- TCS Technical Interview Questions & Answers
- TCS Managerial Interview Questions & Answers
- TCS HR Interview Questions & Answers
- Overview of Cognizant Recruitment Process
- Cognizant Interview Questions: Technical
- Cognizant Interview Questions: HR Round
- Overview of Wipro Technologies Recruitment Rounds
- Wipro Interview Questions
- Technical Round
- HR Round
- Online Assessment Sample Questions
- Frequently Asked Questions
- Overview of Google Recruitment Process
- Google Interview Questions: Technical
- Google Interview Questions: HR round
- Interview Preparation Tips
- About Google
- Deloitte Technical Interview Questions
- Deloitte HR Interview Questions
- Deloitte Recruitment Process
- Technical Interview Questions and Answers
- Level 1 difficulty
- Level 2 difficulty
- Level 3 difficulty
- Behavioral Questions
- Eligibility Criteria for Mindtree Recruitment
- Mindtree Recruitment Process: Rounds Overview
- Skills required to crack Mindtree interview rounds
- Mindtree Recruitment Rounds: Sample Questions
- About Mindtree
- Preparing for Microsoft interview questions
- Microsoft technical interview questions
- Microsoft behavioural interview questions
- Aptitude Interview Questions
- Technical Interview Questions
- Easy
- Intermediate
- Hard
- HR Interview Questions
- Eligibility criteria
- Recruitment rounds & assessments
- Tech Mahindra interview questions - Technical round
- Tech Mahindra interview questions - HR round
- Hiring process at Mphasis
- Mphasis technical interview questions
- Mphasis HR interview questions
- About Mphasis
- Technical interview questions
- HR interview questions
- Recruitment process
- About Virtusa
- Goldman Sachs Interview Process
- Technical Questions for Goldman Sachs Interview
- Sample HR Question for Goldman Sachs Interview
- About Goldman Sachs
- Nagarro Recruitment Process
- Nagarro HR Interview Questions
- Nagarro Aptitude Test Questions
- Nagarro Technical Test Questions
- About Nagarro
- PwC Recruitment Process
- PwC Technical Interview Questions: Freshers and Experienced
- PwC Interview Questions for HR Rounds
- PwC Interview Preparation
- Frequently Asked Questions
- EY Technical Interview Questions (2023)
- EY Interview Questions for HR Round
- About EY
- Morgan Stanley Recruitment Process
- HR Questions for Morgan Stanley Interview
- HR Questions for Morgan Stanley Interview
- About Morgan Stanley
- Recruitment Process at Flipkart
- Technical Flipkart Interview Questions
- Code-Based Flipkart Interview Questions
- Sample Flipkart Interview Questions- HR Round
- Conclusion
- FAQs
- Recruitment Process at Paytm
- Technical Interview Questions for Paytm Interview
- HR Sample Questions for Paytm Interview
- About Paytm
- Most Probable Accenture Interview Questions
- Accenture Technical Interview Questions
- Accenture HR Interview Questions
- Amazon Recruitment Process
- Amazon Interview Rounds
- Common Amazon Interview Questions
- Amazon Interview Questions: Behavioral-based Questions
- Amazon Interview Questions: Leadership Principles
- Company-specific Amazon Interview Questions
- 43 Top Technical/ Coding Amazon Interview Questions
- Juspay Recruitment: Stages and Timeline
- Juspay Interview Questions and Answers
- How to prepare for Juspay interview questions
- Prepare for the Juspay Interview: Stages and Timeline
- Frequently Asked Questions
- Adobe Interview Questions - Technical
- Adobe Interview Questions - HR
- Recruitment Process at Adobe
- About Adobe
- Cisco technical interview questions
- Sample HR interview questions
- The recruitment process at Cisco
- About Cisco
- JP Morgan interview questions (Technical round)
- JP Morgan interview questions HR round)
- Recruitment process at JP Morgan
- About JP Morgan
- Wipro Elite NTH: Selection Process
- Wipro Elite NTH Technical Interview Questions
- Wipro Elite NTH Interview Round- HR Questions
- BYJU's BDA Interview Questions
- BYJU's SDE Interview Questions
- BYJU's HR Round Interview Questions
- A Quick Overview of the KPMG Recruitment Process
- Technical Questions for KPMG Interview
- HR Questions for KPMG Interview
- About KPMG
- DXC Technology Interview Process
- DCX Technical Interview Questions
- Sample HR Questions for DXC Technology
- About DXC Technology
- Recruitment Process at PayPal
- Technical Questions for PayPal Interview
- HR Sample Questions for PayPal Interview
- About PayPal
- Capgemini Recruitment Rounds
- Capgemini Interview Questions: Technical round
- Capgemini Interview Questions: HR round
- Preparation tips
- FAQs
- Technical interview questions for Siemens
- Sample HR questions for Siemens
- The recruitment process at Siemens
- About Siemens
- HCL Technical Interview Questions
- HR Interview Questions
- HCL Technologies Recruitment Process
- List of EPAM Interview Questions for Technical Interviews
- About EPAM
- Atlassian Interview Process
- Top Skills for Different Roles at Atlassian
- Atlassian Interview Questions: Technical Knowledge
- Atlassian Interview Questions: Behavioral Skills
- Atlassian Interview Questions: Tips for Effective Preparation
- Walmart Recruitment Process
- Walmart Interview Questions and Sample Answers (HR Round)
- Walmart Interview Questions and Sample Answers (Technical Round)
- Tips for Interviewing at Walmart and Interview Preparation Tips
- Frequently Asked Questions
- Uber Interview Questions For Engineering Profiles: Coding
- Technical Uber Interview Questions: Theoretical
- Uber Interview Question: HR Round
- Uber Recruitment Procedure
- About Uber Technologies Ltd.
- Intel Technical Interview Questions
- Computer Architecture Intel Interview Questions
- Intel DFT Interview Questions
- Intel Interview Questions for Verification Engineer Role
- Recruitment Process Overview
- Important Accenture HR Interview Questions
- Points to remember
- What is Selenium?
- What are the components of the Selenium suite?
- Why is it important to use Selenium?
- What's the major difference between Selenium 3.0 & Selenium 2.0?
- What is Automation testing and what are its benefits?
- What are the benefits of Selenium as an Automation Tool?
- What are the drawbacks to using Selenium for testing?
- Why should Selenium not be used as a web application or system testing tool?
- Is it possible to use selenium to launch web browsers?
- What does Selenese mean?
- What does it mean to be a locator?
- Identify the main difference between "assert", and "verify" commands within Selenium
- What does an exception test in Selenium mean?
- What does XPath mean in Selenium? Describe XPath Absolute & XPath Relation
- What is the difference in Xpath between "//"? and "/"?
- What is the difference between "type" and the "typeAndWait" commands within Selenium?
- Distinguish between findElement() & findElements() in context of Selenium
- How long will Selenium wait before a website is loaded fully?
- What is the difference between the driver.close() and driver.quit() commands in Selenium?
- Describe the different navigation commands that Selenium supports
- What is Selenium's approach to the same-origin policy?
- Explain the difference between findElement() in Selenium and findElements()
- Explain the pause function in SeleniumIDE
- Explain the differences between different frameworks and how they are connected to Selenium's Robot Framework
- What are your thoughts on the Page Object Model within the context of Selenium
- What are your thoughts on Jenkins?
- What are the parameters that selenium commands come with a minimum?
- How can you tell the differences in the Absolute pathway as well as Relative Path?
- What's the distinction in Assert or Verify declarations within Selenium?
- What are the points of verification that are in Selenium?
- Define Implicit wait, Explicit wait, and Fluent
- Can Selenium manage windows-based pop-ups?
- What's the definition of an Object Repository?
- What is the main difference between obtainwindowhandle() as well as the getwindowhandles ()?
- What are the various types of Annotations that are used in Selenium?
- What is the main difference in the setsSpeed() or sleep() methods?
- What is the way to retrieve the alert message?
- How do you determine the exact location of an element on the web?
- Why do we use Selenium RC?
- What are the benefits or advantages of Selenium RC?
- Do you have a list of the technical limitations when making use of Selenium RC? Selenium RC?
- What's the reason to utilize the TestNG together with Selenium?
- What Language do you prefer to use to build test case sets in Selenium?
- What are Start and Breakpoints?
- What is the purpose of this capability relevant in relation to Selenium?
- When do you use AutoIT?
- Do you have a reason why you require Session management in Selenium?
- Are you able to automatize CAPTCHA?
- How can we launch various browsers on Selenium?
- Why should you select Selenium rather than QTP (Quick Test Professional)?
- Airbus Interview Questions and Answers: HR/ Behavioral
- Industry/ Company-Specific Airbus Interview Questions
- Airbus Interview Questions and Answers: Aptitude
- Airbus Software Engineer Interview Questions and Answers: Technical
- Importance of Spring Framework
- Spring Interview Questions (Basic)
- Advanced Spring Interview Questions
- C++ Interview Questions and Answers: The Basics
- C++ Interview Questions: Intermediate
- C++ Interview Questions And Answers With Code Examples
- C++ Interview Questions and Answers: Advanced
- Test Your Skills: Quiz Time
- MBA Interview Questions: B.Com Economics
- B.Com Marketing
- B.Com Finance
- B.Com Accounting and Finance
- Business Studies
- Chartered Accountant
- Q1. Please tell us something about yourself/ Introduce yourself to us.
- Q2. Describe yourself in one word.
- Q3. Tell us about your strengths and weaknesses.
- Q4. Why did you apply for this job/ What attracted you to this role?
- Q5. What are your hobbies?
- Q6. Where do you see yourself in five years OR What are your long-term goals?
- Q7. Why do you want to work with this company?
- Q8. Tell us what you know about our organization
- Q9. Do you have any idea about our biggest competitors?
- Q10. What motivates you to do a good job?
- Q11. What is an ideal job for you?
- Q12. What is the difference between a group and a team?
- Q13. Are you a team player/ Do you like to work in teams?
- Q14. Are you good at handling pressure/ deadlines?
- Q15. When can you start?
- Q16. How flexible are you regarding overtime?
- Q17. Are you willing to relocate for work?
- Q18. Why do you think you are the right candidate for this job?
- Q19. How can you be an asset to the organization?
- Q20. What is your salary expectation?
- Q21. How long do you plan to remain with this company?
- Q22. What is your objective in life?
- Q23. Would you like to pursue your Master's degree anytime soon?
- Q24. How have you planned to achieve your career goal?
- Q25. Can you tell us about your biggest achievement in life?
- Q26. What was the most challenging decision you ever made?
- Q27. What kind of work environment do you prefer to work in?
- Q28. What is the difference between a smart worker and a hard worker?
- Q29. What will you do if you don't get hired?
- Q30. Tell us three things that are most important for you in a job.
- Q31. Who is your role model and what have you learned from him/her?
- Q32. In case of a disagreement, how do you handle the situation?
- Q33. What is the difference between confidence and overconfidence?
- Q34. If you have more than enough money in hand right now, would you still want to work?
- Q35. Do you have any questions for us?
- Interview Tips for Freshers
- Tell me about yourself
- What are your greatest strengths?
- What are your greatest weaknesses?
- Tell me about something you did that you now feel a little ashamed of
- Why are you leaving (or did you leave) this position??
- 15+ resources for preparing most-asked interview questions
- CoCubes Interview Process Overview
- Common CoCubes Interview Questions
- Key Areas to Focus on for CoCubes Interview Preparation
- Conclusion
- Frequently Asked Questions (FAQs)
- Data Analyst Interview Questions With Answers
- About Data Analyst
50+ Siemens Interview Questions And Answers With Explanatory Diagrams
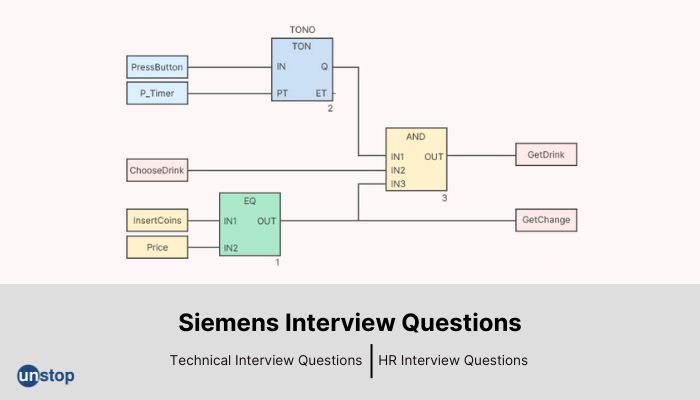
Siemens Limited is among the top IT companies that most of the candidates desire to work with. However, cracking their interview is not that easy and so we compiled the top Siemens PLC interview questions and answers below to help you prepare and secure your dream job at this company.
List of technical interview questions for Siemens
Here are some of the frequently asked interview technical questions for Siemens interview that you must checkout-
1. How does the life cycle of a bug work?
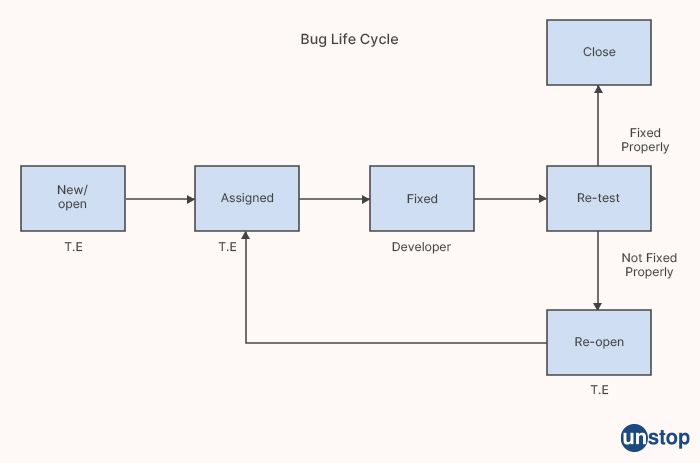
The defect life cycle, also known as the bug life cycle or issue life cycle, is a series of stages that a software defect or bug goes through from the time it is discovered to the time it is resolved. The following are the typical stages in a defect life cycle:
-
Discovery/New: The defect is discovered by a tester, developer, or end-user.
-
Reproduction/Assign: The tester tries to reproduce the defect to identify the exact steps that cause the problem.
-
Analysis: The tester or developer analyzes the defect to determine its severity, impact, and root cause. They may also prioritize the defect based on its impact and severity.
-
Assigning: The defect is assigned to a developer who will work on fixing it.
-
Fixing: The developer fixes the defect and verifies the fix.
-
Testing: The tester verifies the fix by performing regression testing, or testing to make sure that the defect has been fixed and that no new defects have been introduced.
-
Closure: The defect is marked as closed if the tester confirms that the fix has resolved the issue, or reopened if the issue persists.
2. What does linear search time mean?
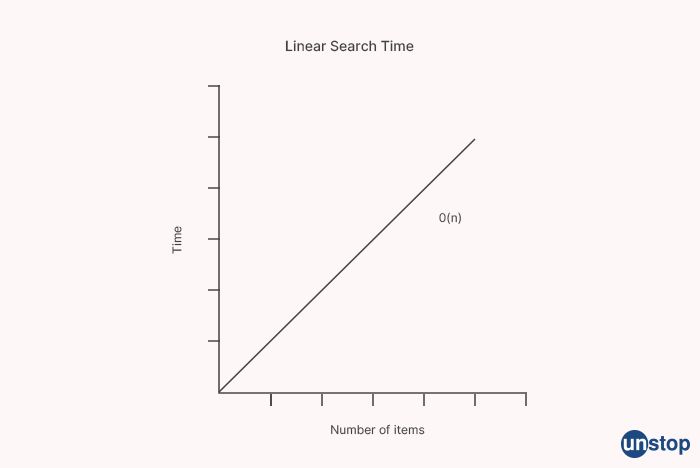
The time complexity of a linear search algorithm is O(n), where n is the number of elements in the list or array being searched. This means that the time taken by the algorithm increases linearly with the size of the input data.
In a linear search, the algorithm examines each element in the list or array one by one until the target element is found or the entire list is searched. In the worst-case scenario, where the target element is not found or is located at the end of the list, the algorithm will have to examine every element in the list, leading to a time complexity of O(n).
The linear search algorithm is a simple algorithm that is useful for small datasets or when the data is not sorted. However, for large datasets or when the data is sorted, more efficient search algorithms such as binary search can be used to achieve faster search times.
3. How can I locate the IP address associated with my destination?
To locate the IP address associated with your destination, you can follow these steps:
- Open a command prompt or terminal window on your computer.
- Type "ping" followed by the website address or domain name of your destination.
- Press the Enter key on your keyboard.
- The ping command will send packets of data to the website address and display the IP address associated with that address in the output. Look for the line that says "Reply from" or "64 bytes from" followed by an IP address.
- Note down the IP address displayed in the output.
4. What does modem mean during packet data transfer?
A modem (short for modulator-demodulator) is a device used to modulate digital data into analog signals that can be transmitted over a phone line, cable, or other communication media, and to demodulate those signals back into digital data at the receiving end.
In the context of packet data transfer, a modem is typically used to connect a computer or other digital device to a network or the Internet over a physical communication medium, such as a phone line, cable, or satellite link. The modem converts the digital data into analog signals that can be transmitted over the communication medium, and then receives and demodulates the signals back into digital data at the receiving end.
Modems are often used in conjunction with protocols such as TCP/IP to enable reliable and efficient packet data transfer over a network or the Internet. The modem may be integrated into the computer or digital device, or it may be a separate device that is connected to the device via a serial or USB port.
5. What is meant by "packet data transfer"?
Packet data transfer refers to the process of transmitting data over a network in discrete units known as packets. In packet data transfer, the data to be transmitted is broken up into small packets, each containing a portion of the data as well as some additional information such as the destination address, source address, and other control information.
The packets are then transmitted over the network, with each packet traveling independently and taking its own route to the destination. As the packets travel over the network, they may encounter congestion, errors, or delays, but the control information contained within each packet allows the network to route the packets to their intended destination and reassemble them into their original form.
6. How many fields does a node in the DLL have?
A node in a Doubly Linked List (DLL) typically has three fields or attributes:
-
A data field: This field stores the actual data or value associated with the node.
-
A "next" field: This field contains a pointer or reference to the next node in the list.
-
A "previous" field: This field contains a pointer or reference to the previous node in the list.
The "next" and "previous" fields allow the DLL to be traversed in both directions, making it easier to insert or delete nodes at any position in the list.
7. What is the role of the IP layer in the network?
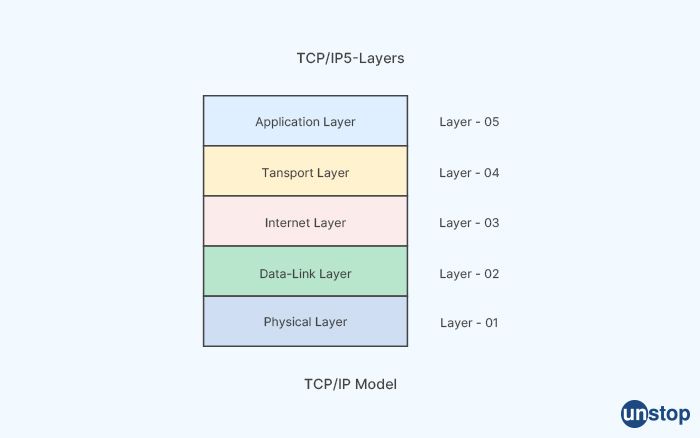
The IP (Internet Protocol) layer is a crucial component of the network stack that provides a standardized way of sending and receiving data over the internet and other computer networks. The main role of the IP layer in the network is to provide a logical addressing system that allows data to be transmitted from a source device to a destination device across different networks.
Specifically, the IP layer:
-
Provides a unique IP address to each device connected to the network, enabling packets of data to be sent to and received from specific devices.
-
Divides large data packets into smaller packets, known as IP datagrams, and encapsulates each packet with the necessary control information, such as the source and destination IP addresses.
-
Routes IP datagrams through the network, making use of routing protocols such as OSPF or BGP to determine the best path for the data to take based on factors such as network congestion and latency.
-
Performs fragmentation and reassembly of IP datagrams when necessary, ensuring that packets can be transmitted over networks with different Maximum Transmission Unit (MTU) sizes.
-
Performs error checking and packet retransmission to ensure that data is transmitted reliably.
8. What is meant by "Machine Warm-Up Time"?
Machine warm-up time refers to the period that a machine or device needs to reach its optimal operating temperature and performance level after being turned on or awakened from a sleep or standby state.
During the warm-up time, the machine may experience reduced efficiency or performance, as well as increased power consumption, as it works to reach its ideal temperature and operational state. This can be particularly noticeable with certain types of equipment, such as printers, photocopiers, and industrial machinery, which may require extended warm-up times to function properly.
9. How long does the circuit breaker stay on while it's operating?
The term "total operating time" refers to the aggregate of "pre-arcing time" and "arcing time." It is about 2 milliseconds, or 0.002 seconds, for a fuse. It ranges anywhere between 0.02 and 0.1 seconds for the circuit breaker.
10. What is the run-up time?
"Run-up time" refers to the amount of time it takes for a system or machine to reach its fully operational state after it has been started or powered on. This time period can vary depending on the complexity and size of the system or machine.
The run-up time is an important consideration in the design and operation of complex systems and machines, as it can impact the efficiency and productivity of the system. In some cases, steps may be taken to reduce the run-up time, such as using faster components or optimizing the start-up process.
11. What does "time step" refer to in a CFD simulation?
In a Computational Fluid Dynamics (CFD) simulation, a "time step" refers to the duration of time over which the simulation is advanced. A CFD simulation typically involves solving a set of mathematical equations that describe the behavior of fluid flow over time. To solve these equations, the simulation must be divided into discrete time steps, with each time step representing a small increment of time during which the fluid flow behavior is assumed to be constant.
12. What is meant by the term "compress function"?
The COMPRESS function's primary purpose is to "compress" a character string by removing all of the blanks and spaces in it. To put it another way, it gets rid of any leading, trailing, and intermediate spaces in the strings. The COMPRESS function accepts parameters of type null. A null argument is handled the same way as a string that has zero characters added to its length.
13. What is meant by the term "block function"?
Functions that use the pattern func.. func/ are referred to as block functions. In other words, they encapsulate a template block and perform operations on the contents of the block that they encompass. Because block functions take precedence over custom methods of the same name, it is not possible to have both a custom function and a block function with the name func. {/func}
14. What is a "calling function", and what is a "called function"?
In computer programming, a "calling function" (also known as a "caller" or "parent function") is a function that invokes or calls another function to perform a specific task as part of its execution. The calling function typically passes one or more arguments to the called function, which are used by the called function to perform its task.
On the other hand, a "called function" (also known as a "callee" or "child function") is a function that is invoked or called by another function to perform a specific task. The called function typically receives one or more arguments from the calling function, which are used by the called function to perform its task. Once the called function completes its task, it returns control to the calling function.
For example, suppose we have two functions: "calculateSum" and "displayResult". The calculateSum function takes two numbers as arguments and returns their sum, while the displayResult function takes a single argument and displays it on the screen. If we want to calculate the sum of two numbers and display the result, we could call the calculateSum function from within the displayResult function, like this:
function calculateSum(a, b) {
return a + b;
}
function displayResult(num) {
var sum = calculateSum(5, 10);
console.log("The sum is " + sum);
}
displayResult();
In this example, the calculateSum function is the called function, and the displayResult function is the calling function. The calculateSum function is called from within the displayResult function, and the result of the calculateSum function is passed as an argument to the displayResult function, which then displays it on the screen.
15. What is meant by the term "complex function"?
A complex function is a function that takes complex numbers as input and outputs more complex values. In other words, it is a function that seems to have a subset of the complex numbers as its domain and the complex numbers as its codomain. In other words, the complex numbers themselves are the codomain. In most cases, complex functions are expected to have domains that include non-empty open subsets of the complex plane.
Stay ahead! Never miss out any trending job or internship opportunity!
16. What is a diagram of function blocks?
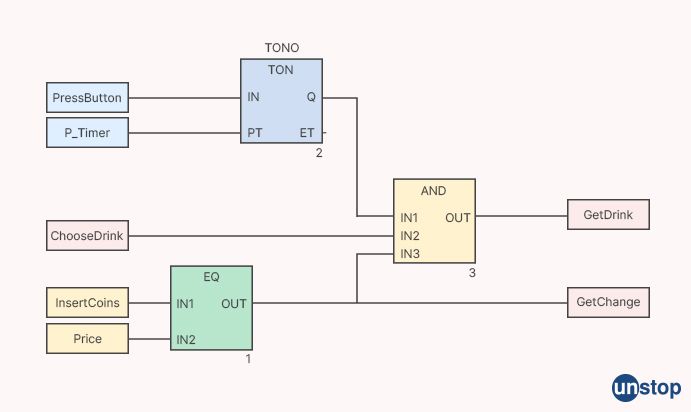
The Function Block Diagram (FBD) is a graphical language for the design of programmable logic controllers that may represent the function that exists between the variables that are input and the variables that are output. One way to think about a function is as a collection of fundamental building elements. Lines of connection are used to link input and output variables to their respective blocks.
17. How do you utilize function modules?
In SAP ABAP programming, function modules are used to encapsulate and reuse pieces of code that perform specific tasks or operations. Here are the basic steps to utilize function modules in your ABAP programs:
-
Find the function module you want to use: You can find function modules using the Function Builder (SE37) transaction in SAP.
-
Declare the function module in your program: Declare the function module you want to use in your program using the FUNCTION statement.
-
Pass input parameters to the function module: Input parameters are the values that are passed to the function module to perform its operation. You can pass input parameters to the function module using the IMPORT statement.
-
Call the function module: Once the input parameters have been set, call the function module using the CALL FUNCTION statement.
-
Retrieve the output parameters: Output parameters are the values returned by the function module after it has completed its operation. You can retrieve the output parameters using the EXPORT statement.
-
Handle any exceptions: Function modules may raise exceptions or errors if there is a problem with the input parameters or the operation being performed. You can handle exceptions using the EXCEPTIONS statement.
18. What do you mean by structured data types?
Structured data types are a way of defining complex data structures that contain multiple data elements of different types. They allow programmers to create more flexible and modular code that can handle different types of data in a structured and organized manner.
There are several different types of structured data types in programming, including:
-
Arrays: An array is a collection of data elements of the same type, stored in contiguous memory locations. Arrays are useful for storing and manipulating large amounts of data that can be accessed using an index.
-
Structures: A structure is a collection of data elements of different types, grouped under a single name. Structures allow programmers to define their own data types that can be used to represent complex data structures.
-
Classes: A class is a blueprint for creating objects that contain data and methods. Classes are used in object-oriented programming to create more modular and reusable code.
-
Records: A record is a collection of data elements of different types, stored under a single name. Records are similar to structures but are used in different programming languages and systems.
-
Enumerations: An enumeration is a data type that consists of a set of named values. Enumerations are useful for defining a fixed set of values that can be used to represent different options or states.
19. Can you name the four different kinds of variables?
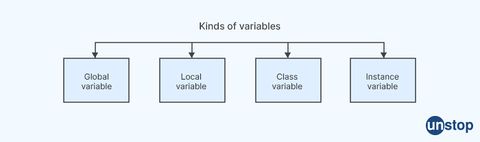
In programming, there are four different kinds of variables:
-
Local variables: Local variables are variables that are defined within a function or block of code and are only accessible within that function or block. They are typically used to store temporary values or intermediate results.
-
Global variables: Global variables are variables that are defined outside of any function or block of code and can be accessed from anywhere in the program. They are typically used to store values that need to be shared between different parts of the program.
-
Instance variables: Instance variables are variables that are defined within a class and are accessible from any method within that class. They are used to store data that is specific to each instance of the class.
-
Class variables: Class variables are variables that are defined within a class but outside of any method, and are shared by all instances of that class. They are used to store data that is common to all instances of the class.
20. What is an error, and how many different kinds of errors are there?
In Java, an Error is a subclass of Throwable that represents a serious problem that a program should not attempt to recover from. Errors are typically caused by low-level problems such as a system crash, out-of-memory conditions, or other unrecoverable issues that prevent the Java Virtual Machine (JVM) from operating properly.
There are several different kinds of Errors in Java:
-
VirtualMachineError: This type of error is thrown when there is a problem with the Java Virtual Machine itself, such as an out-of-memory condition or a stack overflow.
-
AssertionError: This error is thrown when an assertion fails, indicating a programming error.
-
LinkageError: This error is thrown when there is a problem with the class loading mechanism, such as a missing or incorrect class file.
-
OutOfMemoryError: This error is thrown when the JVM runs out of memory and is unable to allocate additional memory.
-
StackOverflowError: This error is thrown when the call stack overflows due to too many recursive function calls.
-
UnknownError: This error is thrown when an unknown error occurs that cannot be classified into one of the other Error subclasses.
21. What is meant by the terms "program compilation" and "program execution"?
In general, program compilation and program execution refer to two distinct phases in the life cycle of a computer program.
Program compilation refers to the process of translating human-readable code, typically written in a high-level programming language, into machine-readable instructions that can be understood and executed by a computer. During compilation, the source code is typically translated into an executable format that can be run directly on the target machine's hardware. The output of the compilation process is typically a file or set of files that can be executed on the target machine.
Program execution, on the other hand, refers to the process of running a compiled program on a computer. This typically involves loading the program into memory, setting up any required data structures, and executing the program's instructions in sequence. During execution, the program interacts with the computer's hardware, accessing and modifying memory locations, sending and receiving data from I/O devices, and performing other operations required to achieve its intended purpose.
22. What is a "program statement"?
A statement is a grammatical unit of an imperative programming language that indicates an action that should be carried out. Statements are used in computer programming. Statements can be strung together in any order to form the basis of a program written in just such a language. A statement could have parts contained inside it (e.g., expressions).
23. What do the terms absolute address and relative address mean?
In computer science, an absolute address refers to a memory address that is specified as a fixed, unchanging value. This value is typically expressed as a hexadecimal number and represents the exact location in memory where data is stored or instructions are executed. Absolute addresses are used in low-level programming languages and systems programming, where direct control over memory is required.
In contrast, a relative address refers to a memory address that is specified relative to another location in memory, rather than as an absolute value. Relative addresses are typically used in higher-level programming languages, where the actual location of data or code in memory is less important. Instead, the programmer specifies the relative position of data or code in relation to another location, such as the beginning of a data structure or function.
24. Can you provide me with an example of a range address?
A range address refers to a group of cells in a spreadsheet application like Microsoft Excel or Google Sheets. The range address specifies the starting cell and the ending cell of the range, separated by a colon (:). Here is an example of a range address in Excel: A1:B10
This range address refers to a rectangular area of cells that starts in cell A1 and extends to cell B10, inclusive. This range contains a total of 20 cells, including cells A1, A2, A3, and so on up to B10.
25. What are some of the advantages of DHCP?
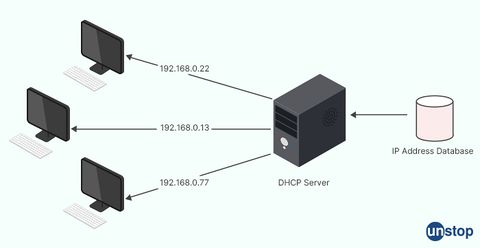
Dynamic Host Configuration Protocol (DHCP) is a network protocol that enables the automatic allocation of IP addresses and other network configuration settings to devices on a network. Here are some advantages of using DHCP:
-
Automatic IP Address Assignment: DHCP automatically assigns IP addresses to devices on a network, eliminating the need for manual configuration. This makes it easier to add new devices to the network and reduces the likelihood of IP address conflicts.
-
Centralized Network Management: DHCP allows network administrators to centrally manage IP address allocation and configuration settings. This simplifies network management and reduces the likelihood of errors that can arise from the manual configuration.
-
Scalability: DHCP is scalable and can easily accommodate networks with a large number of devices. It also simplifies network administration by automating IP address allocation and management, freeing up time for network administrators to focus on other tasks.
-
Flexibility: DHCP provides flexibility in terms of configuration options, such as assigning fixed IP addresses to specific devices or setting up a guest network with limited access to the network resources.
-
Security: DHCP includes features that can enhance network security, such as assigning IP addresses from a pool of addresses that are not publicly routable, and enabling MAC address filtering to limit access to the network.
26. What are some of the downsides of using DHCP?
While DHCP has many advantages, there are also some downsides to consider. Here are a few potential disadvantages of using DHCP:
-
IP Address Conflicts: While DHCP helps reduce the likelihood of IP address conflicts, they can still occur if multiple devices on the network are configured to use the same IP address. This can cause network connectivity issues and can be difficult to diagnose.
-
Single Point of Failure: DHCP relies on a central server to allocate IP addresses and manage network configuration settings. If the DHCP server fails, devices on the network may lose their network connectivity until the server is restored.
-
Configuration Errors: DHCP configuration errors can cause problems on the network, such as assigning incorrect IP addresses or configuration settings to devices. This can lead to connectivity issues and other network problems.
-
Potential Security Risks: DHCP can also introduce security risks if not properly configured. For example, an unauthorized device can potentially obtain an IP address and gain access to the network.
-
Limited Control: While DHCP provides flexibility in terms of configuration options, it also limits the control that network administrators have over individual devices. This can make it difficult to troubleshoot issues or enforce network policies on a per-device basis.
27. In Java, is it possible to make array elements volatile?
No, it is not possible to make individual elements of an array volatile in Java. The volatile keyword in Java can only be applied to fields of classes or to variables declared as local variables in a method or block. It is used to indicate that the value of the field or variable may be modified by multiple threads and that these modifications must be visible to all threads.
In the case of an array, you can declare the array itself as volatile, but this only makes the reference to the array volatile, not the individual elements of the array. If you need to ensure that the individual elements of an array are updated atomically and visible to all threads, you can use the synchronized keyword or other thread-safe mechanisms, such as locks or atomic variables.
28. What is involved in a busy spin? Why should you make use of it?
A busy spin is a technique used in multithreaded programming where a thread repeatedly executes a loop while waiting for a shared resource to become available. Instead of blocking or sleeping, the thread actively spins in a loop, checking the state of the resource at regular intervals.
The main advantage of a busy spin is that it can reduce the latency of accessing a shared resource. If the resource becomes available quickly, the thread can acquire it without any delay, whereas a blocked or sleeping thread would have to wait for the resource to become available and for the operating system scheduler to wake it up. This can result in faster execution times and better performance in some scenarios.
29. Is there no risk of thread tangling with swing?
Yes, there is a risk of thread tangling or thread synchronization issues when working with Swing in Java.
Swing is a GUI (graphical user interface) toolkit that is used to create desktop applications in Java. The Swing toolkit is designed to be used in a single-threaded environment, where all updates to the user interface are performed on a single thread known as the Event Dispatch Thread (EDT).
Any updates to the user interface should be performed on the EDT to avoid thread synchronization issues. If updates are performed on a different thread, it can result in race conditions, deadlocks, or other thread synchronization issues.
30. Why is it not possible to change a string in Java?
As the designers of Java anticipated that string would see heavy use, they made it such that it could not be changed. This allowed for certain optimizations to be made, and it also made it easier for numerous clients to use the same String object. For a more in-depth explanation, please check out the link provided. This is an excellent question for Java programmers who have less expertise because it provides them with food for thought. It prompts them to think about how things function in Java, what Jave designers could have been thinking when they built the String class, and other related topics.
31. In the switch case, is it possible to utilize the string variable?
Yes, it is possible to use a String variable in a switch statement in Java starting from version 7. Before Java 7, only primitive types (byte, short, int, char) and enumerated types could be used in a switch statement.
To use a String variable in a switch statement, you simply provide the String variable as the expression in the switch statement and then list the possible values in the case statements. For example:
String color = "red";
switch(color) {
case "red":
System.out.println("The color is red");
break;
case "blue":
System.out.println("The color is blue");
break;
case "green":
System.out.println("The color is green");
break;
default:
System.out.println("The color is not red, blue, or green");
}
U3RyaW5nIGNvbG9yID0gInJlZCI7Cgpzd2l0Y2goY29sb3IpIHsKY2FzZSAicmVkIjoKU3lzdGVtLm91dC5wcmludGxuKCJUaGUgY29sb3IgaXMgcmVkIik7CmJyZWFrOwpjYXNlICJibHVlIjoKU3lzdGVtLm91dC5wcmludGxuKCJUaGUgY29sb3IgaXMgYmx1ZSIpOwpicmVhazsKY2FzZSAiZ3JlZW4iOgpTeXN0ZW0ub3V0LnByaW50bG4oIlRoZSBjb2xvciBpcyBncmVlbiIpOwpicmVhazsKZGVmYXVsdDoKU3lzdGVtLm91dC5wcmludGxuKCJUaGUgY29sb3IgaXMgbm90IHJlZCwgYmx1ZSwgb3IgZ3JlZW4iKTsKfQ==
In this example, we define a String variable called "color" and then use it as the expression in the switch statement. We then list the possible values for "color" in the case statements. If the value of "color" matches one of the case values, the corresponding code block is executed. If the value of "color" does not match any of the case values, the code block in the default case is executed.
32. What is meant by the term "constructing" in the Java programming language?
In Java, constructing refers to the process of creating an instance of a class. A class is a blueprint or a template for creating objects, and an object is an instance of a class. To create an object, you must first create an instance of the class using the new operator.
When you create an instance of a class, Java allocates memory for the object on the heap and initializes its instance variables. The constructor is a special method that is called automatically when an object is created using the new operator. It has the same name as the class and is used to initialize the object's state. Constructors can have parameters, which are used to pass values to the object during construction. If a class does not define any constructors, Java provides a default constructor that takes no arguments and does nothing.
33. What is the mechanism behind WeakHashMap's operation?
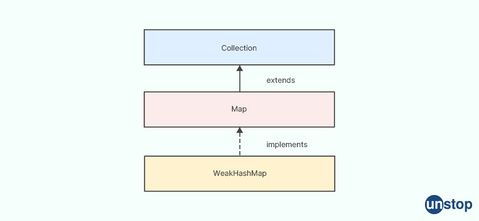
A WeakHashMap in Java is a specialized implementation of the Map interface that uses weak references to keys. In a standard HashMap, the keys are strong references, which means that the object referenced by the key will not be garbage collected until the reference to the key itself is removed. However, in a WeakHashMap, the keys are held using weak references, which means that they can be garbage collected if they are no longer referenced elsewhere in the program.
The main mechanism behind WeakHashMap's operation is that the garbage collector can remove entries whose keys are no longer referenced elsewhere in the program. This allows the WeakHashMap to avoid holding on to objects that are no longer needed, which can help prevent memory leaks and improve performance.
34. Can you explain the Java heap space and the garbage collection process?
Memory is allotted to the Java process whenever the Java command is used to initiate the commencement of a Java process. A portion of this memory is used to create heap space, which will be used to allocate memory to objects whenever they are formed in the program. This space is produced using some of the memory that is currently available. The term "garbage collection" refers to the process that takes place within the JVM that frees up memory that was previously occupied by dead objects so that it may be used for other purposes.
35. In Java, what is the main difference between the stack and heap?
In Java, the main difference between the stack and the heap is how they store data and how memory is allocated and managed.
The stack is a region of memory that is used to store method calls and local variables. Each method call creates a new stack frame that is added to the top of the stack. The stack is managed by the JVM and has a fixed size, which is determined at runtime based on the available memory. Because the stack is limited in size, it is usually used for storing simple data types, such as primitive values and references to objects.
The heap is a region of memory that is used to store objects and arrays. Unlike the stack, the heap is managed dynamically by the JVM and does not have a fixed size. Memory is allocated from the heap as needed, and objects can be resized or garbage-collected when they are no longer in use. Because the heap can grow dynamically, it is usually used for storing more complex data types, such as objects and arrays.
36. What is the definition of wrapper classes?
Java primitives may be converted into reference objects by making use of wrapper classes.
- The following is a list of features that are included in Java wrapper classes:
- Wrapper classes are responsible for transforming numerical strings into their corresponding numeric values.
- They are employed to store data of a more fundamental kind within the item.
- Every single one of the wrapper classes makes use of the typeValue() function. It gives back the value of the object as well as the primitive type of that value. Specifically, the function valueOf() { [native code] }() function is utilized by the wrapper classes.
37. The term "pointer" refers to what? Does Java support a pointer?
Java supports pointers internally, but it does not expose them to developers in the same way that low-level programming languages like C and C++ do. Instead, Java provides a safer and more abstract way of working with memory through object references.
In Java, all objects are accessed through reference variables, which are essentially pointers that hold the memory address of the object. However, unlike pointers in C and C++, reference variables in Java are strongly typed and are automatically initialized to null when they are declared. This helps to prevent many of the memory-related errors that can occur when working with pointers in low-level languages.
38. What are these "instance variables"?
An instance variable is a variable that is defined within a class but not within a method. This type of variable can be used outside of a method. Because these variables are automatically set to their default values before being used, it is not necessary to initialize them before using them.
Important characteristics of instance variables:
- They are defined within the class, which means that they are located outside of the method.
- When an object is formed, instance variables are likewise produced at the same time; however, this process also serves to destroy the object's purpose.
- Instance variables often have access modifiers applied to them.
- They are accessible to all of the constructors, methods, and blocks that are part of the class.
- The instance variables are assigned their respective default values. When the value is a number, it will be written as "0," and when it is a boolean, it will be written as "FALSE."
39. What is the JIT compiler?
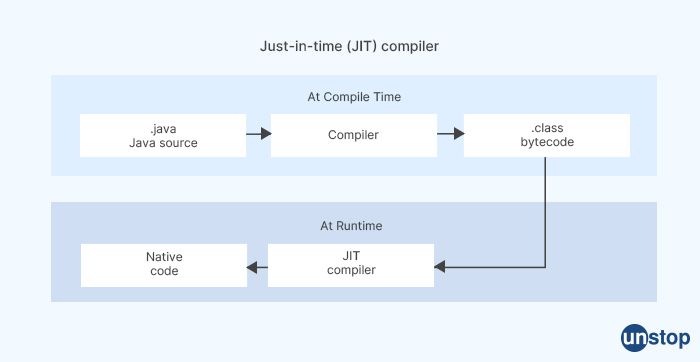
Just-In-Time Compiler is what "JIT" stands for. It enhances the functionality of Java programs when they are being operated, often known as the execution time. It accomplishes this goal by transforming bytecode into native machine code, which may then be sent unmodified to the processor of a computer (CPU). It is turned on automatically whenever a Java method is invoked, as it is enabled by default. The JIT compiler is an integral component of the JVM. Whenever a method has been compiled, the JVM makes a straight call to the code that was compiled for that method rather than interpreting the original code.
The JIT compilation process consumes both the time of the processor and the memory of the computer. The AOT (Ahead-of-Time compilation) and interpretation methods are both incorporated into the JIT compilation process. These methods are used to transform source code into machine code.
40. How can you put the singleton pattern into practice?
The Singleton pattern is a design pattern in object-oriented programming that restricts the instantiation of a class to one single instance and provides global access to that instance. This can be useful in situations where you need to ensure that only one instance of a class exists and that this instance can be accessed from anywhere in your codebase.
Here are the steps to implement the Singleton pattern in Java:
-
Declare a private static variable of the same type as the class itself. This will hold the single instance of the class.
-
Declare a private constructor for the class, to prevent other classes from instantiating it.
-
Define a public static method that returns the single instance of the class. This method should check whether the instance variable is null, and if so, create a new instance of the class.
-
Optionally, implement the Serializable interface and provide a readResolve() method to ensure that deserialized instances are also singletons.
Here is an example implementation of the Singleton pattern in Java:
public class MySingleton {
private static MySingleton instance = null;
private MySingleton() {
// private constructor to prevent instantiation
}
public static MySingleton getInstance() {
if (instance == null) {
instance = new MySingleton();
}
return instance;
}
}
cHVibGljIGNsYXNzIE15U2luZ2xldG9uIHsKcHJpdmF0ZSBzdGF0aWMgTXlTaW5nbGV0b24gaW5zdGFuY2UgPSBudWxsOwoKcHJpdmF0ZSBNeVNpbmdsZXRvbigpIHsKLy8gcHJpdmF0ZSBjb25zdHJ1Y3RvciB0byBwcmV2ZW50IGluc3RhbnRpYXRpb24KfQoKcHVibGljIHN0YXRpYyBNeVNpbmdsZXRvbiBnZXRJbnN0YW5jZSgpIHsKaWYgKGluc3RhbmNlID09IG51bGwpIHsKaW5zdGFuY2UgPSBuZXcgTXlTaW5nbGV0b24oKTsKfQpyZXR1cm4gaW5zdGFuY2U7Cn0KfQ==
41. How does one go about implementing a queue in Java?

A queue is a type of linear data structure that functions similarly to a stack in terms of its structure. It is an interface that can be found in java.util package. Its purpose is to store elements while also allowing for actions of insertion and deletion. During this procedure, the first element is added from the end, which is referred to as the REAR (Tail), and the element that was previously there is removed from the end, which is referred to as the FRONT (Head). FIFO is an acronym that refers to the entire process of implementing queues (First in first out).
42. In Java, what is a classloader?
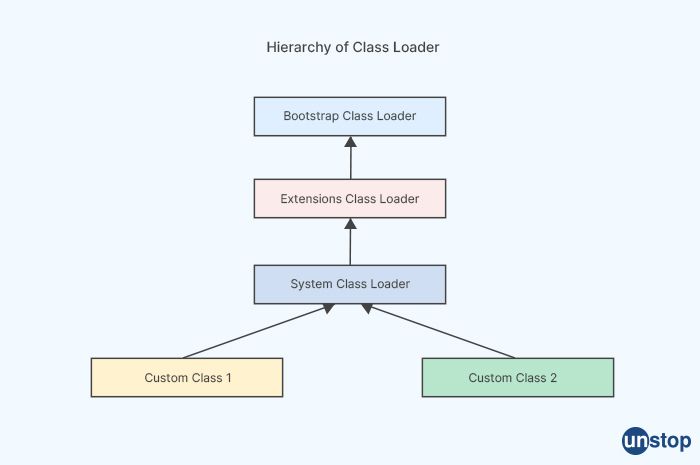
In Java, a class loader is a component of the Java Runtime Environment (JRE) that is responsible for loading Java classes at runtime. The class loader is part of the Java virtual machine (JVM) and is responsible for locating, loading, and linking the bytecode of the class files needed to run a Java program.
There are three types of class loaders in Java:
-
Bootstrap class loader: This is the built-in class loader that is responsible for loading core Java classes, such as those in the java.lang package. It is part of the JVM and is written in native code.
-
Extension class loader: This class loader is responsible for loading classes from the Java extension directories, which are directories specified by the java.ext.dirs system property.
-
System class loader: This class loader is responsible for loading classes from the application classpath, which is a list of directories and JAR files specified by the java.class.path system property.
In addition, Java allows you to create custom class loaders to load classes from non-standard locations or to implement custom loading behavior. The class loader hierarchy in Java is hierarchical, with each class loader delegating to its parent class loader if it cannot find the requested class. This delegation model allows for better control over class loading and prevents classes from being loaded multiple times.
43. What are the most important things to know about Java packages?
A collection of Java classes and interfaces that have been bundled together in such a way that they are connected to one another is referred to as a Java package. Java packages offer several advantages, including the ability to avoid name clashes, assist in the organization of source code, conceal implementation details for numerous classes, simplify the searching for and locating of classes, as well as the utilization of control access and annotations.
44. What is polymorphism?
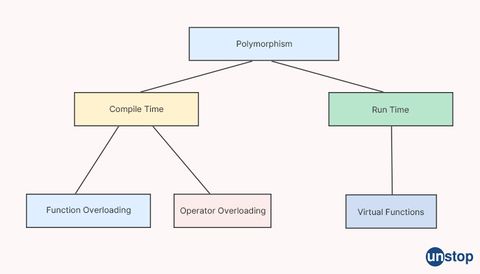
Polymorphism is a fundamental concept in object-oriented programming (OOP) that allows objects of different classes to be treated as if they are objects of the same class. It enables code to be written in a more general way, making it more flexible and reusable.
There are two types of polymorphism:
-
Compile-time polymorphism: This is also called method overloading. It occurs when multiple methods in a class have the same name, but different parameters. The compiler determines which method to call based on the number, types, and order of the arguments passed to it.
-
Runtime polymorphism: This is also called method overriding. It occurs when a subclass provides its implementation of a method that is already defined in its superclass. When a method is called on an object of the subclass, the overridden method in the subclass is called, rather than the method in the superclass.
Polymorphism is important because it allows objects of different classes to be treated uniformly, simplifying the code and making it more flexible. It also enables code to be written in a more general way, reducing duplication and making it easier to maintain and extend.
45. What is the difference between ArrayList and LinkedList in Java?
ArrayList and LinkedList are both implementations of the List interface in Java, but they differ in how they store and access their elements.
ArrayList is implemented as a resizable array. When you add an element to an ArrayList, the element is stored in an array, and if the array is full, a new larger array is created and the existing elements are copied to the new array. This means that accessing an element in an ArrayList is fast because the elements are stored contiguously in memory.
On the other hand, LinkedList is implemented as a doubly linked list. When you add an element to a LinkedList, the element is stored as a node, which contains a reference to the previous and next nodes in the list. This means that accessing an element in a LinkedList requires traversing the list from the beginning or end to find the desired node, which can be slower than accessing an element in an ArrayList. However, adding or removing elements from a LinkedList is fast, because it only requires updating the references of the affected nodes.
46. What is a copy function Object() { [native code] } in Java?
In Java, there is a unique kind of function Object() { [native code] } known as the Duplicate Constructor that is utilized to give a copy of the objects that have been supplied. The majority of the time, a developer will utilize this when they wish to duplicate something heavy to instantiate. In addition, it is suggested that the deep copy method be utilized to remove both of the objects. In addition to that, it grants complete control over the production of objects.
47. What is a Java servlet, and how does it work?
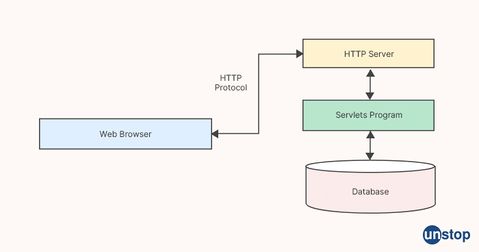
A Java servlet is a server-side component that runs on a web server and is responsible for handling client requests and generating responses to those requests. Servlets are written in Java and follow the Java Servlet API, which defines a set of interfaces and classes that servlets can use to communicate with the web server.
When a client (usually a web browser) sends a request to a web server, the web server passes the request to the appropriate servlet based on the URL in the request. The servlet then processes the request and generates a response, which is sent back to the client.
The lifecycle of a servlet consists of the following stages:
-
Loading: When a servlet is first requested, the web server loads the servlet class into memory.
-
Initialization: After the servlet class is loaded, the web server initializes the servlet by calling its init() method. This is where the servlet can perform any necessary initialization tasks, such as setting up database connections or initializing variables.
-
Handling requests: When a client sends a request to the web server, the web server passes the request to the appropriate servlet. The servlet then processes the request and generates a response, which is sent back to the client.
-
Destroying: When the web server is shutting down, it calls the servlet's method,destroy() allowing the servlet to perform any necessary cleanup tasks.
48. What is the difference between LinkedHashMap and PriorityQueue in Java?
LinkedHashMap and PriorityQueue are two different data structures in Java that serve different purposes.
A LinkedHashMap is a hash table implementation of the Map interface, with predictable iteration order. It maintains a linked list of the entries in the map, in the order in which they were inserted. This means that if you iterate over the map, the entries will be returned in the order in which they were inserted. It is useful when you want to maintain the insertion order of elements and also want fast access to the entries in the map.
On the other hand, a PriorityQueue is a queue implementation that provides priority-based ordering of elements. The elements in a PriorityQueue are ordered based on their natural order or a custom order specified by a Comparator. When you add elements to a PriorityQueue, they are ordered according to their priority, and the element with the highest priority is always at the front of the queue. It is useful when you want to process elements based on their priority.
49. What is the yield() method?
The yield() method is a method in Java's Thread class that suggests to the scheduler that the current thread is willing to yield its current use of a processor. When a thread calls yield(), it gives a hint to the scheduler that it is willing to yield the processor voluntarily. The scheduler can then give the processor to another thread with the same or higher priority. However, the scheduler is free to ignore this hint and continue to allow the current thread to execute. Also, it's important to note that yield() is not a blocking call, so the thread that calls yield() can be scheduled immediately to run again.
The yield() method can be useful in situations where multiple threads are competing for the same resources, or where a lower-priority thread wants to give the processor to a higher-priority thread. However, it's important to use it judiciously, as excessive use of yield() can result in reduced performance, since it may cause unnecessary context switching.

Sample HR questions for Siemens
Here are some of the essential HR interview questions that you should prepare for while walking into the Siemens interview for the HR round-
50. How would you handle a tough situation with effective communication?
51. Will you work on improving your communication skills?
52. Take us through your academic background or academic profile?
53. Tell us about your family background.
54. What tools are you using on your current project?
55. What was your favorite subject in college?
56. Who do you consider your role model?
57. Name 5 leadership qualities that make you a better candidate for this role.
58. Do you believe in delegation? Why do you think it is important?
59. Do you believe intuition plays a role in decision-making? Elaborate on a situation where you trusted your intuition and achieved what you wanted.
The recruitment process at Siemens
Candidates who have just submitted their resumes for consideration at one of Siemens job openings are strongly encouraged to read this article to obtain information that is both comprehensive and verifiable on the Siemens selection process. The following is a rundown of the Siemens hiring process, which is primarily followed by the recruiting team of Siemens to employ qualified applicants to work for their firm.
The recruitment process at Siemens is broken up into 4 steps.
Candidates need to pass each of these phases to be placed on the shortlist. The Siemens technical interview questions and Siemens HR interview Questions are provided here for your use as a reference once you have completed your research on the Siemens test pattern and selection procedure, as well as the most recent Siemens exam pattern for the technical job profile. There are also several Siemens placement papers available that you must go through.
- Technical exam conducted online
- Online aptitude test
- Interviews with technical experts
- HR interview
About Siemens
Siemens Limited is a technology company that specializes in the manufacturing sector, as well as infrastructure, digital transformation, mobility, and the transmission and generation of electrical power. It is Siemens AG's most prominent publicly traded company in India. The organizational structure of the company is perfectly adapted to meet the expectations of the market for higher productivity, quality, adaptability, and swiftness. The product-based firm has a wide portfolio, an organizational structure that is market-oriented, global technological leadership, and strong local expertise, all of which put it in an excellent position to aid the country in attaining long-term success. Siemen is among the most reputed companies across the globe.
There are opportunities to join Siemens practically anywhere on the face of the earth. In the fields of engineering, manufacturing, research and development, information technology, sales and marketing, and operations, they are looking for new talent.
Preparing for tech interviews? Here are more reads for you:
- Top Cognizant Interview Questions and Answers (Prepare Yourself For The D-Day!)
- Top 50+ TCS Interview Questions And Answers (Bookmark Them!)
- An Overview Of Zoho Interview Questions And Recruitment Process
- Top Salesforce Interview Questions To Help You Prepare Well!
- Important BYJU's Interview Questions That Will Help You Prepare Better
I am a storyteller by nature. At Unstop, I tell stories ripe with promise and inspiration, and in life, I voice out the stories of our four-legged furry friends. Providing a prospect of a good life filled with equal opportunities to students and our pawsome buddies helps me sleep better at night. And for those rainy evenings, I turn to my colors.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter















Comments
Add comment