- TCS Technical Interview Questions & Answers
- TCS Managerial Interview Questions & Answers
- TCS HR Interview Questions & Answers
- Overview of Cognizant Recruitment Process
- Cognizant Interview Questions: Technical
- Cognizant Interview Questions: HR Round
- Overview of Wipro Technologies Recruitment Rounds
- Wipro Interview Questions
- Technical Round
- HR Round
- Online Assessment Sample Questions
- Frequently Asked Questions
- Overview of Google Recruitment Process
- Google Interview Questions: Technical
- Google Interview Questions: HR round
- Interview Preparation Tips
- About Google
- Deloitte Technical Interview Questions
- Deloitte HR Interview Questions
- Deloitte Recruitment Process
- Technical Interview Questions and Answers
- Level 1 difficulty
- Level 2 difficulty
- Level 3 difficulty
- Behavioral Questions
- Eligibility Criteria for Mindtree Recruitment
- Mindtree Recruitment Process: Rounds Overview
- Skills required to crack Mindtree interview rounds
- Mindtree Recruitment Rounds: Sample Questions
- About Mindtree
- Preparing for Microsoft interview questions
- Microsoft technical interview questions
- Microsoft behavioural interview questions
- Aptitude Interview Questions
- Technical Interview Questions
- Easy
- Intermediate
- Hard
- HR Interview Questions
- Eligibility criteria
- Recruitment rounds & assessments
- Tech Mahindra interview questions - Technical round
- Tech Mahindra interview questions - HR round
- Hiring process at Mphasis
- Mphasis technical interview questions
- Mphasis HR interview questions
- About Mphasis
- Technical interview questions
- HR interview questions
- Recruitment process
- About Virtusa
- Goldman Sachs Interview Process
- Technical Questions for Goldman Sachs Interview
- Sample HR Question for Goldman Sachs Interview
- About Goldman Sachs
- Nagarro Recruitment Process
- Nagarro HR Interview Questions
- Nagarro Aptitude Test Questions
- Nagarro Technical Test Questions
- About Nagarro
- PwC Recruitment Process
- PwC Technical Interview Questions: Freshers and Experienced
- PwC Interview Questions for HR Rounds
- PwC Interview Preparation
- Frequently Asked Questions
- EY Technical Interview Questions (2023)
- EY Interview Questions for HR Round
- About EY
- Morgan Stanley Recruitment Process
- HR Questions for Morgan Stanley Interview
- HR Questions for Morgan Stanley Interview
- About Morgan Stanley
- Recruitment Process at Flipkart
- Technical Flipkart Interview Questions
- Code-Based Flipkart Interview Questions
- Sample Flipkart Interview Questions- HR Round
- Conclusion
- FAQs
- Recruitment Process at Paytm
- Technical Interview Questions for Paytm Interview
- HR Sample Questions for Paytm Interview
- About Paytm
- Most Probable Accenture Interview Questions
- Accenture Technical Interview Questions
- Accenture HR Interview Questions
- Amazon Recruitment Process
- Amazon Interview Rounds
- Common Amazon Interview Questions
- Amazon Interview Questions: Behavioral-based Questions
- Amazon Interview Questions: Leadership Principles
- Company-specific Amazon Interview Questions
- 43 Top Technical/ Coding Amazon Interview Questions
- Juspay Recruitment: Stages and Timeline
- Juspay Interview Questions and Answers
- How to prepare for Juspay interview questions
- Prepare for the Juspay Interview: Stages and Timeline
- Frequently Asked Questions
- Adobe Interview Questions - Technical
- Adobe Interview Questions - HR
- Recruitment Process at Adobe
- About Adobe
- Cisco technical interview questions
- Sample HR interview questions
- The recruitment process at Cisco
- About Cisco
- JP Morgan interview questions (Technical round)
- JP Morgan interview questions HR round)
- Recruitment process at JP Morgan
- About JP Morgan
- Wipro Elite NTH: Selection Process
- Wipro Elite NTH Technical Interview Questions
- Wipro Elite NTH Interview Round- HR Questions
- BYJU's BDA Interview Questions
- BYJU's SDE Interview Questions
- BYJU's HR Round Interview Questions
- A Quick Overview of the KPMG Recruitment Process
- Technical Questions for KPMG Interview
- HR Questions for KPMG Interview
- About KPMG
- DXC Technology Interview Process
- DCX Technical Interview Questions
- Sample HR Questions for DXC Technology
- About DXC Technology
- Recruitment Process at PayPal
- Technical Questions for PayPal Interview
- HR Sample Questions for PayPal Interview
- About PayPal
- Capgemini Recruitment Rounds
- Capgemini Interview Questions: Technical round
- Capgemini Interview Questions: HR round
- Preparation tips
- FAQs
- Technical interview questions for Siemens
- Sample HR questions for Siemens
- The recruitment process at Siemens
- About Siemens
- HCL Technical Interview Questions
- HR Interview Questions
- HCL Technologies Recruitment Process
- List of EPAM Interview Questions for Technical Interviews
- About EPAM
- Atlassian Interview Process
- Top Skills for Different Roles at Atlassian
- Atlassian Interview Questions: Technical Knowledge
- Atlassian Interview Questions: Behavioral Skills
- Atlassian Interview Questions: Tips for Effective Preparation
- Walmart Recruitment Process
- Walmart Interview Questions and Sample Answers (HR Round)
- Walmart Interview Questions and Sample Answers (Technical Round)
- Tips for Interviewing at Walmart and Interview Preparation Tips
- Frequently Asked Questions
- Uber Interview Questions For Engineering Profiles: Coding
- Technical Uber Interview Questions: Theoretical
- Uber Interview Question: HR Round
- Uber Recruitment Procedure
- About Uber Technologies Ltd.
- Intel Technical Interview Questions
- Computer Architecture Intel Interview Questions
- Intel DFT Interview Questions
- Intel Interview Questions for Verification Engineer Role
- Recruitment Process Overview
- Important Accenture HR Interview Questions
- Points to remember
- What is Selenium?
- What are the components of the Selenium suite?
- Why is it important to use Selenium?
- What's the major difference between Selenium 3.0 & Selenium 2.0?
- What is Automation testing and what are its benefits?
- What are the benefits of Selenium as an Automation Tool?
- What are the drawbacks to using Selenium for testing?
- Why should Selenium not be used as a web application or system testing tool?
- Is it possible to use selenium to launch web browsers?
- What does Selenese mean?
- What does it mean to be a locator?
- Identify the main difference between "assert", and "verify" commands within Selenium
- What does an exception test in Selenium mean?
- What does XPath mean in Selenium? Describe XPath Absolute & XPath Relation
- What is the difference in Xpath between "//"? and "/"?
- What is the difference between "type" and the "typeAndWait" commands within Selenium?
- Distinguish between findElement() & findElements() in context of Selenium
- How long will Selenium wait before a website is loaded fully?
- What is the difference between the driver.close() and driver.quit() commands in Selenium?
- Describe the different navigation commands that Selenium supports
- What is Selenium's approach to the same-origin policy?
- Explain the difference between findElement() in Selenium and findElements()
- Explain the pause function in SeleniumIDE
- Explain the differences between different frameworks and how they are connected to Selenium's Robot Framework
- What are your thoughts on the Page Object Model within the context of Selenium
- What are your thoughts on Jenkins?
- What are the parameters that selenium commands come with a minimum?
- How can you tell the differences in the Absolute pathway as well as Relative Path?
- What's the distinction in Assert or Verify declarations within Selenium?
- What are the points of verification that are in Selenium?
- Define Implicit wait, Explicit wait, and Fluent
- Can Selenium manage windows-based pop-ups?
- What's the definition of an Object Repository?
- What is the main difference between obtainwindowhandle() as well as the getwindowhandles ()?
- What are the various types of Annotations that are used in Selenium?
- What is the main difference in the setsSpeed() or sleep() methods?
- What is the way to retrieve the alert message?
- How do you determine the exact location of an element on the web?
- Why do we use Selenium RC?
- What are the benefits or advantages of Selenium RC?
- Do you have a list of the technical limitations when making use of Selenium RC? Selenium RC?
- What's the reason to utilize the TestNG together with Selenium?
- What Language do you prefer to use to build test case sets in Selenium?
- What are Start and Breakpoints?
- What is the purpose of this capability relevant in relation to Selenium?
- When do you use AutoIT?
- Do you have a reason why you require Session management in Selenium?
- Are you able to automatize CAPTCHA?
- How can we launch various browsers on Selenium?
- Why should you select Selenium rather than QTP (Quick Test Professional)?
- Airbus Interview Questions and Answers: HR/ Behavioral
- Industry/ Company-Specific Airbus Interview Questions
- Airbus Interview Questions and Answers: Aptitude
- Airbus Software Engineer Interview Questions and Answers: Technical
- Importance of Spring Framework
- Spring Interview Questions (Basic)
- Advanced Spring Interview Questions
- C++ Interview Questions and Answers: The Basics
- C++ Interview Questions: Intermediate
- C++ Interview Questions And Answers With Code Examples
- C++ Interview Questions and Answers: Advanced
- Test Your Skills: Quiz Time
- MBA Interview Questions: B.Com Economics
- B.Com Marketing
- B.Com Finance
- B.Com Accounting and Finance
- Business Studies
- Chartered Accountant
- Q1. Please tell us something about yourself/ Introduce yourself to us.
- Q2. Describe yourself in one word.
- Q3. Tell us about your strengths and weaknesses.
- Q4. Why did you apply for this job/ What attracted you to this role?
- Q5. What are your hobbies?
- Q6. Where do you see yourself in five years OR What are your long-term goals?
- Q7. Why do you want to work with this company?
- Q8. Tell us what you know about our organization
- Q9. Do you have any idea about our biggest competitors?
- Q10. What motivates you to do a good job?
- Q11. What is an ideal job for you?
- Q12. What is the difference between a group and a team?
- Q13. Are you a team player/ Do you like to work in teams?
- Q14. Are you good at handling pressure/ deadlines?
- Q15. When can you start?
- Q16. How flexible are you regarding overtime?
- Q17. Are you willing to relocate for work?
- Q18. Why do you think you are the right candidate for this job?
- Q19. How can you be an asset to the organization?
- Q20. What is your salary expectation?
- Q21. How long do you plan to remain with this company?
- Q22. What is your objective in life?
- Q23. Would you like to pursue your Master's degree anytime soon?
- Q24. How have you planned to achieve your career goal?
- Q25. Can you tell us about your biggest achievement in life?
- Q26. What was the most challenging decision you ever made?
- Q27. What kind of work environment do you prefer to work in?
- Q28. What is the difference between a smart worker and a hard worker?
- Q29. What will you do if you don't get hired?
- Q30. Tell us three things that are most important for you in a job.
- Q31. Who is your role model and what have you learned from him/her?
- Q32. In case of a disagreement, how do you handle the situation?
- Q33. What is the difference between confidence and overconfidence?
- Q34. If you have more than enough money in hand right now, would you still want to work?
- Q35. Do you have any questions for us?
- Interview Tips for Freshers
- Tell me about yourself
- What are your greatest strengths?
- What are your greatest weaknesses?
- Tell me about something you did that you now feel a little ashamed of
- Why are you leaving (or did you leave) this position??
- 15+ resources for preparing most-asked interview questions
- CoCubes Interview Process Overview
- Common CoCubes Interview Questions
- Key Areas to Focus on for CoCubes Interview Preparation
- Conclusion
- Frequently Asked Questions (FAQs)
- Data Analyst Interview Questions With Answers
- About Data Analyst
Trending 70+ AWS Interview Questions That You Must Prepare!

AWS is Amazon Web Services offered by Amazon, a cloud computing platform that provides its users with global cloud-based services and products and database storage. It is the most common cloud platform.
Thanks to AWS's highly dependable, scalable, and affordable infrastructure platform, businesses can replace upfront capital infrastructure costs with low variable costs. Millions of customers, including startups, large businesses, and top government agencies, use AWS to save costs, improve security, become more agile, and innovate more quickly through AWS's cloud computing solutions.
AWS Interview Questions and Answers (2026)
Q1. What do you understand by Cloudwatch?
AWS cloud resources and the apps that run on AWS or cloud applications are monitored by Amazon CloudWatch.
CloudWatch is employed to collect data, monitor log files, trigger alarms, and automatically respond to changes in your Amazon Web Services (AWS) resources. To simplify infrastructure and application maintenance, CloudWatch gathers and displays real-time logs, metrics, and event data in automated dashboards.
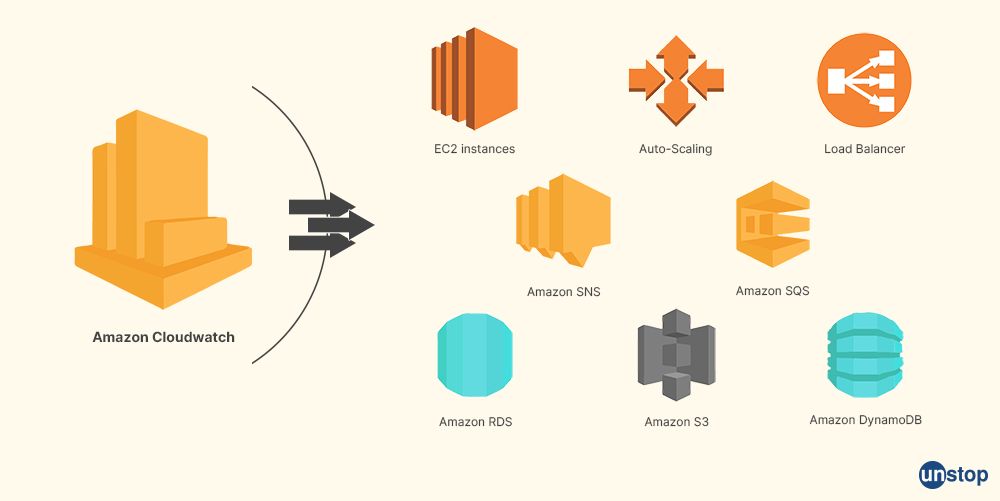
Q2. Explain about EC2.
A web service interface called Amazon Elastic Computation Cloud (EC2) offers resizable computation capacity in the AWS cloud. The Amazon Web Services (AWS) component EC2 enables users to rent virtual computers on which they can run their own computer programs.
EC2 offers a web service through which a user can boot an Amazon Machine Image (AMI) to set up a virtual machine, or what Amazon refers to as an "instance," with whatever software they choose. It acts as an on-demand computing resource for applications. It is similar to on-premises servers.
Q3. Explain the word Snowball.
AWS Snowball is a petabyte-scale data transit service that moves enormous volumes of data into and out of the AWS Cloud using safe devices. Snowball offers the most practical way to move data locally and across a wide network. Using Snowball, users can send up to 50 TB of data straight from their location to the AWS network. It is a data transit solution that speeds up the transfer of terabytes to petabytes of data into and out of Amazon Web Services services.
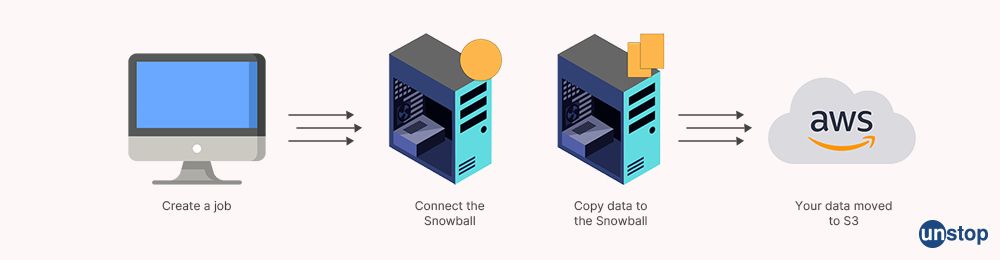
Q4. What do you know about Elastic Transcoder?
A media transcoding service in the cloud called Amazon Elastic Transcoder is intended to be a highly scalable, simple-to-use, and affordable way for developers and businesses to change media files from their original format into versions that can be played back on gadgets like smartphones, tablets, and PCs.
For the purpose of producing media files that can be played back on a certain range of devices, Elastic Transcoder offers pre-defined presets. Elastic Transcoder offers to monitor for AWS resources and client applications that are operating on the Amazon infrastructure.
Q5. What is VPC?
A commercial cloud computing service called Amazon Virtual Private Cloud or VPC offers a logically isolated virtual network that you define. VPC allows you to launch AWS resources into a defined virtual network that closely resembles a physical network that you would run in your own data center while utilizing the advantages of the scalable AWS architecture.
The Amazon Elastic Compute Cloud (Amazon EC2) instances in each subnet can be accessed using several layers of protection, such as security groups and network access control lists, thanks to VPC. Virtual Private Clouds (VPC), subnets, internet gateways, VPN (Virtual Private Network) connections, and flow logs are features that VPC offers so that you may improve and monitor the security for your VPC.
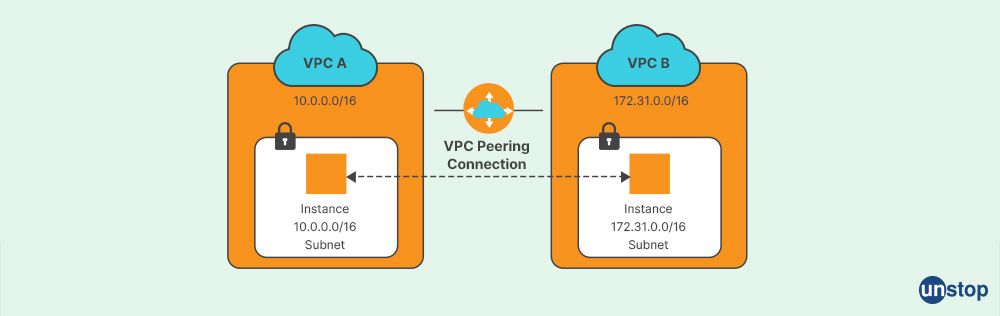
Q6. The DNS and load balancing come under which cloud service?
DNS and Load Balancer Services are Infrastructure As A Service (IaaS) type of Cloud Services.
Q7. What are the storage classes available in the Amazon S3 bucket?
The storage classes available in the S3 bucket are:
- S3 Standard: This storage class offers excellent durability, availability, and performance and is intended for frequently accessed data.
- S3 Intelligent-Tiering: This class is intended for data with erratic or shifting access patterns. Based on shifting access patterns, it automatically shifts items between two access tiers while also conserving money.
- S3 Standard-Infrequent Access: This storage type is intended for persistent data that is accessed infrequently. At a reduced price, it provides S3 Standard's great performance, availability, and durability.
- S3 One Zone-Infrequent Access: This is intended for rarely accessed data that can be rebuilt in the event of a loss. It offers a more affordable option than S3 Standard-Infrequent Access and stores data in a single availability zone.
- S3 Glacier: This is intended for long-term data archiving. It provides affordable choices for retrieving and storing infrequently used data.
- S3 Glacier Deep Archive: This is intended for long-term data archiving with retrieval periods of at least 12 hours. It provides the most affordable storage choice for infrequently accessed data.
Q8. What exactly are T2 instances?
T2 instances are a particular kind of Amazon Elastic Compute Cloud (EC2) instance that offers a base level of CPU performance with the option to burst above the base when necessary.
For applications that periodically need to burst to higher CPU performance but do not require sustained high CPU performance, T2 instances are the best option. Burstable Performance Instances (T2 instances) accumulate CPU Credits when inactive and use CPU Credits when active.
Q9. What do you understand by key pairs in AWS?
When connecting to an Amazon Elastic Compute Cloud (EC2) instance, key pairs are used to establish identity. The user stores the private key, whereas Amazon EC2 stores the public key on the instance. It is a set of security credentials
Q10. What number of subnets can a VPC support?
Users have 200 subnets per Virtual Private Cloud (VPC) in Amazon Web Services (AWS). Users can open a case at the AWS help center if they need to add new subnets. You can raise this restriction by contacting AWS support.
Unlock endless job & internship opportunities!
Q11. List the types of cloud services.
Below are different types of cloud services.
- Infrastructure as a Service (IaaS): You can access computing resources, including virtual computers, storage, and networking by IaaS.
- Platform as a Service (PaaS): Users can create, run, and administer applications on a cloud platform provided by PaaS without worrying about the supporting infrastructure.
- Software as a Service (SaaS): You can have access to software programs that are hosted and managed by a third-party provider through SaaS.
- Serverless: In serverless computing, the cloud provider controls the infrastructure and automatically distributes resources as needed.
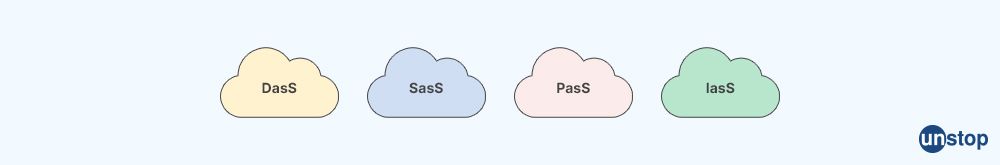
Q12. What do you mean by S3 bucket?
S3 or Simple Storage Service is an Amazon Web Services (AWS) cloud-based object storage service that enables customers to store and access data from any location on the internet. Large volumes of data, like those found in backups, archives, and data lakes, can be stored and accessed with ease using S3. S3(Simple Storage Service) storage classes were created with the specific intent of offering the most affordable storage for various usage patterns.
S3 storage classes can be set up at the object level, and a bucket can hold objects spread out amongst number of different storage classes.
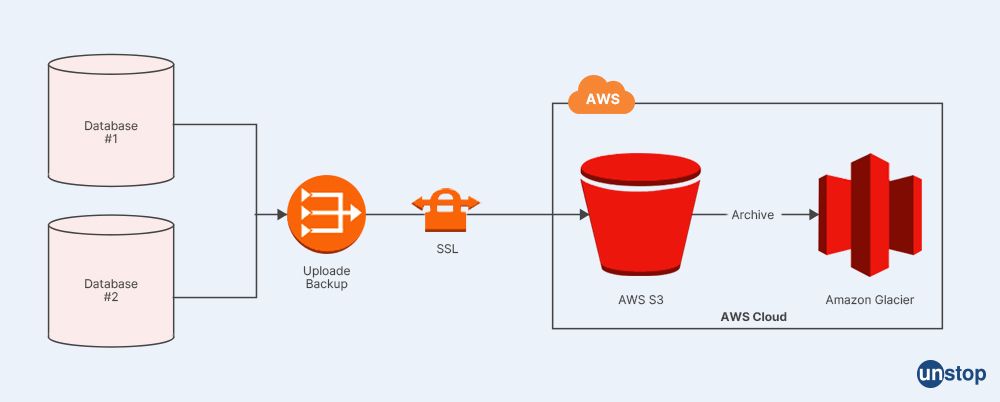
Q13. Do you have an idea how high availability and low latency are given by Amazon Route 53?
Utilizing the dependable and highly available infrastructure of AWS, Amazon Route 53 offers high availability and minimal latency. By avoiding any internet- or network-related problems, Route 53 is designed to employ a globally dispersed network of DNS servers that help assure a consistent ability to route end users to applications.
Route 53 is made to automatically respond to inquiries from the best location depending on network conditions, giving end users the lowest query latency possible. Additionally, Route 53 supports Availability Zones, enabling seamless application and database failover between Availability Zones.
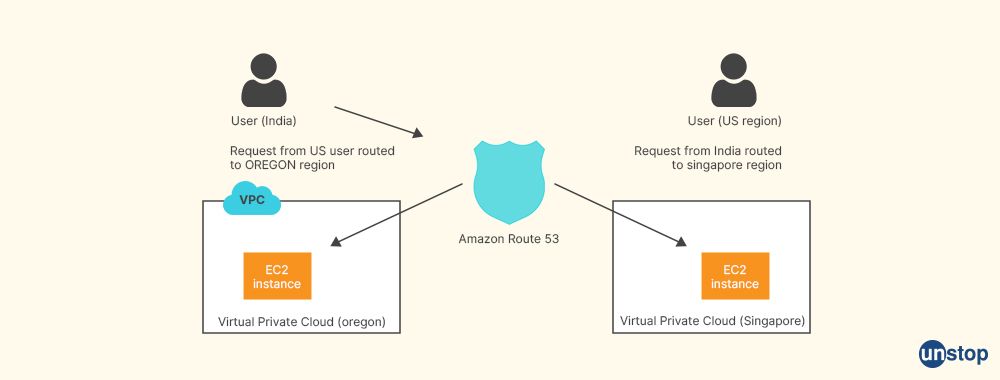
Q14. How does Amazon S3 (Simple Storage Service) get requests?
To send a request to Amazon S3, you can use the REST API or the AWS SDK. In Amazon S3, every contact is either authenticated or anonymous, and requests that are authenticated must contain a value known as the sender's signature.
You must utilize the access key ID and secret key, which are used to uniquely identify an AWS account, in order to send authenticated queries to Amazon S3. Using the REST API or the AWS SDK, you can submit authenticated requests to Amazon S3 using these access credentials.
Q15. What do you think an AMI includes?
AMI is a unique class of virtual appliances that act as the fundamental deployment component for EC2 services.
The main component of an AMI is a read-only file system image that includes an operating system (e.g., Linux, Unix, or Windows) and any additional software required to deliver a service or a portion of it.
An AMI also has launch permissions that control which AWS accounts can use the AMI to launch instances, a block device mapping that specifies the volumes to attach to the instance when it's launched, and the root storage device of the instance, which determines the process you follow to create an AMI.
Q16. What are the types of instances.
The different types of instances are as follows:
- General Purpose Instances
- Compute Optimized Instances
- Memory-Optimized Instances
- Storage Optimized Instances
- Accelerated Computing Instances
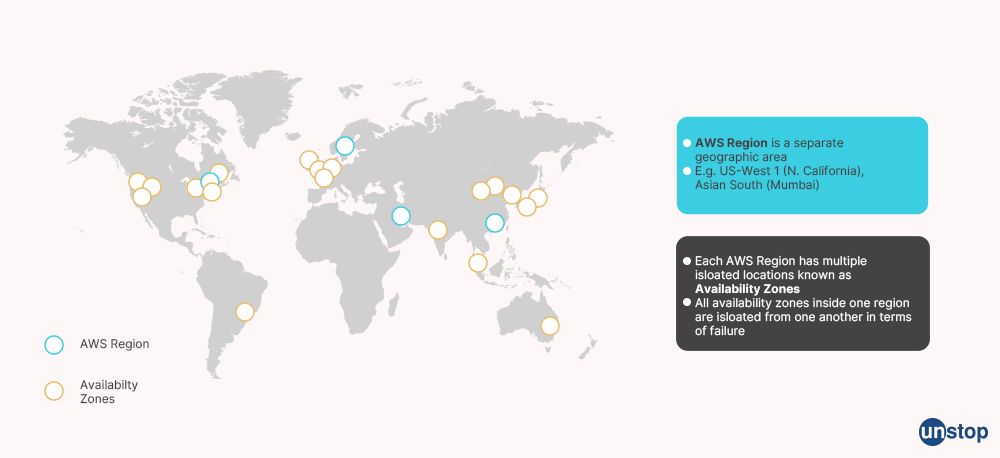
Q17. Do you know about Availability Zone and AWS Region?
A single data center or collection of data centers inside a AWS Region is referred to as an AZ (availability zone). Since each AZ runs separately from the others, a problem in one won't affect the others. Businesses employ numerous AZs in their disaster recovery plans to boost reliability and redundancy.
A collection of data centers in a certain geographic location is known as an AWS Region. The best approach is to select an area that is close to the users' location because this lowers latency, and data gets to the consumers more rapidly.
Several AZs are present in each AWS Region. Each AZ, however, is limited to a certain AWS Region. One Region may have numerous AZs, however, more than one region may not contain the same AZ.
Q18. Mention the tools used to monitor Amazon VPC.
To monitor Amazon VPC, you can use the following tools:
- CloudTrail logs
- Network Access Analyze
- Reachability Analyzer
- Traffic Mirroring
- Amazon VPC IP Address Manager (IPAM)
- VPC Flow Logs
Q19. What are the various EC2 instance kinds based on their prices?
Each instance type offered by Amazon EC2 has a varying price depending on how it is configured.
Different pricing structures, such as On-Demand Instances, Spot Instances, and Reserved Instances, are available for EC2 instances on AWS.
On-Demand instances like compute power are virtual servers that are inexpensive and prepared as needed, but not for a lengthy period of time.
The bidding approach can be used to purchase spot instances, which are comparatively less expensive than on-demand instances.
When you know in advance that you will require an instance for a long time, reserved instances, which may be established for up to a year, are extremely helpful.
Q20. What is meant by stopping and terminating an EC2 instance?
An instance enters a Stopped state and conducts a typical shutdown when it is stopped. An instance can be started again at any time, and the data on the instance's EBS volumes is preserved. Stopping an instance comes in handy if you want to save the instance's state and configurations but don't want to pay for its running time.
When an instance is terminated, the instance shuts down, and the provided virtual machine is permanently removed. Unless the attached Amazon EBS volume's DeleteOnTermination property is set to false, the attached Amazon EBS volumes are removed. When you no longer require an instance or wish to avoid paying for its running time, terminating can be handy.
Q21. Name different consistency models that are available on AWS for modern DBs.
Different consistency models, like eventually consistent reads and highly consistent reads, are available for contemporary databases through Amazon Web Services (AWS).
Eventual consistency: The eventual consistency option in Amazon DynamoDB maximizes read throughput and is the default setting. The outcomes of a recently finished writing may not always be reflected in an eventually consistent read, nonetheless. The average time to achieve consistency across all copies of data is one second.
Strongly consistent: In Amazon DynamoDB, a strongly consistent read yields a result that includes all writes that had successful responses prior to the read. You can provide optional parameters in a request to obtain a strongly consistent read result. Processing a highly consistent read requires more processing power than processing an eventually consistent read.
Q22. Can you explain Geo-Targeting in CloudFront?
Without modifying the URL, geo-targeting in Amazon CloudFront enables businesses to show their audience tailored content based on their location. CloudFront can identify the nation from which users are accessing content, and it can provide the company with the country code in the CloudFront-Viewer-Country header. Using this data, the material that is given to end users can be tailored to their location.
Businesses that wish to share location-specific content with their audience, such as language, currency, or promotions, can benefit from geo-targeting.
Q23. What are the benefits of AWS IAM?
For controlling user access to AWS resources, AWS Identity and Access Management (IAM) offers a number of benefits. One benefit of AWS IAM (Identity and Access Management) is its capacity to grant various users and groups granular access to AWS resources.
It has the capacity to give people access keys and passwords as security credentials and IAM policies for fine-grained access control. IAM policies enable you to set the circumstances under which access is permitted to particular AWS service APIs and resources.
Other benefits of AWS IAM include the ability for users, workloads, and AWS services that need to undertake operations in your AWS accounts to rely on temporary credentials.
Q24. Explain security group.
A sort of rule-based virtual firewall in Amazon Web Services (AWS) called security groups regulates access to your instances. You may or may not want an AWS instance you build to be reachable from the public network, and you may want it to be reachable from some networks but not from others.
You can designate the port numbers, networks, or protocols from which you want to grant or prevent access to your instances by using security groups. When it comes to resources like EC2 instances, a security group manages the traffic that is permitted to enter and exit such resources.
Q25. What do you know about Spot Instances and On-Demand Instances?
Spot instances: Spot instances are those that utilize extra EC2 capacity that is offered for less than the on-demand pricing. A spot instance's hourly price is known as a spot price, and it varies according to long-term supply and demand. It can be up to 90% less expensive than on-demand instances, but there is no guarantee that they will always be accessible.
If you can be flexible with applications running and if your applications can be interrupted, Spot Instances are a cost-effective option. They are suitable for optional tasks, background processing, batch processes, and data analysis.
On-Demand instances: The primary EC2 instances on AWS are called On-Demand Instances, and you can use them when you need them without making any long-term commitments. On-Demand Instances are priced in advance and are billed hourly.
Q26. Tell me about connection draining.
Elastic Load Balancer (ELB) from Amazon Web Services (AWS) has a function called connection draining that guards against breaking open network connections while removing an instance from service, updating its software, or replacing it. Connection draining enables the ELB to finish processing in-flight requests before the instance is pulled out of service. As a result, the requests are not lost, and the user experience is unaffected.
Using the AWS Management Console or the AWS Command Line Interface (CLI), a connection for draining the load balancer can be activated or removed at any time.
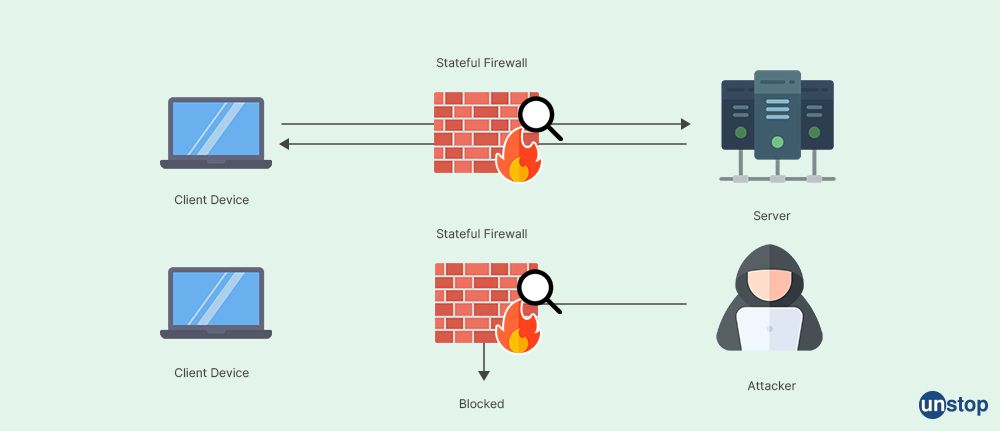
Q27. What do you know about a Stateful and a Stateless Firewall?
Firewalls can be classified into two types: Stateful and Stateless Firewall
Stateful firewall: Stateful firewalls function by maintaining context regarding the processed packets. They monitor the condition of network connections and use this data to decide whether to permit or deny packets. Stateful firewalls can identify and filter packets based on their content, not simply their header information, making them more intelligent than stateless firewalls. They can identify and prevent attacks that utilize numerous packets, making them more secure than stateless firewalls.
Stateless firewall: Stateless firewalls handle packets in accordance with preset guidelines selected by the network administrator. These guidelines never change, and the firewall does not keep track of the packets it has handled. The stateless firewalls safeguard the network by utilizing static data, like destination and source. It only looks at the static data contained in packets sent during cross-network connections. In order to decide whether to allow or deny a packet, they continuously scan the header information of each one and compare it to the rules.
Q28. Explain about the Power User Access in AWS.
Power User Access is a sort of IAM (Identity and Access Management) policy that grants administrator access without allowing users or permissions to be managed. All AWS services are accessible to users with Power User Access, with the exception of IAM group and user management.
Power users can create KMS (Key Management Service) keys, use and manage the keys they produce, and examine all KMS keys and IAM identities.
Q29. Define an Instance Store Volume and an EBS Volume.
A temporary storage device known as an instance store volume is physically connected to the host machine of an EC2 instance. Instance store volumes are not durable; therefore, when an instance is stopped or terminated, the data on them is destroyed. For transient storage, such as cache, scratch data, and other temporary files, instance store volumes are perfect.
A network-attached block storage device called an EBS volume can be connected to an EC2 instance. EBS volumes are durable, thus even after the instance is stopped or terminated, the data on them is kept. They are more durable and available than instance store volumes, and they can be secured.
The main difference between store volume and EBS volume is that: EBS volumes are network-connected and durable, whereas instance store volumes are physically attached to the host machine and transient.
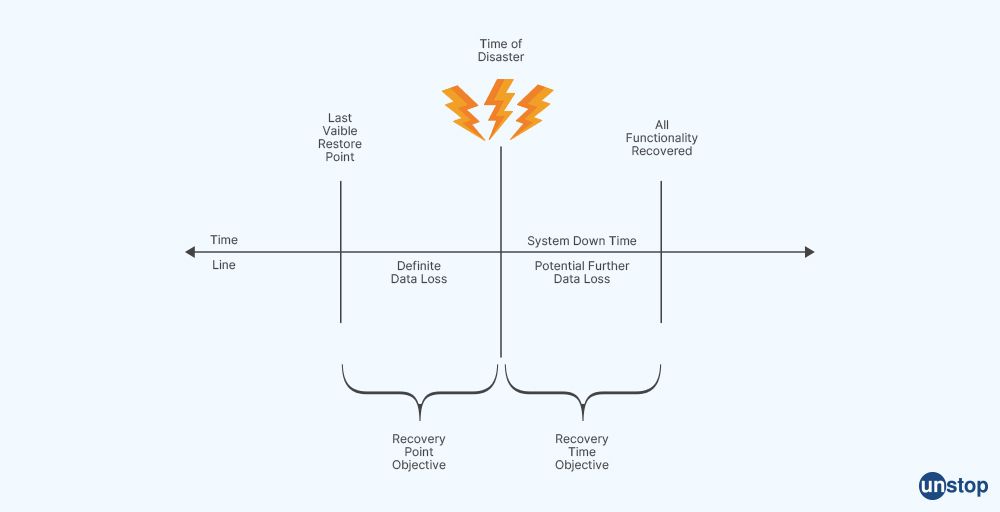
Q30. Do you know about Recovery Time Objective and Recovery Point Objective in AWS?
- Recovery time objective(RTO): RTO is the longest period of time that can be allowed between the interruption of service and its restoration. This establishes a permissible window of time when service is not available.
- Recovery point objective(RPO): RPO is the longest period of time that can be accepted since the last data recovery point, which establishes allowed data loss between the last recovery point and disruption of service. RPO represents the amount of data that can be lost during a disaster recovery event and is usually measured in seconds or minutes.
Q31. Is it possible to upload a file to Amazon S3 that is bigger than 100 Megabytes?
Yes, you can upload a file to Amazon S3 that is more than 100 Megabytes.
Amazon S3 allows for the storage of objects and files up to 5 terabytes. AWS's Multipart upload function can be used to upload files bigger than 100 Megabytes. Multipart upload allows for numerous uploads of large files. This feature enables you to split up a huge file into smaller pieces for faster upload rates. By uploading these pieces simultaneously, you can also speed up the upload time.
Q32. When an EC2 instance is active or stopped, will the Private IP Address change?
The answer is No, the private IP address of the network cannot be changed. The private IP address of an EC2 instance will not change while it is running or is stopped because it is assigned at boot time.
Q33. Do you know about the function of lifecycle hooks in Autoscaling?
With the help of lifecycle hooks in Auto Scaling, you can build solutions that are aware of instance lifecycle events and take specific action on instances when the relevant lifecycle event takes place. Scaling processes that are started by auto-scaling can be stopped using lifecycle hooks.
Before instances are launched or terminated, you can carry out custom operations on them using lifecycle hooks, such as configuring the instance, installing applications, or running scripts.
Q34. Mention the policies that one can set for user passwords.
AWS user password policies are :
- User's passwords must be at least eight characters long and include at least one of each of the following: an uppercase letter, a lowercase letter, a number, and a non-alphanumeric character.
- Users can be made to modify their password length by increasing the minimum password length. A single working password is all that a user can have at once.
- Users cannot reuse the same password since password expiration requires an administrator reset.
- Setting a password policy can be done through either the AWS Command Line Interface or AWS API activities
Q35. Tell me the different types of elastic load balancing in AWS.
Elastic Load Balancing is mainly of 3 types:
- Application Load Balancer
- Gateway Load Balancer
- Network Load Balancer
Q36. What do you understand by classic load and an application load balancer?
The Classic Load Balancing is an established load balancer that equally distributes traffic among numerous virtual devices. It manages TCP traffic routing at both the request and connection levels.
Application load balancer: HTTP/HTTPS traffic is routed using application load balancers, which decide on routing at the application layer. It may direct requests to one or more ports on each container instance in your cluster and provides path-based routing.
Additionally, it supports content-based routing, which enables requests to be forwarded to many apps using a single load balancer. The Application Load Balancer is more adaptable than the Classic Load Balancer and enables dynamic host port mapping than classic load balancer.
Q37. Can you explain edge location?
An edge location is a data center that Amazon Web Services (AWS) uses to cache content and provide services to customers with the least amount of latency. It is the closest location to the user or consumer of the AWS service. Edge locations are utilized to quickly distribute the material to users and can be found in major cities all over the world.
In order to speed up the delivery of material to consumers anywhere, AWS employs edge locations to cache copies of the content.
Q38. Do you know about Amazon Simple Email Service (Amazon Ses)?
Developers may send emails from any application using the affordable, adaptable, and scalable Amazon Simple Email Service (SES). It is a strong and trustworthy solution for instantly sending transactional, notification, and marketing emails. Users can send transactional emails, marketing communications, and any other kind of high-quality information to customers using Amazon SES(Simple Email Service).
Businesses may send and receive emails easily and affordably using simple email service. The infrastructure was created by Amazon.com to serve its own client base, and it is a dependable and scalable simple email service.
Q39. Tell me the name of different types of virtualization.
Amazon Web Services (AWS) offers two types of virtualization: Hardware Virtual Machine (HVM) and Paravirtualization (PV).
- HVM- All virtual machines on HVM's completely virtualized hardware operate independently of one another. These virtual machines run a master boot record in the image's root block device to initiate their boot process.
- PV- It is a simple virtualization method that enables sharing of a single hardware host by several operating systems. The PV AMIs are booted by PV-GRUB, and the PV-GRUB chain loads the kernel that is defined in the menu. Operating systems can benefit from storage and network I/O provided by the host by using PV on HVM.
Q40. What do you understand by AWS CloudTrail?
AWS CloudTrail is a service that is made for storage options as well as logging and tracking API calls. It makes it possible for an AWS account to be managed, governed, and compliant in terms of operations and risks.
CloudTrail logs offer thorough API tracing for Amazon S3, Amazon CloudWatch, and Amazon ECS, among other AWS services.
Q41. On an EBS-backed machine, how can the data on the root volume be saved?
We can override the terminate option in order to save the data on the root volume of an EBS-backed machine. The default behavior for terminating an Amazon EBS-backed instance is deletion of the root volume. We can override the terminate option to avoid data loss by turning off the option to remove the root volume when the instance terminates.
Q42. Why is elastic compute cloud used?
The Amazon Web Service (AWS) cloud computing infrastructure uses Amazon Elastic Compute Cloud (EC2), which enables users to rent virtual computers on which they can run their own applications.
It offers resizable compute capacity in the cloud, allowing users to swiftly scale up or down the number of instances they need to fulfill their processing needs. EC2 offers a variety of instance types that are tailored for various use cases, such as compute-, memory-, and storage-optimized instances. It is a very flexible service that allows users to only pay for the resources they really use, which makes it an affordable option for running applications in the cloud.
Q43. Is it possible to control the security of VPC?
Yes, it is possible to control the security of VPC.
In Amazon Web Service (AWS) Virtual Private Cloud (VPC), security can be controlled in two ways: Security Group and Network Access Control Lists (NACLs).
- Security Group: They are virtual firewall for linked EC2 instances at the instance level that controls both the incoming and outgoing traffic. When a security group is defined when launching an instance, they only apply to that instance.
- Network Access Control Lists: NACLs serve as a firewall for connected subnets, managing incoming and outgoing traffic on a subnet level. They are automatically applied to all instances connected to a subnet.
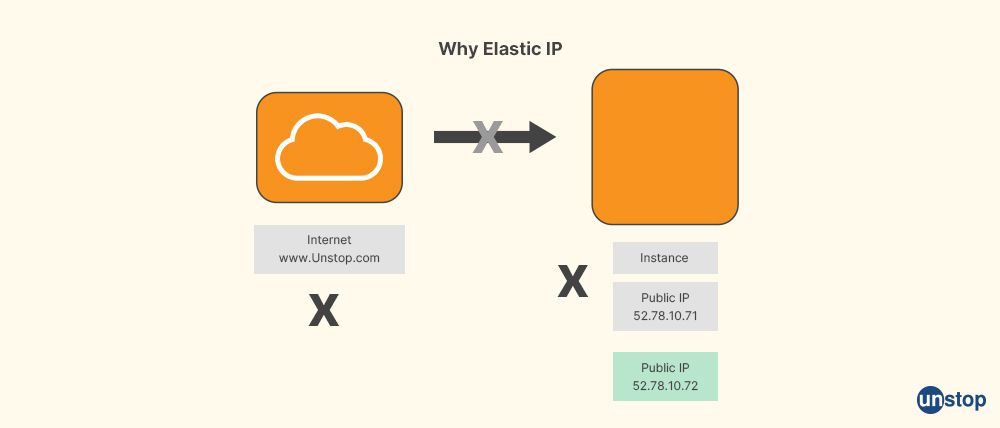
Q44. Define elastic IP address.
Elastic IP addresses are static IPv4 addresses built specifically for dynamic cloud computing. Your AWS account receives an Elastic IP address, which belongs to you until you release it. You can quickly map an Elastic IP address to another instance in your account to hide the failure of software or instance. As an alternative, you can add the Elastic IP address to your domain's DNS records so that your domain will refer to your instance.
Q45. What do you mean by AWS Direct Connect?
Customers can build a dedicated network connection from their on-premises network to one or more Virtual Private Clouds (VPCs) in Amazon Web Services (AWS) using the network service known as AWS Direct Connect. It offers an alternative to accessing the open internet for connecting to AWS cloud services by offering a private, secure, and low-latency connection.
Compared to internet-based connections, AWS Direct Connect can save network expenses, enhance bandwidth throughput, and deliver a more reliable network experience.
Q46. What do you understand by the inbound rule in AWS?
An Amazon Elastic Compute Cloud (EC2) instance or other resources in a Virtual Private Cloud (VPC) can be controlled by an inbound rule. When launching a new EC2 instance, inbound rules can be introduced by making a new security group or updating an existing security group and adding or changing the incoming rules.
Q47. Explain customer gateway.
A customer gateway is a physical or software appliance that the client owns or manages on their on-premises network that is used to connect to Amazon Web Service (AWS) via a Site-to-Site Virtual Private Network (VPN). To represent the customer gateway device in the client's network, a resource was built in AWS. Customers must supply details when setting up customer gateways, including the IP address of the device's external interface, the Autonomous System Number (ASN) for the AWS side of the BGP session, and the IP ranges that the device advertises.
Q48. What benefits can AWS IAM offer your company?
IAM enables companies to create and control IAM users' access to resources, enhancing the security of the resources. Additionally, IAM enables organizations to control access to resources for federated users, enabling safe access to AWS account resources for employees and apps without the need to create IAM roles.
IAM offers workforce and workloads fine-grained access restrictions and enables companies to provide temporary security credentials for workloads that use their AWS resources. It can be used to centrally connect identities to numerous AWS accounts or manage identities across a single AWS(Amazon Web Service) account.
Q49. What do you know about C3 and C4 instances?
Applications requiring a lot of computing power using the Amazon Elastic Compute Cloud (EC2) instance types: C3 and C4. Applications that demand very high CPU use and have powerful processors should use C3 instances. The follow-up to C3 instances is called a C4 instance.
Although they use the same amount of virtual CPUs (vCPUs) and memory as C3 instances, C4 instances offer more computing power, greater Elastic Block Store (EBS) performance, and quicker networking. The EBS throughput on C4 instances is higher and they are less expensive.
Q50. What do you know about Identity-based policies?
An Identity and Access Management (IAM) for user, group, or role is associated with identity-based policies in Amazon Web Service (AWS). These identity-based policies outline the identity's permissions and the actions that the identity may carry out on AWS resources. AWS-controlled policies, client-managed policies, and inline policies are some examples of identity-based policies.
AWS creates and manages AWS-managed policies, whereas the client creates and manages customer-managed policies.
Q51. Tell me about the latency-based routing policy.
By serving requests from the area that offers the lowest latency, the latency-based routing policy in Amazon Route 53 is used to enhance the performance of applications hosted across various AWS regions. When Route 53 receives a DNS request for a domain or subdomain, it assesses which AWS regions have latency records and which region offers the customer the lowest latency. This is done in order to employ a latency-based routing policy.
Applications that have users in many locations and need minimal latency to deliver a positive user experience can benefit from latency-based routing.
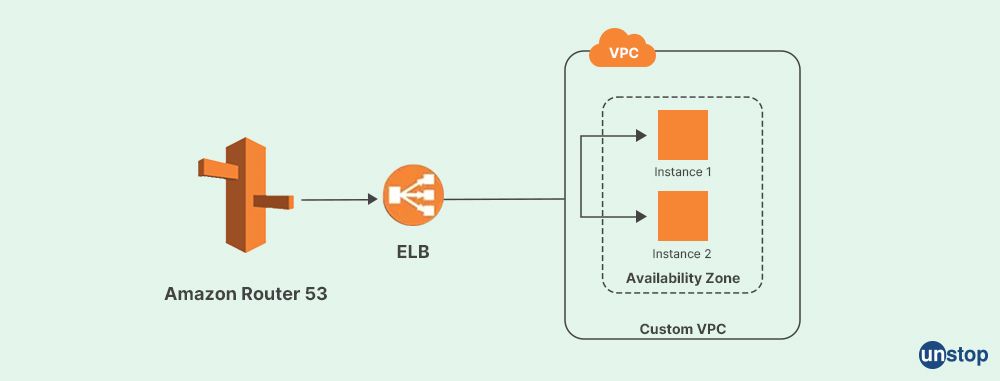
Q52. Describe advanced policy.
Advanced policies in AWS(Amazon Web Service) Identity and Access Management (IAM) provide more flexibility and control to the AWS Access Management accounts. These rules comprise permissions boundaries (PBs) and customer-managed policies (CMPs). CMPs are independent policies that the customer creates and maintains and can be used to allow or prohibit access to AWS resources by roles in AWS accounts.
The maximum permissions that an identity-based policy can provide to a role are set using PBs. Advanced policies are helpful for providing the least privilege access control and managing access to resources in complicated situations. AWS(Amazon Web Service) also offers other kinds of policies, such as session policies, access control lists (ACLs), identity-based policies, and resource-based policies.
Q53. Tell me about Weighted Routing Policy.
Users can assign several resources to a single domain name or subdomain name and control how much traffic is delivered to each resource by using the weighted routing policy in Amazon Route 53. This policy might be helpful for testing new software versions and load balancing. Users establish records with the same name and type for each of their resources, then set up a weighted routing policy by giving each record a relative weight that reflects how much traffic they want to deliver to each resource.
A record's weight expressed as a percentage of the group's overall weight determines how much traffic Amazon Route 53 directs to that resource.
For example, if a user wants to send a tiny portion of their traffic to one resource and the rest to another resource, they might specify weights of 1 and 255. The resource with a weight of 1 gets 1/256th of the traffic, and the other resource gets 255/256ths of the traffic.
Q54. What is outbound traffic?
Data transmitted from one AWS resource to another outside the AWS environment is referred to in AWS as "outbound traffic." Outbound traffic is governed by security rules and regulations set forth in AWS Security Groups, which serve as an extra firewall layer on top of the operating system.
It is advised to configure AWS Security Groups' outbound traffic rules effectively in order to safeguard the resources in the AWS(Amazon Web Service) environment because they are highly broad and insecure by default.
Q55. What do you know about Amazon Redshift?
Data warehousing service Amazon Redshift is a component of the larger cloud computing service Amazon Web Service (AWS). To manage big data sets and database migrations, it is constructed using technologies from the massive parallel processing (MPP) data warehouse startup ParAccel. A column-oriented DBMS called Amazon Redshift is made to handle analytical workloads on massive data sets. It supports data clusters with up to 16 petabytes, as opposed to Amazon RDS Aurora's 128 terabyte limit.
Using AWS-designed tools, Amazon Redshift analyses structured and semi-structured data from data lakes, operational databases, and data warehouses using SQL. Amazon Redshift is based on an older version of PostgreSQL 8.0.2, and Redshift has made changes to that version.
Q56. What is Amazon Elastic Block Store?
Amazon Web Service (AWS) provides Block storage which is called as Amazon Elastic Block Store (EBS). It offers raw bock-level storage that can be connected to Amazon EC2 instances. It serves as a repository for permanent data and offers highly available block-level storage volumes, making it appropriate for EC2 instances.
There are several alternatives for storage performance and cost provided by Amazon EBS, which are split into two main categories: Using disk-backed storage for throughput-intensive applications like big data and data warehousing and SSD-backed storage for transactional workloads like databases and boot volumes. Several functions offered by Amazon EBS(Amazon elastic block store) help with data management, backups, and performance optimization.
Q57. Tell me about Amazon ElastiCache.
By obtaining data from controlled in-memory caches rather than only using slower disk-based databases, Amazon ElastiCache, a fully managed in-memory data store, and cache service offered by Amazon Web Services (AWS), enhances the efficiency of web applications. It serves as an in-memory data store and cache to enable applications with the highest demands for millisecond response times.
Amazon ElastiCache is intended to make memcached and Redis deployments easier to set up, run, and scale. Users can easily set up, operate, and grow well-known open-source compatible in-memory data stores with the help of our managed Redis and Memcached service. Caching techniques supported by Amazon ElastiCache offer quick and affordable access to copies of data.
Q58. What is Amazon RDS (Amazon Relational Database Service)?
AWS's managed SQL database service, known as Amazon RDS (Amazon Relational Database Service), makes it simpler to set up, run, and scale a relational database on the AWS(Amazon Web Service) Cloud. It performs typical database administration activities and offers affordable, resizable capacity for an industry-standard relational database.
Routine database functions, including provisioning, patching, backup, recovery, failure detection, and repair, are handled by Amazon RDS(Amazon Relational Database Service).
It offers capabilities like read replicas, Multi-AZ deployments, automatic software patching, and more. DB Parameter Groups offer fine-grained control and database tweaking, and Amazon RDS database instances are preloaded with parameters and settings appropriate for the engine and class are chosen by the user.
Q59. What do you know about Amazon Simple Storage Service?
Amazon Simple Storage Service (S3) is online storage that can be used to store and retrieve any volume of data from any location at any time. Mazon S3 handles data using an object storage architecture that offers high durability, scalability, and high availability. In Amazon S3, objects are the fundamental storage units. Each object is recognized by a special, user-assigned key.
Q60. How many types of scaling are there in AWS?
There are two types of Scaling. Horizontal Scaling and Vertical Scaling
- Horizontal Scaling: Adding more nodes or machines to the resource pool, such as more servers to a cluster, is referred to as horizontal scaling. Scaling out, or horizontal scaling, is another name for it.
- Vertical Scaling: Vertical scaling is the process of giving existing devices extra power, such as boosting a server's CPU or RAM. While horizontal scaling delivers new infrastructure, vertical scaling enhances existing infrastructure.
Q61. What does AMI stand for?
An Amazon Machine Image (AMI) is a virtual image that provides the information required to launch an instance, which is a copy of the AMI running as a virtual server in the cloud. An AMI is a template that consists of an operating system, an application server, and applications. It is the fundamental deployment component for services provided through EC2. As many different AMIs as you require can be used to launch instances, and each instance you launch from an AMI is a duplicate of the original AMI.
Q62. How can you distinguish an Instance and AMI (Amazon Machine Images)?
An instance is a virtual server, and when an instance is launched, its configuration is a replica of the AMI that was specified at that time. An instance, or operating copy of the AMI in the cloud, is created using an AMI, which is a pre-configured virtual machine image.
An Amazon Machine Image (AMI) functions similarly to a template that has an operating system or application server and other software configured to specify the user's operating environment. A functioning virtual machine that may be launched from an AMI is called an instance.
Q63. What is AWS CodeDeploy?
AWS CodeDeploy is a tool that automates software deployments to any instance, including instances running on-premises, serverless Lambda functions, Amazon EC2 instances, and more.
AWS CdeDeploy enables automated software deployments to the available on-premises servers, such as AWS LAMBDA and FARGATE, Amazon EC2 instances, etc.CodeDeploy supports Amazon EC2 Auto Scaling, which launches Amazon EC2 instances automatically in accordance with user-defined parameters.
Q64. Do you know about AWS Elastic Beanstalk?
Amazon Web Services (AWS) provides a fully managed service called AWS Elastic Beanstalk for launching and expanding web services and applications. This web infrastructure management service manages the deployment and scalability of web services and applications.
AWS Elastic Beanstalk, a pre-configured server, uses EC2 to develop and deploy the resources required by web applications in AWS. EC2 accepts application code and environmental setup natively. It makes web apps available so customers can concentrate on their businesses, and it gives users a quick, easy approach to uploading and making web applications available.
AWS Elastic Beanstalk adds another level of abstraction to bare EC2 instances and other AWS resources.
Q65. Tell me about the public IP Address.
A public IP Address is an IP address that can be accessed from the internet and is used to access the internet.
The ISP gives a home or business router a public IP address so that it may route internet traffic. While dynamic public IP addresses have a tendency to vary over time, static public IP addresses are assigned by the ISP and remain constant.
Q66. Do you have an idea about the destination bucket?
A destination bucket in AWS is a bucket where data is exported or replicated. Users can log into the AWS Management Console and follow the directions for creating an S3 bucket in order to create a destination bucket.
Users can select to replicate to a bucket or buckets in their account or in another AWS account when configuring replication for source and destination buckets. Users must add a bucket policy to the destination buckets to provide the owner of the source bucket account authorization to replicate objects if the destination is in a different account than the source bucket.
Q67. Explain the outbound rules in AWS.
The rules that regulate outgoing traffic from an EC2 instance or a resource are referred to as "outbound rules" in the AWS system. The security group settings, which also comprise inbound rules, include outbound rules. Because customers trust the software running on their own EC2 instance, outbound policies are typically set to "Allow All".
To securely control and filter outgoing traffic and prevent data leaks, users must manually set up outbound rules because outbound traffic rules in AWS Security Groups are, by default, quite large and insecure. Outbound traffic refers to the database server's answers or traffic leaving EC2 instances.
Q68. What do you understand by Amazon Kinesis?
Amazon Kinesis is a fully managed, serverless data streaming service that eliminates the need to provision or manage the capacity required for running applications. With Kinesis Data Streams, users can adjust their capacity to stream gigabytes per second of data and get automatic provisioning and scaling with the on-demand mode.
Q69. Do you know about standby instances, have you heard about them?
Instances that are still maintained by the Auto Scaling Group but taken out of service until they are returned to the InService state are referred to as standby instances in AWS. Standby instances can be utilized to temporarily remove instances from the Auto Scaling group without terminating them.
For troubleshooting or making adjustments to instances that are already running, standby instances can be used.
Q70. Tell me about Amazon Aurora.
A relational database engine that is completely managed and functional with MySQL and PostgreSQL is called Amazon Aurora. Aurora can be utilized with the same programs, tools, and databases that you use with your MySQL and PostgreSQL databases. Without requiring changes to the majority of current applications. Amazon Aurora can give up to five times the throughput of MySQL and up to three times the throughput of PostgreSQL for certain workloads.
Q71. Explain Amazon Elastic Container Service.
With Amazon Elastic Container Service (Amazon ECS), a fully managed container service, you can easily deploy, manage, and scale containerized applications. Running containerized apps on Amazon ECS is the safest, most dependable, and most scalable option available.
Amazon ECS offers the safest, most dependable, and most scalable solution to execute containerized applications. It's fully managed because it has an AWS setup. You can manage your on-premises container workloads using the Amazon ECS UI and the AWS CLI because of the external instance option that Amazon ECS offers with ECS Anywhere.
Q72. What is inbound traffic in AWS?
Data or network traffic that is sent to resources hosted in the AWS cloud is referred to as Inbound Traffic. It can also include requests, messages, or data packets sent to AWS services, such as EC2 instances, load balancers, or databases, from outside networks or the internet.
Resources are often given IP addresses or domain names when they are created in AWS, making them reachable through the internet. When people or systems open connections to these resources, inbound traffic is produced. For instance, if you host a web application on an EC2 instance, requests from users' web browsers to view your website would make up the inbound traffic.
We hope the above AWS interview questions gave you a good idea about this topic. For more articles like these, stay tuned to Unstop.
Suggested reads:
I am a storyteller by nature. At Unstop, I tell stories ripe with promise and inspiration, and in life, I voice out the stories of our four-legged furry friends. Providing a prospect of a good life filled with equal opportunities to students and our pawsome buddies helps me sleep better at night. And for those rainy evenings, I turn to my colors.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter
Blogs you need to hog!

This Is My First Hackathon, How Should I Prepare? (Tips & Hackathon Questions Inside)

10 Best C++ IDEs That Developers Mention The Most!

Advantages and Disadvantages of Cloud Computing That You Should Know!











Comments
Add comment