types, formats, and protocols used for inter-microservice communication. They are necessary for microservices-based applications because they enable the autonomous deployment of microservices. Each microservice must give its customers, which are other microservices, a versioned, well-defined contract and must not violate these versioned contracts until it is clear that no other microservice relies on a specific, versioned contract.
Contract testing is a method for evaluating an integration point that involves examining each application separately to make sure that the messages it delivers or receives comply with the contract. By using this method, you can make sure that every microservice abides by the contract and that there is dependable and there is constant communication between them.
Q6. What does server-side discovery mean?
The client connects to the proxy layer or API Gateway layer in this method, which then directs the request to the relevant service. By separating the client and the services, server-side discovery addresses one of the major problems with client-side discovery. Through a router or load balancer, client applications can find services thanks to server-side service discovery.
Q7. Is the architecture of microservices monolithic? Explain in your own words.
No, the architecture of microservices is not monolithic.
In contrast, a microservices architecture is a group of smaller, independently deployable services. On the other hand, a monolithic architecture is constructed as a single integrated entity.
Q8. State the primary difference between REST and microservices.
REST, or Representational State Transfer, is a framework for creating APIs, and the APIs thus created/ that adhere to REST are referred to as REST API. In comparison to this, microservices are a design approach and architectural model for creating applications that are made up of tiny, autonomous services that communicate with one another via simple protocols like HTTP, and you can access client applications on HTTP.
Q9. What is the purpose of event sourcing?
Event sourcing is a pattern for storing data in an append-only log as a series of events. Event sourcing offers a full history of the data, enabling a full audit trail of data changes. Event sourcing offers benefits including atomic state changes, publishing events, and the ability to keep materialized views of entities even as application operations alter them.

Microservices Interview Questions And Answers: Intermediate To Advanced
Q10. What does a container do in the context of microservices?
A container is a logical packing of a microservice-based application that separates it from the environment in which it runs. Applications can travel across environments and execute independently using containers, which are lightweight, efficient, and common methods. They package an application along with all of its dependencies, making deployment simple and reliable. Containers share the host operating system's kernel, eliminating the need for a hypervisor's infrastructure costs. It is simpler to manage and expand microservices-based applications thanks to containers, which offer a consistent and dependable approach to package, distribute, and run microservices.
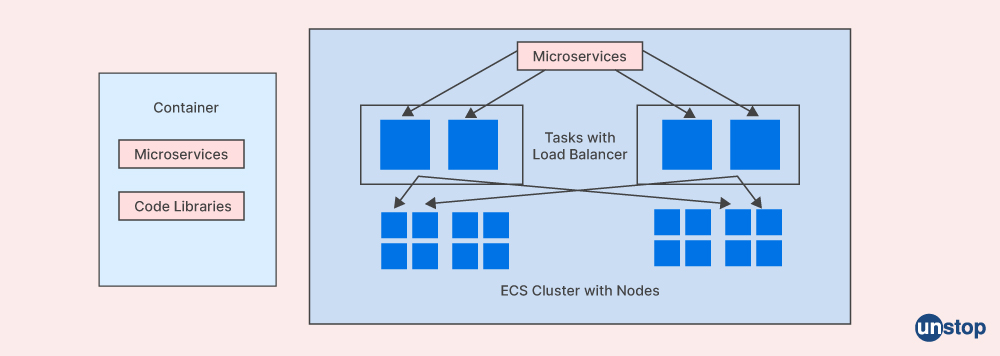
Q11. What role do restful web services serve?
RESTful web APIs serve the purpose of merging various microservices into a single application in the context of microservices. They are like the architectural style to help the system with the internet. Restful web services give developers a logical framework for creating interfaces between microservices, enabling them to communicate without needing to know each other inside and out. RESTful APIs must adhere to the OpenAPI Specification, which provides a defined contract for how services are supposed to communicate throughout ongoing development and employ standard HTTP verbs for creating, retrieving, updating, and deleting activities.
Q12. What do microservice's reactive modifications entail?
The reactive system architecture is used in microservices to make it possible for applications made up of several microservices to cooperate. Asynchronous messaging patterns are used in reactive systems design to handle resilience in the structure. Reactive microservices are built to manage high levels of traffic and requests and are scalable, performant, and robust.
Reactive microservices handle requests and responses using non-blocking I/O and event-driven programming, enabling them to handle numerous requests concurrently without blocking. Frameworks like Spring WebFlux, Play Framework, Ratpack, and Vert.x can be used to construct reactive microservices.
Q13. Describe dumb pipelines and smart endpoints.
The 'dumb pipelines and smart endpoints' are design ideas in Microservices. According to this design idea, the microservices should use simple/ basic architecture, along with their own tried-and-true communication techniques, instead of using complicated middleware.
The theory states that the pipelines have to be kept straightforward and devoid of any complexity, while the endpoints should be the ones in charge of carrying their communication logic. In microservices, the endpoints are made to be intelligent, meaning they handle the majority of the processing logic, while the pipelines are made to be dumb, meaning they merely transfer data from one endpoint to another.
The ability to decentralize the architecture, particularly with how endpoints are maintained, updated, and expanded, is the primary advantage of creating smart endpoints and dumb pipelines.
Q14. What does the 'serverless model' refer to?
The term 'serverless model' describes a cloud computing architecture in which the server infrastructure is managed by a separate cloud provider, allowing developers to concentrate on creating code without concern about the supporting infrastructure. In a serverless paradigm, programmers distribute their code as functions that run whenever certain events or triggers occur. These functions are often stateless, short-lived, and created to carry out a particular activity or function for an application. In microservices-based architectures, where each microservice is built as a serverless function that can be scaled independently and delivered quickly, serverless models are frequently employed.
Q15. What does the phrase 'semantic monitoring' mean?
Semantic monitoring is an active monitoring strategy that combines monitoring and automated testing to find business requirements that the microservices-based application is failing to meet. Semantic monitoring, also known as synthetic monitoring, routinely executes a portion of an application's automated tests against the live production system.
The results of these tests are fed into the monitoring service, which sends alarms when something goes wrong. Semantic monitoring offers insights into business transaction functionality, service availability, and overall application performance, enabling faster bug triaging and isolation, hence lowering the overall time needed to repair. Semantic monitoring has its roots in the functional testing area of synthetic transactions, where scripts simulate actual users interacting with the application or business transaction to ensure that the code is sound.
Q16. What exactly is 'domain-driven design'?
The goal of domain-driven design (DDD) is to model the software to fit a certain domain using feedback from experts in that subject. The DDD emphasizes the value of having a common language to describe the domain and of developing a shared understanding of the domain amongst developers and domain experts. It offers a set of guidelines and practices to assist programmers in building elegant object systems with domain models that contain intricate business logic. DDD is a kind of architectural style that uses object-oriented analysis design methods and focuses on domain logic.
Q17. What does the OAuth protocol mean?
OAuth stands for Open Authorization. The OAuth (open authorization protocol) is an open standard for access delegation that gives resource owners a mechanism to securely delegate access to client applications for server resources. It is frequently used by internet users as a way to provide websites or applications access to their information on other websites without having to give them their passwords.
Authorization protocol permits authorization servers to grant access tokens to third-party clients with the resource owner's consent. The third party then employs the access token to enter the resource server's protected resources. The industry-standard protocol for authorization is called OAuth 2.0, and it places a strong emphasis on client application simplicity while also offering specialized authorization procedures.
Q18. What exactly is a consumer-driven contract (CDC), and how can one obtain one?
The consumer-driven contract (CDC) is a strategy to guarantee service communication compatibility in microservices. The main principle of CDC is that each API user enters into a contract with the provider that outlines the expected behavior of the API and that the service consumer establishes the requirements for the service provider's API. The CDC is a software testing approach that is used to evaluate individual system components in isolation while verifying that provider components are compliant with expectations placed on them by consumer components.
To obtain a CDC for a microservice, the service consumer must specify the needs of the provider's API and enter into a contract with the provider that outlines the expected behavior of the API. In a consumer-driven approach, the consumer influences modifications to contracts between a consumer (the client) and a provider (the server), assisting providers in creating APIs that match the actual needs of the consumers rather than attempting to predict these in advance.
Q19. What does the phrase 'service discovery' mean?
The process of automatically locating devices and services on a computer network is known as service discovery. An application learns about the services on the network through this method. Because it can be challenging to identify network locations, service discovery is frequently used in microservice designs and containerization platforms, especially those that are cloud-based. By automatically identifying devices and available services over a network, service discovery minimizes configuration efforts for administrators and decreases the need for manual configuration.
Q20. What distinguishes cohesion from coupling?
|
Cohesion |
Coupling |
|
Cohesion shows relationships within a module. |
Coupling shows a relationship between modules. |
|
Cohesion should be increased for software. |
For software, increasing coupling is avoided. |
|
The best software results from high coherence. |
The best software is produced by loose coupling. |
|
The same module bonds together to form cohesion. |
There is a coupling established between two distinct modules. |
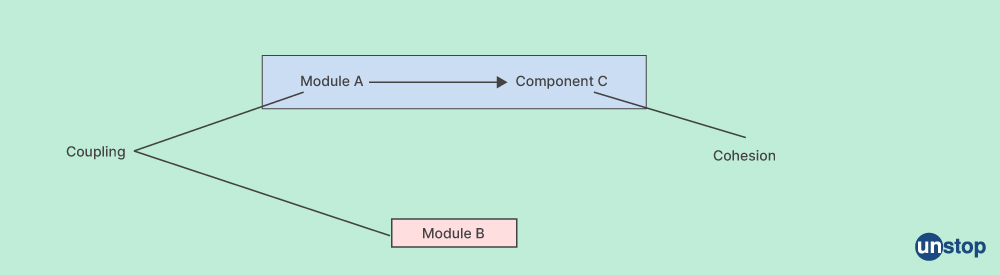
Also read- Cohesion Vs. Coupling: Know The Differences Between The Two For A Better Software Design!
Q21. What is distributed transaction?
Any transaction that modifies data on two or more networked computer systems is referred to as a distributed transaction. It is a database procedure that involves two or more network hosts. Typically, hosts supply transactional resources, and the transaction manager is in charge of constructing and overseeing a global transaction that includes all activities against those resources. When data activities are executed over two or more databases, this is known as a distributed transaction. Transactions that span many databases are frequent, and a distributed transaction is just a database transaction that needs to be synchronized among several participating databases spread over various network hosts.
Q22. What does the phrase 'Canary Releasing' mean?
By gradually exposing the change to a small portion of traffic, canary releasing is a deployment approach that releases an application or service progressively to a subset of users prior to distributing it over the entire infrastructure and lowers the risk of introducing a new software version in production. A candidate version of a microservice that receives a tiny amount of traffic is called a "canary release." It lowers the danger of using a new software version.
The objective behind the canary release is to test a new version of a microservice is to test it in a setting similar to production with actual traffic but only on a limited subset of users. This is done before the new version of the microservice is made available to all users.
Q23. What does end-to-end microservices testing mean?
End-to-end testing in microservices is a testing method used to test an application's flow through a business transaction, confirming that the system satisfies users' needs and accomplishes their business goals, and covers all the microservices in the application using the same interfaces that users would. Distributed testing, on the other hand, offers a substitute that enables isolation testing of each microservice before interfacing testing.
Q24. What does 'client certificate' mean?
The client certificate is a kind of digital certificate used by client systems to send verified requests to remote servers. It is a certificate that is utilized to authenticate users during an SSL handshake, offering reliable guarantees of the requester's identity. The client certificate gives the server evidence of the user's identity when they connect and provide strong assurance of the user's identity.
Client certificates are frequently employed in private networks where the server may confirm the client's identity and give access to particular resources depending on that identity. Client systems use remote servers to authenticate their requests.
Q25. What is Ubiquitous Language, and why is it important?
Everyone involved in a software development project, from domain experts to developers, uses a shared, standard vocabulary known as the "ubiquitous language" in microservices to guarantee that everyone has a shared understanding of the domain and the issue at hand. It is a crucial idea in domain-driven design and is used to explain the domain model and the microservices that comprise the system. Ubiquitous language needs to be as clear as a crystal.
Q26. What does the phrase 'bounded context' mean?
A central pattern in Domain-Driven Design (DDD) specifies a logical boundary within which a certain domain model applies. It is a domain where certain sub-domains make sense, although, in other limited contexts, the same concepts could have different meanings. Here, a bounded context is a means to break up a big, complicated domain into smaller, easier-to-manage chunks, each having its domain model. Inside this boundary, all terms, laws, and ideas are uniformly applicable, and the domain model is described using the common language.
The bounded context is a clearly defined boundary that contains a domain model that converts widespread language into a software model.
Q27. What exactly is 'contract testing'?
Contract testing is a software testing technique that examines how various software components or microservices interact with one another in light of the contracts that have been reached. It is a technique for independently confirming integration between two apps to check whether what has been passed and id what has been received matches up. Contract testing can be crucial in microservices since it guarantees that each microservice is functioning properly and that the contracts between them are being honored. Contract testing happens at the boundary of an external service.
Q28. When should one use 'Netflix Hystrix'?
A library called Netflix Hystrix was created to regulate how dispersed services communicate with one another while offering better tolerance for delay and failure. One should employ the Netflix Hystrix library to increase a distributed system's overall resilience and prevent the failure cascade. When working with third-party services that are not under your control, Hystrix is very helpful since it offers a mechanism to isolate and resolve errors in those services without affecting the rest of the system.
Hystrix offers the Circuit Breaker Pattern implementation, which isolates calls to other services by enclosing them in a circuit breaker object, serving as a proxy, and only forwarding the calls to the underlying service when it is closed.
Q29. What distinguishes a 'tasklets' from a 'Chunk'?
A tasklet is a simple step that completes a single task. A chunk, in comparison, is a more complicated step that reads data, processes it, and publishes it back to the database in chunks. While chunks are good for processing huge amounts of data in a batch job, tasklets are useful for small jobs that don't require complicated processing. While chunks execute throughout numerous transactions, tasklets only execute once.
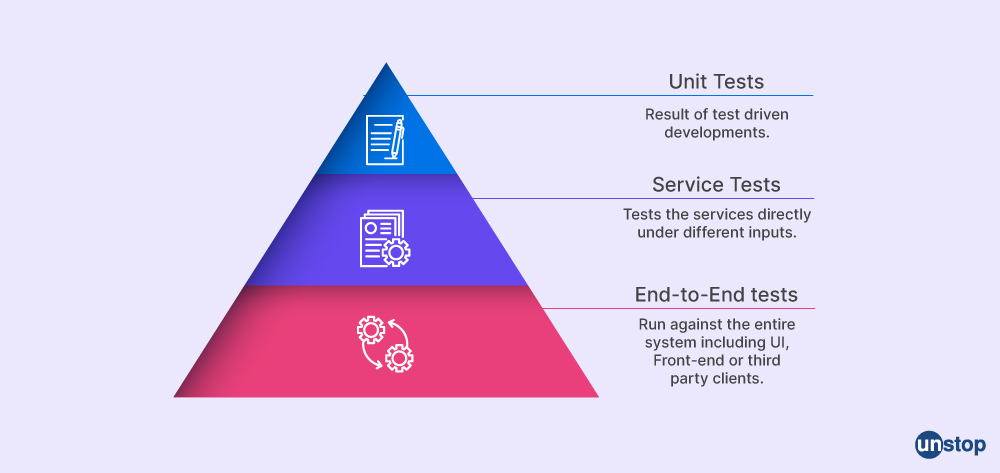
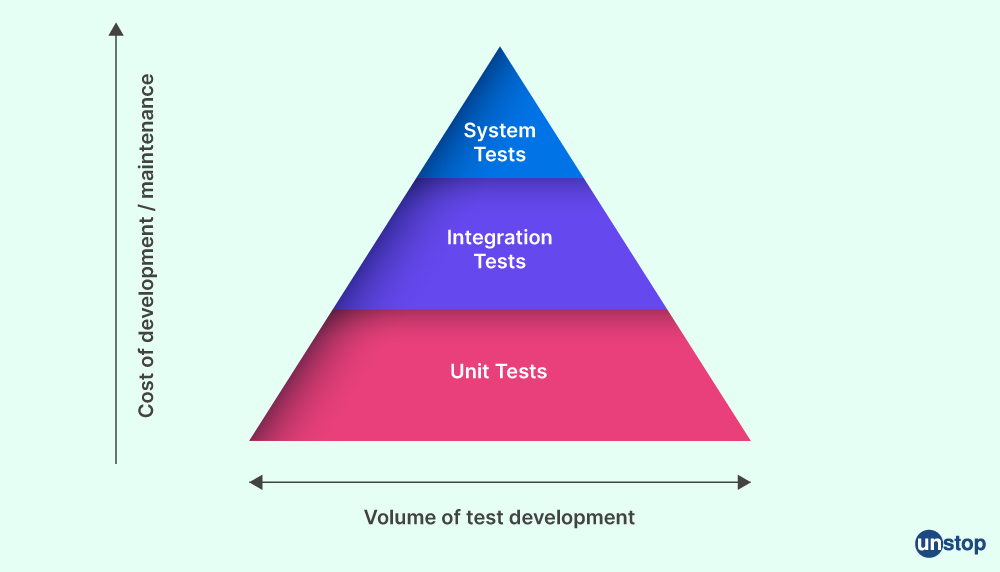
Q30. Explain Mike Cohn's Test Pyramid.
Mike Cohn test is a technique for testing software applications that can be created using the pyramid notion. It is a metaphorical representation that asks us to consider the various testing levels and their varying degrees of importance. Unit testing, service level testing, and user interface tests make up the three tiers of the Test Pyramid.
Unit testing, which are automated tests that confirm the functionality of specific pieces of code, makes up the bottom layer of the pyramid-like performance test. The middle layer is made up of automated tests called service level testing that validate the behavior of the services that comprise the application. The top layer is made up of UI tests, which are automated tests that examine how an application's user interface functions. According to the Test Pyramid, fewer tests should be administered at the top of the pyramid than at its base.
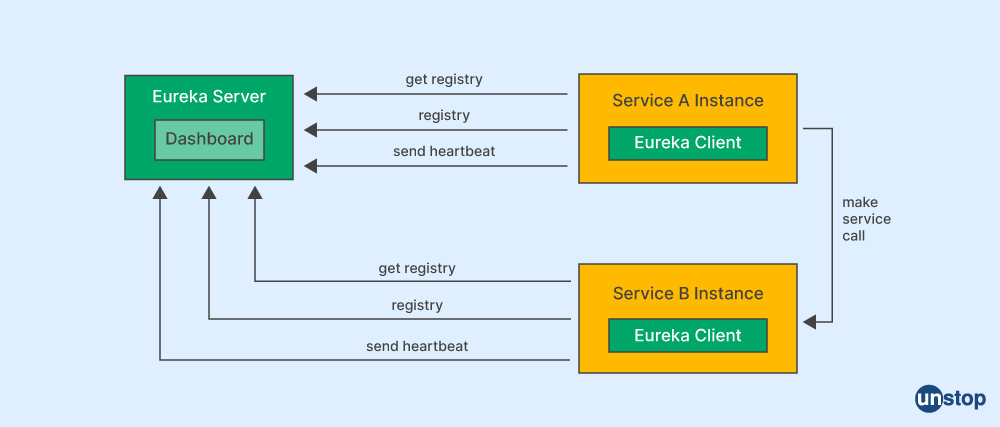
Q31. What does 'Eureka' mean in reference to the microservices architecture?
In a microservices architecture, Eureka is a service discovery tool that aids in finding services and instances of services. All client service applications, including the addresses of all registered microservices, are kept on the Eureka server. It is simpler to scale and manage microservices using Eureka because it gives microservices a mechanism to discover one another without hardcoding IP addresses and port numbers. If the current instance of a service fails, clients can automatically switch to a healthy instance thanks to load balancing and failover features offered by the Eureka server.
Spring Cloud is bundled with Eureka Server. Each microservice may be written, tested, and deployed independently of other microservices thanks to Eureka Server, which enables developers to create durable and scalable microservices-based systems.
Even though Eureka Server is just one of many service discovery technologies available for microservices-based systems, the Spring Cloud community makes extensive use of it and provides strong support.
Q32. What is the most important function that docker fulfills in the context of microservices?
The primary purpose of Docker is to provide a container environment that enables autonomous packaging and deployment of microservices. Using the container technology of Docker, programmers can create microservices, which decentralize packages and separate jobs into independent integrations that cooperate. Docker maintains consistency across all microservice container environments, ensuring that each has its resources that are segregated from the others and assisting with memory and access management. Docker accelerates the software delivery process by enabling developers to independently create, ship, test, and deploy microservices.
The docker container environment makes it simpler to scale and manage microservices because they are lightweight and modular and offer a platform for their deployment that is independent of the underlying infrastructure.
Q33. Why are reporting and dashboards necessary for microservices?
Both dashboards and reports are crucial for system management and monitoring in microservices. They enable quick identification and resolution of problems since they offer insights into the operation of the system as a whole. Key metrics for microservices deployed to various container orchestration platforms can be shown on dashboards, giving a centralized view of the system. The reporting module keeps track of all changes via a messaging system and saves the updated information in a different report database, enabling improved efficiency and effective change tracking.
Q34. How is a 'Mock' different from a 'Stub'?
A mock and a stub are both types of test duplicates used in software testing, but they have different functions.
|
Mock |
Stub |
|
Using a mock ensures that specific methods are invoked in the code you're testing. |
A stub helps provide data that the code being tested needs to function. |
|
A mock object helps verify that the objects are being applied using the proper methods and pathways. |
A stub simulates real objects using the bare minimum of test-related methods. |
|
A mock is used to test the behavior of the code as well as the interactions between objects. |
A stub is used to replace an actual item with a condensed variant that produces known outcomes. It is used to check the code's functionality |
Q35. How can a system built on microservices be scaled?
There are several ways to scale a microservices-based system, including vertical scaling and horizontal scaling. When a microservice is vertically scaled, more resources are added to a single instance of the service, such as more server resources for CPU, memory, or storage. When a microservice needs more resources to manage more traffic or workload, vertical scaling is helpful.
Horizontal scaling is the process of increasing the number of microservice instances to handle growing workloads or traffic by adding more servers to a load balancer. When a microservice must handle a lot of requests or when the effort is unevenly distributed throughout the system, horizontal scaling is helpful. Y-axis scaling, another technique for scaling microservices, divides the application into its constituent parts.
Q36. Describe the differences between orchestration and choreography.
Orchestration and choreography are two alternative methods for coordinating microservices in a distributed system. Some key differences between the two are-
|
Orchestration |
Choreography |
|
It involves a centralized controller that manages the interactions between microservices, acting as a conductor that directs the flow of data and control between the services. |
Choreography involves a decentralized approach where each microservice is responsible for its behavior and communication with other services. |
|
In orchestration, the controller is responsible for managing the state of the system, handling errors, and ensuring that the services are working together correctly. |
In choreography, each service communicates with other services through events or messages, and there is no central controller that manages the interactions between services. |
Q37. What does YAML in microservices mean?
Microservices frequently employ the human-readable data serialization language- YAML, for setup and deployment purposes. A popular option for configuration files in microservices is YAML since it allows for the definition of data structure in a way that is simple to read and write.
YAML files are employed to define the various microservices' constituent parts, including the services, containers, and volumes, as well as to provide their configuration options. The files are also utilized to define the deployment and scaling of microservices, defining the resources needed for each instance as well as the number of replicas to be deployed. YAML files can also be used with container orchestrators like Kubernetes, which do so to specify the desired state of the system using YAML files.
Q38. What does 'blue/green deployment' mean?
The blue/green deployment is a deployment approach used in software engineering, and it entails building two identical production environments, known as 'blue' and 'green'. Then one of these environments is used in operation and to manage incoming traffic. The other is idle and is utilized for application testing and the rollout of new versions. To ensure a smooth transition between different versions of the program, traffic is gradually moved from the active environment to the idle environment.
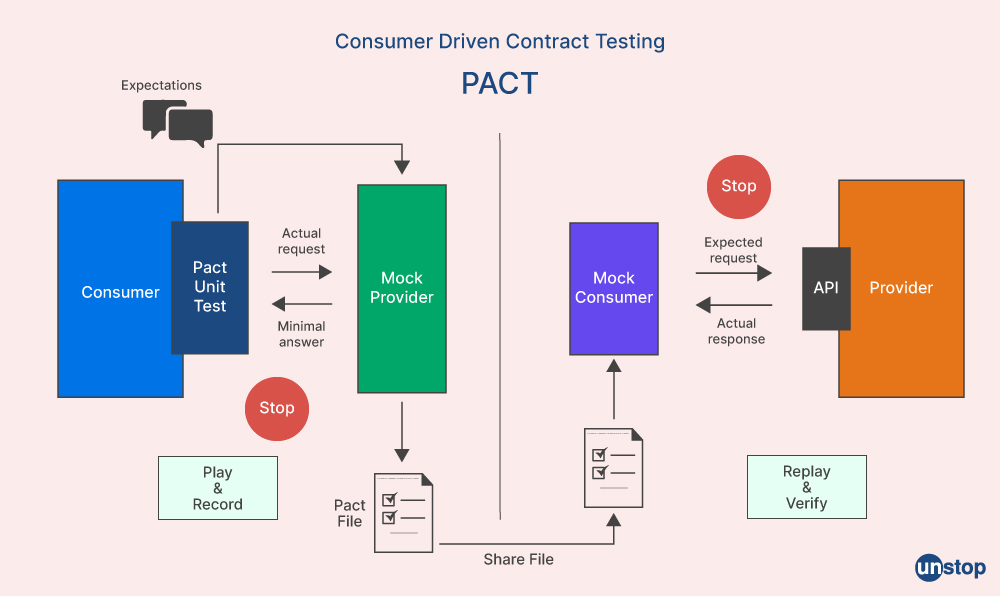
Q39. What is PACT in the architecture of microservices?
In the microservices architecture, PACT is an open-source tool for contract testing HTTP and message integrations. Consumer-driven contracts, such as PACT, specify the expected request and response formats between services. It is a popular tool that lowers the possibility of mistakes and system failures and enables developers to design contracts on the consumer side and conduct tests as part of the development process. The authenticity of microservices integration increases because of PACT.
Q40. What is microservice's continuous monitoring?
Continuous monitoring in microservices is the activity of continuously keeping an eye on microservices-based systems to see problems as they arise or risk issues and take immediate action. Utilizing technologies like log analyzers, metrics collectors, and tracing systems, continuous monitoring entails keeping an eye on many elements of the system, and virtualized infrastructure metrics, including performance, availability, and security. The CI/CD pipeline should include continuous monitoring to ensure that new code releases are continually checked for performance and availability and that there are no risk issues.
Q41. What do you understand by the term two-factor authentication?
In microservices-based systems, two-factor authentication can be utilized to add an additional level of security on top of only a username and password. It can be difficult to implement 2FA in microservices-based systems, but several options and techniques can be employed, like using a centralized authentication service or adding 2FA at the API gateway level or proxy layer. It helps in enabling a second level of authentication.
API gateways act as a point of entry for outside clients, and it streamlines the client by transferring the logic for making multiple service calls from the client to the API gateways. Additionally, it aids in separating external API gateways from internal microservices patterns and keeps clients from knowing the service's history and versioning information.
Q42. What are the fundamental principles of DDD?
Fundamental principles of domain-driven design, which is an architectural style, are- concentrating on the core domain and domain logic, analyzing domain models to uncover complex designs, and regularly working with domain experts to enhance the application model and handle new domain concerns. Note that the DDD handles the business domains.
Q43. What is the purpose of Reactive Extensions?
Reactive Extensions is a library and a design pattern (which is a popular tool, that allows the creation of event-based and asynchronous programs utilizing observable sequences. This popular tool is denoted by Rx. It can be used to create reactive microservices that communicate over a process boundary utilizing asynchronous message-passing in the context of microservices. Reactive microservices are extremely performant and scalable since they are made to execute their activities without blocking. Reactive microservices can cooperate and work together without being tightly connected since they are message-driven, opening up new development and deployment patterns. Rx is an open-source tool that works the opposite of legacy flows.
Q44. What do you understand by the term continuous integration?
Continuous Integration, often referred to as CI in microservices, is an essential practice that entails regularly merging code changes into the main branch and automatically creating and testing code to make sure it is functioning as intended. Building and testing each microservice separately before merging them into the larger system is what continuous integration (CI) entails in the context of microservices.
CI makes modifications to the codebase less likely to introduce bugs or other problems that could negatively affect the system as a whole. With the help of CI, developers may find problems in microservices early by testing code and guaranteeing that the system is always in a functional state.
Q45. Describe the main types of testing used in microservices.
The testing used in microservices is categorized based on their level as follows:
Bottom-level tests: These refer to technology-focused tests such as unit tests and performance tests
Middle-level tests: They are exploratory tests that help to identify issues related to performance and user experience, like stress tests. A stress test is performed to assess a system's maximum capacity and to find performance problems and bottlenecks.
Top-level tests: These tests, which have fewer acceptance tests, serve to confirm that the program is operating properly and giving users the functionality they are expecting by verifying the software features. Software features help stakeholders to verify and understand the functions.
Q46. Can you tell what Non-deterministic tests (NDT) means?
Non-deterministic tests (NDT) in microservices mean that they are unreliable tests, i.e., they may succeed or fail without observable changes to the code, tests, or environment.
Q47. In microservices, what does container image mean?
A static file containing executable code, system libraries, system tools, and other platform parameters necessary to operate an isolated process on IT infrastructure is known as a container image in a microservices architecture. It includes a bundled application, its dependencies, and details on the processes that are launched when it is launched. Container images may be deployed consistently in any environment and are immutable, which means they cannot be modified.
Q48. What difficulties do users of microservices encounter?
The problems of a microservices architecture are both functional and technical.
Some of the technical difficulties include:
- Due to the distributed nature of the system and the interdependencies between the microservices, there are several technical problems to be aware of, including operations overhead.
- For the support of heterogeneously distributed microservices, skilled professionals are required.
- Because there are so many tiny components, it is challenging to automate because each one needs to be developed, deployed, and monitored separately.
The functional difficulties that developers might face with microservices are that they have a heavy infrastructure setup, there is a significantly heavy investment (i.e., microservices involve a heavy investment), and lastly, the is a need for excessive planning to address or control operational overhead.
Q49. Can large-scale applications be developed using microservices?
Yes, it is possible to develop large-scale applications with microservices. However, it's difficult to develop microservice large-scale applications successfully, and doing so calls for more complex coordination. It is crucial to be aware of the performance and efficiency goals, supported by an efficient monitoring system in place and a strategy that would help maintain the optimal performance of microservices in order to expand a microservices-based application effectively.
Q50. Tell me some advantages of microservices.
The advantages of using microservices are-
Technology variety- Due to their ease of integration with various frameworks, libraries, and databases, microservices enable technology diversity.
Fault isolation - A system's capacity to contain and isolate faults or failures inside a particular service or component without affecting the entire system is known as fault isolation.
Microservices design offers better support for smaller, parallel teams, enabling quicker development and deployment. Another benefit of the microservices architecture is that each microservice can be independently deployed without affecting the system as a whole.
Spring/ Spring Boot Microservices Interview Questions
In this section, we will focus on interview questions you will come across in reference to microservices with Spring Boot.
Q51. Can you tell me what enables the production-ready feature of the spring boot application?
The production-ready feature in a spring boot application is enabled through the Spring Boot Actuator.
Q52. What does load balancing mean in the context of spring cloud?
In Spring Cloud, the term 'load balancing' describes the process of dividing incoming network traffic among several instances of service to maximize throughput, reduce response times, and prevent the overloading of any single resource. The Spring Cloud Load Balancer library works with service discovery to distribute incoming traffic among accessible instances of a service. It offers client-side load balancing for Spring Cloud applications. Spring cloud combines with an external system.
Q53. Describe various embedded containers that Spring Boot supports.
Spring Boot supports several embedded containers like-
Tomcat- It can be integrated into Java web applications.
Undertow- Java-based Undertow is a flexible and powerful web server that offers both blocking and non-blocking APIs based on NIO.
Jetty- Jetty is a popular Java server that can be run as an embedded container in any Java application server.
Q54. Can you explain spring cloud to me?
A collection of frameworks and tools called Spring Cloud assists programmers in creating and deploying microservices-based systems. It adapts to external systems. It offers a range of functions that are necessary for creating and deploying microservices, including service discovery, configuration management, load balancing, and circuit breakers. Spring Cloud connects with Spring Boot, a well-liked Java microservices development framework. With Spring Cloud, programmers can quickly construct microservices using Spring Boot, allow load balancing, scale up and down microservices, and centralize microservice configuration.
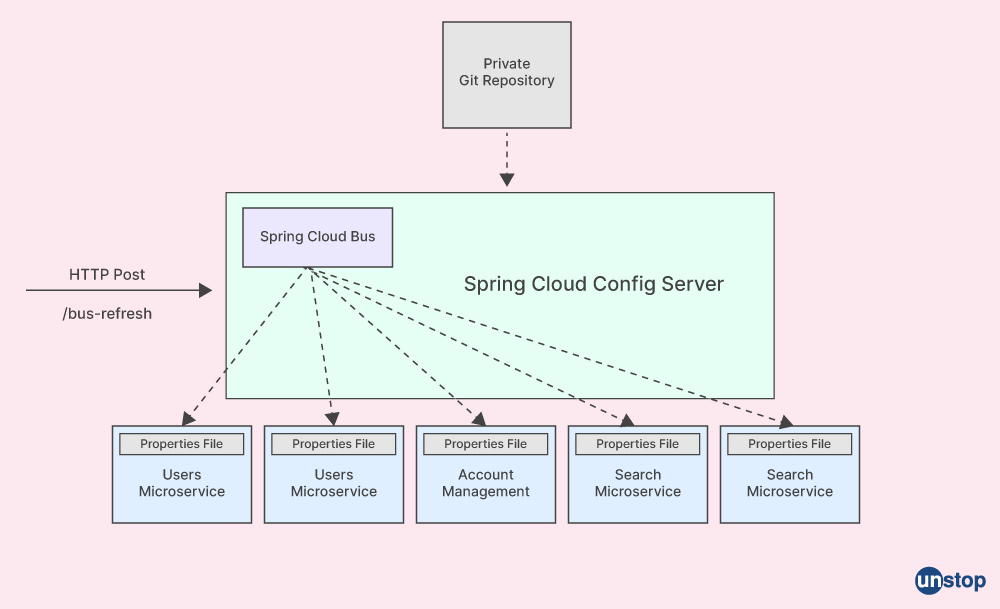
Q55. Tell me about the spring cloud bus and spring cloud gateway.
Spring Cloud Bus is a framework that connects a distributed system's nodes to a simple message broker. Spring Cloud Bus is most often used to disseminate configuration changes or other state changes throughout a distributed system. It can be used to minimize network traffic and enhance system performance. Spring Cloud Bus can also be used to remove the requirement for clients to poll for configuration changes. Here, a message broker propagates state changes to all the microservice instances that have registered with Spring Cloud Bus.
Spring Cloud Gateway is a Java-based API gateway that offers a quick and easy way to access APIs and address concerns that cut across several APIs, like security and monitoring. The Spring Cloud Gateway is a load balancer and proxy replacement that is built on top of the Spring Framework ecosystem. Services must connect in a distributed environment, and Spring Cloud Gateway can be used to control this communication. The Spring WebFlux HandlerMapping architecture contains several built-in route predicate factories and filters, and Spring Cloud Gateway matches routes as part of that infrastructure. Authentication, rate restriction, and circuit breaking are a few examples of cross-cutting concerns that can be implemented with Spring Cloud Gateway.
Q56. What do you understand by SCDF?
SCDF is a microservices-based data processing framework for Cloud Foundry and Kubernetes that supports both streaming and batch data processing. The Data Flow Server, a microservice application built on Spring Boot that serves as the main entry point to the framework, is the center of the SCDF ecosystem. Using the REST API, SCDF enables programmers to build pipelines made up of Spring Boot apps created using the Spring Cloud Stream or Spring Cloud Task microservice frameworks. Additionally, SCDF helps with distributed tracing. REST API can be used to access SCDF.
Q57. What exactly is the 'Spring Batch Framework'?
The Spring Batch Framework is a free, open-source, all-inclusive batch processing framework created to facilitate the creation of reliable batch applications. Spring Batch offers a collection of reusable parts and patterns for batch processing, building on the POJO-based development paradigm of the Spring Framework. The development and management of batch applications are made simpler by Spring Batch's inclusion features like parallel processing, transaction management, job restart, and skip/retry functionality.
Q58. Explain the role of the actuator in Spring Boot.
The Spring Boot Actuator is an important component of the Spring Boot Framework. It exposes operational data about any application that is currently executing using HTTP endpoints. The primary advantage of using the actuator is that we get health and monitoring information from applications that are ready for production when we use this library. Actuator also makes it quite simple to acquire metrics, evaluate traffic, and know the status of databases.
You must enable the spring-boot-actuator requirement in your pom.xml file to use Actuator in your application, as shown here-
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>
Q59. Could you describe a spring boot?
Spring Boot is a solution that makes it simpler to quickly construct production-quality apps and services using the Spring framework. It is constructed on top of the Spring Framework and offers a simpler and quicker method for setting up, configuring application servers, and running straightforward and sophisticated Spring applications. Since Spring Boot is intended to have an opinion, it offers a set of defaults and standards that make it simpler to begin using Spring programming.
The development process is further made simpler by various features and tools, such as auto-configuration, which configures the Spring application depending on the dependencies in the classpath. Due to its speedier and simpler development process, Spring Boot is frequently used to create web apps and microservices using the Spring Framework and provides an easier way to deploy these applications.
You may also be interested in these articles:
- Top Goldman Sachs Interview Questions With Answers (2024)
- Mindtree Interview Questions 2024 That Will Take Your Preparation To The Next Level!
- 60+ AngularJS Interview Questions & Answers You Must Know
- Important KPMG Interview Questions 2024 With Answers For Technical And HR Rounds
- Top L&T Interview Questions With Answers That You Should Not Skip
An economics graduate with a passion for storytelling, I thrive on crafting content that blends creativity with technical insight. At Unstop, I create in-depth, SEO-driven content that simplifies complex tech topics and covers a wide array of subjects, all designed to inform, engage, and inspire our readers. My goal is to empower others to truly #BeUnstoppable through content that resonates. When I’m not writing, you’ll find me immersed in art, food, or lost in a good book—constantly drawing inspiration from the world around me.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter
Blogs you need to hog!

How To Write Finance Cover Letter For Morgan Stanley (+Free Sample!)

55+ Data Structure Interview Questions For 2026 (Detailed Answers)

How To Negotiate Salary With HR: Tips And Insider Advice









Comments
Add comment