- TCS Technical Interview Questions & Answers
- TCS Managerial Interview Questions & Answers
- TCS HR Interview Questions & Answers
- Overview of Cognizant Recruitment Process
- Cognizant Interview Questions: Technical
- Cognizant Interview Questions: HR Round
- Overview of Wipro Technologies Recruitment Rounds
- Wipro Interview Questions
- Technical Round
- HR Round
- Online Assessment Sample Questions
- Frequently Asked Questions
- Overview of Google Recruitment Process
- Google Interview Questions: Technical
- Google Interview Questions: HR round
- Interview Preparation Tips
- About Google
- Deloitte Technical Interview Questions
- Deloitte HR Interview Questions
- Deloitte Recruitment Process
- Technical Interview Questions and Answers
- Level 1 difficulty
- Level 2 difficulty
- Level 3 difficulty
- Behavioral Questions
- Eligibility Criteria for Mindtree Recruitment
- Mindtree Recruitment Process: Rounds Overview
- Skills required to crack Mindtree interview rounds
- Mindtree Recruitment Rounds: Sample Questions
- About Mindtree
- Preparing for Microsoft interview questions
- Microsoft technical interview questions
- Microsoft behavioural interview questions
- Aptitude Interview Questions
- Technical Interview Questions
- Easy
- Intermediate
- Hard
- HR Interview Questions
- Eligibility criteria
- Recruitment rounds & assessments
- Tech Mahindra interview questions - Technical round
- Tech Mahindra interview questions - HR round
- Hiring process at Mphasis
- Mphasis technical interview questions
- Mphasis HR interview questions
- About Mphasis
- Technical interview questions
- HR interview questions
- Recruitment process
- About Virtusa
- Goldman Sachs Interview Process
- Technical Questions for Goldman Sachs Interview
- Sample HR Question for Goldman Sachs Interview
- About Goldman Sachs
- Nagarro Recruitment Process
- Nagarro HR Interview Questions
- Nagarro Aptitude Test Questions
- Nagarro Technical Test Questions
- About Nagarro
- PwC Recruitment Process
- PwC Technical Interview Questions: Freshers and Experienced
- PwC Interview Questions for HR Rounds
- PwC Interview Preparation
- Frequently Asked Questions
- EY Technical Interview Questions (2023)
- EY Interview Questions for HR Round
- About EY
- Morgan Stanley Recruitment Process
- HR Questions for Morgan Stanley Interview
- HR Questions for Morgan Stanley Interview
- About Morgan Stanley
- Recruitment Process at Flipkart
- Technical Flipkart Interview Questions
- Code-Based Flipkart Interview Questions
- Sample Flipkart Interview Questions- HR Round
- Conclusion
- FAQs
- Recruitment Process at Paytm
- Technical Interview Questions for Paytm Interview
- HR Sample Questions for Paytm Interview
- About Paytm
- Most Probable Accenture Interview Questions
- Accenture Technical Interview Questions
- Accenture HR Interview Questions
- Amazon Recruitment Process
- Amazon Interview Rounds
- Common Amazon Interview Questions
- Amazon Interview Questions: Behavioral-based Questions
- Amazon Interview Questions: Leadership Principles
- Company-specific Amazon Interview Questions
- 43 Top Technical/ Coding Amazon Interview Questions
- Juspay Recruitment: Stages and Timeline
- Juspay Interview Questions and Answers
- How to prepare for Juspay interview questions
- Prepare for the Juspay Interview: Stages and Timeline
- Frequently Asked Questions
- Adobe Interview Questions - Technical
- Adobe Interview Questions - HR
- Recruitment Process at Adobe
- About Adobe
- Cisco technical interview questions
- Sample HR interview questions
- The recruitment process at Cisco
- About Cisco
- JP Morgan interview questions (Technical round)
- JP Morgan interview questions HR round)
- Recruitment process at JP Morgan
- About JP Morgan
- Wipro Elite NTH: Selection Process
- Wipro Elite NTH Technical Interview Questions
- Wipro Elite NTH Interview Round- HR Questions
- BYJU's BDA Interview Questions
- BYJU's SDE Interview Questions
- BYJU's HR Round Interview Questions
- A Quick Overview of the KPMG Recruitment Process
- Technical Questions for KPMG Interview
- HR Questions for KPMG Interview
- About KPMG
- DXC Technology Interview Process
- DCX Technical Interview Questions
- Sample HR Questions for DXC Technology
- About DXC Technology
- Recruitment Process at PayPal
- Technical Questions for PayPal Interview
- HR Sample Questions for PayPal Interview
- About PayPal
- Capgemini Recruitment Rounds
- Capgemini Interview Questions: Technical round
- Capgemini Interview Questions: HR round
- Preparation tips
- FAQs
- Technical interview questions for Siemens
- Sample HR questions for Siemens
- The recruitment process at Siemens
- About Siemens
- HCL Technical Interview Questions
- HR Interview Questions
- HCL Technologies Recruitment Process
- List of EPAM Interview Questions for Technical Interviews
- About EPAM
- Atlassian Interview Process
- Top Skills for Different Roles at Atlassian
- Atlassian Interview Questions: Technical Knowledge
- Atlassian Interview Questions: Behavioral Skills
- Atlassian Interview Questions: Tips for Effective Preparation
- Walmart Recruitment Process
- Walmart Interview Questions and Sample Answers (HR Round)
- Walmart Interview Questions and Sample Answers (Technical Round)
- Tips for Interviewing at Walmart and Interview Preparation Tips
- Frequently Asked Questions
- Uber Interview Questions For Engineering Profiles: Coding
- Technical Uber Interview Questions: Theoretical
- Uber Interview Question: HR Round
- Uber Recruitment Procedure
- About Uber Technologies Ltd.
- Intel Technical Interview Questions
- Computer Architecture Intel Interview Questions
- Intel DFT Interview Questions
- Intel Interview Questions for Verification Engineer Role
- Recruitment Process Overview
- Important Accenture HR Interview Questions
- Points to remember
- What is Selenium?
- What are the components of the Selenium suite?
- Why is it important to use Selenium?
- What's the major difference between Selenium 3.0 & Selenium 2.0?
- What is Automation testing and what are its benefits?
- What are the benefits of Selenium as an Automation Tool?
- What are the drawbacks to using Selenium for testing?
- Why should Selenium not be used as a web application or system testing tool?
- Is it possible to use selenium to launch web browsers?
- What does Selenese mean?
- What does it mean to be a locator?
- Identify the main difference between "assert", and "verify" commands within Selenium
- What does an exception test in Selenium mean?
- What does XPath mean in Selenium? Describe XPath Absolute & XPath Relation
- What is the difference in Xpath between "//"? and "/"?
- What is the difference between "type" and the "typeAndWait" commands within Selenium?
- Distinguish between findElement() & findElements() in context of Selenium
- How long will Selenium wait before a website is loaded fully?
- What is the difference between the driver.close() and driver.quit() commands in Selenium?
- Describe the different navigation commands that Selenium supports
- What is Selenium's approach to the same-origin policy?
- Explain the difference between findElement() in Selenium and findElements()
- Explain the pause function in SeleniumIDE
- Explain the differences between different frameworks and how they are connected to Selenium's Robot Framework
- What are your thoughts on the Page Object Model within the context of Selenium
- What are your thoughts on Jenkins?
- What are the parameters that selenium commands come with a minimum?
- How can you tell the differences in the Absolute pathway as well as Relative Path?
- What's the distinction in Assert or Verify declarations within Selenium?
- What are the points of verification that are in Selenium?
- Define Implicit wait, Explicit wait, and Fluent
- Can Selenium manage windows-based pop-ups?
- What's the definition of an Object Repository?
- What is the main difference between obtainwindowhandle() as well as the getwindowhandles ()?
- What are the various types of Annotations that are used in Selenium?
- What is the main difference in the setsSpeed() or sleep() methods?
- What is the way to retrieve the alert message?
- How do you determine the exact location of an element on the web?
- Why do we use Selenium RC?
- What are the benefits or advantages of Selenium RC?
- Do you have a list of the technical limitations when making use of Selenium RC? Selenium RC?
- What's the reason to utilize the TestNG together with Selenium?
- What Language do you prefer to use to build test case sets in Selenium?
- What are Start and Breakpoints?
- What is the purpose of this capability relevant in relation to Selenium?
- When do you use AutoIT?
- Do you have a reason why you require Session management in Selenium?
- Are you able to automatize CAPTCHA?
- How can we launch various browsers on Selenium?
- Why should you select Selenium rather than QTP (Quick Test Professional)?
- Airbus Interview Questions and Answers: HR/ Behavioral
- Industry/ Company-Specific Airbus Interview Questions
- Airbus Interview Questions and Answers: Aptitude
- Airbus Software Engineer Interview Questions and Answers: Technical
- Importance of Spring Framework
- Spring Interview Questions (Basic)
- Advanced Spring Interview Questions
- C++ Interview Questions and Answers: The Basics
- C++ Interview Questions: Intermediate
- C++ Interview Questions And Answers With Code Examples
- C++ Interview Questions and Answers: Advanced
- Test Your Skills: Quiz Time
- MBA Interview Questions: B.Com Economics
- B.Com Marketing
- B.Com Finance
- B.Com Accounting and Finance
- Business Studies
- Chartered Accountant
- Q1. Please tell us something about yourself/ Introduce yourself to us.
- Q2. Describe yourself in one word.
- Q3. Tell us about your strengths and weaknesses.
- Q4. Why did you apply for this job/ What attracted you to this role?
- Q5. What are your hobbies?
- Q6. Where do you see yourself in five years OR What are your long-term goals?
- Q7. Why do you want to work with this company?
- Q8. Tell us what you know about our organization
- Q9. Do you have any idea about our biggest competitors?
- Q10. What motivates you to do a good job?
- Q11. What is an ideal job for you?
- Q12. What is the difference between a group and a team?
- Q13. Are you a team player/ Do you like to work in teams?
- Q14. Are you good at handling pressure/ deadlines?
- Q15. When can you start?
- Q16. How flexible are you regarding overtime?
- Q17. Are you willing to relocate for work?
- Q18. Why do you think you are the right candidate for this job?
- Q19. How can you be an asset to the organization?
- Q20. What is your salary expectation?
- Q21. How long do you plan to remain with this company?
- Q22. What is your objective in life?
- Q23. Would you like to pursue your Master's degree anytime soon?
- Q24. How have you planned to achieve your career goal?
- Q25. Can you tell us about your biggest achievement in life?
- Q26. What was the most challenging decision you ever made?
- Q27. What kind of work environment do you prefer to work in?
- Q28. What is the difference between a smart worker and a hard worker?
- Q29. What will you do if you don't get hired?
- Q30. Tell us three things that are most important for you in a job.
- Q31. Who is your role model and what have you learned from him/her?
- Q32. In case of a disagreement, how do you handle the situation?
- Q33. What is the difference between confidence and overconfidence?
- Q34. If you have more than enough money in hand right now, would you still want to work?
- Q35. Do you have any questions for us?
- Interview Tips for Freshers
- Tell me about yourself
- What are your greatest strengths?
- What are your greatest weaknesses?
- Tell me about something you did that you now feel a little ashamed of
- Why are you leaving (or did you leave) this position??
- 15+ resources for preparing most-asked interview questions
- CoCubes Interview Process Overview
- Common CoCubes Interview Questions
- Key Areas to Focus on for CoCubes Interview Preparation
- Conclusion
- Frequently Asked Questions (FAQs)
- Data Analyst Interview Questions With Answers
- About Data Analyst
45+ Cognizant Interview Questions And Answers For 2026

Cognizant is a multinational technology corporation that specializes in information technology, digital systems, outsourcing, digital operations, and business consulting. It was established as the internal technical unit of Dun & Bradstreet in 1994 and began serving foreign clients in 1996.
Given how Cognizant is helping businesses use modern technology with innovative processes to transform the overall customer experience, it has become a dream company for any individual interested in software development, network security, systems, technologies, etc.
Cognizant has also become a top choice for software engineers who wish to gain job experience. Among the multiple career aspirations, the job opportunities offered by Cognizant, especially under the software development category, make it a good option for a high percentage of students post-college or graduation. Before we discuss the Cognizant interview questions, let us take an overview of the recruitment process at Cognizant.
Cognizant Recruitment Process
Cognizant recruitment process consists of written rounds as well as interview rounds. The company takes in candidates both through campus recruitment and off-campus hiring through various job portals. Following are the main rounds in Cognizant recruitment process:
- Round 1 - Skill aptitude assessment or test: Assessment for logical reasoning, problem-solving ability, English comprehension, and quantitative abilities of candidates. The test includes both MCQs and conceptual coding challenges.
- Round 2 - Technical interview: This is an in-person round conducted to test the technical knowledge and programming skills of candidates. It is performed to learn about the level of understanding of candidates about the different programming languages, individual programming abilities of each programming language, implementation techniques for software configuration management, and much more.
- Round 3 - HR interview: This round is designed to know candidates on a personal level, in terms of their qualifications, situation-based capabilities, verbal ability, etc.
List of Technical Interview Questions for Cognizant
Other than the aptitude test online, the technical interview is a crucial step in the Cognizant interview process. It helps in deciding whether a candidate will proceed to the final HR round or not. THe round is a mix of basic questions and questions that need in-depth knowledge. To help you prepare better, here is a list of technical questions with answers that are asked during round two or the technical interview process as part of the recruitment process at Cognizant.
1. What do you understand by data abstraction?
When it comes to OOPS, data abstraction is known to be one part of the three main different principles, in addition to inheritance and encapsulation. Through the data abstraction process, a software developer or programmer can easily hide all the data that is relevant to an object to increase efficiency and reduce the level of complexity significantly.
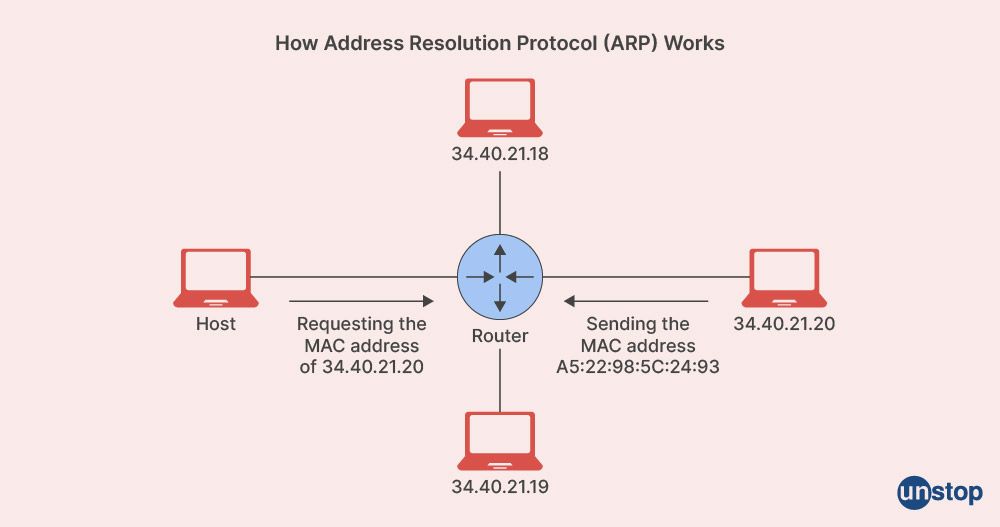
2. What is the meaning of ARP, and what is its main function?
The full form of ARP is address resolution protocol. It is commonly used to observe and determine the LAN address from the main network address. Under the ARP protocol, a node with the destination of IP for packet delivery is decided. And, for the nodes to transfer individual frames through the local link, a link to your address is required. This is where ARP helps. It first sends a broadcast message to the available nodes to state the MAC address of the IP address in question, allowing easy flow communication through the same.
3. What is a code snippet?
A code snippet refers to a small block of code that is reusable and can easily be inserted in any court file using the context menu, also known as the right-click menu command, or by using different combinations of the available hotkeys. One code snippet can contain a list of reusable code blocks and can easily be inserted into either the entire method or the entire class. It is available in multiple programming languages, including Visual Basic, T-SQL, C++, etc.
4. What is the root partition in OS?
The root partition is the place wherein an operating system kernel is placed along with the crucial system files that are potentially held up in other places during boot time.
5. What is the use of dynamic loading in better utilization of memory space?
In a programming language, the routine is never loaded until it is called, especially when it comes to dynamic loading. It is a strategy that is highly effective when there is a high quantity of courts, including the error routines that can occur infrequently. To save a routine, a relocatable load format is necessary on the desk. Once the main program is loaded into the memory of the system, it is executed, and at the same time, each routine requires the next routine to follow.
In order to determine if the necessary routine is loaded, a relocatable linking loader is utilized. This loader is responsible for loading the requested memory, which is stored in a way that allows updates to be made to the current program's address tables. This entire process is achieved through dynamic loading. So, one of the key benefits of dynamic loading is the optimization of memory space utilization because it involves loading certain parts of a program into memory only when they are actually needed, as opposed to loading everything at once.
6. What are the key differences between a file structure and the storage structure?
A storage structure is a type of data storage wherein the main data is directly stored in the prime memory, which is called RAM. Once the data stored is there, as soon as the function that uses the respective data is done with the complete execution, it is directly deleted.
A file structure, on the other hand, is the type of data representation that is stored in the auxiliary or secondary memory of any device like pen drives and hard drives. The main purpose is to store data and keep it intact until it is deleted manually.
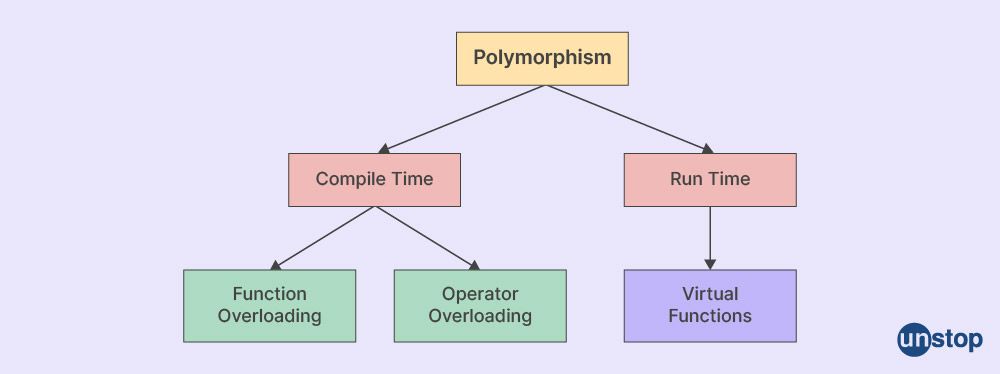
7. What do you understand by polymorphism?
In object-oriented programming, the term 'polymorphism' refers to an entity's capacity to assume several forms, like the form of a variable, function, or object. In other words, a single entity might act in several ways depending on the circumstances. Compile-time polymorphism and run-time polymorphism are the two forms of polymorphism.
An individual who possesses many traits simultaneously is a real-world example of polymorphism. Men can be fathers, husbands, and workers simultaneously and behave differently in each of these roles.
8. What are some of the disadvantages of the classic life cycle model?
- The first disadvantage of the classic life cycle model is that the working version of this particular program is not yet available. So, any customer will have to have a lot of patience to work with it.
- The second disadvantage is that when it comes to real projects, sequential flow is rarely followed and thus creates unexpected problems.
- Lastly, in a classic life cycle model, it is relatively challenging for any customer to ask for all the requirements directly or project requirements upfront. Customers might not be able to foresee all their needs or potential issues at the beginning of a project. For example, the Waterfall model follows a sequential approach where each phase must be completed before moving on to the next. This structure can be less flexible when it comes to accommodating changes or evolving requirements.
9. What do you understand about software configuration management?
Software configuration management is the process of controlling and talking about all the changes that take place within a software. It has a function called change control that monitors all the changes that are made in a software system while also ensuring that they are consistent and use the same rules and regulations of an organization.
10. What is the time complexity of any linked list during the process of insertion?
Speaking of the time complexity of deletion or insertion, especially in a singly linked list, it is directly dependent on the position in the software where you want to perform the respective command. For instance, if you want to add an element towards the end of the linked list during insertion, you have to either travel or transfer the entire list, making the complexity O(n).
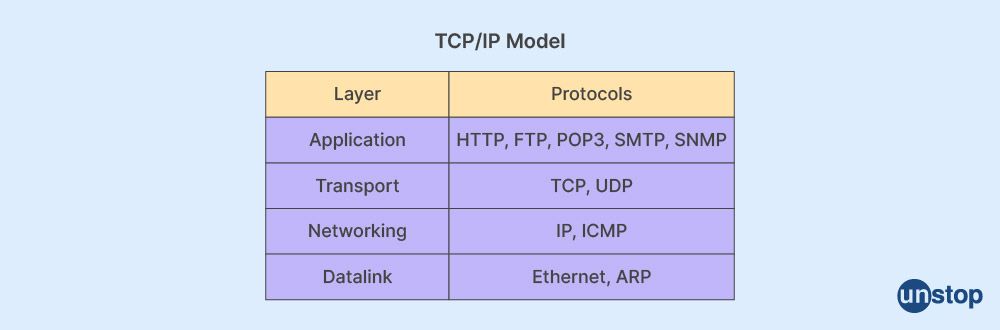
11. What is the role of the IP model or the TCP model?
The IP model or the TCP model is considered to be a compressed version of the model called OSI. Under this model, there are four layers, including the process or application layer, the host-to-host or transport layer, the internet layer or network layer, and the network access or combination of physical and data link layers.
12. What is the meaning of a bridge router?
Commonly known as a brouter, a bridge router is a network device that can work as both a router and a bridge. The main function of the bridge router is to forward all the different packets, including a bridge, with known protocols and other route packets. In simple words, the bridge router can successfully handle the characteristics of both non-routable and routable protocols with ease. Within a network system, the bridge router is known to be the connecting device that helps as either a network bridge or a router within the internet work.
13. Explain what a resident set and a working set mean in any programming language.
The resident set and the working set are correlated. When it comes to a resident set, it is part of the chosen processed image, which is stored in the real memory location. When the processed image is broken down for use in two separate subsets, each of these subsets is known as a working set. Therefore, the working set is necessary as it is an essential part of the resident set, needed for correct execution, and acts on memory.
14. What is the difference between a pre-increment operator and a post-increment operator?
The pre-increment operator is used to denote the value of a particular variable right before adding it to an expression. The post-increment operator, on the other hand, is used to denote the value of a particular variable after the expression execution is completed.
Explore jobs and internships across 180+ categories!
15. What is the garbage collector function system in Java?
Multiple programming languages like C++ and C are known to be used for both creation and destruction of any particular object. However, in some cases, a programmer may not remember to destroy the unnecessary objects, using up more memory location space and suffocating the limited memory available, causing memory leaks. Thus, for these reasons, Java garbage collector becomes helpful.
Java Garbage Collector (GC) is an automatic memory management mechanism in Java that identifies and reclaims memory occupied by objects no longer in use, preventing memory leaks and ensuring efficient memory utilization. The primary goal of the Java GC is to alleviate developers from manual memory management tasks, allowing them to focus on coding while the runtime system takes care of memory deallocation.
16. What is the Hamming code?
Hamming code is a set of error correction codes that can be used to detect and correct errors that may occur when data is transferred or stored from one source to another. In this, unnecessary fragments are additional binary bits that are built and added to the data transfer bits to ensure that no bits are lost during data transfer. Hamming code is the actual method used for additional measurement components to allow for error detection.
17. What is the fill factor in SQL? What is its default value?
Fill factor is a feature to fill the percentage of space on each level page that will be filled with data. The smallest unit in the SQL server is a page, made up of 8K pages. Depending on the size of the line, each page may contain only one or more lines. The default fill factor value is 100, which is equal to the value of 0. The SQL server will fill index-level pages with the maximum number of lines that can be entered if the fill factor is set to 100 or 0. If the fill factor is 100, then the page will not have space or minimal space.
18. What exactly is index hunting, and how does it aid query performance?
Index hunting is a way to improve a collection of clues. This is because the indicators improve the performance of questions and the time to process them. It helps to improve query performance in the following ways:
- Using the quiz optimizer, relevant questions are raised
- For outcome assessment, parameters such as reference, questionnaire distribution, and performance are used
- The database is well organized into a small group of problematic questions
19. What is the monkey function?
Monkey function, also known as monkey patching, is available in Python programming language. Using this, a programmer can modify a code at runtime for a class or a module. With the help of this monkey function, it is easier to reopen a module or a class for behavior alteration to complete a project using code at runtime.
20. What is caching? How does caching work?
Caching is a way of saving multiple copies of data that are widely used in temporary storage (or archive) for quick access. It stores data in temporary formats for software applications, servers, and web browsers. So, users do not have to download information every time they visit a website or use an application.
Cached data works to save data to device memory for later access. The data is stored in computer memory directly below the central processing unit (CPU). The primary cache level is installed on the device's microprocessor chip, followed by other secondary cache levels that feed the primary level. This information is stored until the life of the content, which specifies how long it should be stored in the archive, expires.
Also Read: What is Cache Memory?
21. What do you understand about 'Proactive Updates' in the context of DBMS?
Proactive Updates are changes that were made to the website before use in the real-world environment. Other types of updates are:
-
Retroactive Updates: These updates are applied to the website after it has worked in the real world.
-
Simultaneous Updates: These updates are applied to the website at the same boot time as they first came into effect in the real world.
22. What are some of the factors that influence whether or not the need for a detection algorithm in a deadlock avoidance system is there?
One of the main factors that help influence whether or not the need for a detection algorithm is required is that it is directly dependent on the frequency of a deadlock occurrence each time the algorithm is implemented. Other than this, the number of processes that will be directly or indirectly affected due to this deadlock as soon as the algorithm is put to use is another determining factor.
23. What are the main features of a virtual file system or VFS?
The presence of an abstract layer right on the top of a more specific and concrete file or system is called a virtual file system. The main purpose of a virtual file system is to allow various client applications to access a variety of different concrete file systems regularly and easily.
In addition to that, it acts as a bridge between Windows, traditional macOS, UNIX file systems, and much more. Lastly, it is used to define a kernel interface within a particular file system, which adds more support to the new file system that is being implemented in the kernel.
24. What do you understand by an exterior gateway protocol?
An exterior gateway protocol allows all the different internet gateways from both the same or separate systems to share information on network reachability easily. There are three purposes for it, including:
- Creation of a set of neighbors
- Monitor the neighbors
- Create a notification system for all neighbors to notify them.
25. What is your understanding of BufferedWriter?
In programming languages, BufferedWriter is known to be a temporary source of data storage used to create an output stream for a buffered character with the use of the default output buffer size.
26. What is the integer data type size?
The integer data type size is either 2 bytes or 4 bytes.
27. What do you mean by the recursion method?
Recursion is an approach or a programming technique where a function calls itself to solve a problem. This is done by breaking the function down into smaller instances of the same problem. Even though this technique helps to get concise code and simplifies complex tasks, it requires careful consideration of termination conditions to avoid infinite loops.
28. What are the key characteristics of the OFC language?
The key characteristics of the OFC language include flexibility, modularity, portability, reliability, interactivity, efficiency, and effectiveness.
29. In the C programming language, what do you understand by a modifier?
The main purpose of a modifier in C is to derive the necessary space for variable allocation. All the modifiers are fixed and consist of basic data types that can either be increased or decreased based on the amount of variable storage allocation.
30. Explain what you mean by virtual functions.
In almost all object-oriented programming languages, a virtual method or function is the inheritable or overrideable function method used for dynamic dispatch facilitation. It is an essential core part of polymorphism called runtime.
31. In Java, what is the meaning of inheritance?
For all developers, the actual meaning of inheritance is the ability of new objects to take on some of the old properties of the previous objects without any concerns. For instance, when a class uses inheritance, it is called a base class or a superclass. On the other hand, when the class inherits data from the main base class, it is either called a subclass or a child class.
32. Mention the disability between pop and push methods in a stack.
The popping and pushing of data deal with how data is fetched and stored from a particular stack. Popping gets something out of the stack while pushing stacks up a new item.

33. Where do you place the programming language C?
Among all the different programming languages, the C language is known as the middle-level language. It is a bridge between the low- or machine-level languages and the other high-level languages. This is a commonly used language as it is highly user-friendly and offers multiple support options.
34. What is the meaning of a pointer?
A pointer is known to be a variable that stores the various addresses of multiple other variables that have the same value as the main point. Out of all the pointers, the direct pointer is specifically used to point to various values of the variables but indirectly to manipulate them easily.
35. What do you understand by demand paging?
Demand paging refers to the recognition of the area of a memory that is not being used currently. this is done to easily swap it on the disk to accommodate other means of the application without storage concerns.
36. How to easily implement a stack using the queue method?
There are two different types of queues that can be used for implementation in a stack. They are push and pull.
37. What do you know about lvalue and rvalue?
If an expression is appearing towards the right side of the assignment operator, then it is known to be rvalue. The rvalue is given to the lvalue when needed and it appears on the left side of the chosen assignment operator as it is a variable instead of a constant.
38. What is Preemptive Multitasking?
Computer programs can share operating systems, computing time, and underlying hardware resources when using preemptive multitasking. Preemptive multitasking allows the operating system to move the context of a running process to another process at any time. Before allowing another computer job to access its computer resources, such as computer's central processing unit (CPU), the operating system employs a set of criteria to decide how long to perform a particular computer task.
39. What do you understand by cryptosystem algorithm?
Computer systems that use encryption techniques are referred to as cryptosystems. A cryptosystem algorithm in cryptography is a collection of algorithms used to encrypt and decrypt communications. These systems offer a range of security and information protection techniques. These systems encode the communication using codes so that only the target audience can read and comprehend it.
40. What is RSA?
RSA (Rivest-Shamir-Adleman) is a popular public-key cryptosystem for secure data transfer. It is a method used for encrypting and decrypting data that was created by Ron Rivest, Adi Shamir, and Leonard Adleman.
It is challenging to infer an RSA key because there is no effective way to factor really big integers, which is the foundation of RSA. It uses the concept of factorization. Two keys—a public key and a private key are used in the RSA algorithm. While the private key is kept secret and is used to decode communications, the public key may be seen by everyone and is used to encrypt messages.
41. What is a comparison operator?
A comparison operator is a component or operator used in programming languages to compare items and ascertain their connection. These operators are frequently employed in logical statements to determine if two variables or values are equal or different. Based on the outcome of the comparison, comparison operators return a boolean value, either true or false.
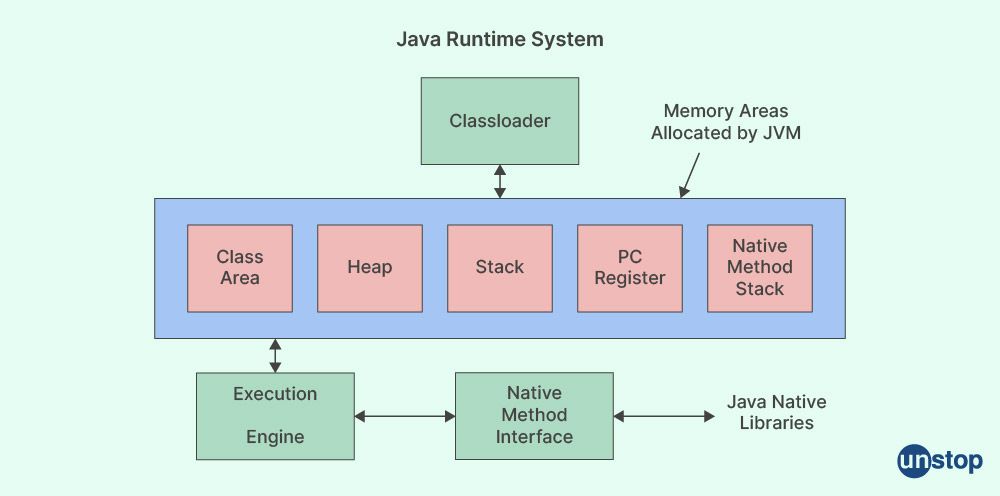
42. What is JVM?
JVM, which stands for Java Virtual Machine, is a program that runs other programs. It is an abstract machine that provides a runtime environment for Java bytecode execution. Translating Java bytecode into machine language is the responsibility of the Java Virtual Machine (JVM), a part of the Java Runtime Environment (JRE). JVM is a platform-dependent program. Therefore, it may run on a variety of computer hardware and operating systems.
43. Give examples for dynamic data structure.
Some examples of dynamic data structure are:
- Linked list
- Stack
- Vector
- Queue
Learn the basics of data structures! Join our course
44. Give some examples of non-linear data structure.
Some examples of non-linear data structures are:
- Trees
- Graphs
- Heaps
- Hashing
45. What is a digital signature algorithm?
Digital signature algorithm or DSA is a widely used digital signature algorithm that incorporates the algebraic properties of discrete logarithm problems and modular exponentiations for generating an electronic signature for various applications. It is based on the mathematical concepts of modular exponentiation and the discrete logarithm problem and involves four operations: key generation, key distribution, signing, and signature verification.
46. Define OOPs concept.
OOPs concept refers to programming languages that revolve around the concept of objects, which encapsulate data and methods to perform tasks. The viewer or user sees objects as they do the tasks you've given them. Real-world concepts like inheritance, hiding, polymorphism, etc., are intended to be incorporated into programming through object-oriented design. The primary goal of OOP is to bind together the data and the functions that use them such that only that function and no other section of the code may access the data.
These were some important TCS interview questions for the technical round. Along with revising the basic concepts, the candidates must also keep themselves abreast with the latest digital technology, as questions can be asked from there as well.
TCS Interview Questions for HR Round
Following are some of the common questions likely to be asked in the HR round.
1. Tell me something about yourself.
Tip: Be concise and highlight your skills and interests that align with the role being offered. Read More
2. Are you willing to relocate to different parts of India?
Tip: Be honest with this answer. If you are not comfortable with relocating, state your reasons clearly. Also, do ask if the company offers any assistance in relocating. Read More
3. What are your strengths?
Tip: State your core strengths, especially those that align with the role. Read More
4. Why should we hire you?
Tip: Project yourself as an asset for the company. State any examples from your previous job where you showed outstanding results. Convey your keen interest in joining the company by highlighting your liking for the company's culture. Read More
5. Describe your final year project. What new ideas did you bring to the table for this project?
Tip: To answer this question, study your final year project well and try to analyze it from different angles. See how you could have further improved it.
We hope the above questions will help you prepare well for facing the TCS interview questions. Keep learning and practicing, and stay tuned to Unstop.
Suggested Reads:
I am a storyteller by nature. At Unstop, I tell stories ripe with promise and inspiration, and in life, I voice out the stories of our four-legged furry friends. Providing a prospect of a good life filled with equal opportunities to students and our pawsome buddies helps me sleep better at night. And for those rainy evenings, I turn to my colors.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter
Blogs you need to hog!

This Is My First Hackathon, How Should I Prepare? (Tips & Hackathon Questions Inside)

10 Best C++ IDEs That Developers Mention The Most!

Advantages and Disadvantages of Cloud Computing That You Should Know!










Comments
Add comment