- TCS Technical Interview Questions & Answers
- TCS Managerial Interview Questions & Answers
- TCS HR Interview Questions & Answers
- Overview of Cognizant Recruitment Process
- Cognizant Interview Questions: Technical
- Cognizant Interview Questions: HR Round
- Overview of Wipro Technologies Recruitment Rounds
- Wipro Interview Questions
- Technical Round
- HR Round
- Online Assessment Sample Questions
- Frequently Asked Questions
- Overview of Google Recruitment Process
- Google Interview Questions: Technical
- Google Interview Questions: HR round
- Interview Preparation Tips
- About Google
- Deloitte Technical Interview Questions
- Deloitte HR Interview Questions
- Deloitte Recruitment Process
- Technical Interview Questions and Answers
- Level 1 difficulty
- Level 2 difficulty
- Level 3 difficulty
- Behavioral Questions
- Eligibility Criteria for Mindtree Recruitment
- Mindtree Recruitment Process: Rounds Overview
- Skills required to crack Mindtree interview rounds
- Mindtree Recruitment Rounds: Sample Questions
- About Mindtree
- Preparing for Microsoft interview questions
- Microsoft technical interview questions
- Microsoft behavioural interview questions
- Aptitude Interview Questions
- Technical Interview Questions
- Easy
- Intermediate
- Hard
- HR Interview Questions
- Eligibility criteria
- Recruitment rounds & assessments
- Tech Mahindra interview questions - Technical round
- Tech Mahindra interview questions - HR round
- Hiring process at Mphasis
- Mphasis technical interview questions
- Mphasis HR interview questions
- About Mphasis
- Technical interview questions
- HR interview questions
- Recruitment process
- About Virtusa
- Goldman Sachs Interview Process
- Technical Questions for Goldman Sachs Interview
- Sample HR Question for Goldman Sachs Interview
- About Goldman Sachs
- Nagarro Recruitment Process
- Nagarro HR Interview Questions
- Nagarro Aptitude Test Questions
- Nagarro Technical Test Questions
- About Nagarro
- PwC Recruitment Process
- PwC Technical Interview Questions: Freshers and Experienced
- PwC Interview Questions for HR Rounds
- PwC Interview Preparation
- Frequently Asked Questions
- EY Technical Interview Questions (2023)
- EY Interview Questions for HR Round
- About EY
- Morgan Stanley Recruitment Process
- HR Questions for Morgan Stanley Interview
- HR Questions for Morgan Stanley Interview
- About Morgan Stanley
- Recruitment Process at Flipkart
- Technical Flipkart Interview Questions
- Code-Based Flipkart Interview Questions
- Sample Flipkart Interview Questions- HR Round
- Conclusion
- FAQs
- Recruitment Process at Paytm
- Technical Interview Questions for Paytm Interview
- HR Sample Questions for Paytm Interview
- About Paytm
- Most Probable Accenture Interview Questions
- Accenture Technical Interview Questions
- Accenture HR Interview Questions
- Amazon Recruitment Process
- Amazon Interview Rounds
- Common Amazon Interview Questions
- Amazon Interview Questions: Behavioral-based Questions
- Amazon Interview Questions: Leadership Principles
- Company-specific Amazon Interview Questions
- 43 Top Technical/ Coding Amazon Interview Questions
- Juspay Recruitment: Stages and Timeline
- Juspay Interview Questions and Answers
- How to prepare for Juspay interview questions
- Prepare for the Juspay Interview: Stages and Timeline
- Frequently Asked Questions
- Adobe Interview Questions - Technical
- Adobe Interview Questions - HR
- Recruitment Process at Adobe
- About Adobe
- Cisco technical interview questions
- Sample HR interview questions
- The recruitment process at Cisco
- About Cisco
- JP Morgan interview questions (Technical round)
- JP Morgan interview questions HR round)
- Recruitment process at JP Morgan
- About JP Morgan
- Wipro Elite NTH: Selection Process
- Wipro Elite NTH Technical Interview Questions
- Wipro Elite NTH Interview Round- HR Questions
- BYJU's BDA Interview Questions
- BYJU's SDE Interview Questions
- BYJU's HR Round Interview Questions
- A Quick Overview of the KPMG Recruitment Process
- Technical Questions for KPMG Interview
- HR Questions for KPMG Interview
- About KPMG
- DXC Technology Interview Process
- DCX Technical Interview Questions
- Sample HR Questions for DXC Technology
- About DXC Technology
- Recruitment Process at PayPal
- Technical Questions for PayPal Interview
- HR Sample Questions for PayPal Interview
- About PayPal
- Capgemini Recruitment Rounds
- Capgemini Interview Questions: Technical round
- Capgemini Interview Questions: HR round
- Preparation tips
- FAQs
- Technical interview questions for Siemens
- Sample HR questions for Siemens
- The recruitment process at Siemens
- About Siemens
- HCL Technical Interview Questions
- HR Interview Questions
- HCL Technologies Recruitment Process
- List of EPAM Interview Questions for Technical Interviews
- About EPAM
- Atlassian Interview Process
- Top Skills for Different Roles at Atlassian
- Atlassian Interview Questions: Technical Knowledge
- Atlassian Interview Questions: Behavioral Skills
- Atlassian Interview Questions: Tips for Effective Preparation
- Walmart Recruitment Process
- Walmart Interview Questions and Sample Answers (HR Round)
- Walmart Interview Questions and Sample Answers (Technical Round)
- Tips for Interviewing at Walmart and Interview Preparation Tips
- Frequently Asked Questions
- Uber Interview Questions For Engineering Profiles: Coding
- Technical Uber Interview Questions: Theoretical
- Uber Interview Question: HR Round
- Uber Recruitment Procedure
- About Uber Technologies Ltd.
- Intel Technical Interview Questions
- Computer Architecture Intel Interview Questions
- Intel DFT Interview Questions
- Intel Interview Questions for Verification Engineer Role
- Recruitment Process Overview
- Important Accenture HR Interview Questions
- Points to remember
- What is Selenium?
- What are the components of the Selenium suite?
- Why is it important to use Selenium?
- What's the major difference between Selenium 3.0 & Selenium 2.0?
- What is Automation testing and what are its benefits?
- What are the benefits of Selenium as an Automation Tool?
- What are the drawbacks to using Selenium for testing?
- Why should Selenium not be used as a web application or system testing tool?
- Is it possible to use selenium to launch web browsers?
- What does Selenese mean?
- What does it mean to be a locator?
- Identify the main difference between "assert", and "verify" commands within Selenium
- What does an exception test in Selenium mean?
- What does XPath mean in Selenium? Describe XPath Absolute & XPath Relation
- What is the difference in Xpath between "//"? and "/"?
- What is the difference between "type" and the "typeAndWait" commands within Selenium?
- Distinguish between findElement() & findElements() in context of Selenium
- How long will Selenium wait before a website is loaded fully?
- What is the difference between the driver.close() and driver.quit() commands in Selenium?
- Describe the different navigation commands that Selenium supports
- What is Selenium's approach to the same-origin policy?
- Explain the difference between findElement() in Selenium and findElements()
- Explain the pause function in SeleniumIDE
- Explain the differences between different frameworks and how they are connected to Selenium's Robot Framework
- What are your thoughts on the Page Object Model within the context of Selenium
- What are your thoughts on Jenkins?
- What are the parameters that selenium commands come with a minimum?
- How can you tell the differences in the Absolute pathway as well as Relative Path?
- What's the distinction in Assert or Verify declarations within Selenium?
- What are the points of verification that are in Selenium?
- Define Implicit wait, Explicit wait, and Fluent
- Can Selenium manage windows-based pop-ups?
- What's the definition of an Object Repository?
- What is the main difference between obtainwindowhandle() as well as the getwindowhandles ()?
- What are the various types of Annotations that are used in Selenium?
- What is the main difference in the setsSpeed() or sleep() methods?
- What is the way to retrieve the alert message?
- How do you determine the exact location of an element on the web?
- Why do we use Selenium RC?
- What are the benefits or advantages of Selenium RC?
- Do you have a list of the technical limitations when making use of Selenium RC? Selenium RC?
- What's the reason to utilize the TestNG together with Selenium?
- What Language do you prefer to use to build test case sets in Selenium?
- What are Start and Breakpoints?
- What is the purpose of this capability relevant in relation to Selenium?
- When do you use AutoIT?
- Do you have a reason why you require Session management in Selenium?
- Are you able to automatize CAPTCHA?
- How can we launch various browsers on Selenium?
- Why should you select Selenium rather than QTP (Quick Test Professional)?
- Airbus Interview Questions and Answers: HR/ Behavioral
- Industry/ Company-Specific Airbus Interview Questions
- Airbus Interview Questions and Answers: Aptitude
- Airbus Software Engineer Interview Questions and Answers: Technical
- Importance of Spring Framework
- Spring Interview Questions (Basic)
- Advanced Spring Interview Questions
- C++ Interview Questions and Answers: The Basics
- C++ Interview Questions: Intermediate
- C++ Interview Questions And Answers With Code Examples
- C++ Interview Questions and Answers: Advanced
- Test Your Skills: Quiz Time
- MBA Interview Questions: B.Com Economics
- B.Com Marketing
- B.Com Finance
- B.Com Accounting and Finance
- Business Studies
- Chartered Accountant
- Q1. Please tell us something about yourself/ Introduce yourself to us.
- Q2. Describe yourself in one word.
- Q3. Tell us about your strengths and weaknesses.
- Q4. Why did you apply for this job/ What attracted you to this role?
- Q5. What are your hobbies?
- Q6. Where do you see yourself in five years OR What are your long-term goals?
- Q7. Why do you want to work with this company?
- Q8. Tell us what you know about our organization
- Q9. Do you have any idea about our biggest competitors?
- Q10. What motivates you to do a good job?
- Q11. What is an ideal job for you?
- Q12. What is the difference between a group and a team?
- Q13. Are you a team player/ Do you like to work in teams?
- Q14. Are you good at handling pressure/ deadlines?
- Q15. When can you start?
- Q16. How flexible are you regarding overtime?
- Q17. Are you willing to relocate for work?
- Q18. Why do you think you are the right candidate for this job?
- Q19. How can you be an asset to the organization?
- Q20. What is your salary expectation?
- Q21. How long do you plan to remain with this company?
- Q22. What is your objective in life?
- Q23. Would you like to pursue your Master's degree anytime soon?
- Q24. How have you planned to achieve your career goal?
- Q25. Can you tell us about your biggest achievement in life?
- Q26. What was the most challenging decision you ever made?
- Q27. What kind of work environment do you prefer to work in?
- Q28. What is the difference between a smart worker and a hard worker?
- Q29. What will you do if you don't get hired?
- Q30. Tell us three things that are most important for you in a job.
- Q31. Who is your role model and what have you learned from him/her?
- Q32. In case of a disagreement, how do you handle the situation?
- Q33. What is the difference between confidence and overconfidence?
- Q34. If you have more than enough money in hand right now, would you still want to work?
- Q35. Do you have any questions for us?
- Interview Tips for Freshers
- Tell me about yourself
- What are your greatest strengths?
- What are your greatest weaknesses?
- Tell me about something you did that you now feel a little ashamed of
- Why are you leaving (or did you leave) this position??
- 15+ resources for preparing most-asked interview questions
- CoCubes Interview Process Overview
- Common CoCubes Interview Questions
- Key Areas to Focus on for CoCubes Interview Preparation
- Conclusion
- Frequently Asked Questions (FAQs)
- Data Analyst Interview Questions With Answers
- About Data Analyst
Mindtree Interview Questions 2026 That Will Take Your Preparation To The Next Level!

Mindtree Limited is an IT and MNC consulting company, with headquarters in Bangalore, India. In 2019, Mindtree was acquired by Larsen and Toubro before being merged with L&T Infotech (LTI) in 2022 to form LTIMindtree. The company was founded by Ashok Soota, Krishnakumar Natrajan, Subroto Bagchi, and Anjan Lahiri.
For Software Engineering graduates, Mindtree is a good company for gaining professional experience. In this article, we will cover an overview of the Mindtree recruitment process and take you through some important Mindtree interview questions.
Eligibility Criteria for Mindtree Recruitment
The candidate must meet the following criteria:
- BE, BTech(from AICTE-recognized College of Engineering) and MCA graduates are eligible.
- Candidates need to score 65% or above in their 10th, 12th, and BE/BTech/MCA.
- Not more than 2 backlogs.
- Freshers from CSE/IT branches are eligible.

Mindtree Recruitment Process: Rounds Overview
The Mindtree recruitment process is considered extremely close to the Tech Mahindra recruitment process. Generally, the following rounds are included in Mindtree selection process.
1. Aptitude Test
The aptitude test at Mindtree tests the quantitative ability, logical ability, and verbal ability of the candidate. It is a 140-minute long test wherein 75 questions need to be answered.
2. Coding Test
In this round, you need to answer 2 coding questions within 45 minutes. Topics like recursion, pointers, data structures and algorithms, recursion, strings, and mathematical concepts from any one language like C, C++, Java, or Python according to your choice.
3. Technical Interview Process
The Mindtree technical interview may involve questions on topics such as C, C++, and Java. Since you are expected to be aware of the latest developments, your knowledge of trending technologies like AI, IoT, ML, and blockchain may also be checked.
HR Interview Process
The HR interview round may involve basic questions about your personality, family background, training, hobbies, internships, work experience (if relevant), general knowledge, etc. The main purpose of the HR round is to test your knowledge as well as your communication skills.
Note: The aptitude test is moderately difficult and the coding round is fairly hard. The technical and HR rounds are relatively easy if prepared properly. It is also better if you gain some mock interview experience beforehand. Having some interview experience will ease your hesitation and boost your confidence during the Mindtree interview.
Skills required to crack Mindtree interview rounds
Technical Skills:
- Programming languages like C, Java, Python, and C++.
- Strong grasp of CS subjects like OS, Networking, DBMS, DatabaseSQL Databases, Relational structures, SDLC, etc.
- DQL like SQL and MySQL.
- Technical knowledge of Blockchain, ML, Java App Development, Frontend, and Backend Technologies is preferred.
Soft Skills:
- Candidates must possess good communication skills.
- Ability to do teamwork.
- Candidates must be creative and should be able to adapt to different situations and be comfortable working with various technologies.
- Candidates must have good problem-solving skills, analytical thinking, and decision-making in challenging situations.
- Maintain a good work ethic.
- Good time management skills.
- Leadership abilities.
Mindtree Recruitment Rounds: Detailed explanation
Aptitude Test:
The online Aptitude Test is 140 minutes in duration. It includes the following sections.
-
Quantitative Section
-
Logical Section
-
Verbal Section
The quantitative section will have questions from topics:
- Averages
- LCM & HCF
- Ratio & Proportion
- Algebra
- Logarithms
- Permutation and Combinations
- Probability
- Profit and Loss
- Simple and Compound Interest
- Time, Speed, and Distance
- Inverse
- Area, Shapes & Perimeter
- Percentages
- Divisibility
- Pipes & Cisterns
- Numbers, decimal fractions, and power
- Time and Work
The Logical Section questions will include topics:
- Coding deductive logic
- Blood Relation
- Directional Sense
- Objective Reasoning
- Selection decision tables
- Analogy and Classification pattern recognition
- Coding pattern and Number series pattern recognition
- Odd Man Out
- Statement & Conclusion
- Seating Arrangement
- Logical word sequence
- Data sufficiency
- Mathematical Order
- Inferred Meaning
The Verbal Ability section will include topics:
- Synonyms
- Antonyms
- Contextual Vocabulary
- Jumbled Sentences
- Sentence Formation
- Error Identification
- Sentence Improvement & Construction
- Subject-Verb Agreement
- Tenses & Articles
- Proposition & Conjunctions
- Speech & Voices
- Reading Comprehension
- Comprehension ordering
Sample Questions for Mindtree Aptitude Round
Q1: How many three-digit numbers can be formed with the digits 6, 7, 8, 9, and 3 (repetition of digits not allowed)?
Options:
- 150
- 60
- 120
- 125
Ans: 2. 60
Solution:
The number of numbers formed would be given by = 5 x 4 x 3 (given that the first digit can be filled in 5 ways, the second in 4 ways, and the third in 3 ways).
Q2: A Range Rover covers a distance of 376 km at a certain speed in 8 hours. How much time would a truck take at an average speed which is 18 kmph more than that of the speed of Range Rover to cover a distance which is 14 km more than that traveled by the range rover?
Options:
- 4 hours
- 5 hours
- 8 hours
- 6 hours
Answer: 4. 6 hours
Solution:
Speed of the range rover = Distance/time = 376/8 = 47 kmph
Now, speed of truck = (speed of range rover + 18) kmph = (47 + 18) = 65 kmph
Distance travelled by truck = 376 + 14 = 390 km
Time taken by truck = Distance/Speed = 390/65 = 6 hours.
Q3: Two pipes, P and Q, together can fill a cistern in 2 hours and P alone can in 3 hours. Then Q alone can fill the cistern in?
Options:
- 5 hours
- 5.5 hours
- 6 hours
- 6.5 hours
Answer: 3. 6 hours
Solution:
Let p and q be time taken by P and Q to fill the tank
Total time required to fill the tank, t = pq/ (p + q)
Here,
t =2 hour
p = 3 hour
So,
2 = 3q/(3+q)
q = 6
So, Required time = 6 hours
Q4: Milkha takes 3 steps for every 5 steps of Bolt. If one step of Milkha is equal to 3 steps of Bolt, the ratio of the speed of the Milkha to that of Bolt is?
Options:
- 3:4
- 4:3
- 5:9
- 9:5
Answer: 4. 9:5
Solution:
Milkha: Bolt = (3 x 3) 4 Steps of Bolt: 5 Steps of Milkha = 9: 5
Q5: The sum of the ages of 5 children born at the intervals of 3 years each is 50 years. what is the age of the youngest child?
Options:
- 10
- 9
- 8
- 4
Answer: 4. 4
Solution:
Let x = the youngest child.
Each of the other four children will then be x+3, x+6, x+9, x+12.
We know that the sum of their ages is 50.
so, x+(x+3)+(x+6)+(x+9)+(x+12) = 50
⇒ 5x+30 = 50
⇒ 5x = 20
⇒ x= 4
The youngest child is 4 years old.
Logical Reasoning Questions with Answers:
Q6: 5040, 720,480,?
Options:
- 280
- 420
- 380
- 360
Answer: 4. 360
Solution:
Logic - Multiplying each term by ½, ⅔, ¾, ⅘…
5040 * ½ = 720,
720 * ⅔ = 480,
480 * ¾ = 360.
Q7: Find the missing letter in the sequence.
FAG, GAF, HAI, IAH, ____.
Options:
- JAI
- HAK
- HAL
- JAK
Answer: 4. JAK
Solution:
The middle letters are static, so concentrate on the first and third letters. The series involves an alphabetical order with a reversal of the letters. The first letters are in alphabetical order: F, G, H, I, J. The second and fourth segments are reversals of the first and third segments. The missing segment begins with a new letter.
Q8: Geologist: Earth Rocks::? :?
Options:
- Shining Body: Celestial Body
- Moon: Satellite
- Ibiza: Island
- Ornithologist: Bird
Answer: 4. Ornithologist: Bird
Solution:
As Geologist is a specialist of Earth Rocks similarly Ornithologist is a specialist of Birds.
Q9: Arrange the words given below in a meaningful sequence.
- Marriage
- Death
- Young
- Born
- Job
Options:
- 54312
- 45312
- 43512
- 43521
Answer: 4. 43512
Solution:
4, 3, 5, 1, 2
The correct sequence will be:
Born ---> Young ---> Job ---> Marriage ---> Death
The sequence is based on the life cycle of a person.
Q10: After 10 years, what will be the sum of the ages of Mahesh and Samantha?
- 10 years before, Mahesh was 5 years older than Samantha.
- At present, the ratio of their ages is 5: 6.
Options:
- If statement II alone is sufficient to answer the question
- If statement I alone is sufficient to answer the question
- If both the statements together are sufficient to answer the question
- If either statement I or statement II are sufficient to answer the question
- If both the statement are insufficient to answer the question
Answer: 3. If both statements together are sufficient to answer the question.
Solution:
10 years before, let the age of Mahesh = x then the age of Samantha = x – 10
At present, their age will be, Mahesh = x + 10 years, Samantha = x -10 + 10 = x years
In statement II, the ratio of x + 5 and x are given
Therefore, by combining both statements, we can conclude our answer.
Verbal Ability Questions with Answers:
Q11: During the world cup, the ball on the field certainly did ____ more than usual.
Options:
- bounced
- was bouncing
- bounce
- jumped
Answer: 3. bounce
Solution:
In simple past tense, we always use 'did' as an auxiliary verb. However, when 'did' is used in a sentence, the main verb following it will always be in the simple verb form (present tense form).
Q12: Shikha went to see __________ palmist yesterday for the first time.
Options:
- None of these
- A
- An
- The
Answer: 2. A
Solution:
Here a palmist can be any palmist, there is no specific palmist is mentioned, so, ‘a’ article will be used. Since we have used ‘for the first time’ it again informs us that Shikha didn’t know the palmist.
Q13: They never fail ______ die in a great cause.
Options:
- which
- whose
- who
- whom
Answer: 3. who
Solution:
'They' is the subject over here hence we use ‘who’.
Q14: The pair of shoes on the floor ____ mine. The shoe ___ made in Italy. The 300 dollars I spent on them ____ worth it.
Options:
- is was, was
- is, were, was
- are, were, were
- are, were, was
Answer: 2. is, were, was
Solution:
When we use the word ‘pair’ of something, the pair means one even if it has two objects in it. The word ‘pair’ is treated as singular so we use a singular verb with it.
In the second blank, we have removed the word ‘pair’ and the objects ‘shoes’ are treated individually, which gives us the plural form, so we use the plural verb.
However in the last blank, we are talking about an amount and according to rules, an amount is always considered singular.
Q15: With his ______ eyesight, Salman khan spotted a trio of deer on the hillside and he reduced the speed of his car to shoot the deer.
Options:
- inferior
- ductile
- keen
- conspirator
Answer: 3. keen
Solution:
Keen eyesight means eagerness.
Coding Test:
Following is the syllabus of the coding test:
- Syntax
- Logical and Algorithms
- Data Structures and Unions
- File System
- Operators
- Database Management Systems
- Networks and Connections
- Network layer protocols
- Network layer functions
- Presentation layer
- Application layer
- Physical layer
- Link layer
- Responsibilities of session layer
- Transport layer header
- Lowest layer
- Strings
- String input
- Vector of Strings or String vector
- String temp
- String void
- unsorted arrays
- Array Bool
- Temporary Array
- Subnetting, advantages of subnetting, and disadvantages of subnetting
- Subnet in Subnetting
- Mail Services
- Service Point Address
- File transfer access
- Feature File
- Header File
- Time complexity
- Shorter burst times
- Element Matches
- Key form
- Error control
- Flow control
- Nodes
- Node to Node transport
- Transport from one node to another node
- Network priority and Priority task
- Full-duplex transmission modes
- Half-duplex or full-duplex mode of transmission
- Legacy systems
- Non-relational or distributed databases
- Scheduling
- preemptive and non-preemptive scheduling algorithms
- Preemptive Scheduling
- non-preemptive scheduling
- Limited timeIN non-preemptive scheduling
- Shared dataNon-Preemptive scheduling
- Document-based, graph databases
- Sorting Algorithm
- Table employee database problem
Previous Year Questions with Answers for coding round
Q16: Write a program to reverse the characters in the individual strings.
Function Description:
Complete the reverseString function. It has the following parameter(s):
Constraints: 1 < len(stringValue) < 10^5.
Input Format For Custom Testing:
The first line contains a string, stringValue, denoting the reversed string.
CODE:
def reverseWord():
List = list(input().split(" "))
updatedList= [x[::-1] for x in List]
return str(' '.join(updatedList))
print(reverseWord())
ZGVmIHJldmVyc2VXb3JkKCk6CiAgTGlzdCA9IGxpc3QoaW5wdXQoKS5zcGxpdCgiICIpKQogIHVwZGF0ZWRMaXN0PSBbeFs6Oi0xXSBmb3IgeCBpbiBMaXN0XQogIHJldHVybiBzdHIoJyAnLmpvaW4odXBkYXRlZExpc3QpKQogICAKcHJpbnQocmV2ZXJzZVdvcmQoKSk=
OUTPUT:
the string is used
gnirts si desu
Explanation: We define a function that will reverse the words. We input the words into a List and then create another List that will input the words in a reverse manner. Then we print the updated list.
Q17: Problem Statement –
Abhijeet is one of those students who try to get his own money by part-time jobs in various places to fill up the expenses for buying books. He is not placed in one place, so what he does is he tries to allocate how much the book he needs will cost, and then work to earn that much money only. He works and then buys the book respectively. Sometimes he gets more money than he needs so the money is saved for the next book. Sometimes he doesn’t. At that time, if he has stored money from previous books, he can afford it, otherwise, he needs money from his parents.
Now His parents go to work and he can’t contact them for a day. You are his friend, and you have to find how much money minimum he can borrow from his parents so that he can buy all the books. He can Buy the book in any order.
Constraints:
- 1 <= N <= 10^3
- 1 <= EarnArray[i] <= 10^3
- 1 <= CostArray[i] <= 10^3
Input Format:
- The first line contains N.
- Second N lines contain The ith earning for the ith book.
- After that N lines contain The cost of the ith book.
Output Format: The minimum money he needs to cover the total expense.
Sample Input 1:
3
[3 4 2]
[5 3 4]
Sample Output 1:
3
CODE:
#include <bits/stdc++.h>
using namespace std;
int main()
{
int n, ans =0,sum=0;
cin>>n;
vector arr1(n),arr2(n);
for(int i=0;i<n;i++) cin>>arr2[i];
for(int i=0;i<n;i++) cin>>arr1[i];
for(int i=0;i<n;i++) arr2[i]-=arr1[i];
sort(arr2.begin(),arr2.end(),greater());
for(int i=0;i<n;i++)
{
sum+=arr2[i];
if(sum<0)
{ans+=abs(sum);sum=0;}
}
cout<<ans;
}
I2luY2x1ZGUgPGJpdHMvc3RkYysrLmg+CnVzaW5nIG5hbWVzcGFjZSBzdGQ7CmludCBtYWluKCkKewogICAgaW50IG4sIGFucyA9MCxzdW09MDsKICAgIGNpbj4+bjsKICAgIHZlY3RvcjxpbnQ+IGFycjEobiksYXJyMihuKTsKICAgIGZvcihpbnQgaT0wO2k8bjtpKyspIGNpbj4+YXJyMltpXTsKICAgIGZvcihpbnQgaT0wO2k8bjtpKyspIGNpbj4+YXJyMVtpXTsKICAgIGZvcihpbnQgaT0wO2k8bjtpKyspIGFycjJbaV0tPWFycjFbaV07CiAKICAgIHNvcnQoYXJyMi5iZWdpbigpLGFycjIuZW5kKCksZ3JlYXRlcjxpbnQ+KCkpOwogICAgZm9yKGludCBpPTA7aTxuO2krKykKICAgIHsKICAgICAgICBzdW0rPWFycjJbaV07CiAgICAgICAgaWYoc3VtPDApCiAgICAgICAge2Fucys9YWJzKHN1bSk7c3VtPTA7fQogICAgfQogICAgY291dDw8YW5zOwp9
OUTPUT:
3
4 3 2
3 5 3
2
Explanation:
At first, he buys the 2nd book, which costs 3 rupees, so he saves 1 rupee. Then he buys the 1st book, which takes 2 rupees more. So he spends his stored 1 rupee and hence he needs 1 rupee more. Then he buys the last book.
Q18: Problem Statement-
You are given an integer array containing the IDs of a product. Write a program to calculate the number of repetitions of the given ID in the array and return the count.
Complete the getCount function in the editor below. It has the following parameter(s):
Return: The function must return an integer, denoting the count for all the recurrence of the given product ID in the array.
Constraints:
- 1 < n < 10^5
- 1 < arr[i] < 10^5
- 1 < id < 10^5
Input Format For Custom Testing:
The first line contains an integer, n, denoting the number of elements in arr.
Each line i of the n subsequent lines (where 0 < i < n) contains an integer describing the ids in the array.
The next line contains an integer, id, denoting the id to be found.
Sample test cases:
CODE:
def getCount():
l=[]
size=int(input())
for i in range(size):
c=int(input())
l.append(c)
ID=int(input())
return l.count(ID)
print(getCount())
ZGVmIGdldENvdW50KCk6ICAgCiAgbD1bXSAgIAogIHNpemU9aW50KGlucHV0KCkpICAgCiAgZm9yIGkgaW4gcmFuZ2Uoc2l6ZSk6ICAgICAgIAogICAgYz1pbnQoaW5wdXQoKSkgICAgICAgCiAgICBsLmFwcGVuZChjKSAgIAogIElEPWludChpbnB1dCgpKSAgIAogIHJldHVybiBsLmNvdW50KElEKSAgIApwcmludChnZXRDb3VudCgpKQ==
OUTPUT:
6
12
1
13
12
14
12
12
3
Q19: Problem Statement:
An automobile company manufactures both a two-wheeler (TW) and a four-wheeler (FW). A company manager wants to make the production of both types of the vehicle according to the given data below:
- 1st data, Total number of vehicles (two-wheeler + four-wheeler)=v
- 2nd data, Total number of wheels = W
The task is to find how many two-wheelers as well as four-wheelers need to manufacture as per the given data.
Example :
Input :
- 200 -> Value of V
- 540 -> Value of W
Output :
- TW =130 FW=70
Explanation:
130+70 = 200 vehicles
(704)+(1302)= 540 wheels
Constraints :
- 2<=W
- W%2=0
- V<W
Print “INVALID INPUT” , if inputs did not meet the constraints.
The input format for testing
The candidate has to write the code to accept two positive numbers separated by a new line.
- First Input line – Accept value of V.
- Second Input line- Accept value for W.
The output format for testing
- Written program code should generate two outputs, each separated by a single space character(see the example)
- Additional messages in the output will result in the failure of the test case.
import java.util.*;
public class Main
{
public static void main(String[] args)
{
Scanner sc=new Scanner(System.in);
int v=sc.nextInt();
int w=sc.nextInt();
float res=((4*v)-w)/2;
if(w>=2 && (w%2==0) && v
aW1wb3J0IGphdmEudXRpbC4qOwpwdWJsaWMgY2xhc3MgTWFpbgp7CiAgICBwdWJsaWMgc3RhdGljIHZvaWQgbWFpbihTdHJpbmdbXSBhcmdzKQogICAgewogICAgICAgICAgICAgU2Nhbm5lciBzYz1uZXcgU2Nhbm5lcihTeXN0ZW0uaW4pOwogICAgICAgICAgICAgaW50IHY9c2MubmV4dEludCgpOwogICAgICAgICAgICAgaW50IHc9c2MubmV4dEludCgpOwogICAgICAgICAgICAgZmxvYXQgcmVzPSgoNCp2KS13KS8yOwogICAgICAgICAgICAgaWYodz49MiAmJiAodyUyPT0wKSAmJiB2PHcgKSAKICAgICAgICAgICAgICAgU3lzdGVtLm91dC5wcmludGxuKCJUVz0gIisoaW50KShyZXMpKyIgRlc9ICIrKGludCkodi1yZXMpKTsKICAgICAgICAgICAgIGVsc2UKICAgICAgICAgICAgICAgIFN5c3RlbS5vdXQucHJpbnRsbigiSU5WQUxJRCBJTlBVVCIpOwoKICAgICAgICAgICAgICBzYy5jbG9zZSgpOwogICAgfQp9
OUTPUT:
200
540
TW= 130 FW= 70
Q20: Problem Statement:
Given a string S(input consisting) of ‘’ and ‘#’. The length of the string is variable. The task is to find the minimum number of ‘’ or ‘#’ to make it a valid string. The string is considered valid if the number of ‘’ and ‘#’ are equal. The ‘’ and ‘#’ can be at any position in the string.
Note: The output will be a positive or negative integer based on the number of ‘*’ and ‘#’ in the input string.
- (*>#): positive integer
- (#>*): negative integer
- (#=*): 0
Example 1:
Input 1:
- ###*** -> Value of S
Output :
- 0 → number of * and # are equal
CODE:
#include <bits/stdc++.h>
using namespace std;
int main()
{
string s;
int a=0,b=0;
getline(cin,s);
for(auto i:s)
if(i=='#') a++;
else if(i=='*') b++;
cout<<b-a;
}
I2luY2x1ZGUgPGJpdHMvc3RkYysrLmg+CnVzaW5nIG5hbWVzcGFjZSBzdGQ7CiAKaW50IG1haW4oKQp7CiAgICBzdHJpbmcgczsKICAgIGludCBhPTAsYj0wOwogICAgZ2V0bGluZShjaW4scyk7CiAgICBmb3IoYXV0byBpOnMpCiAgICBpZihpPT0nIycpIGErKzsKICAgIGVsc2UgaWYoaT09JyonKSBiKys7CiAgICBjb3V0PDxiLWE7Cn0=
OUTPUT:
##***
1
##**#
-1
Technical Questions:
Candidates' understanding of programming languages, computer networks, and their approach to software development, code implementation, and compilation errors will be checked. Questions on C, C++, and Java might also be asked.
Previous Year/Sample Questions:
Q21: Explain HTTP and HTTPS protocols.
These are network layer protocols.
- HTTP: HTTP is a Hypertext Transfer Protocol which is a set of rules and standards that control how information can be transmitted across the Internet between web browsers and servers.
- HTTPS: HTTPS is Hyper Text Transfer Protocol Secure which is a highly advanced and secure HTTP version and it uses port 443 for the communication of data. Encrypting all communication using SSL, helps in secure transactions.
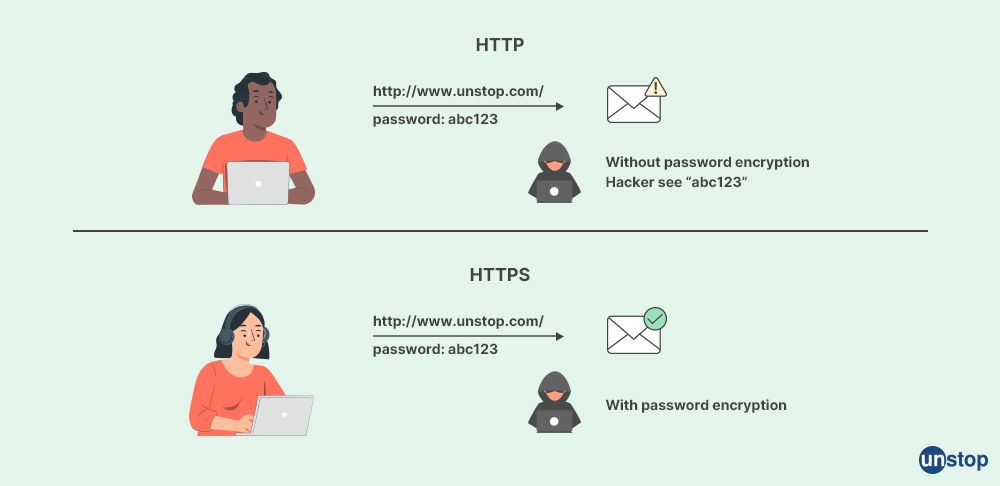
HTTP (Hypertext Transfer Protocol) and HTTPS (Hypertext Transfer Protocol Secure) are both protocols used for transmitting data over the internet. However, they have some differences:
-
Security: The main difference between HTTP and HTTPS is that HTTPS is a secure version of HTTP. HTTPS uses encryption to protect the data being transmitted, making it more secure against interception and tampering. HTTP does not provide any encryption, making it more vulnerable to attacks.
-
Port: HTTP uses port 80, while HTTPS uses port 443.
-
Certificate: HTTPS requires an SSL/TLS certificate, which is used to encrypt the data being transmitted. HTTP does not require a certificate.
-
Speed: Because HTTPS adds encryption and decryption overhead, it can be slower than HTTP.
-
Use case: HTTP is commonly used for transmitting non-sensitive data such as text, images, and videos, while HTTPS is used for transmitting sensitive data such as passwords, credit card numbers, and other personal information.
In general, HTTPS is a more secure and reliable protocol than HTTP, making it the preferred choice for transmitting sensitive data over the Internet.
Q22: Differentiate between interface and abstract class in the context of Java.
Answer:
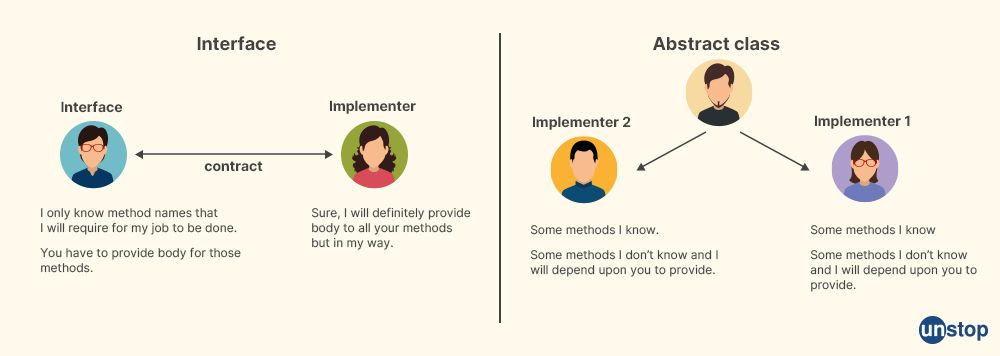
In the context of Java, both interfaces and abstract classes are used to achieve abstraction and define contracts for implementing classes, but they have some differences:
-
Definition: An interface is a collection of abstract methods that define a set of actions that an implementing class must support, while an abstract class is a class that cannot be instantiated and may contain one or more abstract methods, as well as concrete methods.
-
Method implementation: An interface cannot implement any methods, only declare them, while an abstract class can implement both abstract and concrete methods.
-
Inheritance: An interface can be implemented by multiple classes, while an abstract class can only be extended by one class. However, a class can implement multiple interfaces.
-
Constructor: An interface cannot have a constructor, while an abstract class can have a constructor that is called when a concrete subclass is instantiated.
-
Access modifiers: All methods of an interface are implicitly public, while abstract class methods can have any access modifier.
In general, if you want to define a contract for a group of related classes, you can use an interface. If you want to provide a partial implementation of a class and force its subclasses to provide the remaining implementation, you can use an abstract class.
Q23: Write a program to calculate the Least Common Multiple (LCM) of two numbers.
Example :
Input :a = 10, b =15
Output :30
a = 5, b =7
Output :35
Answer: First, explain your approach, then dive into coding.
Approach:
Let us assume the two numbers are a and b. Then, the two numbers have the following relationship:
a * b = LCM(a, b) * GCD(a, b)
or,
LCM(a, b) = (a * b) / GCD(a, b)
Let us take an example to understand better.
For a = 10 and b = 15, a * b = 150, LCM(10, 15) = 30, GCD(10, 15) = 5. So, a * b = LCM(a, b) * GCD(a, b).
Code :
CODE:
#include
using namespace std;
//Function to find the greatest common divisor of the two numbers
int findGCD(int a,int b)
{
if (b == 0)
return a;
return findGCD(b, a % b);
}
// Function to return LCM of two numbers
int findLCM(int a, int b)
{
return (a * b) / findGCD(a, b);
}
int main()
{
int a = 17, b = 20;
cout <<"The Least Common Multiple of the two numbers " << a << " and " << b << " is : " << findLCM(a, b);
return 0;
}
I2luY2x1ZGUgPGlvc3RyZWFtPgp1c2luZyBuYW1lc3BhY2Ugc3RkOwogCi8vRnVuY3Rpb24gdG8gZmluZCB0aGUgZ3JlYXRlc3QgY29tbW9uIGRpdmlzb3Igb2YgdGhlIHR3byBudW1iZXJzCmludCBmaW5kR0NEKGludCBhLGludCBiKQp7CiAgaWYgKGIgPT0gMCkKICAgIHJldHVybiBhOwogIHJldHVybiBmaW5kR0NEKGIsIGEgJSBiKTsKfQogCi8vIEZ1bmN0aW9uIHRvIHJldHVybiBMQ00gb2YgdHdvIG51bWJlcnMKaW50IGZpbmRMQ00oaW50IGEsIGludCBiKQp7CiAgICByZXR1cm4gKGEgKiBiKSAvIGZpbmRHQ0QoYSwgYik7Cn0KICAKaW50IG1haW4oKQp7CiAgICBpbnQgYSA9IDE3LCBiID0gMjA7CiAgICBjb3V0IDw8IlRoZSBMZWFzdCBDb21tb24gTXVsdGlwbGUgb2YgdGhlIHR3byBudW1iZXJzICIgPDwgYSA8PCAiIGFuZCAiIDw8IGIgPDwgIiBpcyA6ICIgPDwgZmluZExDTShhLCBiKTsKICAgIHJldHVybiAwOwp9
OUTPUT:
The Least Common Multiple of the two numbers 17 and 20 is : 340
Here's a Python program to calculate the LCM of two numbers using the formula LCM = (a * b) / GCD(a, b), where GCD is the greatest common divisor of a and b:
def gcd(a, b):
if b == 0:
return a
else:
return gcd(b, a % b)
def lcm(a, b):
return (a * b) / gcd(a, b)
a = int(input("Enter the first number: "))
b = int(input("Enter the second number: "))
print("LCM of", a, "and", b, "is", lcm(a, b))
ZGVmIGdjZChhLCBiKToKaWYgYiA9PSAwOgpyZXR1cm4gYQplbHNlOgpyZXR1cm4gZ2NkKGIsIGEgJSBiKQoKZGVmIGxjbShhLCBiKToKcmV0dXJuIChhICogYikgLyBnY2QoYSwgYikKCmEgPSBpbnQoaW5wdXQoIkVudGVyIHRoZSBmaXJzdCBudW1iZXI6ICIpKQpiID0gaW50KGlucHV0KCJFbnRlciB0aGUgc2Vjb25kIG51bWJlcjogIikpCgpwcmludCgiTENNIG9mIiwgYSwgImFuZCIsIGIsICJpcyIsIGxjbShhLCBiKSk=
Explanation: In this program, we first define a function gcd to calculate the greatest common divisor of two numbers using the Euclidean algorithm. We then define a function lcm to calculate the LCM using the formula mentioned above. Finally, we take input from the user for two numbers a and b, and print out the LCM using the lcm function.
Q24: What do you understand by super key, candidate key, primary key, and foreign key in the context of database management systems?
In the context of database management systems, the following terms have specific meanings:
-
Super key: A super key is a set of one or more attributes that can be used to uniquely identify each record in a table. It can contain more attributes than are required to uniquely identify the record, and it can include attributes that are not necessarily unique.
-
Candidate key: A candidate key is a minimal super key - that is, a set of one or more attributes that uniquely identify each record in a table, and cannot be further reduced without losing uniqueness. In other words, it is a subset of the super key that uniquely identifies each record.
-
Primary key: A primary key is a candidate key that has been selected as the main key for a table. It is used to uniquely identify each record in the table and to enforce data integrity. A table can have only one primary key, and it cannot contain NULL values.
-
Foreign key: A foreign key is an attribute or set of attributes in one table that refers to the primary key of another table. It is used to establish a relationship between the two tables, enabling data to be linked and integrated across tables.
Overall, these terms are important concepts in database design and are used to establish relationships and enforce data integrity between tables.
Q25: What are the different types of SQL commands?
SQL (Structured Query Language) is a domain-specific language used for managing data in relational database management systems (RDBMS). There are several types of SQL commands, which are:
-
Data Definition Language (DDL) commands: These commands are used to define, alter, and delete database objects like tables, indexes, views, and stored procedures. Examples of DDL commands include CREATE, ALTER, DROP, TRUNCATE, and RENAME.
-
Data Manipulation Language (DML) commands: These commands are used to manipulate data stored in the database. Examples of DML commands include SELECT, INSERT, UPDATE, and DELETE.
-
Data Control Language (DCL) commands: These commands are used to control access to the database. Examples of DCL commands include GRANT and REVOKE.
-
Transaction Control Language (TCL) commands: These commands are used to manage transactions in the database. Examples of TCL commands include COMMIT, ROLLBACK, and SAVEPOINT.
Overall, SQL commands are designed to help users interact with and manipulate data in a database, enabling them to perform tasks such as creating, updating, and querying data.
Q26: Can we override the static method?
In object-oriented programming, a static method is a method that is associated with a class, rather than an instance of that class. It can be called without creating an instance of the class, and it operates on the class itself rather than on any specific object of the class.
Since static methods are associated with a class and not with any instance of that class, they cannot be overridden in the traditional sense. When a subclass defines a static method with the same name as a static method in its superclass, the subclass's method will simply hide the superclass's method. That is, the subclass's static method will be called instead of the superclass's static method when the method is called on the subclass.
However, it is still possible to achieve similar functionality to overriding a static method by using a technique known as method hiding. Method hiding involves defining a static method with the same name as a static method in a superclass in a subclass. When this is done, the subclass's static method hides the superclass's static method when called on an instance of the subclass.
Here's an example in Python:
class Parent:
@staticmethod
def my_static_method():
print("Parent's static method")
class Child(Parent):
@staticmethod
def my_static_method():
print("Child's static method")
Parent.my_static_method() # output: Parent's static method
Child.my_static_method() # output: Child's static method
Y2xhc3MgUGFyZW50Og0KQHN0YXRpY21ldGhvZA0KZGVmIG15X3N0YXRpY19tZXRob2QoKToNCnByaW50KCJQYXJlbnQncyBzdGF0aWMgbWV0aG9kIikNCg0KY2xhc3MgQ2hpbGQoUGFyZW50KToNCkBzdGF0aWNtZXRob2QNCmRlZiBteV9zdGF0aWNfbWV0aG9kKCk6DQpwcmludCgiQ2hpbGQncyBzdGF0aWMgbWV0aG9kIikNCg0KUGFyZW50Lm15X3N0YXRpY19tZXRob2QoKSAjIG91dHB1dDogUGFyZW50J3Mgc3RhdGljIG1ldGhvZA0KQ2hpbGQubXlfc3RhdGljX21ldGhvZCgpICMgb3V0cHV0OiBDaGlsZCdzIHN0YXRpYyBtZXRob2Q=
Q27: What do you understand by cloud computing?
Cloud computing is a technology that enables on-demand access to computing resources such as servers, storage, applications, and services over the Internet. In cloud computing, these resources are made available to users through a network of remote servers hosted on the internet, instead of being stored and managed on local computers or on-premises servers.
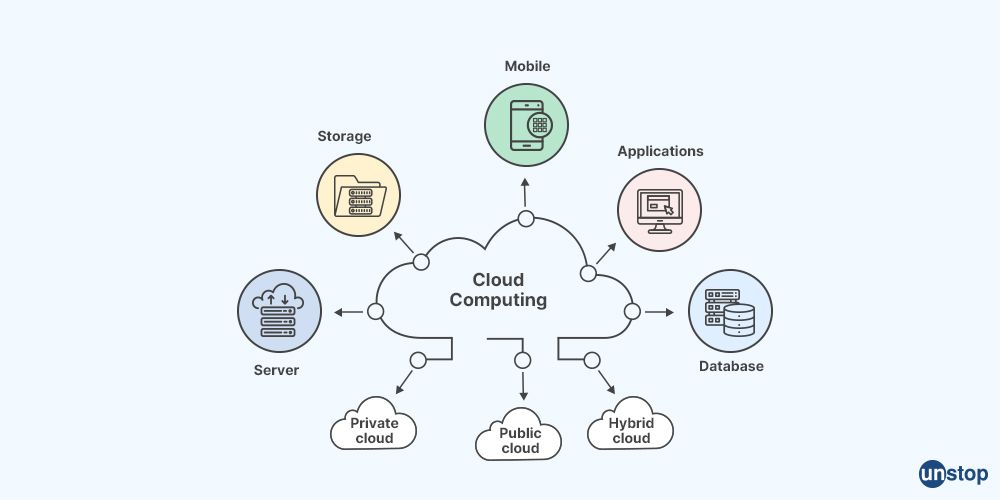
The cloud computing model provides a flexible, scalable, and cost-effective way to access computing resources, allowing users to pay for only the resources they need and use, without having to invest in and maintain their own physical infrastructure. Cloud computing services are typically provided by third-party vendors, who manage and maintain the underlying hardware, software, and network infrastructure, while users access the services through a web browser or other client application.
Q28: What is a virtual function?
In object-oriented programming, a virtual function is a function that is declared in a base class and is meant to be overridden (redefined) by derived classes. When a virtual function is called on an object of the derived class, the derived class's implementation of the function is called instead of the base class's implementation.
Virtual functions allow for polymorphism, which is the ability of objects of different types to be treated as if they are of the same type. This enables code to be written that works with objects at a higher level of abstraction, without knowing the specific type of object being used.
Q29: What does IP Address mean in networking?
In computer networking, an IP address (Internet Protocol address) is a unique numerical identifier assigned to each device that is connected to a computer network. An IP address is used to identify and communicate with other devices on the network.
There are two versions of IP addresses in use today: IP version 4 (IPv4) and IP version 6 (IPv6). An IPv4 address consists of 32 bits, usually represented as four decimal numbers separated by dots, such as 192.168.0.1. An IPv6 address, on the other hand, consists of 128 bits, usually represented as eight groups of four hexadecimal digits separated by colons, such as 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
IP addresses are assigned to devices by the network administrator or Internet Service Provider (ISP). Each device on the network must have a unique IP address, which allows it to send and receive data packets on the network. IP addresses can be static, meaning they are assigned to a device permanently, or dynamic, meaning they are assigned to a device for a limited time period and can change over time.
Q30: What is the difference between abstraction and interface?
Abstraction is the process of hiding implementation details and exposing only the necessary information to the user. It is a way of simplifying complex systems by breaking them down into smaller, more manageable parts. In object-oriented programming, abstraction is achieved through the use of abstract classes and methods.
An interface, on the other hand, is a contract that specifies a set of methods that a class must implement if it wants to adhere to the interface. An interface contains only method declarations and constants, but no implementation. In other words, an interface defines a set of methods that a class must provide, but it does not provide any implementation details for those methods.
One key difference between abstraction and interface is that abstraction can contain both abstract and concrete methods, while an interface can only contain method declarations. Another difference is that an abstract class can provide default implementations for some or all of its methods, while an interface cannot provide any implementation.
Q31: Difference between hashmap and hashtable?
Both HashMap and Hashtable are data structures in Java that store key-value pairs, but there are some key differences between hashmap and hashtable.
-
Synchronization:
Hashtableis synchronized, meaning that it is thread-safe and can be accessed by multiple threads at the same time without causing data corruption or race conditions.HashMapis not synchronized, and accessing it concurrently from multiple threads can result in unpredictable behavior or data corruption. If you need a thread-safe version ofHashMap, you can useConcurrentHashMap. -
Null values:
Hashtabledoes not allow null values for both keys and values, whereasHashMapallows null values for both keys and values. If you try to add a null value to aHashtable, aNullPointerExceptionwill be thrown. -
Iteration: The iteration order of elements in
HashMapis not guaranteed, and can change over time if the map is modified.Hashtablealso does not guarantee the order of iteration, but its iterator is fail-safe, meaning that it will not throw aConcurrentModificationExceptionif the map is modified during iteration. -
Performance:
HashMapis generally faster thanHashtable, because it is not synchronized and does not have the overhead of synchronization. However, the difference in performance is usually negligible for small maps, andHashtablemay be a better choice for thread-safe operations in certain scenarios.
Q32: What is Inter-Network Communication?
Inter-network communication, also known as internetworking, is the process of connecting two or more networks together to enable communication between the devices and hosts on each network.
In today's world of interconnected networks, internetworking is essential for enabling communication between different devices, hosts, and networks. The internet, for example, is a vast collection of interconnected networks that allow devices and hosts to communicate with each other regardless of their location or network configuration.
Internetworking is achieved using a variety of technologies and protocols, including routers, switches, gateways, and protocols such as TCP/IP, which are used to facilitate communication between different devices on different networks.
Routers are the most important devices for internetworking, as they enable the transfer of data between different networks. They use routing protocols to exchange information with other routers on the network, allowing them to determine the best path for sending data to its intended destination.
Q33: Write a query in SQL to find the details of an employee having the nth highest salary from a given table Employee.
To find the details of an employee having the nth highest salary from a given table Employee in SQL, you can use the following query:
SELECT *
FROM Employee
WHERE Salary = (
SELECT DISTINCT Salary
FROM Employee
ORDER BY Salary DESC
LIMIT n-1, 1
);
U0VMRUNUICoKRlJPTSBFbXBsb3llZQpXSEVSRSBTYWxhcnkgPSAoClNFTEVDVCBESVNUSU5DVCBTYWxhcnkKRlJPTSBFbXBsb3llZQpPUkRFUiBCWSBTYWxhcnkgREVTQwpMSU1JVCBuLTEsIDEKKTs=
In this query, we use a subquery to find the nth highest salary from the table Employee. The subquery selects the unique salary values from the "Employee" table, orders them in descending order, and then selects the nth highest salary using the LIMIT clause.
The outer query then selects all the details of the employee(s) whose salary matches the nth highest salary found in the subquery, using the WHERE clause.
Note: Replace "n" with the actual value of the desired rank, e.g., if you want to find the details of the employee with the 3rd highest salary, replace "n" with 3.
Q34: What is the use of internal routers?
Internal routers, also known as interior routers or intra-domain routers, are network routers that operate within a single autonomous system (AS). An autonomous system is a collection of networked devices and hosts that are managed by a single organization and that share a common routing policy.
Internal routers are used to facilitate communication between the different subnets or networks within an autonomous system. They use interior gateway protocols (IGPs) such as OSPF (Open Shortest Path First), EIGRP (Enhanced Interior Gateway Routing Protocol), and RIP (Routing Information Protocol) to exchange routing information with other routers within the same autonomous system.
The primary use of internal routers is to enable efficient and optimized routing of data packets within a single autonomous system, ensuring that packets are delivered to their intended destinations quickly and reliably. They also provide fault tolerance and redundancy by maintaining multiple paths to reach a destination.
Q35: What are the advantages and disadvantages of subnetting?
Subnetting is a technique used in computer networking to divide a large network into smaller, more manageable sub-networks, or subnets. Subnetting has several advantages and disadvantages, which are outlined below:
Advantages:
-
Better Network Performance: Subnetting can improve network performance by reducing network traffic and congestion. By dividing a large network into smaller subnets, traffic is localized, and fewer devices need to process each network packet. This reduces the overall network load and improves performance.
-
Improved Security: Subnetting can improve network security by enabling network administrators to isolate sensitive data or devices on a separate subnet, making it more difficult for unauthorized users to access them.
-
Efficient Use of IP Addresses: Subnetting enables more efficient use of IP addresses by allowing network administrators to allocate IP addresses based on the actual number of devices on each subnet. This reduces the number of unused or wasted IP addresses on the network.
-
Easier Network Management: Subnetting can make network management easier by dividing a large network into smaller, more manageable subnets. This simplifies network configuration, troubleshooting, and maintenance.
Disadvantages:
-
Increased Complexity: Subnetting adds complexity to network design, configuration, and management. Network administrators must have a thorough understanding of subnetting concepts, IP addressing, and routing protocols to effectively manage a subnetted network.
-
Increased Administrative Overhead: Subnetting requires additional administrative overhead, such as monitoring network traffic, managing routing tables, and configuring security policies. This can increase the workload for network administrators.
-
Network Segmentation: Subnetting can lead to network segmentation, which can make it more difficult to share resources and collaborate across different subnets.To reach a Process in the case of a single network, only three steps are required: Source Host to Destination Network, Destination Network to Destination Host, and lastly Destination Host to Process. Subnetting, on the other hand, necessitates four phases for Inter-Network Communication. Source Host to Destination Network, Destination Network to appropriate Subnet, Subnet to Host, and lastly Host to Process are the steps. As a result, Time complexity rises. More time is necessary for communication or data transfer in the case of Subnet.
Q36: What is a sorting algorithm?
A sorting algorithm is a procedure that arranges a set of data in a specific order, typically in ascending or descending order. They are widely used in computer science and other fields where data needs to be organized for efficient processing.
There are many different sorting algorithms, each with its own strengths and weaknesses. Some common sorting algorithms include:
-
Bubble Sort: This is a simple sorting algorithm that repeatedly steps through the list to be sorted, compares each pair of adjacent items, and swaps them if they are in the wrong order. It has a time complexity of O(n^2), which makes it inefficient for large datasets.
-
Insertion Sort: This algorithm works by repeatedly taking an element from the unsorted portion of the list and inserting it into its correct position in the sorted portion. It has a time complexity of O(n^2) in the worst case, but can be more efficient than other algorithms for small datasets.
-
Quick Sort: This algorithm divides the dataset into smaller sub-datasets based on a "pivot" value, and then recursively sorts the sub-datasets. It has an average time complexity of O(n log n), making it efficient for large datasets.
-
Merge Sort: This algorithm divides the dataset into smaller sub-datasets, recursively sorts each sub-dataset, and then merges the sorted sub-datasets together. It has a time complexity of O(n log n) in the worst case.
Also Read: Understanding Time Complexity Of Algorithms In Detail
Q37: Explain the physical layer in networking.
The physical layer is the first layer of the OSI (Open Systems Interconnection) model and is responsible for the transmission and reception of unstructured raw data between a device and a physical transmission medium such as a wire, cable, or air.
The physical layer is responsible for defining the physical characteristics of the communication medium, such as the voltage levels, bit rate, encoding method, and other physical parameters. The physical layer establishes and maintains the physical connection between the devices, as well as the transmission medium used to send the data.
Some of the key functions of the physical layer include:
-
Data Encoding: The physical layer converts the digital data into a format suitable for transmission over the communication medium. Different encoding methods are used depending on the medium being used.
-
Data Transmission: The physical layer is responsible for transmitting the encoded data over the communication medium in the form of signals. The transmission method used can be analog or digital, and can include various modulation techniques.
-
Data Reception: The physical layer receives the signals from the communication medium and converts them back into digital data.
-
Signal Amplification: The physical layer may need to amplify the signals to overcome attenuation and other signal losses that can occur during transmission.
-
Signal Multiplexing: The physical layer may also be responsible for multiplexing multiple signals onto a single transmission medium to increase efficiency.
Overall, the physical layer is responsible for establishing and maintaining the physical communication link between devices, as well as ensuring that the data is transmitted in a reliable and efficient manner.
Q38: What are the basic principles to override a method?
In object-oriented programming, method overriding is the ability of a subclass to provide a different implementation of a method that is already defined in its superclass. To successfully override a method, the following basic principles should be followed:
-
Inheritance: The subclass must inherit from the superclass that contains the method to be overridden. This means that the subclass must be a direct or indirect subclass of the superclass.
-
Same method signature: The overridden method in the subclass must have the same method signature (entity name, return type, and parameters) as the method in the superclass. This ensures that the method in the subclass can be used in place of the method in the superclass.
-
Access modifiers: The access modifier of the overridden method in the subclass must not be more restrictive than the access modifier of the method in the superclass. For example, if the method in the superclass is public, the overridden method in the subclass must also be public or protected, but not private.
-
Method body: The overridden method in the subclass must provide a different implementation of the method than the method in the superclass. This means that the method body in the subclass should have different functionality from the method body in the superclass.
By following these principles, a subclass can override a method in its superclass and provide its own implementation of the method. This allows for greater flexibility and customization in object-oriented programming.
Q39: How to handle dynamic objects?
Handling dynamic objects depends on the programming language you are using and the specific context of your program. However, in general, here are some guidelines that can be helpful:
-
Understand the dynamic behavior: Dynamic objects are those that can change their structure and behavior at runtime. To handle dynamic objects, you need to understand how they change and when these changes happen.
-
Use appropriate data structures: You need to choose data structures that are suitable for dynamic objects. For example, if you are dealing with dynamic lists or arrays, you might use a linked list or dynamic array, respectively.
-
Utilize appropriate programming constructs: You may need to use appropriate programming constructs like loops or recursion to handle dynamic objects. These individual contributors constructs can help you iterate through the elements of the dynamic object and perform operations on them.
-
Implement error handling: Since dynamic objects can change their organisational structure and behavior at runtime, it's important to implement error handling mechanisms that can handle unexpected changes. This can help you avoid crashes and errors in your program.
-
Test and debug: Finally, it's important to test and debug your code thoroughly when handling dynamic objects. You may encounter unexpected behaviors or errors, and it's important to identify and fix these issues before deploying your code.
Overall, handling dynamic objects can be challenging, but by following these guidelines and using appropriate tools and techniques, you can effectively manage dynamic behavior in your programs.
Q40: What is a manual tester?
A manual tester is a software quality assurance professional who performs testing on software applications or systems manually, without the aid of automation tools. Manual testers follow predefined test cases or test scenarios, execute them step-by-step, and report any defects or issues they encounter during testing.
Manual testing is a crucial part of the software development life cycle (SDLC) and involves testing the software for defects, user experience, usability, and other functional and non-functional aspects. Manual testers may also be involved in identifying test scenarios and creating test cases, documenting test results, and collaborating with developers to resolve defects.
Q41: Given two unsorted arrays. Check if the second array is a subarray of the first array.
We use two pointers to explore both the array and the subarray. We maintain the pointer of array arr2[] and increase the pointer of both arrays if any element of arr1[] matches the first element of arr2[], otherwise set the pointer of arr1 to the next element of the previous starting point and reset the pointer of arr2 to 0. If all of arr2's elements match, print True; otherwise, print False.
#include
#include
using namespace std;
bool isSubarray(vector& arr1, vector& arr2) {
for (int i = 0; i <= arr1.size() - arr2.size(); i++) {
bool found = true;
for (int j = 0; j < arr2.size(); j++) {
if (arr1[i+j] != arr2[j]) {
found = false;
break;
}
}
if (found) {
return true;
}
}
return false;
}
int main() {
vector arr1 = {3, 7, 5, 9, 2, 8, 10};
vector arr2 = {5, 9, 2};
if (isSubarray(arr1, arr2)) {
cout << "arr2
I2luY2x1ZGUgPGlvc3RyZWFtPgojaW5jbHVkZSA8dmVjdG9yPgoKdXNpbmcgbmFtZXNwYWNlIHN0ZDsKCmJvb2wgaXNTdWJhcnJheSh2ZWN0b3I8aW50PiYgYXJyMSwgdmVjdG9yPGludD4mIGFycjIpIHsKZm9yIChpbnQgaSA9IDA7IGkgPD0gYXJyMS5zaXplKCkgLSBhcnIyLnNpemUoKTsgaSsrKSB7CmJvb2wgZm91bmQgPSB0cnVlOwpmb3IgKGludCBqID0gMDsgaiA8IGFycjIuc2l6ZSgpOyBqKyspIHsKaWYgKGFycjFbaStqXSAhPSBhcnIyW2pdKSB7CmZvdW5kID0gZmFsc2U7CmJyZWFrOwp9Cn0KaWYgKGZvdW5kKSB7CnJldHVybiB0cnVlOwp9Cn0KcmV0dXJuIGZhbHNlOwp9CgppbnQgbWFpbigpIHsKdmVjdG9yPGludD4gYXJyMSA9IHszLCA3LCA1LCA5LCAyLCA4LCAxMH07CnZlY3RvcjxpbnQ+IGFycjIgPSB7NSwgOSwgMn07CmlmIChpc1N1YmFycmF5KGFycjEsIGFycjIpKSB7CmNvdXQgPDwgImFycjI=
Q42: Explain the Open Systems Interconnection (OSI) model in the context of computer networks.
The Open Systems Interconnection (OSI) model is a conceptual model that describes how data is transferred over a network. It is a layered model that is designed to enable communication between different computer systems regardless of their underlying architecture, operating system, or physical transmission medium.
The OSI model consists of seven layers, each of which defines a specific set of functions that are performed on data as it passes through the network. The layers are:
-
Physical Layer: Physical layer defines the physical transmission medium used to transmit data, such as copper wires, fiber-optic cables, or wireless signals. The physical layer also defines the electrical and physical specifications of the transmission medium.
-
Data Link Layer: This layer provides a reliable means of transmitting data across the physical transmission medium by adding error checking and flow control mechanisms. It is responsible for framing data into packets, adding error detection and correction codes, and managing the flow of data between devices. After producing frames, the Data link layer adds the sender and/or receiver's physical addresses (MAC addresses) to the header of each frame.
-
Network Layer: This layer is responsible for routing data packets between different networks. It determines the most efficient path for data to travel through the network based on the network topology and the destination address of the packet.
-
Transport Layer: This layer provides end-to-end communication between applications running on different devices. It ensures that data is delivered reliably and in the correct order, and provides flow control mechanisms to prevent the sender from overwhelming the receiver. (Read more about transport layer protocols)
-
Session Layer: This layer establishes, manages, and terminates communication sessions between devices. It allows applications to establish and maintain ongoing conversations and provides mechanisms for recovery from communication failures.
-
Presentation Layer: This layer is responsible for converting data between different formats and character sets, and for encrypting and decrypting data as required for secure communication.
-
Application Layer: This layer provides services and interfaces to applications that enable them to communicate with other preferable choices for applications over the network.
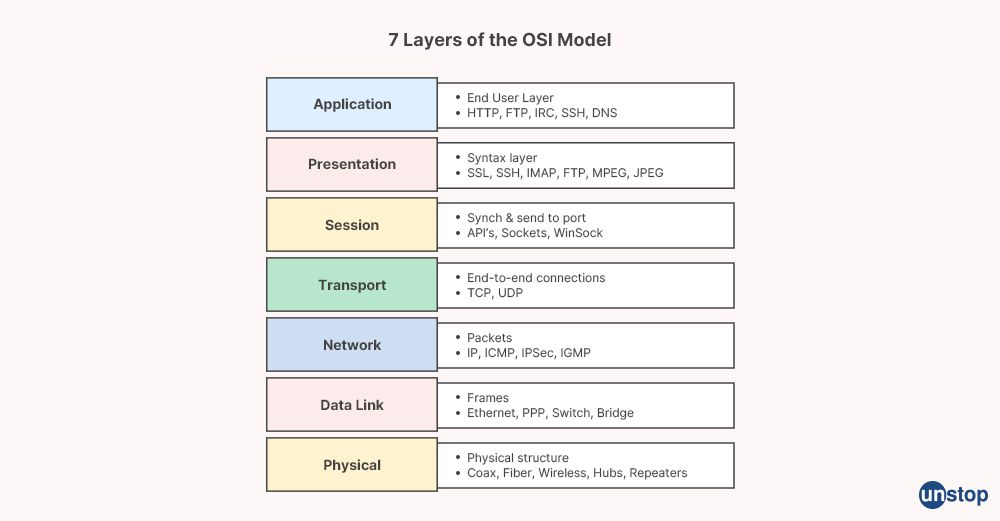
The OSI model provides a common framework for network communication, allowing hardware and software from different vendors to interoperate seamlessly. It also facilitates the development of standardized network protocols and allows network designers to focus on specific layers of the model without having to consider the entire network infrastructure.
Q43: Differentiate between preemptive and non-preemptive scheduling algorithms
In computer operating systems, scheduling algorithms determine how tasks or processes are scheduled on the CPU. Preemptive and non-preemptive scheduling algorithms are two common types of scheduling algorithms, which differ in how they handle the interruption of running tasks.
Here's the difference between preemptive and non-preemptive scheduling algorithms:
-
Preemptive Scheduling: In preemptive scheduling, the CPU can be taken away from a running process or task even if it has not completed its execution. This means that a higher-priority process can interrupt a lower-priority process, causing it to temporarily stop executing so that the higher-priority process can run. Preemptive scheduling is more responsive to changes in system priorities, but it can cause more overhead and may be less efficient.
-
Non-Preemptive Scheduling: In non-preemptive scheduling, the CPU is not taken away from a running process until it has completed its execution or it voluntarily releases the CPU. This means that once a process has been allocated the CPU, it keeps it until it finishes its execution, even if a higher-priority process becomes available. Non-preemptive scheduling is more predictable and can be more efficient than preemptive scheduling, but it may not respond as quickly to changes in system priorities.
To summarize, preemptive scheduling allows for the possibility of interruption of running tasks, while non-preemptive scheduling does not. Preemptive scheduling can provide better responsiveness to changes in system priorities, but it can also cause more overhead. Non-preemptive scheduling can be more efficient but may not respond as quickly to changes in priorities.
Unlock endless job and internship opportunities on Unstop!
HR Interview Round
After the first three rounds, you advance to the final round i.e.the HR round.
To help you crack the actual interview, we have gathered some of the most frequently asked management interview questions and answers.
Sample Questions:
Q26: Why are you interested in this position?
Model Answer: I have successfully handled these responsibilities in my past roles, and am sure that I can apply the acquired skills in this role and further my career. Also, working with a firm that offers a good learning ground and great professional exposure is a dream job for me.
Q27: Tell me about an incident in your past when you handled confidential information.
Model Answer: In my past role as manager, I had to handle confidential information of my team members on a regular basis. Precaution needed to be exercised and any fault would have been catastrophic. So I accessed the information only when needed and never shared it with unauthorized people.
Q28: How will you manage work pressure?
Model Answer: I prioritize my work based on deadlines. This way I minimized work pressure. (Read More)
Q29: Are you comfortable with rotational shifts?
Model Answer: Yes, I am comfortable with rotational shifts. OR No, I won't be very comfortable. I have a strict schedule, and working in rotational shifts might hamper my performance. However, I would love to be guided in this regard.
Q30: Are you a team player?
Model Answer: Yes, I am a team player. During our summer internship at XYZ Enterprises, my friends and I worked together on a project despite having different character traits. I worked in tandem and contributed wholeheartedly.
Also Read: How To Answer 'What Does Teamwork Mean To You?' In Job Interview
About Mindtree
Mindtree Consulting Private Limited was founded by ten IT professionals in 1999. In 2019, Larsen & Toubro (L&T), one of the largest conglomerates in India, took over control of Mindtree.
Mindtree is involved in multiple IT services like App Development and Maintenance, Digital Services, Data Analytics, Business Process Management, Accounting systems, Enterprise Application Integration and Services, Engineering R&D, Testing, and Infrastructure Management Services and offers enriching opportunities for young professionals.
Suggested Reads:
- 64 Toughest Interview Questions For Job (With 17+ Prep Resources)
- Answering 'How Do You Prioritize Your Work?' During Job Interview
- Guide To Answer- "What Is Your Greatest Strength?" (Samples Inside)
- Top 35 Interview Questions For Freshers With Answers
- Know How You Can Negotiate Your Salary Well (With CTC Explained In Simple Terms)
As a biotechnologist-turned-writer, I love turning complex ideas into meaningful stories that inform and inspire. Outside of writing, I enjoy cooking, reading, and travelling, each giving me fresh perspectives and inspiration for my work.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter
Blogs you need to hog!

This Is My First Hackathon, How Should I Prepare? (Tips & Hackathon Questions Inside)

10 Best C++ IDEs That Developers Mention The Most!

Advantages and Disadvantages of Cloud Computing That You Should Know!










Comments
Add comment