- TCS Technical Interview Questions & Answers
- TCS Managerial Interview Questions & Answers
- TCS HR Interview Questions & Answers
- Overview of Cognizant Recruitment Process
- Cognizant Interview Questions: Technical
- Cognizant Interview Questions: HR Round
- Overview of Wipro Technologies Recruitment Rounds
- Wipro Interview Questions
- Technical Round
- HR Round
- Online Assessment Sample Questions
- Frequently Asked Questions
- Overview of Google Recruitment Process
- Google Interview Questions: Technical
- Google Interview Questions: HR round
- Interview Preparation Tips
- About Google
- Deloitte Technical Interview Questions
- Deloitte HR Interview Questions
- Deloitte Recruitment Process
- Technical Interview Questions and Answers
- Level 1 difficulty
- Level 2 difficulty
- Level 3 difficulty
- Behavioral Questions
- Eligibility Criteria for Mindtree Recruitment
- Mindtree Recruitment Process: Rounds Overview
- Skills required to crack Mindtree interview rounds
- Mindtree Recruitment Rounds: Sample Questions
- About Mindtree
- Preparing for Microsoft interview questions
- Microsoft technical interview questions
- Microsoft behavioural interview questions
- Aptitude Interview Questions
- Technical Interview Questions
- Easy
- Intermediate
- Hard
- HR Interview Questions
- Eligibility criteria
- Recruitment rounds & assessments
- Tech Mahindra interview questions - Technical round
- Tech Mahindra interview questions - HR round
- Hiring process at Mphasis
- Mphasis technical interview questions
- Mphasis HR interview questions
- About Mphasis
- Technical interview questions
- HR interview questions
- Recruitment process
- About Virtusa
- Goldman Sachs Interview Process
- Technical Questions for Goldman Sachs Interview
- Sample HR Question for Goldman Sachs Interview
- About Goldman Sachs
- Nagarro Recruitment Process
- Nagarro HR Interview Questions
- Nagarro Aptitude Test Questions
- Nagarro Technical Test Questions
- About Nagarro
- PwC Recruitment Process
- PwC Technical Interview Questions: Freshers and Experienced
- PwC Interview Questions for HR Rounds
- PwC Interview Preparation
- Frequently Asked Questions
- EY Technical Interview Questions (2023)
- EY Interview Questions for HR Round
- About EY
- Morgan Stanley Recruitment Process
- HR Questions for Morgan Stanley Interview
- HR Questions for Morgan Stanley Interview
- About Morgan Stanley
- Recruitment Process at Flipkart
- Technical Flipkart Interview Questions
- Code-Based Flipkart Interview Questions
- Sample Flipkart Interview Questions- HR Round
- Conclusion
- FAQs
- Recruitment Process at Paytm
- Technical Interview Questions for Paytm Interview
- HR Sample Questions for Paytm Interview
- About Paytm
- Most Probable Accenture Interview Questions
- Accenture Technical Interview Questions
- Accenture HR Interview Questions
- Amazon Recruitment Process
- Amazon Interview Rounds
- Common Amazon Interview Questions
- Amazon Interview Questions: Behavioral-based Questions
- Amazon Interview Questions: Leadership Principles
- Company-specific Amazon Interview Questions
- 43 Top Technical/ Coding Amazon Interview Questions
- Juspay Recruitment: Stages and Timeline
- Juspay Interview Questions and Answers
- How to prepare for Juspay interview questions
- Prepare for the Juspay Interview: Stages and Timeline
- Frequently Asked Questions
- Adobe Interview Questions - Technical
- Adobe Interview Questions - HR
- Recruitment Process at Adobe
- About Adobe
- Cisco technical interview questions
- Sample HR interview questions
- The recruitment process at Cisco
- About Cisco
- JP Morgan interview questions (Technical round)
- JP Morgan interview questions HR round)
- Recruitment process at JP Morgan
- About JP Morgan
- Wipro Elite NTH: Selection Process
- Wipro Elite NTH Technical Interview Questions
- Wipro Elite NTH Interview Round- HR Questions
- BYJU's BDA Interview Questions
- BYJU's SDE Interview Questions
- BYJU's HR Round Interview Questions
- A Quick Overview of the KPMG Recruitment Process
- Technical Questions for KPMG Interview
- HR Questions for KPMG Interview
- About KPMG
- DXC Technology Interview Process
- DCX Technical Interview Questions
- Sample HR Questions for DXC Technology
- About DXC Technology
- Recruitment Process at PayPal
- Technical Questions for PayPal Interview
- HR Sample Questions for PayPal Interview
- About PayPal
- Capgemini Recruitment Rounds
- Capgemini Interview Questions: Technical round
- Capgemini Interview Questions: HR round
- Preparation tips
- FAQs
- Technical interview questions for Siemens
- Sample HR questions for Siemens
- The recruitment process at Siemens
- About Siemens
- HCL Technical Interview Questions
- HR Interview Questions
- HCL Technologies Recruitment Process
- List of EPAM Interview Questions for Technical Interviews
- About EPAM
- Atlassian Interview Process
- Top Skills for Different Roles at Atlassian
- Atlassian Interview Questions: Technical Knowledge
- Atlassian Interview Questions: Behavioral Skills
- Atlassian Interview Questions: Tips for Effective Preparation
- Walmart Recruitment Process
- Walmart Interview Questions and Sample Answers (HR Round)
- Walmart Interview Questions and Sample Answers (Technical Round)
- Tips for Interviewing at Walmart and Interview Preparation Tips
- Frequently Asked Questions
- Uber Interview Questions For Engineering Profiles: Coding
- Technical Uber Interview Questions: Theoretical
- Uber Interview Question: HR Round
- Uber Recruitment Procedure
- About Uber Technologies Ltd.
- Intel Technical Interview Questions
- Computer Architecture Intel Interview Questions
- Intel DFT Interview Questions
- Intel Interview Questions for Verification Engineer Role
- Recruitment Process Overview
- Important Accenture HR Interview Questions
- Points to remember
- What is Selenium?
- What are the components of the Selenium suite?
- Why is it important to use Selenium?
- What's the major difference between Selenium 3.0 & Selenium 2.0?
- What is Automation testing and what are its benefits?
- What are the benefits of Selenium as an Automation Tool?
- What are the drawbacks to using Selenium for testing?
- Why should Selenium not be used as a web application or system testing tool?
- Is it possible to use selenium to launch web browsers?
- What does Selenese mean?
- What does it mean to be a locator?
- Identify the main difference between "assert", and "verify" commands within Selenium
- What does an exception test in Selenium mean?
- What does XPath mean in Selenium? Describe XPath Absolute & XPath Relation
- What is the difference in Xpath between "//"? and "/"?
- What is the difference between "type" and the "typeAndWait" commands within Selenium?
- Distinguish between findElement() & findElements() in context of Selenium
- How long will Selenium wait before a website is loaded fully?
- What is the difference between the driver.close() and driver.quit() commands in Selenium?
- Describe the different navigation commands that Selenium supports
- What is Selenium's approach to the same-origin policy?
- Explain the difference between findElement() in Selenium and findElements()
- Explain the pause function in SeleniumIDE
- Explain the differences between different frameworks and how they are connected to Selenium's Robot Framework
- What are your thoughts on the Page Object Model within the context of Selenium
- What are your thoughts on Jenkins?
- What are the parameters that selenium commands come with a minimum?
- How can you tell the differences in the Absolute pathway as well as Relative Path?
- What's the distinction in Assert or Verify declarations within Selenium?
- What are the points of verification that are in Selenium?
- Define Implicit wait, Explicit wait, and Fluent
- Can Selenium manage windows-based pop-ups?
- What's the definition of an Object Repository?
- What is the main difference between obtainwindowhandle() as well as the getwindowhandles ()?
- What are the various types of Annotations that are used in Selenium?
- What is the main difference in the setsSpeed() or sleep() methods?
- What is the way to retrieve the alert message?
- How do you determine the exact location of an element on the web?
- Why do we use Selenium RC?
- What are the benefits or advantages of Selenium RC?
- Do you have a list of the technical limitations when making use of Selenium RC? Selenium RC?
- What's the reason to utilize the TestNG together with Selenium?
- What Language do you prefer to use to build test case sets in Selenium?
- What are Start and Breakpoints?
- What is the purpose of this capability relevant in relation to Selenium?
- When do you use AutoIT?
- Do you have a reason why you require Session management in Selenium?
- Are you able to automatize CAPTCHA?
- How can we launch various browsers on Selenium?
- Why should you select Selenium rather than QTP (Quick Test Professional)?
- Airbus Interview Questions and Answers: HR/ Behavioral
- Industry/ Company-Specific Airbus Interview Questions
- Airbus Interview Questions and Answers: Aptitude
- Airbus Software Engineer Interview Questions and Answers: Technical
- Importance of Spring Framework
- Spring Interview Questions (Basic)
- Advanced Spring Interview Questions
- C++ Interview Questions and Answers: The Basics
- C++ Interview Questions: Intermediate
- C++ Interview Questions And Answers With Code Examples
- C++ Interview Questions and Answers: Advanced
- Test Your Skills: Quiz Time
- MBA Interview Questions: B.Com Economics
- B.Com Marketing
- B.Com Finance
- B.Com Accounting and Finance
- Business Studies
- Chartered Accountant
- Q1. Please tell us something about yourself/ Introduce yourself to us.
- Q2. Describe yourself in one word.
- Q3. Tell us about your strengths and weaknesses.
- Q4. Why did you apply for this job/ What attracted you to this role?
- Q5. What are your hobbies?
- Q6. Where do you see yourself in five years OR What are your long-term goals?
- Q7. Why do you want to work with this company?
- Q8. Tell us what you know about our organization
- Q9. Do you have any idea about our biggest competitors?
- Q10. What motivates you to do a good job?
- Q11. What is an ideal job for you?
- Q12. What is the difference between a group and a team?
- Q13. Are you a team player/ Do you like to work in teams?
- Q14. Are you good at handling pressure/ deadlines?
- Q15. When can you start?
- Q16. How flexible are you regarding overtime?
- Q17. Are you willing to relocate for work?
- Q18. Why do you think you are the right candidate for this job?
- Q19. How can you be an asset to the organization?
- Q20. What is your salary expectation?
- Q21. How long do you plan to remain with this company?
- Q22. What is your objective in life?
- Q23. Would you like to pursue your Master's degree anytime soon?
- Q24. How have you planned to achieve your career goal?
- Q25. Can you tell us about your biggest achievement in life?
- Q26. What was the most challenging decision you ever made?
- Q27. What kind of work environment do you prefer to work in?
- Q28. What is the difference between a smart worker and a hard worker?
- Q29. What will you do if you don't get hired?
- Q30. Tell us three things that are most important for you in a job.
- Q31. Who is your role model and what have you learned from him/her?
- Q32. In case of a disagreement, how do you handle the situation?
- Q33. What is the difference between confidence and overconfidence?
- Q34. If you have more than enough money in hand right now, would you still want to work?
- Q35. Do you have any questions for us?
- Interview Tips for Freshers
- Tell me about yourself
- What are your greatest strengths?
- What are your greatest weaknesses?
- Tell me about something you did that you now feel a little ashamed of
- Why are you leaving (or did you leave) this position??
- 15+ resources for preparing most-asked interview questions
- CoCubes Interview Process Overview
- Common CoCubes Interview Questions
- Key Areas to Focus on for CoCubes Interview Preparation
- Conclusion
- Frequently Asked Questions (FAQs)
- Data Analyst Interview Questions With Answers
- About Data Analyst
50+ Cisco Interview Questions With Detailed Answers (2026 Updated)
Cisco is among the top tech companies with a number of branches across the globe. If you are planning to prepare for the Cisco interview, then you must check out the well-curated list of basic technical questions with answers below for all freshers and experienced candidates.
List of Cisco technical interview questions
To help you get an insight into the technical interview round, here is a list of technical questions for the Cisco Interview that you must know before appearing for D-Day:
1. What do you know about network failure?
Network failure refers to the situation where a computer network, which includes a range of hardware products such as routers, switches, and servers, as well as software components like protocols and applications, experiences a communication breakdown. Network failure can result in a range of issues, from minor delays and performance degradation to complete loss of software connectivity.
There are several causes of network failure, including hardware failures, software bugs, security breaches, power outages, and natural disasters. Some of the common symptoms of network failure include slow response times, inability to connect to network resources, dropped connections, and network outages.
2. What are the types of destination addresses?

In networking, there are two types of destination addresses: MAC addresses and IP addresses.
-
MAC addresses: Media Access Control (MAC) addresses are unique identifiers assigned to every network interface controller (NIC) in a device. A MAC address is a 48-bit number and is used at the data link layer (Layer 2) of the OSI model to identify a specific device on a network. MAC addresses are used in local area networks (LANs) and are used to deliver data packets within the same LAN.
-
IP addresses: Internet Protocol (IP) addresses are unique identifiers assigned to every device on a network. IP addresses are 32-bit or 128-bit numbers and are used at the network layer (Layer 3) of the OSI model to route data between different networks. IP addresses are used in wide area networks (WANs) and the internet and are used to deliver data packets between different networks.
3. What are the three types of memory?
In computing, there are three types of memory:
-
Random Access Memory (RAM): RAM is a type of volatile memory that temporarily stores data and instructions that the CPU needs to access quickly. The data in RAM is lost when the computer is turned off or restarted. RAM is used to run applications and software on a computer.
-
Read-Only Memory (ROM): ROM is a type of non-volatile memory that contains firmware or system software that cannot be altered or modified. It is used to store the BIOS (Basic Input/Output System) and other critical boot-up programs that are required to start up a computer.
-
Secondary Storage: Secondary storage refers to non-volatile storage devices like hard disk drives (HDDs), solid-state drives (SSDs), and external storage devices that store data and programs for long-term use. Unlike RAM, data in secondary storage is not lost when the computer is turned off.
4. What do you understand about a network device?
A network device is a hardware device that is used to enable communication and data transfer between different devices on a computer network. Network devices are used to connect, manage, and secure networks, and they play a critical role in ensuring that data is transmitted efficiently and securely.
Some common types of network devices include:
-
Routers: Routers are used to connect different networks and to direct data traffic between them.
-
Switches: Switches are used to connect multiple devices on a network, allowing them to communicate with each other.
-
Hubs: Hubs are used to connect multiple devices on a network and to broadcast data to all devices on the network.
-
Firewalls: Firewalls are used to protect networks from unauthorized access by filtering out unwanted traffic.
-
Modems: Modems are used to convert digital signals into analog signals, allowing data to be transmitted over telephone lines.
-
Access Points: Access Points are used to enable wireless devices to connect to a wired network.
5. What is a single network?
A single network, also known as a standalone network, is a computer network that exists independently and is not connected to any other network. In a single network, all devices are connected to the same local network and can communicate with each other without the need for a router or other network device to facilitate communication between different networks.
Single networks are typically used in small businesses or homes, where it is sufficient to meet the communication needs of the users. For example, a standalone network can be set up in a small office with several desktop computers and printers connected to a single router or switch, which allows them to communicate with each other and share resources like files and printers.
6. What is meant by network congestion?
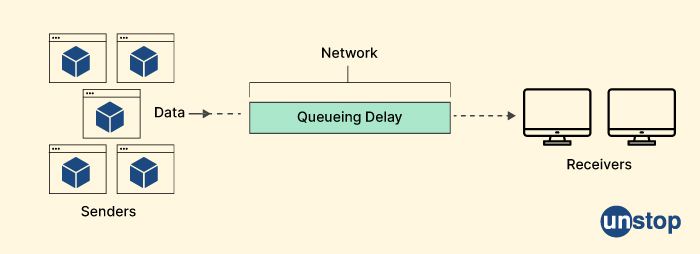
Network congestion occurs when there is too much data traffic on a computer network, resulting in slow response times and degraded network performance. It can occur at any point in the network where data traffic converges, such as routers, switches, or network links.
When network congestion occurs, data packets are delayed or dropped, which can result in slow file transfers, video buffering, or dropped calls in voice or video communications. Network congestion can be caused by a variety of factors, including:
-
Too many devices on the network: When there are too many devices on a network, the available bandwidth can become saturated, resulting in network congestion.
-
Large file transfers: When large files are being transferred over the network, they can consume a large amount of bandwidth, leading to congestion.
-
Peak usage times: During periods of peak network usage, such as when many users are streaming video or downloading files, network congestion can occur.
-
Network equipment failure: When network equipment, such as routers or switches, fail or become overloaded, network congestion can occur.
To prevent network congestion, network administrators can use various techniques such as traffic shaping, load balancing, and Quality of Service (QoS) to prioritize traffic and manage network traffic flow. It is also important to have an adequate amount of bandwidth and to regularly monitor the network for congestion issues to prevent them from occurring.
7. Do you know networking concepts?
Networking concepts refer to the fundamental principles and components that make up a computer network. These concepts are essential to understand when building, maintaining, or troubleshooting computer networks. Some of the key networking concepts include:
-
Network Topology: Network topology refers to the physical or logical layout of a network. Common network topologies include bus, ring, star, mesh, and hybrid topologies.
-
Network Protocols: Network protocols are sets of rules and standards that govern how data is transmitted over a network. Examples of network protocols include TCP/IP, HTTP, FTP, and SMTP.
-
IP Addressing: IP addressing is a system used to identify devices on a network. IP addresses are unique numerical identifiers assigned to each device on the network.
-
Routing: Routing refers to the process of directing data packets from one network to another. Routers are used to perform this function.
-
Switching: Switching refers to the process of directing data packets within a network. Switches are used to perform this function.
-
Network Security: Network security refers to the measures taken to protect a network from unauthorized access, attacks, and other security threats. Network security measures may include transparent firewalls, intrusion detection and prevention systems, and encryption.
-
Network Management: Network management refers to the processes and tools used to monitor, configure, and troubleshoot a network. Network management tools may include network monitoring software, configuration management tools, and diagnostic tools.
8. What are the 4 types of IP addresses?
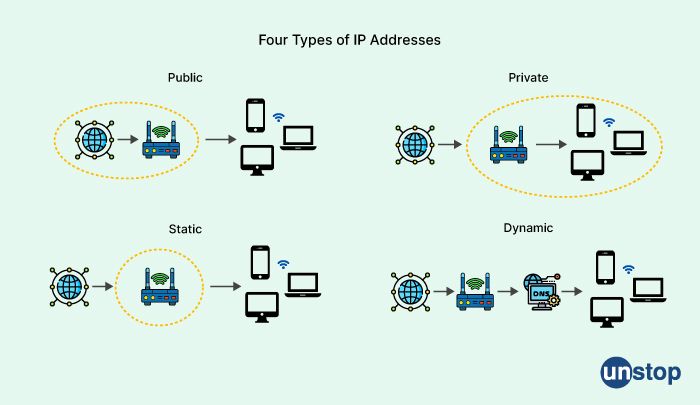
The four types of IP addresses:
-
Public IP addresses: Public IP addresses are unique addresses that are assigned to devices on the internet. They are used to identify devices on the internet and allow them to communicate with other devices on the internet. Public IP addresses are assigned by Internet Service Providers (ISPs) and are typically used by servers, routers, and other networking devices.
-
Private IP addresses: Private IP addresses are used within a private network to identify devices and allow them to communicate with each other. Private IP addresses are not unique and can be reused within different networks. Private IP addresses are assigned by the network administrator and are typically used by computers, printers, and other devices on a local network.
-
Static IP addresses: A static IP address is an IP address that is assigned to a device and does not change. Static IP addresses are commonly used for servers, routers, and other networking devices that require a consistent IP address for remote access and management.
-
Dynamic IP addresses: A dynamic IP address is an IP address that is assigned to a device by a DHCP (Dynamic Host Configuration Protocol) server. Dynamic IP addresses can change periodically and are typically used by client devices such as computers and smartphones.
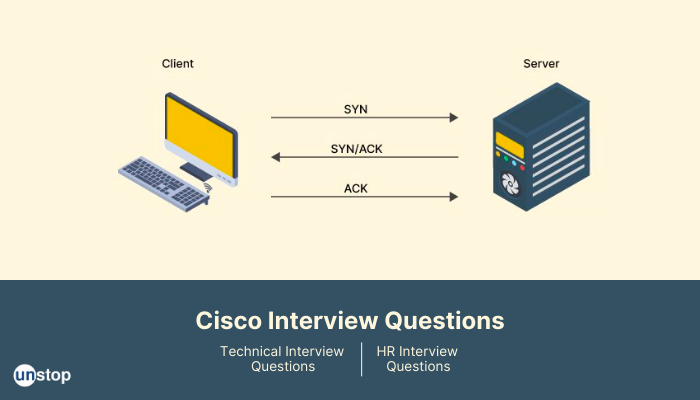
9. What is connection establishment in TCP?
In TCP (Transmission Control Protocol), connection establishment refers to the process of establishing a reliable connection between two devices on a network before data transfer can begin. The connection establishment process involves a three-way handshake, which is a series of messages exchanged between the devices to establish and synchronize the connection.
The three-way handshake works as follows:
-
The initiating device sends an SYN (synchronize) packet to the receiving device to request a connection.
-
The receiving device responds with an SYN-ACK (synchronize-acknowledgment) packet to acknowledge the request and indicate that it is willing to establish a connection.
-
The initiating device responds with an ACK (acknowledgment) packet to confirm the connection has been established.
Once the three-way handshake is complete, the devices are synchronized, and data transfer can begin. TCP ensures reliable data transfer by using mechanisms such as flow control, error detection, and retransmission of lost packets.
10. What is the importance of a networked server?
A networked server is a computer system that provides services to other devices on a network. The importance of a networked server can be summarized as follows:
-
Centralized management: A networked server can centralize the management of resources, applications, and data. This makes it easier for network administrators to manage and maintain the network, as they can control access, backups, updates, and security policies from a central location.
-
Resource sharing: A networked server can allow multiple devices to share resources, such as printers, storage, and applications. This can increase efficiency and reduce costs by avoiding the need for each device to have its resources.
-
Improved collaboration: A networked server can facilitate collaboration by allowing multiple users to access the same data and applications simultaneously. This can improve productivity, as users can work together in real-time, share ideas, and exchange feedback.
-
Increased security: A networked server can improve network security by centralizing access control, authentication, and data encryption. This can help prevent unauthorized access, data breaches, and malware attacks.
-
Scalability: A networked server can provide a scalable solution to meet the growing demands of a network. As the number of users and devices on the network increases, the server can be upgraded or expanded to accommodate the growth.
11. What are software testing techniques?
Software testing techniques are methods or approaches used to ensure that software applications or systems are functioning as expected and meet the desired requirements. There are several types of software testing techniques, including:
-
Black-box testing: Black-box testing is a testing technique that focuses on the functionality of the software application or system, without considering its internal code. Testers typically use inputs and expected outputs to verify that the software performs as intended.
-
White-box testing: White-box testing is a testing technique that focuses on the internal code of the software application or system. Testers typically use code analysis and debugging tools to verify that the software performs as intended.
-
Gray-box testing: Gray-box testing is a testing technique that combines elements of both black-box and white-box testing. Testers typically have some knowledge of the internal code but focus primarily on the functionality of the software.
- Functional testing: It is focused on verifying that the software application or system is working according to its intended functionality. The goal is to test if the software does what it is supposed to do, and that it meets the requirements specified in the design documents or user stories.
- Non-Functional testing: It is focused on verifying the performance, reliability, usability, and other quality attributes of the software application or system. The goal is to test how well the software works, and how it performs under different conditions.
12. What are the three programming languages?
The three popular programming languages:
-
Java: Java is a popular programming language that is designed to be platform-independent, meaning that it can run on multiple platforms and operating systems. It is commonly used for developing enterprise-level applications, web applications, and Android mobile applications.
-
Python: Python is a high-level programming language that emphasizes code readability and simplicity. It is widely used in scientific computing, data analysis, artificial intelligence, machine learning, and web development.
-
C++: C++ is an object-oriented programming language that is used for developing high-performance applications, such as video games, operating systems, and embedded systems. It is a popular choice for systems programming and is widely used in the development of large-scale software systems.
13. What is error detection in the operating systems?
Error detection is the process of identifying errors or anomalies in an operating system (OS) or the software that runs on it. An operating system can detect errors in various ways, including:
-
Memory error detection: An operating system can detect memory errors such as page faults, segmentation faults, or other memory-related errors that occur when a program attempts to access an invalid memory address.
-
System call error detection: System calls are used by programs to request services from the operating system. An OS can detect system call errors by checking for the return value of the system call and identifying any error codes.
-
File system error detection: An operating system can detect errors in the file system by checking for inconsistencies, such as missing or corrupted files or directories.
-
Network error detection: An operating system can detect errors in network communication by monitoring network traffic and detecting errors such as dropped packets or network congestion.
-
Hardware error detection: An operating system can detect hardware errors such as disk failures, network card failures, or other hardware-related errors by monitoring system logs and error messages.
14. How do you know if your hardware crashes?
Hardware crashes can be caused by a wide range of factors such as software conflicts, driver issues, overheating, power supply problems, and physical damage. Here are some common signs that your setup of hardware may have crashed:
-
Blue Screen of Death (BSOD): If your computer screen turns blue and displays an error message, it may be an indication of a hardware crash. The BSOD occurs when the operating system encounters a critical error that it cannot recover from.
-
Freezing or Locking up: If your computer freezes or locks up frequently, it may be an indication of a hardware issue. This can be caused by overheating, faulty memory, or a failing hard drive.
-
Strange Noises: If you hear strange noises coming from your computer, such as clicking, grinding, or whirring sounds, it may be an indication of a failing hard drive, fan, or other hardware components.
-
Error Messages: If you receive error messages when you try to access files or programs, it may be an indication of a hardware issue. Error messages can occur due to faulty RAM, hard drive failure, or other hardware-related issues.
-
System Not Booting: If your system does not boot up or start properly, it may be an indication of a hardware failure. This can be caused by a failing power supply, hard drive failure, or other hardware issues.
If you suspect that your hardware has crashed, it is important to take immediate action to diagnose and resolve the issue. Contacting a computer technician or IT professional can help you identify the cause of the problem and take steps to repair or replace the faulty hardware.
One click. Endless opportunities. Land your dream job today!
15. What is an application layer? What are its types?
The application layer is the topmost layer in the OSI model, which is responsible for providing network services and applications to end-users. It is responsible for supporting communication between software applications running on different networked devices. There are several types of application layer protocols, including:
-
Hypertext Transfer Protocol (HTTP): HTTP is a protocol used for transmitting data over the World Wide Web. It is the primary protocol used for transmitting web pages, multimedia content, and other resources.
-
Simple Mail Transfer Protocol (SMTP): SMTP is a protocol used for sending and receiving email messages over the internet. It is used by email clients to send messages to email servers, which then route the messages to their destination.
-
File Transfer Protocol (FTP): FTP is a protocol used for transferring files between computers over a network. It is commonly used for uploading and downloading files to and from a web server.
-
Domain Name System (DNS): DNS is a protocol used for converting domain names into IP addresses. It is responsible for translating human-readable domain names into machine-readable IP addresses that can be used to route network traffic.
-
Simple Network Management Protocol (SNMP): SNMP is a protocol used for managing and monitoring network devices, such as routers, switches, and servers. It allows network administrators to monitor network performance and troubleshoot network issues.
Overall, the application layer protocols play a critical role in facilitating communication between software applications and networked devices. They provide a standardized way for applications to communicate over a network and enable users to access a wide range of network services and applications.
16. What does the media access control address do?
The Media Access Control (MAC) address is a unique identifier assigned to network interface controllers (NICs) for use as a network address in communications within a network segment. Basically, the MAC address is a hardware address that is embedded into the NIC by the manufacturer and cannot be changed.
It is used to identify a device on a network. When a device wants to communicate with another device on the same network, it uses the MAC address of the destination device to send the data directly to that device. The MAC address is used at the data link layer of the OSI model, which is responsible for transmitting data over a physical network.
In addition to being used for communication within a network segment, the MAC address is also used for security purposes. Network administrators can use MAC address filtering to allow or block access to the network based on the MAC address of the device trying to connect. This can be useful for restricting access to specific devices on the network, such as printers or servers.
17. What is included in the MAC address table?
A MAC address table, also known as a content-addressable memory (CAM) table or forwarding database, is a database used by network switches to keep track of the MAC addresses of devices on a network. The MAC address table contains the following information:
-
MAC Address: This is the unique hardware address of the device.
-
Interface: This is the port on the switch where the device is connected.
-
Aging Time: This is the amount of time a MAC address is kept in the table before it is removed.
-
VLAN ID: This is the VLAN (Virtual Local Area Network) to which the device belongs.
The MAC address table is used by the switch to forward network traffic to the appropriate destination. When a switch receives a frame, it checks the MAC address table to see if it knows the destination MAC address.
18. What is an address positioning table in networking?
ARP positioning, also recognized as ARP Spoofing, is a form of cyber attack that is carried out over a Local Area Network (LAN). This type of cyber attack means sending malicious ARP packets to a default gateway on a LAN. This is done as an attempt to transform the pairings inside the default gateway's IP to the MAC address table. ARP Poisoning is understood as ARP Spoofing. The ARP Protocol is responsible for translating MAC addresses into IP addresses.
19. List some advantages of IP access control.
IP (Internet Protocol) access control is a security mechanism used to restrict access to network resources based on the IP address of the client device. Some of the advantages of IP access control include:
-
Improved security: By limiting access to network resources based on IP addresses, IP access control can help prevent unauthorized access, hacking attempts, and other security threats.
-
Simplified management: IP access control can be easier to manage than other security mechanisms, such as user-based access control because it doesn't require individual user accounts or passwords.
-
Granular control: IP access control can be used to provide granular control over network resources by allowing or denying access based on the IP address of the client device.
-
Flexibility: IP access control can be used to restrict access to specific areas of a network or specific types of resources, providing greater flexibility in managing network security.
-
Scalability: IP access control can be easily scaled up or down as network requirements change, making it a flexible and adaptable security mechanism.
-
Cost-effective: IP access control can be a cost-effective security solution because it doesn't require additional hardware or software, and it can be implemented using existing network infrastructure.
20. What is an authentication server?
An authentication server is a type of server that is responsible for verifying the identity of users or devices that are trying to access network resources. It typically works by comparing a set of login credentials provided by the user or device against a database of authorized users or devices, and granting or denying access based on the results of the authentication process.
Authentication servers are commonly used in enterprise networks to control access to sensitive resources, such as corporate databases or file servers. They can support a variety of authentication protocols, including the popular RADIUS (Remote Authentication Dial-In User Service) and LDAP (Lightweight Directory Access Protocol) protocols.
Some of the key benefits of using an authentication server include improved security, centralized management of user accounts and access permissions, and simplified access control policies. By requiring users to authenticate themselves before gaining access to network resources, authentication servers can help prevent unauthorized access, reduce the risk of data breaches, and ensure compliance with security policies and regulations.
21. What is meant by the active link in HTML?
In HTML, the term "active link" refers to a hyperlink that is currently being clicked or activated by the user.
When a user clicks on a hyperlink in a web page, the link becomes an active link, and the destination page or resource begins to load in the browser window. The active link is usually highlighted or visually differentiated from other links on the page, to indicate to the user that it is currently being clicked.
The appearance of an active link can be controlled using CSS (Cascading Style Sheets) properties, such as color, font, and background. By modifying the styles of active links, web designers can create a more interactive and engaging user experience, and provide visual feedback to users as they navigate through the site.
22. What is a backup path?
In networking, a backup path is a secondary route that can be used to transmit data packets if the primary route is unavailable or congested.
Backup paths are typically configured in routing protocols or network devices, such as routers or switches, and are designed to provide network redundancy and ensure that data can continue to flow even in the event of a network failure or outage.
There are several types of backup paths that can be used in networking challenge, including:
-
Redundant links: Multiple physical links between network devices can be configured as backup paths, so that if one link fails, traffic can automatically be rerouted over the remaining links.
-
Alternate routes: In some routing protocols, such as OSPF (Open Shortest Path First), a range of alternative routes to a destination network can be calculated and stored in a routing table, so that if the primary route fails, an alternate route can be used instead.
-
Load balancing: Some network devices can be configured to distribute traffic over multiple paths, providing both redundancy and increased network capacity.
23. What is the purpose of SYN and ACK flags?
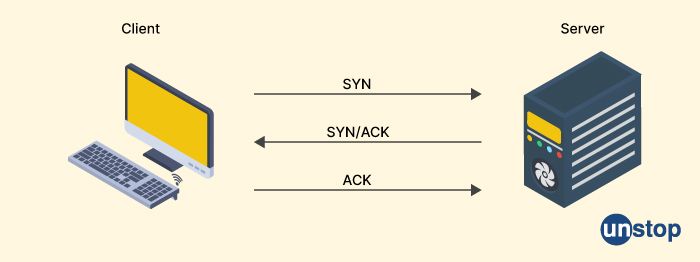
The SYN and ACK flags are two types of control flags used in the TCP (Transmission Control Protocol) protocol. They play a crucial role in the establishment and termination of TCP connections between network devices.
The SYN flag (short for "synchronize") is used to initiate a TCP connection between two devices. When a device wants to establish a connection with another device, it sends an SYN packet to the destination device, which contains a random sequence number that is used to synchronize the sequence numbers between the two devices. The SYN flag is set to 1 in the TCP header to indicate that the packet is an SYN packet.
The ACK flag (short for "acknowledge") is used to acknowledge the receipt of data or confirm the status of a connection. When a device receives an SYN packet from another device, it sends back an ACK packet that acknowledges the receipt of the SYN packet and contains a sequence number that is one higher than the received sequence number. The ACK flag is set to 1 in the TCP header to indicate that the packet is an ACK packet.
During the establishment of a TCP connection, a series of SYN and ACK packets are exchanged between the two devices until a connection is established. The SYN-ACK sequence is used to establish the connection, while the ACK flag is used to confirm that the connection has been established.
24. A node is a component of a network. True or false?
True. A point or junction in a network that allows for the formation of connections is referred to as a node. It may be a computer, or it might be a gadget, but it will always be connected to a network. To establish a link between two or more networks, a network has to have at least two nodes.
25. What is the use of routers?
Routers are networking devices that are used to connect multiple networks together and allow devices on those networks to communicate with each other. They are used to forward data packets between different networks, using a routing algorithm to determine the best path for each packet based on the destination address in the packet header.
Routers perform several functions, including:
-
Forwarding packets: Routers are responsible for forwarding data IP packets between different networks, using a routing table that maps the destination addresses of packets to the appropriate network interface.
-
Network segmentation: Routers can be used to segment a large network into smaller sub-networks, which can help to improve network performance and the lowest security level by reducing the amount of broadcast traffic on the network.
-
Network address translation (NAT): Routers can be used to perform NAT, which allows multiple devices on a private network to share a single public IP address when communicating with the Internet.
-
Firewalling: Routers can be used to implement transparent firewall rules, which can help to filter and block unwanted traffic between different networks.
26. What does it mean to have a connection that goes from point to point?
A connection that goes from point to point is a dedicated communication link between two specific devices or locations. It is also referred to as a point-to-point connection or a leased line.
In a point-to-point connection, data travels directly between the two endpoints without passing through any intermediate devices or nodes. This type of connection can be either physical, such as a dedicated cable or a wireless link, or virtual, such as a VPN connection.
Point-to-point connections offer several advantages, including:
-
Security: Since data is transmitted directly between two endpoints, it is less vulnerable to interception or eavesdropping by third parties hence ensuring the security levels of the network.
-
Reliability: Point-to-point connections are typically more reliable than shared connections, since they are not affected by network congestion or other issues that can impact shared connections.
-
Performance: Point-to-point connections can provide higher performance than shared connections, since they offer dedicated bandwidth and are not affected by other traffic on the network.
-
Control: Point-to-point connections allow for more control over the communication link, since the link can be configured and managed specifically for the needs of the two endpoints.
27. What is meant by the phrase "anonymous FTP"?
Anonymous FTP refers to a type of File Transfer Protocol (FTP) service that allows users to connect to an FTP server and access its files without providing a username or password. Instead, users are granted anonymous access to the server by using a default username, such as "anonymous" or "ftp", and providing their email address as the password.
Anonymous FTP is often used by organizations or individuals who want to share files publicly without requiring users to have a specific account or login credentials. For example, software vendors may use anonymous FTP to distribute software updates or patches to their customers, or universities may use it to share research data or other resources with the public.
While anonymous FTP can be a convenient way to share files, it also presents some security risks, since it allows anyone to access the files on the server without any authentication. To mitigate these risks, many anonymous FTP servers are configured to limit access to certain files or directories, or to impose download limits or other restrictions on anonymous users.
28. What does the term subnet mask refer to?
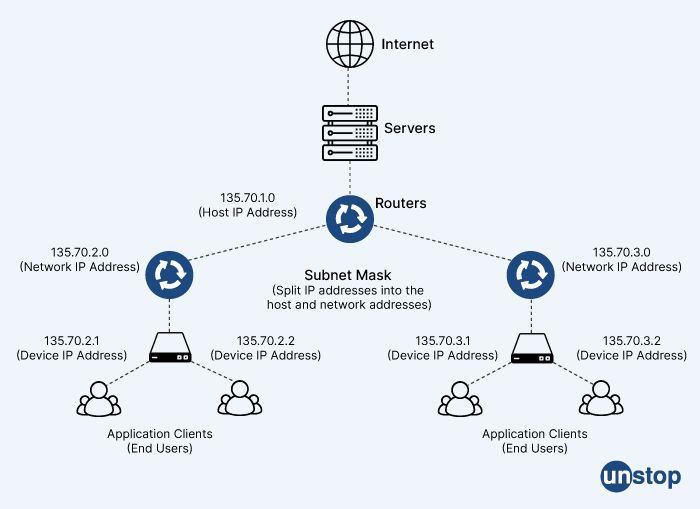
In computer networking, a subnet mask is a 32-bit number that is used to divide an IP address into network and host portions. It is used in conjunction with the IP address to determine the network address and host address of a device on a network.
The subnet mask is represented as four sets of numbers separated by periods, each set consisting of eight bits. For example, a subnet mask of 255.255.255.0 means that the first 24 bits of the IP address represent the network address, and the last 8 bits represent the host address.
Subnet masks are used in conjunction with IP addresses to determine whether two devices are on the same network or on different networks. If two devices have the same network portion of their IP addresses and subnet masks, they are on the same network and can communicate directly with each other. If they have different network portions, they are on different networks and communication between them requires routing through a router or gateway.
29. What is the longest length of a cable that uses the UTP protocol?
The maximum length of a cable that uses Unshielded Twisted Pair (UTP) protocol depends on the category of the cable and the transmission speed.
For Category 5 (Cat5) UTP cable, which is commonly used for Ethernet networks, the maximum length is 100 meters (328 feet) when transmitting at speeds up to 100 megabits per second (Mbps). For Category 6 (Cat6) UTP cable, which supports faster transmission speeds up to 10 gigabits per second (Gbps), the maximum length is also 100 meters.
It's worth noting that the maximum cable length can be affected by a variety of factors, such as electromagnetic interference (EMI), cable quality, and the number of connectors and splices in the cable. In some cases, it may be necessary to use signal repeaters or switches to extend the effective length of the cable.
30. What does encapsulating data into a container mean?
In networking, encapsulation refers to the process of adding a header and sometimes a trailer to a piece of data (such as a packet or frame) in order to transmit it over a network. The header and trailer provide information such as the source and destination addresses, error detection codes, and protocol information.
Encapsulation can be thought of as wrapping the data inside a container, with the header and trailer forming the walls and lid of the container. This container allows the data to be transmitted over the network and delivered to the intended destination.
For example, in the TCP/IP protocol suite, data is encapsulated in a series of layers, with each layer adding its own header and possibly trailer to the data. The layers are often referred to as the OSI (Open Systems Interconnection) model, and include the application layer, transport layer, network layer, data link layer, and physical layer. Each layer is responsible for a different aspect of data transmission, such as addressing, routing, and error detection and correction.
31. Explain the topology of the network.
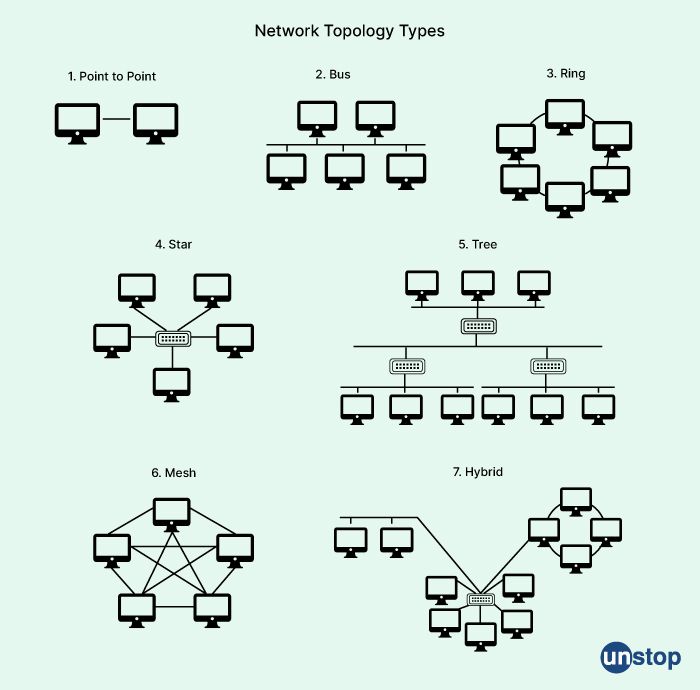
In networking, the term "topology" refers to the physical or logical arrangement of devices and connections in a network. It describes how devices are interconnected and how data flows between them.
There are several different types of network topologies, each with its own advantages and disadvantages:
-
Bus topology: In a bus topology, all devices are connected to a single cable or "bus". Data is transmitted along the bus and all devices receive the data, but only the intended recipient processes the data. A break in the cable can disrupt the entire network.
-
Star topology: In a star topology, all devices are connected to a central hub or switch. Data is transmitted from one device to the hub, and then the hub sends the data to the intended recipient. The hub provides a central point for managing the network, but if the hub fails, the entire network may be affected.
-
Ring topology: In a ring topology, devices are connected in a circular chain. Data is transmitted from one device to the next until it reaches the intended recipient. A break in the chain can disrupt the entire network.
-
Mesh topology: In a mesh topology, each device is connected to every other device in the network. Data can take multiple paths to reach its destination, providing redundancy and fault tolerance. However, this type of topology can be expensive to implement.
-
Tree topology: In a tree topology, devices are arranged in a hierarchical structure, with multiple levels of branching. Data is transmitted up and down the tree until it reaches the intended recipient. This topology can be scalable and fault-tolerant, but it can be complex to manage.
32. What is a VPN?
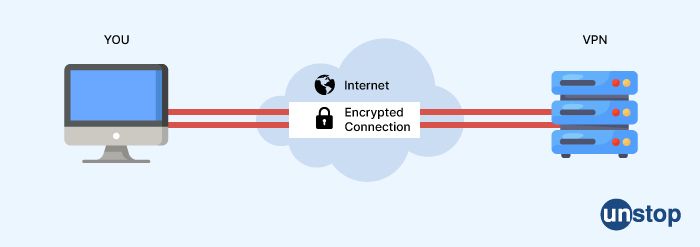
VPN stands for Virtual Private Network. It is a technology that allows users to securely access a private network over the internet.
When you connect to a VPN, your device creates an encrypted tunnel through which all data traffic is routed. This ensures that any data sent or received over the internet is secure and protected from interception or unauthorized access.
VPNs are commonly used by individuals who want to access restricted content or bypass internet censorship, as well as by businesses and organizations to allow remote workers to securely access the company network.
VPNs can be configured to use different protocols, encryption standards, and authentication methods depending on the security levels required and the specific needs of the user or organization.
33. Provide an explanation of NAT in a nutshell.
NAT, or Network Address Translation, is a technique used to enable devices on a private network to access the internet using a single public IP address.
When a device on a private network sends a request to the internet, NAT modifies the source IP address of the request to the public IP address of the router or gateway that connects the private network to the internet. When the response is sent back from the internet, NAT translates the public IP address back to the original private IP address of the device that made the request.
This allows multiple devices on a private network to share a single public IP address, which is useful in conserving limited public IP addresses and protecting the private network from direct exposure to the internet.
NAT can be implemented in different ways, such as Static NAT, Dynamic NAT, and Port Address Translation (PAT), each with their own advantages and limitations depending on the specific requirements of the network.
34. Describe Open Systems Interconnect (OSI) and the role it plays in computer networks.
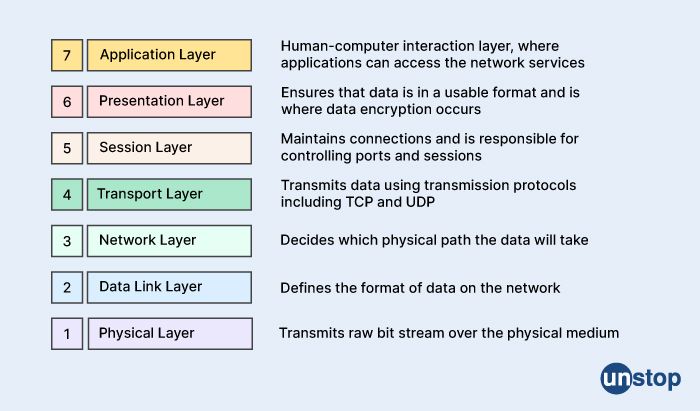
The Open Systems Interconnect (OSI) model is a conceptual model for computer networks that describes a set of layers and protocols that govern the communication between different devices on a network. The model consists of seven layers, each of which has a specific function and interacts with the layers above and below it.
The seven layers of the OSI model are:
-
Physical layer - This layer deals with the physical transmission of data over the network, including the cabling, connectors, and signals.
-
Data link layer - This layer handles the organization and management of data frames, including error detection and correction.
-
Network layer - This layer provides the routing and forwarding of data between different networks, including the determination of the best path to send data between devices.
-
Transport layer - This layer provides end-to-end data delivery and reliability, including flow control, error recovery, and retransmission of lost packets.
-
Session layer - This layer establishes, maintains, and terminates communication sessions between applications running on different devices.
-
Presentation layer - This layer provides a common format for data exchange between different applications and systems, including encryption and compression of data.
-
Application layer - This layer provides the interface between the network and the application programs that use the network, including email, file transfer, and web browsing.
35. What does the term "Bridge" mean in the context of networking?
In the context of networking, a bridge is a device that connects two or more network segments together and allows them to communicate as if they were a single network. Bridges operate at the data link layer (layer 2) of the OSI model and are designed to filter and forward network traffic based on the media access control (MAC) addresses of the devices on the network.
Bridges work by maintaining a table of MAC addresses and the corresponding network segment they are connected to. When a packet arrives at the bridge, the bridge checks the destination MAC address and forwards the packet to the appropriate segment based on the MAC address table. If the MAC address is not found in the table, the bridge will broadcast the packet to all segments, allowing the device with the corresponding MAC address to respond and update the table.
Bridges are commonly used to connect LANs (local area networks) together, as well as to segment a single LAN into smaller, more manageable sub-networks. They can also be used to extend the range of wireless networks by connecting multiple access points together.
36. What is the meaning of ARP in the world of networking?
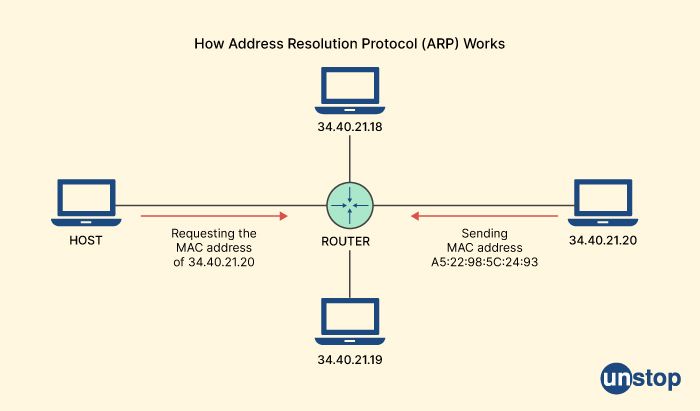
In the world of networking, ARP stands for Address Resolution Protocol. It is a protocol used to map a physical or MAC (Media Access Control) address of a device to its corresponding IP address.
ARP is used by a device to find the MAC address of another device in the same network. When a device wants to send data to another device on the same network, it checks its ARP cache to see if it already has the MAC address of the device. If it does not have the MAC address, it sends an ARP request to the network asking for the MAC address of the device with the specific IP address. The device with the specified IP address responds with its MAC address, and the requesting device can then use this MAC address to send data to the target device.
ARP is a critical protocol for communication between devices on a local network, and it is used by many different networking protocols, including Ethernet and Wi-Fi.
There are four distinct categories of ARPs, which are as follows:
- Proxy ARP
- Gratuitous ARP
- Reverse ARP
- Inverse ARP
37. In terms of networking, what is DNS?
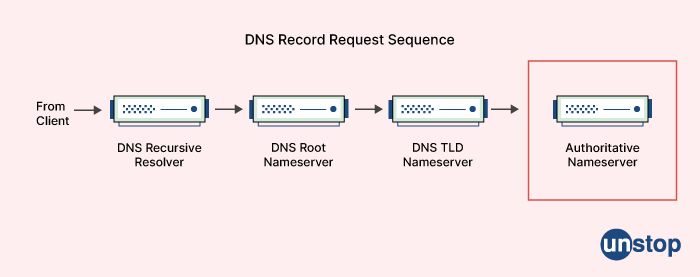
The Domain Name System (DNS) is a host naming system that is hierarchical and may be hooked up to the internet or, indeed, any private wireless network. The method entails transforming the domain names of the entities or hosts that are participating into an IP address or destination address that can be understood by computers.
Since 1985, the Domain Name System (DNS) has been an essential component of the operation of the internet. DNS is something that we use daily without even realizing it when we check our emails or browse the web on our cell phones. Your wireless network provider will set up the DNS server that you use whenever you access the internet. This will happen automatically whenever you log in.
38. In networking, what does "ping" stand for?
In networking, "ping" stands for Packet Internet Groper. It is a utility used to test the connectivity and responsiveness of a network device or host by sending a small packet of data (known as an ICMP echo request) to the target and waiting for a response.
The ping command is widely used in network troubleshooting and is a simple way to determine if a network device, such as a router or server, is reachable and responding to network requests. The command can also be used to measure the round-trip time (RTT) for packets sent between two hosts on a network, which can be useful for detecting network latency or determining the quality of a network connection.
The ping command is available on most operating systems, including Windows, macOS, and Linux, and it is typically accessed from a command prompt or terminal window.
39. In networking, what does the term "socket" refer to?
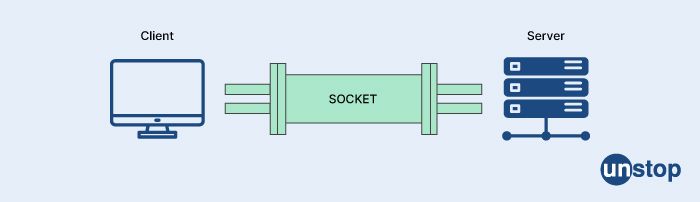
In networking, a socket is a software endpoint that establishes a connection between a computer program and a network protocol. It is an abstraction that allows programs to communicate over a network by providing a standardized interface for sending and receiving data.
A socket is identified by an IP address and a port number, which together create a unique address that can be used to establish a connection between two endpoints on a network. A socket can be thought of as a combination of an IP address and a port number that together form a channel for communication between two devices on a network.
In programming, sockets are typically implemented through a set of system calls that allow programs to create, configure, and manage network connections. Sockets can be used for a variety of network communication protocols, including TCP/IP, UDP, and ICMP.
40. What does the term "Host" mean in networking?
A computer device (also known as a server) that is coupled with other computers and devices that are connected to a network is known as a host. At least one network address, either explicitly specified by an administrator or automatically issued through the use of DHCP, is given to each of the hosts on the network.
A host on a network often functions as a server, providing users or other hosts on the network with access to various services, information resources, software programs, and so on. Every host that takes part in a network that employs an internet protocol suite is given a distinct IP address, and this type of host is referred to as an IP host. The IP host is the entity that is accountable for storing data as well as transferring that data to other computers or devices, which are referred to as remote terminals.
41. What is the NOS?
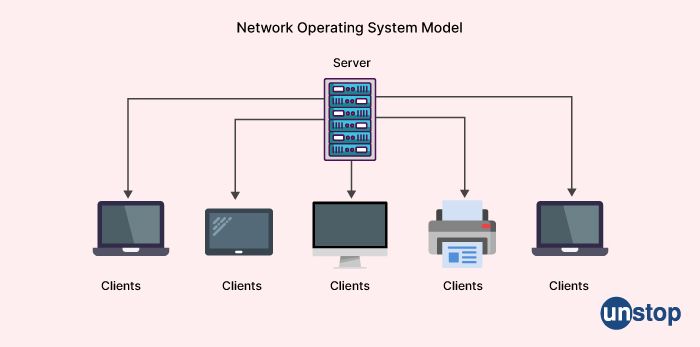
A network operating system (NOS) is a type of operating system that is designed to support and manage computer networks. It provides the necessary software infrastructure for managing network resources, such as file servers, printers, and other devices, and it enables multiple users to access these resources simultaneously.
A network operating system typically includes a range of features that are specifically designed for network management, such as directory services, network security, and remote access. It may also include features for managing user accounts and authentication, data backup and recovery, and system monitoring and reporting.
Examples of network operating systems include Microsoft Windows Server, Linux-based systems like Ubuntu Server and Red Hat Enterprise Linux, and Novell NetWare. These systems are used by organizations of all sizes to manage their network resources and ensure reliable and secure network operations.
42. What does DoS mean?
DoS stands for "Denial of Service". In the context of computer networks, a DoS attack is an attempt to make a resource unavailable to its intended users. This is typically done by flooding the targeted resource, such as a web server, with a large volume of traffic or requests. The goal of a DoS attack is to overwhelm the targeted system's resources, making it unable to respond to legitimate requests. DoS attacks can cause significant disruption to network services and can be used as a means of extortion or as a diversionary tactic to cover other malicious activities.
43. In the context of networking, what is subnetting?
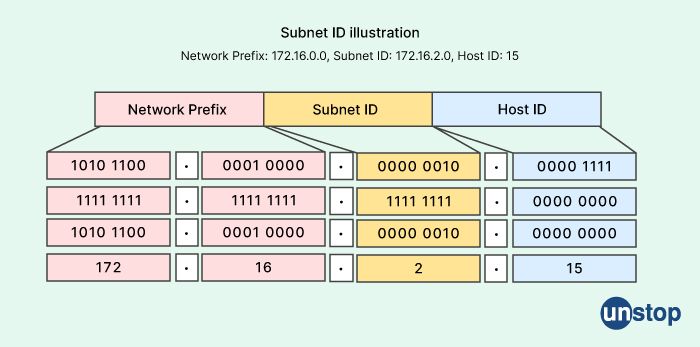
Subnetting is a technique used in computer networking that allows a single large network to be divided into smaller sub-networks, or subnets. This is typically done to improve network efficiency, manageability, and security.
When a network is subnetted, its IP address range is divided into smaller sub-ranges, with each sub-range assigned to a separate physical or logical network segment. This allows traffic to be routed more efficiently and helps to reduce network congestion. It also enables network administrators to apply security policies more effectively and to manage network resources more efficiently.
Subnetting is often used in enterprise networks, where there may be a large number of hosts and devices that need to be connected to the network. By breaking the network into smaller subnets, administrators can more easily manage network traffic and improve network performance.
44. In networking, what does "Domain" mean?
In networking, a domain refers to a group of network resources that share a common namespace and administrative authority. It is a logical grouping of computers, users, servers, and other network resources that are managed by a single administrative entity. Domains are used to simplify network administration, improve security, and provide centralized authentication and resource management. They are commonly used in Microsoft Windows environments, where they are known as Active Directory domains, but can also be implemented in other network operating systems.
45. What kind of network is the backbone?
A backbone network, also known as a backbone or core network security device , is a high-speed centralized network that connects multiple smaller networks, such as local area networks (LANs) or wide area networks (WANs), together. The backbone network is designed to facilitate communication between these smaller networks and to provide a pathway for data to travel across the network efficiently and quickly. The backbone network typically uses high-speed routers, switches, and other networking devices to handle the heavy traffic flow between the connected networks.
46. What is a PAN network, and how will it vary from a LAN in any meaningful way?
A PAN (Personal Area Network) is a type of network that is designed to allow devices to communicate with each other over a short range, typically within a few meters. A common example of a PAN is a Bluetooth network, which allows wireless communication between devices such as phones, tablets, and computers.
On the other hand, a LAN (Local Area Network) is a type of network that is designed to connect devices within a limited geographical area, such as a home, office building, or school. LANs typically use wired or wireless connections to allow devices to communicate with each other and share resources, such as printers, files, and internet access.
The main difference between a PAN and a LAN is the range of coverage. A PAN covers a much smaller area than a LAN and is designed for personal or private use, while a LAN is used for organizational or institutional purposes. PANs are typically used for connecting devices that are in close proximity, such as wearable technology or smart home devices, while LANs are used to connect computers and other devices within a building or campus.
47. Will you be able to handle the sublet network?
Yes, with the help of a dedicated team I can surely take care of the sublet network. From regular network checking to resolve any issue, all will be done under my supervision.
48. Will you be able to tackle networking problems immediately?
Yes, but the time for a solution depends upon the type of problem we are dealing with. If there is an issue with local servers then I will be able to fix it immediately otherwise I have to look deeper into the issue and then come up with the required solution.
49. Will you be able to deal with any attack on an internal networking system?
Yes, but as a network specialist I will be able to detect the issue, but solving the attack on the internal network depends upon the degree and type of attack.
50. What do you think about server drives?
Server drives are specialized hard drives designed for use in servers, which are used to store and manage data for multiple users or technological options. These drives are typically designed to be more reliable and durable than consumer-grade hard drives, with features such as better cooling systems, higher spindle speeds, and advanced error-correction capabilities.
There are several types of server drives, including:
-
Hard Disk Drives (HDDs) - These are the most common type of server drive and use spinning platters to store data.
-
Solid State Drives (SSDs) - These drives use flash memory to store data and are faster and more reliable than HDDs.
-
Redundant Array of Independent Disks (RAID) - This is a system of multiple hard drives that work together to provide increased performance and data redundancy.
-
Network Attached Storage (NAS) - These are specialized drives that are designed to be shared over a network and provide centralized data storage and management.

Sample HR interview questions for Cisco
These are some of the top HR questions that you must check out for your CISCO interview.
-
Do you have the required analytical skills?
-
How would you rate your soft skills?
-
Do you have any experience as a software developer?
-
Why do you consider yourself a potential candidate for this job?
-
What do you consider your weaknesses?
-
How will you adapt to the working atmosphere?
-
Tell us something about your current job role?
-
What do you like the most about your current job role?
-
Do you have an openness to developing new skill sets?
-
Rate your skill sets on a scale of 1 to 10?
-
Do you have any freelance experience in this field?
-
Will you be able to operate networking on client computers?
The recruitment process at Cisco
Candidates are awarded the opportunity to learn about the nature of the company's operations, as well as its culture and the people who work there while learning more about the applicants. The requirements of the continuing business are used to guide the examination of the candidates' prior experiences and capabilities. During the interview process, a candidate should expect to be questioned about his or her prior professional and academic experiences, as well as their accomplishments and the value that they can provide to Cisco. There is also the option for the applicants to pose their questions.
The interview rounds at Cisco prompt hundreds of hopeful candidates to demonstrate their competitive talents to be considered for a variety of technical roles. The interview procedure at Cisco consists of three rounds that last way longer than 5 min time, which are as follows:
- Online Assessment Test (with negative marking)
- Technical Interview Rounds
- HR Interview with some behavioral interview questions
About Cisco
Cisco Systems, Inc. is one of the most successful companies in the world when it comes to the distribution of products, systems, and services related to computer networking. The company's product portfolio includes routers, switches, remote management devices, protocol interpreters, Internet services devices, as well as networking and network management software. These products all link together unevenly distributed local area networks (LANs), wide area networks (WANs), as well as the Internet itself.
The three primary segments that Cisco serves for its target market are large organizations (such as corporations, government entities, utilities, and educational institutions) that require complex networking solutions. They typically plan to bridge multiple locations; service providers (such as Internet access providers, telephone as well as cable companies, and providers of wireless communications), as well as small and medium-sized businesses whose necessities include operating networks, accessing the internet, and/or connecting to other networks. The company is considered the top avenue for career advancement.
Suggested reads:
- How To Answer "What Can You Contribute To The Company?"
- Skills That Can Make Your Resume Stand Out
- Answering 'How Do You Prioritize Your Work?' During A Job Interview
- Know How To Answer "How do you define success?" During A Job Interview
- Have A Gap Year In Your Resume? Provide The Best Explanation With These Tips
I am a storyteller by nature. At Unstop, I tell stories ripe with promise and inspiration, and in life, I voice out the stories of our four-legged furry friends. Providing a prospect of a good life filled with equal opportunities to students and our pawsome buddies helps me sleep better at night. And for those rainy evenings, I turn to my colors.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter














Comments
Add comment