- TCS Technical Interview Questions & Answers
- TCS Managerial Interview Questions & Answers
- TCS HR Interview Questions & Answers
- Overview of Cognizant Recruitment Process
- Cognizant Interview Questions: Technical
- Cognizant Interview Questions: HR Round
- Overview of Wipro Technologies Recruitment Rounds
- Wipro Interview Questions
- Technical Round
- HR Round
- Online Assessment Sample Questions
- Frequently Asked Questions
- Overview of Google Recruitment Process
- Google Interview Questions: Technical
- Google Interview Questions: HR round
- Interview Preparation Tips
- About Google
- Deloitte Technical Interview Questions
- Deloitte HR Interview Questions
- Deloitte Recruitment Process
- Technical Interview Questions and Answers
- Level 1 difficulty
- Level 2 difficulty
- Level 3 difficulty
- Behavioral Questions
- Eligibility Criteria for Mindtree Recruitment
- Mindtree Recruitment Process: Rounds Overview
- Skills required to crack Mindtree interview rounds
- Mindtree Recruitment Rounds: Sample Questions
- About Mindtree
- Preparing for Microsoft interview questions
- Microsoft technical interview questions
- Microsoft behavioural interview questions
- Aptitude Interview Questions
- Technical Interview Questions
- Easy
- Intermediate
- Hard
- HR Interview Questions
- Eligibility criteria
- Recruitment rounds & assessments
- Tech Mahindra interview questions - Technical round
- Tech Mahindra interview questions - HR round
- Hiring process at Mphasis
- Mphasis technical interview questions
- Mphasis HR interview questions
- About Mphasis
- Technical interview questions
- HR interview questions
- Recruitment process
- About Virtusa
- Goldman Sachs Interview Process
- Technical Questions for Goldman Sachs Interview
- Sample HR Question for Goldman Sachs Interview
- About Goldman Sachs
- Nagarro Recruitment Process
- Nagarro HR Interview Questions
- Nagarro Aptitude Test Questions
- Nagarro Technical Test Questions
- About Nagarro
- PwC Recruitment Process
- PwC Technical Interview Questions: Freshers and Experienced
- PwC Interview Questions for HR Rounds
- PwC Interview Preparation
- Frequently Asked Questions
- EY Technical Interview Questions (2023)
- EY Interview Questions for HR Round
- About EY
- Morgan Stanley Recruitment Process
- HR Questions for Morgan Stanley Interview
- HR Questions for Morgan Stanley Interview
- About Morgan Stanley
- Recruitment Process at Flipkart
- Technical Flipkart Interview Questions
- Code-Based Flipkart Interview Questions
- Sample Flipkart Interview Questions- HR Round
- Conclusion
- FAQs
- Recruitment Process at Paytm
- Technical Interview Questions for Paytm Interview
- HR Sample Questions for Paytm Interview
- About Paytm
- Most Probable Accenture Interview Questions
- Accenture Technical Interview Questions
- Accenture HR Interview Questions
- Amazon Recruitment Process
- Amazon Interview Rounds
- Common Amazon Interview Questions
- Amazon Interview Questions: Behavioral-based Questions
- Amazon Interview Questions: Leadership Principles
- Company-specific Amazon Interview Questions
- 43 Top Technical/ Coding Amazon Interview Questions
- Juspay Recruitment: Stages and Timeline
- Juspay Interview Questions and Answers
- How to prepare for Juspay interview questions
- Prepare for the Juspay Interview: Stages and Timeline
- Frequently Asked Questions
- Adobe Interview Questions - Technical
- Adobe Interview Questions - HR
- Recruitment Process at Adobe
- About Adobe
- Cisco technical interview questions
- Sample HR interview questions
- The recruitment process at Cisco
- About Cisco
- JP Morgan interview questions (Technical round)
- JP Morgan interview questions HR round)
- Recruitment process at JP Morgan
- About JP Morgan
- Wipro Elite NTH: Selection Process
- Wipro Elite NTH Technical Interview Questions
- Wipro Elite NTH Interview Round- HR Questions
- BYJU's BDA Interview Questions
- BYJU's SDE Interview Questions
- BYJU's HR Round Interview Questions
- A Quick Overview of the KPMG Recruitment Process
- Technical Questions for KPMG Interview
- HR Questions for KPMG Interview
- About KPMG
- DXC Technology Interview Process
- DCX Technical Interview Questions
- Sample HR Questions for DXC Technology
- About DXC Technology
- Recruitment Process at PayPal
- Technical Questions for PayPal Interview
- HR Sample Questions for PayPal Interview
- About PayPal
- Capgemini Recruitment Rounds
- Capgemini Interview Questions: Technical round
- Capgemini Interview Questions: HR round
- Preparation tips
- FAQs
- Technical interview questions for Siemens
- Sample HR questions for Siemens
- The recruitment process at Siemens
- About Siemens
- HCL Technical Interview Questions
- HR Interview Questions
- HCL Technologies Recruitment Process
- List of EPAM Interview Questions for Technical Interviews
- About EPAM
- Atlassian Interview Process
- Top Skills for Different Roles at Atlassian
- Atlassian Interview Questions: Technical Knowledge
- Atlassian Interview Questions: Behavioral Skills
- Atlassian Interview Questions: Tips for Effective Preparation
- Walmart Recruitment Process
- Walmart Interview Questions and Sample Answers (HR Round)
- Walmart Interview Questions and Sample Answers (Technical Round)
- Tips for Interviewing at Walmart and Interview Preparation Tips
- Frequently Asked Questions
- Uber Interview Questions For Engineering Profiles: Coding
- Technical Uber Interview Questions: Theoretical
- Uber Interview Question: HR Round
- Uber Recruitment Procedure
- About Uber Technologies Ltd.
- Intel Technical Interview Questions
- Computer Architecture Intel Interview Questions
- Intel DFT Interview Questions
- Intel Interview Questions for Verification Engineer Role
- Recruitment Process Overview
- Important Accenture HR Interview Questions
- Points to remember
- What is Selenium?
- What are the components of the Selenium suite?
- Why is it important to use Selenium?
- What's the major difference between Selenium 3.0 & Selenium 2.0?
- What is Automation testing and what are its benefits?
- What are the benefits of Selenium as an Automation Tool?
- What are the drawbacks to using Selenium for testing?
- Why should Selenium not be used as a web application or system testing tool?
- Is it possible to use selenium to launch web browsers?
- What does Selenese mean?
- What does it mean to be a locator?
- Identify the main difference between "assert", and "verify" commands within Selenium
- What does an exception test in Selenium mean?
- What does XPath mean in Selenium? Describe XPath Absolute & XPath Relation
- What is the difference in Xpath between "//"? and "/"?
- What is the difference between "type" and the "typeAndWait" commands within Selenium?
- Distinguish between findElement() & findElements() in context of Selenium
- How long will Selenium wait before a website is loaded fully?
- What is the difference between the driver.close() and driver.quit() commands in Selenium?
- Describe the different navigation commands that Selenium supports
- What is Selenium's approach to the same-origin policy?
- Explain the difference between findElement() in Selenium and findElements()
- Explain the pause function in SeleniumIDE
- Explain the differences between different frameworks and how they are connected to Selenium's Robot Framework
- What are your thoughts on the Page Object Model within the context of Selenium
- What are your thoughts on Jenkins?
- What are the parameters that selenium commands come with a minimum?
- How can you tell the differences in the Absolute pathway as well as Relative Path?
- What's the distinction in Assert or Verify declarations within Selenium?
- What are the points of verification that are in Selenium?
- Define Implicit wait, Explicit wait, and Fluent
- Can Selenium manage windows-based pop-ups?
- What's the definition of an Object Repository?
- What is the main difference between obtainwindowhandle() as well as the getwindowhandles ()?
- What are the various types of Annotations that are used in Selenium?
- What is the main difference in the setsSpeed() or sleep() methods?
- What is the way to retrieve the alert message?
- How do you determine the exact location of an element on the web?
- Why do we use Selenium RC?
- What are the benefits or advantages of Selenium RC?
- Do you have a list of the technical limitations when making use of Selenium RC? Selenium RC?
- What's the reason to utilize the TestNG together with Selenium?
- What Language do you prefer to use to build test case sets in Selenium?
- What are Start and Breakpoints?
- What is the purpose of this capability relevant in relation to Selenium?
- When do you use AutoIT?
- Do you have a reason why you require Session management in Selenium?
- Are you able to automatize CAPTCHA?
- How can we launch various browsers on Selenium?
- Why should you select Selenium rather than QTP (Quick Test Professional)?
- Airbus Interview Questions and Answers: HR/ Behavioral
- Industry/ Company-Specific Airbus Interview Questions
- Airbus Interview Questions and Answers: Aptitude
- Airbus Software Engineer Interview Questions and Answers: Technical
- Importance of Spring Framework
- Spring Interview Questions (Basic)
- Advanced Spring Interview Questions
- C++ Interview Questions and Answers: The Basics
- C++ Interview Questions: Intermediate
- C++ Interview Questions And Answers With Code Examples
- C++ Interview Questions and Answers: Advanced
- Test Your Skills: Quiz Time
- MBA Interview Questions: B.Com Economics
- B.Com Marketing
- B.Com Finance
- B.Com Accounting and Finance
- Business Studies
- Chartered Accountant
- Q1. Please tell us something about yourself/ Introduce yourself to us.
- Q2. Describe yourself in one word.
- Q3. Tell us about your strengths and weaknesses.
- Q4. Why did you apply for this job/ What attracted you to this role?
- Q5. What are your hobbies?
- Q6. Where do you see yourself in five years OR What are your long-term goals?
- Q7. Why do you want to work with this company?
- Q8. Tell us what you know about our organization
- Q9. Do you have any idea about our biggest competitors?
- Q10. What motivates you to do a good job?
- Q11. What is an ideal job for you?
- Q12. What is the difference between a group and a team?
- Q13. Are you a team player/ Do you like to work in teams?
- Q14. Are you good at handling pressure/ deadlines?
- Q15. When can you start?
- Q16. How flexible are you regarding overtime?
- Q17. Are you willing to relocate for work?
- Q18. Why do you think you are the right candidate for this job?
- Q19. How can you be an asset to the organization?
- Q20. What is your salary expectation?
- Q21. How long do you plan to remain with this company?
- Q22. What is your objective in life?
- Q23. Would you like to pursue your Master's degree anytime soon?
- Q24. How have you planned to achieve your career goal?
- Q25. Can you tell us about your biggest achievement in life?
- Q26. What was the most challenging decision you ever made?
- Q27. What kind of work environment do you prefer to work in?
- Q28. What is the difference between a smart worker and a hard worker?
- Q29. What will you do if you don't get hired?
- Q30. Tell us three things that are most important for you in a job.
- Q31. Who is your role model and what have you learned from him/her?
- Q32. In case of a disagreement, how do you handle the situation?
- Q33. What is the difference between confidence and overconfidence?
- Q34. If you have more than enough money in hand right now, would you still want to work?
- Q35. Do you have any questions for us?
- Interview Tips for Freshers
- Tell me about yourself
- What are your greatest strengths?
- What are your greatest weaknesses?
- Tell me about something you did that you now feel a little ashamed of
- Why are you leaving (or did you leave) this position??
- 15+ resources for preparing most-asked interview questions
- CoCubes Interview Process Overview
- Common CoCubes Interview Questions
- Key Areas to Focus on for CoCubes Interview Preparation
- Conclusion
- Frequently Asked Questions (FAQs)
- Data Analyst Interview Questions With Answers
- About Data Analyst
Deloitte Interview Questions For Freshers and Experienced Candidates

Deloitte is a multinational professional services network and a leading provider of audit, consulting, advisory services (financial and risk), legal services, tax, and associated services across the globe. It's wide client base includes government organizations, non-profit entities, private organizations, and legal entities, among others. This 178-year-old firm is also dedicated to supporting environmental sustainability and social growth.
Let's start the prep for your dream job at one of the Big Four accounting firms with these technical interview questions:
Deloitte Technical Interview Questions
1. Tell me about Distributed Cache in Apache Hadoop.
The MapReduce framework in Apache Hadoop has a feature called Distributed Cache that allows users to cache files, including text, archives, jars, and more which are needed by applications. The purpose of Distributed Cache is to cache small to moderate read-only files that are required by MapReduce jobs so that they do not have to be read every time from HDFS. This will increase seek time and latency and offer valuable utility features.
2. Have you heard about Heartbeat in Hadoop? If yes, explain it.
Yes, I know about Heartbeat in Hadoop.
Heartbeat is a Hadoop term for the signal indicating life which is provided by the DataNode to the NameNode at regular intervals and by the Task Tracker to the Job Tracker at regular intervals. The Hadoop framework's default heartbeat interval is 3 seconds. If the DataNode fails to transmit the heartbeat signal to the NameNode for more than 10 minutes, it is regarded as dead or unavailable. This is known as the "Heartbeat Lost" condition.
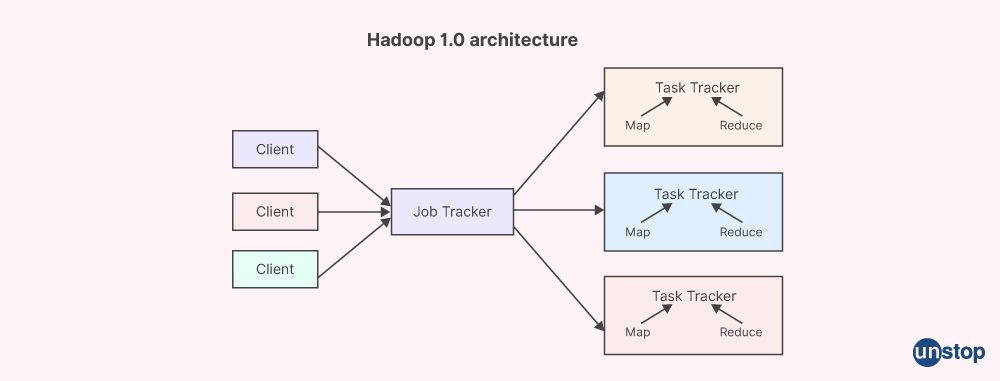
3. Tell me about YARN in Hadoop.
YARN (Yet Another Resource Negotiator) is a core component of Apache Hadoop's resource management layer. It is responsible for allocating system resources to various applications running in a Hadoop cluster and scheduling the tasks to be executed on different cluster nodes. The core concept behind YARN is to divide up resource management and job scheduling or monitoring functions into distinct daemons. It includes data processing engines like batch processing, graph processing, stream processing, interactive processing, etc.
The YARN consists of a Resource Manager master daemon, a Node Manager slave daemon, and Application Master.
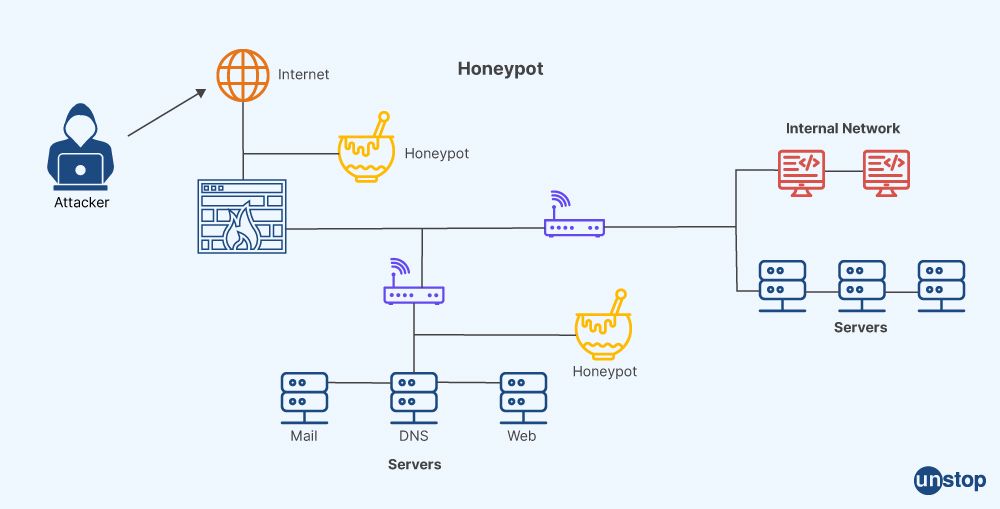
4. Explain honeypots.
A honeypot is a cybersecurity tool that employs a fake attack target to prevent online criminals from attacking real targets. It is a network-attached machine that acts as a decoy or trap to lure online criminals. By using honeypots, organizations may detect and block hackers who interact with honeypots in an attempt to hack into information systems without authorization. Honeypots can be designed to look like any digital asset, such as servers, software, or even the network itself. They intentionally mimic the model's structure, components, and content in order to appear to be a valid target.
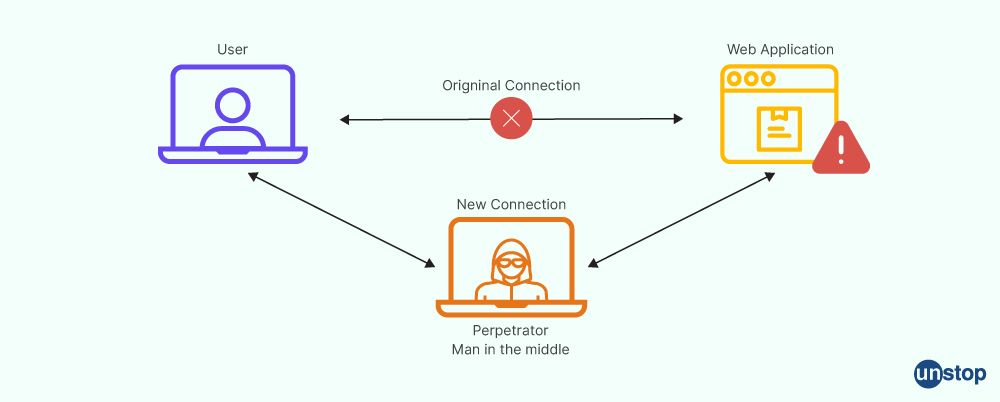
5. Describe "Man-in-the-Middle Attack".
A cyberattack known as a "Man-in-the-Middle" (MitM) occurs when an attacker stands between two parties that think they are chatting directly with one another. An attacker can secretly transmit and even alters their messages. The attacker might steal sensitive information, covertly listen in on the chat, or even pass themselves off as one of the other participants.
It is a frequent form of a cybersecurity attack that allows attackers to eavesdrop on conversations between two targets. Users can employ security best practices like using a VPN, avoiding public Wi-Fi networks, and not clicking on questionable email links to prevent MitM attacks.
6. Explain a session in PHP.
A session in PHP is a method of storing data (in variables) to be used across several pages. It enables information sharing across several pages of a single website or app. Unlike a cookie, the data stored in the session is kept on the server rather than on the user's PC.
7. Assume that you have a 2-dimensional Boolean array matrix with m rows and n columns and each row is sorted. How can you then find the row that will have the most 1s in it?
If we have a 2-D Boolean array matrix and each row is sorted, then we can implement a binary search to find the row which will have the most 1s in it.
As we know that each row is sorted, we can use a binary search to determine the index of the first instance of 1 in each row. The total number of columns minus the index of the first 1 will equal the count of 1s. We can record the most 1s that have been seen thus far and the row's index that has the most 1s. The index of the row with the greatest number of 1s can be returned at the conclusion.
Example:
CODE SNIPPET IS HEREI2luY2x1ZGUgPGlvc3RyZWFtPgoKI2luY2x1ZGUgPHZlY3Rvcj4KCgoKCnVzaW5nIG5hbWVzcGFjZSBzdGQ7CgoKCgppbnQgY291bnRPbmVzKHZlY3Rvcjx2ZWN0b3I8Ym9vbD4+JiBtYXRyaXgpIHsKCmludCBtYXhDb3VudCA9IDA7CgppbnQgbWF4Um93SW5kZXggPSAtMTsKCmludCByb3dzID0gbWF0cml4LnNpemUoKTsKCmludCBjb2xzID0gbWF0cml4WzBdLnNpemUoKTsKCgoKCmZvciAoaW50IGkgPSAwOyBpIDwgcm93czsgaSsrKSB7CgppbnQgbGVmdCA9IDA7CgppbnQgcmlnaHQgPSBjb2xzIC0gMTsKCmludCBjb3VudCA9IDA7CgoKCgovLyBCaW5hcnkgc2VhcmNoIHRvIGZpbmQgdGhlIGluZGV4IG9mIHRoZSBmaXJzdCAxIGluIHRoZSByb3cKCndoaWxlIChsZWZ0IDw9IHJpZ2h0KSB7CgppbnQgbWlkID0gbGVmdCArIChyaWdodCAtIGxlZnQpIC8gMjsKCmlmIChtYXRyaXhbaV1bbWlkXSkgewoKY291bnQgPSBjb2xzIC0gbWlkOyAvLyBDb3VudCBvZiAxcyBpbiB0aGUgcm93CgpyaWdodCA9IG1pZCAtIDE7IC8vIExvb2sgZm9yIDFzIGluIHRoZSBsZWZ0IHN1YmFycmF5Cgp9CgplbHNlIHsKCmxlZnQgPSBtaWQgKyAxOyAvLyBMb29rIGZvciAxcyBpbiB0aGUgcmlnaHQgc3ViYXJyYXkKCn0KCn0KCgoKCmlmIChjb3VudCA+IG1heENvdW50KSB7CgptYXhDb3VudCA9IGNvdW50OwoKbWF4Um93SW5kZXggPSBpOwoKfQoKfQoKCgoKcmV0dXJuIG1heFJvd0luZGV4OwoKfQoKCgoKaW50IG1haW4oKSB7Cgp2ZWN0b3I8dmVjdG9yPGJvb2w+PiBtYXRyaXggPSB7Cgp7dHJ1ZSwgdHJ1ZSwgdHJ1ZSwgdHJ1ZX0sCgp7ZmFsc2UsIGZhbHNlLCB0cnVlLCB0cnVlfSwKCntmYWxzZSwgZmFsc2UsIHRydWUsIHRydWV9LAoKe3RydWUsIHRydWUsIHRydWUsIHRydWV9LAoKe2ZhbHNlLCB0cnVlLCB0cnVlLCB0cnVlfQoKfTsKCgoKCmludCByb3dJbmRleCA9IGNvdW50T25lcyhtYXRyaXgpOwoKY291dCA8PCAiUm93IHdpdGggdGhlIG1vc3QgMXM6ICIgPDwgcm93SW5kZXgrMSA8PCBlbmRsOwoKCgoKcmV0dXJuIDA7Cgp9CgpPVVRQVVQ6CgpSb3cgd2l0aCB0aGUgbW9zdCAxczogMQ==
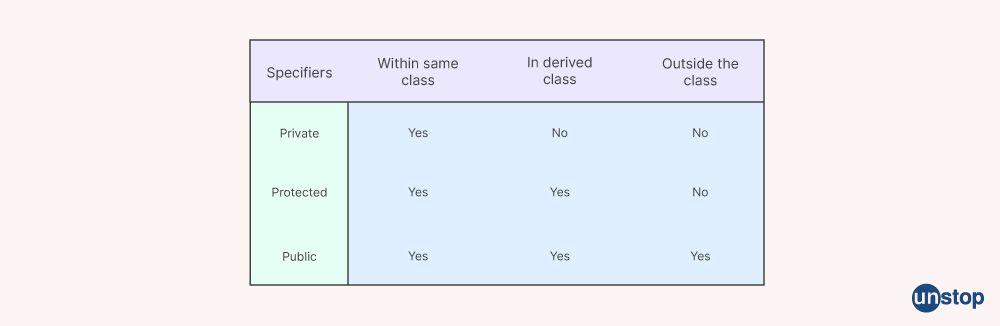
8. Describe the access specifiers in C++.
In C++ programming language, there are three types of access specifiers. These are:
Public: Everyone will have access to every class member stated using the public specifier. Using the class's object, they can be accessed from outside the class.
Private: Members that can't be accessed outside of the class are considered private.
Protected: Members marked as protected cannot be accessed from outside the class.
Example:
CODE SNIPPET IS HEREY2xhc3MgTXlDbGFzcyB7CgpwdWJsaWM6CgppbnQgcHVibGljVmFyOwoKdm9pZCBwdWJsaWNGdW5jKCkgewoKLy8gY29kZQoKfQoKCgoKcHJpdmF0ZToKCmludCBwcml2YXRlVmFyOwoKdm9pZCBwcml2YXRlRnVuYygpIHsKCi8vIGNvZGUKCn0KCgoKCnByb3RlY3RlZDoKCmludCBwcm90ZWN0ZWRWYXI7Cgp2b2lkIHByb3RlY3RlZEZ1bmMoKSB7CgovLyBjb2RlCgp9Cgp9Ow==
9. Explain the generational garbage collector in Java.
Generational garbage collection is a technique used in Java to manage memory by classifying objects based on their lifespans and allocating them accordingly to different generations. Java objects are formed in the heap, which is split into Young generation, Tenured or Old generation, and Perm area of the heap for the purpose of garbage collection.
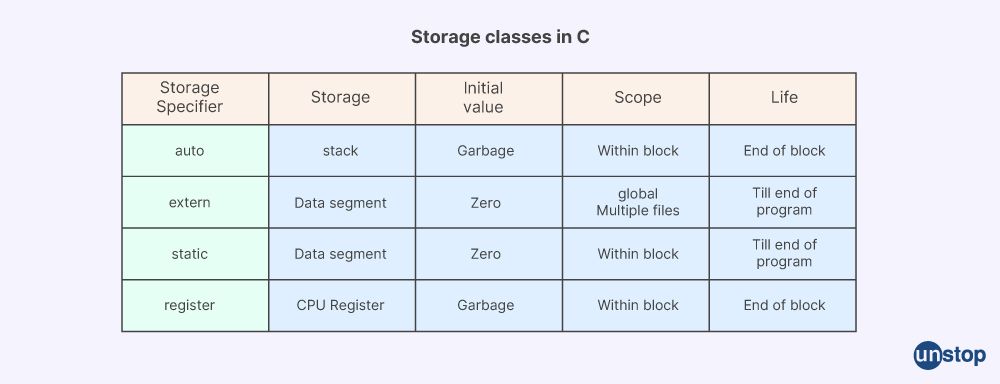
10. Tell me about the different storage classes in C.
In C programming language, there are four types of storage classes available. These classes are listed below:
AUTO: All local variables have this storage class by default. It is used to define variables that are local to a block or function. The variables declared with the auto storage class are automatically destroyed when the block or function is exited.
STATIC: This storage class is used to define variables that are local to a block or function but retain their values between function calls. The variables declared with the static storage class are initialized only once, and their values are retained between function calls.
REGISTER: The storage type called register is used to specify variables that need to be kept in registers rather than RAM. The variables declared with the register storage class are faster to access than those stored in RAM, but they have a limited size and cannot be accessed using the unary & operator.
EXTERN: Declaring variables that are declared in another file or module is done using this storage class. Although no memory is allocated for the variables declared with the extern storage class, they are utilized to access the variables defined in another file or module.
11. What's the difference between declaration and definition in C?
Here's a look at the difference between declaration and definition in C:
Declaration:
A declaration notifies the compiler that a variable or function declaration exists and provides basic information about a symbol, such as its type and name. No memory is allocated and no variable or function is initialized by a declaration.
Definition for a variable:
A definition gives a symbol's type, return type, name, memory allocation, and initialization, information. The body of a function or a variable's value are both parts of a definition. Multiple declarations of a variable are permitted, but it can be defined only once.
Example:
CODE SNIPPET IS HERELy8gRGVjbGFyYXRpb24gb2YgYSB2YXJpYWJsZQoKZXh0ZXJuIGludCB4OwoKCgoKLy8gRGVmaW5pdGlvbiBvZiBhIHZhcmlhYmxlCgppbnQgeCA9IDEwOwoKCgoKLy8gRGVjbGFyYXRpb24gb2YgYSBmdW5jdGlvbgoKaW50IGFkZChpbnQgYSwgaW50IGIpOwoKCgoKLy8gRGVmaW5pdGlvbiBvZiBhIGZ1bmN0aW9uCgppbnQgYWRkKGludCBhLCBpbnQgYikgewoKcmV0dXJuIGEgKyBiOw==
12. Define transaction atomicity in context to OS.
The Database management system’s transaction atomicity in context to OS guarantees that either all or none of the transaction activities are carried out. This means that a transaction is viewed as a single unit of operation that is either carried out entirely or not at all. This attribute assures that the database is consistent before and after the transaction, which is important.
13. Do you know the reason why a single serial port is controlled by a single interrupt-driven I/O and a front-end processor is managed by a polling I/O?
A single port is controlled by a single interrupt-driven I/O because I/O operations on a single serial port are infrequent and lengthy whereas, a front-end processor's I/O operations are frequent and short. Hence, in this situation, polling I/O is more effective than interrupt-driven I/O.
14. What is reference counting in OS and how does it deal with objects?
Reference counting is a memory management approach that counts the references, pointers, or handles to resources like objects, memory blocks, disc space, and others. It is an automatic memory management technique that enables the computer to recognize right away when it is appropriate to release a specific value or block of values from memory. However, when there are cyclic references, the reference counting method will fail to reclaim objects.
Reference counting deal with objects by keeping a count in each object, usually in a header, of how many references there are to it.
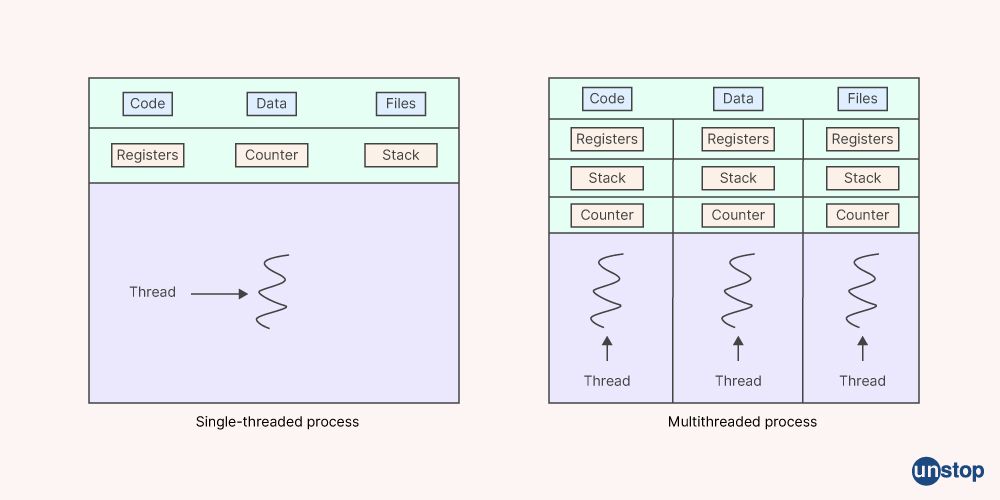
15. Tell me about the advantages and disadvantages of Threads.
Here are the major advantages and disadvantages of threads:
Advantages:
Increased responsiveness: Multithreading enables us to make our program more responsive and improve software structure simplicity.
Increased throughput: An application operating on a multiprocessor or multi-core system may experience a boost in throughput because of multithreading.
Efficient: Since identities and resources, such as the program counter, registers, and stack pointers, are shared, thread switching is incredibly effective and is far less expensive.
Lightweight: Threads are lightweight compared to processes, which means they require less overhead to create and manage.
Disadvantages:
Deadlocks: When two or more threads are waiting for each other to release resources, a deadlock might happen, leaving no threads moving forward.
Race circumstances: When two or more threads access memory concurrently, race conditions might happen, leading to unpredictable behaviour.
Context switching overhead: Switching between threads incurs a context switching overhead, which can impact performance.
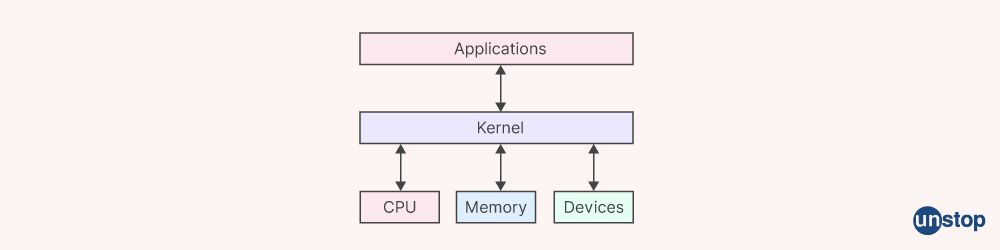
16. Define kernel.
The central element of an operating system that serves as a link between the hardware and software is called a kernel. It oversees system resources and offers fundamental services to all other OS components. The kernel assists with duties like process and memory management, file systems, and device drivers in addition to accessing computer resources like RAM and I/O devices.
17. What are DDL and DCL?
DDL and DCL are different types of SQL's domain-specific language.
Data Definition Language (DDL): DDL statements are used to describe the database schema as well as to create and modify the structure of database objects. CREATE, ALTER, and DROP are a few instances of DDL statements. Tables, indexes, and views are among the database objects that can be created, modified, and deleted using these statements.
DCL (Data Control Language): DCL statements are used to control access to the database and its objects. Some examples of DCL statements are GRANT and REVOKE. These statements are used to grant or revoke privileges and permissions to users and roles.
Unlock endless job and internship opportunities on Unstop!
18. Tell me the points of dissimilarities in hierarchical database models and network models.
There are several dissimilarities between hierarchical database models and network models, namely:
Hierarchical Database:
The hierarchical structure provides data organization in the form of a tree with a single root to which all other data is connected.
A child node will only have one parent node in this architecture.
It supports one-to-many relationships.
It does not support many-to-many relationships.
It supports only simple relationships between entities.
Network Models:
Network model organizes data in a graph-like structure, where each parent can have multiple children and children can also have multiple parents.
It supports many-to-many relationships.
The data is arranged in the form of a graph.
It supports more interrelations between entities than the hierarchical model.
It allows more relationships to be established in the database model, making data access easier and faster.
19. What is Hash join, Sort Merge join and Nested Loop join?
HASH JOIN:
When massive, unsorted, and non-indexed data (which are found in tables) needs to be combined, a hash join is utilized. Hash join is used primarily when larger tables need to be joined. When big, unsorted, and non-indexed data from tables need to be linked, hash join is the ideal approach for us to use.
SORT MERGE JOIN:
This join has two phases in the join algorithm, namely, the sort phase and the merge phase. It is usually used to join two independent sources of data represented in a sorted order. Merge algorithm is the fastest join algorithm. This is the reason that Sort Merge join is the fastest in case of sorted relations.
NESTED LOOP JOIN:
A nested loop is employed when we need to combine two relationships. This is the simplest join type, which works best with little amounts of data and less frequent transactions. This join uses an internal join technique, therefore it is invisible to the naked eye. It is handled by creating an outer loop within an inner loop, and then the inner loop is processed separately for less number of entries.

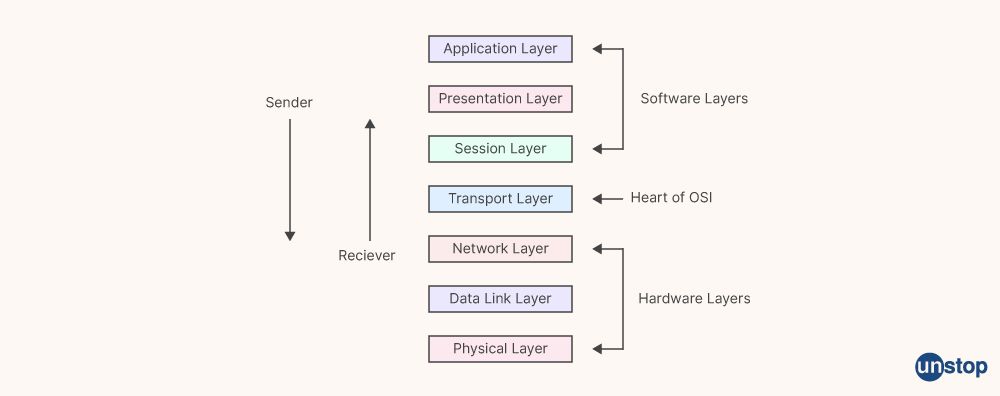
20. Explain the physical layers in the OSI model?
The physical layer is the first and lowest layer in the OSI (Open Systems Interconnection) model of computer networking. It is responsible for the actual physical connection between the devices by identifying the equipment involved in the data transfer. The physical layer is made up of different types of cables, connectors, receivers, and connectors. It specifies how to use physical links to connect network nodes instead of logical data packets to send raw bits.
21. What is a star topology?
A network structure known as a star topology connects each device to a central hub or switch, which acts as a channel for messages. Point-to-point connections are used to connect each device to the hub or switch. The connecting nodes behave as clients, and the central hub functions as a server. The central node can transmit packets to other nodes in the network after receiving them from connecting nodes. In star networks, the central node and connecting devices must be connected from point to point to form the channel for messages. A hub-and-spoke network topology is another name for star topology.
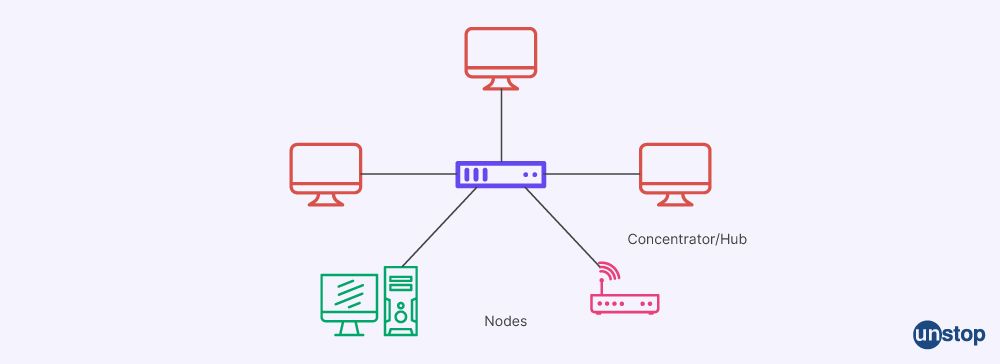
22. Explain tunneling protocol.
By encapsulating packets at the peer level or lower, the tunneling protocol enables the secure transfer of data between networks. It entails using a technique called encapsulation that enables private network communications to be sent across a public network (like the Internet).
23. What's the difference between CSMA/CD (Carrier Sense Multiple Access / Collision Detection) and CSMA/CA (Carrier Sense Multiple Access / Collision Avoidance)?
CSMA (Carrier Sense Multiple Access) is a protocol used in network communication. It is divided into two parts: CSMA CA (Collision Avoidance) and CSMA CD (Collision Detection). Here are the key differences between the two:
CSMA/CD (Carrier Sense Multiple Access / Collision Detection)
CSMA/CD is a carrier transmission network protocol that stops the transmission when a collision or interrupt signal is detected and sends a jam signal before waiting for a random time context before retransmission.
CSMA/CD is used to detect collisions after their occurrence.
It is used in the medium access control layer that monitors the interaction between wireless transmission mediums.
It resends the data frame whenever a conflict occurs.
It detects collisions by broadcast sensing from the other channel for broadcasting.
It is used for collision detection on a shared channel within a very short time.
CSMA/CA (Carrier Sense Multiple Access / Collision Avoidance)
CSMA/CA is used to prevent collisions prior to their occurrence.
It sends a request to send (RTS) signal before transmitting data packets on a network.
It then transmits the intent to send for data transmission.
It is effective before a collision.
24. Define SMTP.
SMTP stands for Simple Mail Transfer Protocol and is an application layer protocol. It is a widely used communication protocol for sending electronic mail over the Internet. Email transmission between servers and client process is its main application. POP (post office protocol) or IMAP (internet message access protocol) are pull protocols and are used to retrieve emails at the recipient's end, while SMTP (simple mail transfer protocol) is a push protocol used to send mail.
When an SMTP process notices a TCP (Transmission Control Protocol) connection from any client, it creates a connection. As soon as a TCP connection is successfully established, the client process sends the letter.
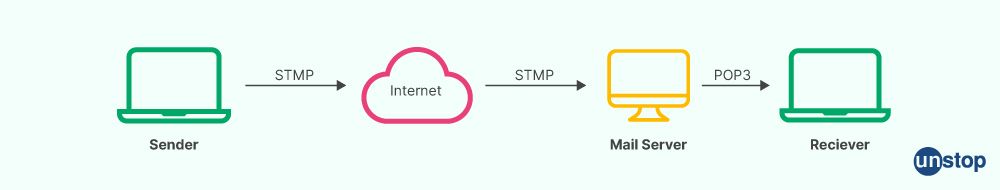
25. Explain stored procedure and triggers in SQL.
Stored procedure:
A stored procedure in SQL is a set of SQL statements that perform some defined actions and are stored together in a database as a named object. Stored procedures are used to group one or more SQL statements into logical units. They can be reused over and over again, saving coding effort and programming time.
Triggers:
A unique class of stored procedure is called a trigger which is launched automatically when an event takes place. It is connected to a table and only fires off when something is inserted, updated, or deleted. Triggers are employed to keep the database's data's integrity. Unlike stored procedures, triggers cannot be executed explicitly.
26. Tell me when an implicit cursor is created.
Implicit cursors are created automatically by Oracle when a SQL statement (a domain-specific language) is executed and there isn't an explicit cursor for the statement. Because they do not need to be declared, opened, fetched, and closed separately, implicit cursors can fetch a single row at a time and are quicker than explicit cursors.
27. Differentiate between lists and tuples in Python.
Lists:
Lists are an ordered collection of items, and they can contain duplicate values. Lists can have their contents modified after they are generated because they are mutable. Lists are widely used to store and manipulate data that needs to be regularly sorted or modified.
Tuples:
Tuples are an ordered collection of items. It is immutable which implies that their contents cannot be changed after they have been created. It's important to note that while the elements within tuples can't be modified individually, you can create new tuples with different values. Dates and coordinates are common examples of linked data that should not be modified, and can be stored and transmitted using tuples.
28. Tell 2 key features of Java.
Two key features of Java are:
Object-oriented: Everything in Java is an object, which makes it simple to extend and modify. This makes Java object-oriented.
Platform-independent: Java is a platform-independent programming language that is portable. Any platform with a JVM installed can run Java bytecode.
29. What is a DISTINCT keyword in SQL?
To remove duplicate records and retrieve only unique records, the SELECT statement and the DISTINCT keyword are used in SQL.
SYNTAX:
SELECT DISTINCT column1, column2, ... FROM table_name;
30. Explain object lock.
Object locks in OS refer to the ways to acquire locks on specific systems or application objects. Object lock is a mechanism that allows multiple threads to access an object in a mutually exclusive way, ensuring that only one thread can access the object at a time.
31. Tell me the name of the memory space available in C++?
There are three types of memory space available in C++, namely:
Stack: A data structure that adheres to the LIFO (Last In First Out) principle is a stack. The stack is created as a container adaptor, a class that uses an enclosed object of a certain container class as its underlying container.
Heap: This is the location where the new or malloc operators are used to allocate dynamic memory. The heap is a part of memory that the compiler does not automatically manage, therefore it is up to the programmer to allocate and deallocate memory there.
Static: Static variables and constants are kept in this section. Once initialised, static variables retain their values for the duration of the program.
32. Tell me the names of different types of arguments present in C++.
In C++, there are two types of arguments, namely:
Value arguments: A copy of the argument is passed on to the function when using that kind of argument.
Reference arguments: A reference to the argument is passed to the function in this kind of argument.
33. Is this statement true: Interrupt is a hardware method?
Yes, an interrupt is a hardware method.
An interrupt is a signal sent to the processor by hardware or software to let it know that something has to be addressed right away. An external device, such as a disc controller or an external peripheral, will send the processor an electronic alerting signal known as a hardware method interrupt.
34. What is the default value of an uninitialized int variable in Java?
The default value of an uninitialized int variable in Java is 0.
35. Does a primary key in SQL support auto-incrementing value?
Yes, a primary key in SQL supports auto-incrementing value. Because of auto-incrementing value, it is possible to generate a unique integer whenever a new entry is added to a database.
36. Tell me the difference between char and varchar.
The differences between char and varchar are:
| CHAR | VARCHAR |
| Character strings of a defined length are stored using the CHAR datatype. |
Character strings of varying lengths are stored using the VARCHAR datatype. |
| CHAR means character. | VARCHAR means Variable Character. |
| The storage size for CHAR datatypes depends on the specified length. | The actual length of the entered string in bytes corresponds to the storage size of the VARCHAR datatype. |
37. What do you mean by volatile keyword in Java?
Java uses the volatile keyword to allow separate threads to change a variable's value and to make classes thread-safe. It implies that there won't be any issues if many threads simultaneously use a method and an instance of a class.
38. What do you mean by JAR File?
A JAR file (Java Archive) is a package file type used to compile and distribute several Java class files along with the related information and resources (text, pictures, etc.). JAR file is used to compress and group several files into a single platform-independent file format and is based on the well-known ZIP file format. Java runtimes can effectively deploy a full application—including its classes and resources—in a single request thanks to JAR files.
39. What is application layer protocol?
The topmost layer in the OSI and TCP/IP models is the application layer. The shared communications protocols and interface techniques used by the hosts in a communications network are specified by this application layer protocol. The application layer protocols are used to speed up, improve the effectiveness, secure, and reliably transmit data between sender and receiver.
40. Define custom objects.
Custom objects are used to store particular data or information relating to an organization.
They can be subclassed, independently securable, and persisted in the object store. Custom objects can store arbitrary JSON-formatted data and have a user-defined unique identifier within the defined container. They are defined in a specific view where the properties associated with the custom object are defined.
41. Tell me about autonomous memory management.
Autonomous memory management automates the allocation and deallocation of memory, without the requirement for manual intervention. It is a kind of automatic memory management that evenly distributes the available memory across different components as needed, enabling the system to make the most of the memory that is available. Numerous systems, including Oracle, Couchbase, and self-driving cars, use autonomous memory management.
42. Which operator will you use to compare the conflicting objects?
We will use the 'equals()' operator to compare the conflicting objects.
Deloitte HR Interview Questions
Apart from the technical interview, the Deloitte recruitment process also includes an HR round. This round usually includes behavioral or situation-based questions that test an applicant's communication skills, time-management skills, etc.
Here are some common interview questions that can be asked in the HR round:
1. Tell us something about yourself.
This is one of the most commonly asked questions in job interviews and yet one that most people struggle to answer. It's important to not overthink your answer but rather, be honest. A great way to differentiate your answer is by focusing on the skill sets or experiences that go beyond your work history. In fact, when answering this question, try to focus on skill sets that are not highlighted or included in your resume.
Sample answer: I'm someone who loves to experiment with new things. This is why I joined multiple clubs in college and was able to actively contribute to each. This actually taught me the value of paying attention to details and working with people with different opinions. Apart from this, my latest love is podcasts - and I enjoy listening to them on my way to college or work.
2. Why Deloitte?
This is a common question in Deloitte interviews. When answering these, applicants should try and align their personal goals and ambition with the opportunities available at the organization. This allows them to provide a more personalized answer to the question. Candidates may tailor their responses to the role they're applying for.
Sample answer: I wish to work with Deloitte, a global leader in consulting and advisory services. It has a diverse set of service offerings that will enable me to build a versatile skill set, while also providing me with the kind of exposure I'm looking for at this stage in my career. Deloitte has also consistently ranked among the 100 best places to work and has a strong commitment to employee growth - and that makes the idea of working with Deloitte even more exciting.
3. How do you handle multiple deadlines?
Interviewers ask this question to test your time-management skills. Additionally, the nature of work at Deloitte is such that candidates may be expected to simultaneously work on multiple projects. When answering, focus on practical tips that you've employed in the past.
Sample answer - I employ and divide and conquer approach to handling multiple deadlines. I divide my work into short, achievable targets. This acts as a source of motivation, since with each completed goal, I am one step closer to achieving my target. I also prioritize the work based on urgency and complexity so that I can properly understand the time required for each task and plan accordingly.
4. How do you deal with stressful situations at work?
Irrespective of an applicant's competency level or the organizational structure, a stressful situation may occur at the workplace. And interviewers want to understand how applicants respond to such stressful or difficult situations at work. When answering, give examples of past experiences, if any, or provide actual solutions rather than a vague response.
A - I understand that there can be stress-inducing situations at work but I try to focus on the task at hand and move ahead. I also believe in asking for help where required and collaborating to produce the best results. It was the same approach that I followed when I was organizing my college fest. We faced many stressful situations, including a time when one of our main performers for the night had to back out due to health concerns. Disappointing the crowd was not an option here. Instead of wasting that time, I planned an impromptu open mic, inviting the crowd to participate. It actually ended up being one of the highlights of the fest.
5. Are you willing to relocate?
Deloitte has a worldwide presence and its business model is one where relocation is common. Thus, this is a common question that applicants face. When answering, it's important to give a genuine answer. If you're not open to relocating, be sure to provide adequate reasoning for it. If you're open to relocating, this is an opportunity to ask for any additional information about the process, if needed.
A- Yes I am open to relocation but I would like to understand what resources and support are provided to relocating employees.
Deloitte Recruitment Process
Deloitte's expansive offerings and impressive client base, along with its work culture, make it a dream organization to work for. But, it's not easy landing a job at one of the most well-known MNCs in the world. Thus, it's better to read about the organization and job description in detail and gather information about the recruitment process.
The Deloitte recruitment process is broadly divided into three parts, namely an aptitude test, a group discussion or just-a-minute (JAM) round, and the interview round(s). There are usually multiple rounds of interviews, but the two most common are - a technical interview to test your technical skills and an HR round to understand if you're the right fit for the job role and the organization.
Read ahead to understand what each round entails:
i) Aptitude Test:
Applicants whose resumes get shortlisted have to take an aptitude or assessment test. It usually takes place online. The Deloitte aptitude test includes questions on quantitative, verbal, and logical reasoning.
In certain cases, experienced professionals may not be required to undergo an aptitude test.
ii) Group Discussion/Just-a-Minute (JAM) round:
The Deloitte recruitment process also includes a group discussion round. The group discussion is usually based on a case study. Applicants get a short time to study the case study and then 15 minutes to discuss it.
In some cases, instead of a group discussion, applicants may undergo a JAM round. A JAM round is where interviewers ask applicants to speak for a minute on an assigned topic.
iii) Interview Round - HR
The HR round usually covers behavioral and situational questions. These questions test how an individual's communication skills, time management skills, and response to stressful situations, among other skill sets.
iv) Interview Round - Technical
As the name suggests, this round tests an applicant's technical skills. It's usually conducted by a senior member of the team or a panel. Since the round tests an applicant's technical skill level, applicants who make it to this interview stage should be well-versed in job-specific technical knowledge. They should also be able to explain the responsibilities of their current role (in the case of experienced professionals).
The basic recruitment process at Deloitte usually includes the aforementioned rounds. However, additional questions (like management interview questions) or rounds may be added for a more senior role. Similarly, a round may even be skipped depending on the job role and the experience required by the applicants.
Discussions on salary expectations may take place in either of the interview rounds or happen at the end of all interview rounds. Applicants should ideally gather information about the starting salary for freshers that Deloitte and its competitors offer if this is their first role. Seasoned professionals should also, ideally, be aware of the salary trends in the industry and negotiate accordingly.
Applicants can also refer to Deloitte's tips on answering commonly asked questions. This is one of the most useful interview preparation resources for Deloitte and can help improve your chances of success.
Applicants who clear all the interview rounds and receive an appointment letter have to undergo an orientation and training program as part of the onboarding. It's important that candidates pay attention to the orientation program to better understand corporate policies and organizational structure, among other things. Post the onboarding begins your Deloitte journey!
You may also be interested in the following:
I am a storyteller by nature. At Unstop, I tell stories ripe with promise and inspiration, and in life, I voice out the stories of our four-legged furry friends. Providing a prospect of a good life filled with equal opportunities to students and our pawsome buddies helps me sleep better at night. And for those rainy evenings, I turn to my colors.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter
Blogs you need to hog!

This Is My First Hackathon, How Should I Prepare? (Tips & Hackathon Questions Inside)

10 Best C++ IDEs That Developers Mention The Most!

Advantages and Disadvantages of Cloud Computing That You Should Know!










Comments
Add comment