- TCS Technical Interview Questions & Answers
- TCS Managerial Interview Questions & Answers
- TCS HR Interview Questions & Answers
- Overview of Cognizant Recruitment Process
- Cognizant Interview Questions: Technical
- Cognizant Interview Questions: HR Round
- Overview of Wipro Technologies Recruitment Rounds
- Wipro Interview Questions
- Technical Round
- HR Round
- Online Assessment Sample Questions
- Frequently Asked Questions
- Overview of Google Recruitment Process
- Google Interview Questions: Technical
- Google Interview Questions: HR round
- Interview Preparation Tips
- About Google
- Deloitte Technical Interview Questions
- Deloitte HR Interview Questions
- Deloitte Recruitment Process
- Technical Interview Questions and Answers
- Level 1 difficulty
- Level 2 difficulty
- Level 3 difficulty
- Behavioral Questions
- Eligibility Criteria for Mindtree Recruitment
- Mindtree Recruitment Process: Rounds Overview
- Skills required to crack Mindtree interview rounds
- Mindtree Recruitment Rounds: Sample Questions
- About Mindtree
- Preparing for Microsoft interview questions
- Microsoft technical interview questions
- Microsoft behavioural interview questions
- Aptitude Interview Questions
- Technical Interview Questions
- Easy
- Intermediate
- Hard
- HR Interview Questions
- Eligibility criteria
- Recruitment rounds & assessments
- Tech Mahindra interview questions - Technical round
- Tech Mahindra interview questions - HR round
- Hiring process at Mphasis
- Mphasis technical interview questions
- Mphasis HR interview questions
- About Mphasis
- Technical interview questions
- HR interview questions
- Recruitment process
- About Virtusa
- Goldman Sachs Interview Process
- Technical Questions for Goldman Sachs Interview
- Sample HR Question for Goldman Sachs Interview
- About Goldman Sachs
- Nagarro Recruitment Process
- Nagarro HR Interview Questions
- Nagarro Aptitude Test Questions
- Nagarro Technical Test Questions
- About Nagarro
- PwC Recruitment Process
- PwC Technical Interview Questions: Freshers and Experienced
- PwC Interview Questions for HR Rounds
- PwC Interview Preparation
- Frequently Asked Questions
- EY Technical Interview Questions (2023)
- EY Interview Questions for HR Round
- About EY
- Morgan Stanley Recruitment Process
- HR Questions for Morgan Stanley Interview
- HR Questions for Morgan Stanley Interview
- About Morgan Stanley
- Recruitment Process at Flipkart
- Technical Flipkart Interview Questions
- Code-Based Flipkart Interview Questions
- Sample Flipkart Interview Questions- HR Round
- Conclusion
- FAQs
- Recruitment Process at Paytm
- Technical Interview Questions for Paytm Interview
- HR Sample Questions for Paytm Interview
- About Paytm
- Most Probable Accenture Interview Questions
- Accenture Technical Interview Questions
- Accenture HR Interview Questions
- Amazon Recruitment Process
- Amazon Interview Rounds
- Common Amazon Interview Questions
- Amazon Interview Questions: Behavioral-based Questions
- Amazon Interview Questions: Leadership Principles
- Company-specific Amazon Interview Questions
- 43 Top Technical/ Coding Amazon Interview Questions
- Juspay Recruitment: Stages and Timeline
- Juspay Interview Questions and Answers
- How to prepare for Juspay interview questions
- Prepare for the Juspay Interview: Stages and Timeline
- Frequently Asked Questions
- Adobe Interview Questions - Technical
- Adobe Interview Questions - HR
- Recruitment Process at Adobe
- About Adobe
- Cisco technical interview questions
- Sample HR interview questions
- The recruitment process at Cisco
- About Cisco
- JP Morgan interview questions (Technical round)
- JP Morgan interview questions HR round)
- Recruitment process at JP Morgan
- About JP Morgan
- Wipro Elite NTH: Selection Process
- Wipro Elite NTH Technical Interview Questions
- Wipro Elite NTH Interview Round- HR Questions
- BYJU's BDA Interview Questions
- BYJU's SDE Interview Questions
- BYJU's HR Round Interview Questions
- A Quick Overview of the KPMG Recruitment Process
- Technical Questions for KPMG Interview
- HR Questions for KPMG Interview
- About KPMG
- DXC Technology Interview Process
- DCX Technical Interview Questions
- Sample HR Questions for DXC Technology
- About DXC Technology
- Recruitment Process at PayPal
- Technical Questions for PayPal Interview
- HR Sample Questions for PayPal Interview
- About PayPal
- Capgemini Recruitment Rounds
- Capgemini Interview Questions: Technical round
- Capgemini Interview Questions: HR round
- Preparation tips
- FAQs
- Technical interview questions for Siemens
- Sample HR questions for Siemens
- The recruitment process at Siemens
- About Siemens
- HCL Technical Interview Questions
- HR Interview Questions
- HCL Technologies Recruitment Process
- List of EPAM Interview Questions for Technical Interviews
- About EPAM
- Atlassian Interview Process
- Top Skills for Different Roles at Atlassian
- Atlassian Interview Questions: Technical Knowledge
- Atlassian Interview Questions: Behavioral Skills
- Atlassian Interview Questions: Tips for Effective Preparation
- Walmart Recruitment Process
- Walmart Interview Questions and Sample Answers (HR Round)
- Walmart Interview Questions and Sample Answers (Technical Round)
- Tips for Interviewing at Walmart and Interview Preparation Tips
- Frequently Asked Questions
- Uber Interview Questions For Engineering Profiles: Coding
- Technical Uber Interview Questions: Theoretical
- Uber Interview Question: HR Round
- Uber Recruitment Procedure
- About Uber Technologies Ltd.
- Intel Technical Interview Questions
- Computer Architecture Intel Interview Questions
- Intel DFT Interview Questions
- Intel Interview Questions for Verification Engineer Role
- Recruitment Process Overview
- Important Accenture HR Interview Questions
- Points to remember
- What is Selenium?
- What are the components of the Selenium suite?
- Why is it important to use Selenium?
- What's the major difference between Selenium 3.0 & Selenium 2.0?
- What is Automation testing and what are its benefits?
- What are the benefits of Selenium as an Automation Tool?
- What are the drawbacks to using Selenium for testing?
- Why should Selenium not be used as a web application or system testing tool?
- Is it possible to use selenium to launch web browsers?
- What does Selenese mean?
- What does it mean to be a locator?
- Identify the main difference between "assert", and "verify" commands within Selenium
- What does an exception test in Selenium mean?
- What does XPath mean in Selenium? Describe XPath Absolute & XPath Relation
- What is the difference in Xpath between "//"? and "/"?
- What is the difference between "type" and the "typeAndWait" commands within Selenium?
- Distinguish between findElement() & findElements() in context of Selenium
- How long will Selenium wait before a website is loaded fully?
- What is the difference between the driver.close() and driver.quit() commands in Selenium?
- Describe the different navigation commands that Selenium supports
- What is Selenium's approach to the same-origin policy?
- Explain the difference between findElement() in Selenium and findElements()
- Explain the pause function in SeleniumIDE
- Explain the differences between different frameworks and how they are connected to Selenium's Robot Framework
- What are your thoughts on the Page Object Model within the context of Selenium
- What are your thoughts on Jenkins?
- What are the parameters that selenium commands come with a minimum?
- How can you tell the differences in the Absolute pathway as well as Relative Path?
- What's the distinction in Assert or Verify declarations within Selenium?
- What are the points of verification that are in Selenium?
- Define Implicit wait, Explicit wait, and Fluent
- Can Selenium manage windows-based pop-ups?
- What's the definition of an Object Repository?
- What is the main difference between obtainwindowhandle() as well as the getwindowhandles ()?
- What are the various types of Annotations that are used in Selenium?
- What is the main difference in the setsSpeed() or sleep() methods?
- What is the way to retrieve the alert message?
- How do you determine the exact location of an element on the web?
- Why do we use Selenium RC?
- What are the benefits or advantages of Selenium RC?
- Do you have a list of the technical limitations when making use of Selenium RC? Selenium RC?
- What's the reason to utilize the TestNG together with Selenium?
- What Language do you prefer to use to build test case sets in Selenium?
- What are Start and Breakpoints?
- What is the purpose of this capability relevant in relation to Selenium?
- When do you use AutoIT?
- Do you have a reason why you require Session management in Selenium?
- Are you able to automatize CAPTCHA?
- How can we launch various browsers on Selenium?
- Why should you select Selenium rather than QTP (Quick Test Professional)?
- Airbus Interview Questions and Answers: HR/ Behavioral
- Industry/ Company-Specific Airbus Interview Questions
- Airbus Interview Questions and Answers: Aptitude
- Airbus Software Engineer Interview Questions and Answers: Technical
- Importance of Spring Framework
- Spring Interview Questions (Basic)
- Advanced Spring Interview Questions
- C++ Interview Questions and Answers: The Basics
- C++ Interview Questions: Intermediate
- C++ Interview Questions And Answers With Code Examples
- C++ Interview Questions and Answers: Advanced
- Test Your Skills: Quiz Time
- MBA Interview Questions: B.Com Economics
- B.Com Marketing
- B.Com Finance
- B.Com Accounting and Finance
- Business Studies
- Chartered Accountant
- Q1. Please tell us something about yourself/ Introduce yourself to us.
- Q2. Describe yourself in one word.
- Q3. Tell us about your strengths and weaknesses.
- Q4. Why did you apply for this job/ What attracted you to this role?
- Q5. What are your hobbies?
- Q6. Where do you see yourself in five years OR What are your long-term goals?
- Q7. Why do you want to work with this company?
- Q8. Tell us what you know about our organization
- Q9. Do you have any idea about our biggest competitors?
- Q10. What motivates you to do a good job?
- Q11. What is an ideal job for you?
- Q12. What is the difference between a group and a team?
- Q13. Are you a team player/ Do you like to work in teams?
- Q14. Are you good at handling pressure/ deadlines?
- Q15. When can you start?
- Q16. How flexible are you regarding overtime?
- Q17. Are you willing to relocate for work?
- Q18. Why do you think you are the right candidate for this job?
- Q19. How can you be an asset to the organization?
- Q20. What is your salary expectation?
- Q21. How long do you plan to remain with this company?
- Q22. What is your objective in life?
- Q23. Would you like to pursue your Master's degree anytime soon?
- Q24. How have you planned to achieve your career goal?
- Q25. Can you tell us about your biggest achievement in life?
- Q26. What was the most challenging decision you ever made?
- Q27. What kind of work environment do you prefer to work in?
- Q28. What is the difference between a smart worker and a hard worker?
- Q29. What will you do if you don't get hired?
- Q30. Tell us three things that are most important for you in a job.
- Q31. Who is your role model and what have you learned from him/her?
- Q32. In case of a disagreement, how do you handle the situation?
- Q33. What is the difference between confidence and overconfidence?
- Q34. If you have more than enough money in hand right now, would you still want to work?
- Q35. Do you have any questions for us?
- Interview Tips for Freshers
- Tell me about yourself
- What are your greatest strengths?
- What are your greatest weaknesses?
- Tell me about something you did that you now feel a little ashamed of
- Why are you leaving (or did you leave) this position??
- 15+ resources for preparing most-asked interview questions
- CoCubes Interview Process Overview
- Common CoCubes Interview Questions
- Key Areas to Focus on for CoCubes Interview Preparation
- Conclusion
- Frequently Asked Questions (FAQs)
- Data Analyst Interview Questions With Answers
- About Data Analyst
EY Interview Questions And Answers (2026)

Ernst & Young also referred to as just EY, is a global professional service provider with its headquarters in London, England. It is one of the biggest networks for professional services to help clients overcome their most difficult obstacles. They offer consultancy, assurance, tax, and transaction services and guide business operations. They collaborate across various services to develop fresh solutions to challenging problems and assist their clients in realizing their goals.
If you are planning to join EY and it is your dream company, you must go through this blog which covers the most important technical interview as well as HR questions to take your preparation to the next level.
EY Technical Interview Questions (2026)
Q1. Explain normalization.
The process of organizing data into a database to reduce inconsistent dependency and eliminate Insert, Update, and Delete anomalies is called normalization. It entails breaking up bigger tables into smaller ones so that it takes less disk space and connects them with relationships.
Normalization's primary goals are to reduce errors in data change, get rid of redundant data, and make queries easier and the database flexible. It makes sure that a database's dependencies between its columns and tables are implemented properly by utilizing database constraints.
Q2. Describe the object-oriented model.
An Object-Oriented model is an approach to modeling an application that is employed in the software development cycle at the outset of the software life cycle. It is a method of problem-solving that uses models structured around notions from the real world.
Some key features of the object-oriented concepts are:
- Objects: In an object-oriented context, an object is a real-world component that may exist physically or conceptually or in real-world problems.
- Class: It refers to a blueprint or a template that is used for creating objects.
- Encapsulation: Encapsulation is the process of masking an object's internal components from view.
- Inheritance: The technique of constructing new classes from older classes is known as inheritance.
- Polymorphism: An object's ability to adopt various forms is known as polymorphism.
Understand the difference between class and object.
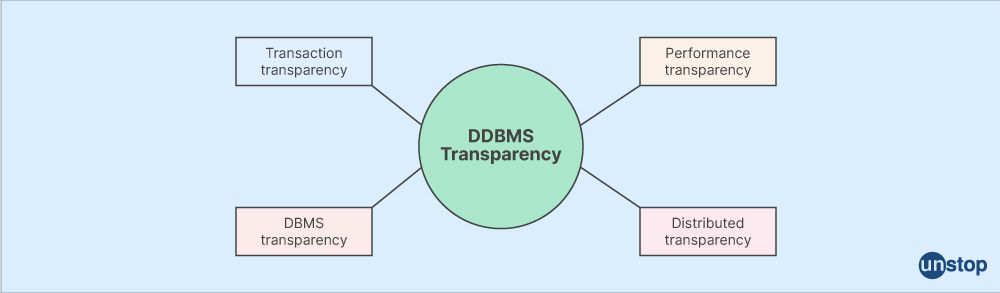
Q3. Describe transparent DBMS.
A transparent database management system (DBMS) with a transparent function that conceals the implementation of physical structure details from the user. It indicates that the user is unaware of the system's underlying details, including data location, fragmentation, replication, and performance.
Q4. Explain Deadlock.
A deadlock is a circumstance in which two or more processes are obstructed because each process is holding a resource while also waiting for another resource that is held by another process, including itself, to take action. Deadlocks are a frequent issue in multiprocessing systems and can make the system unresponsive.
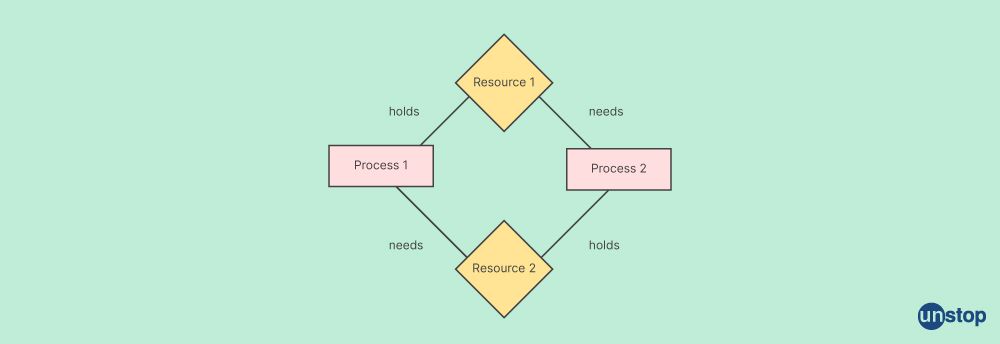
Some features of Deadlock are:
- Mutual Exclusion: Only one process can use two or more resources at once, and they are not shared.
- Hold and Wait: A process is holding one or more resources while it awaits the arrival of other resources.
- No Preemption: There can be no preemption of resources from a process.
- Circular Wait: A group of procedures are in a circular chain of waiting for one another.
Q5. What is an interface?
A collection of methods that a class must implement are defined by an interface, which is a programming structure. It is a contractual representation that is language-specific and utilized in programming languages, and provides code reusability.
Some features of the interface are:
- Blueprint: A class's interface serves as a blueprint by defining the set of methods that the class must implement.
- Implementation: The implementations of the methods listed in an interface may be provided by such multiple classes that might otherwise not necessarily be related to one another.
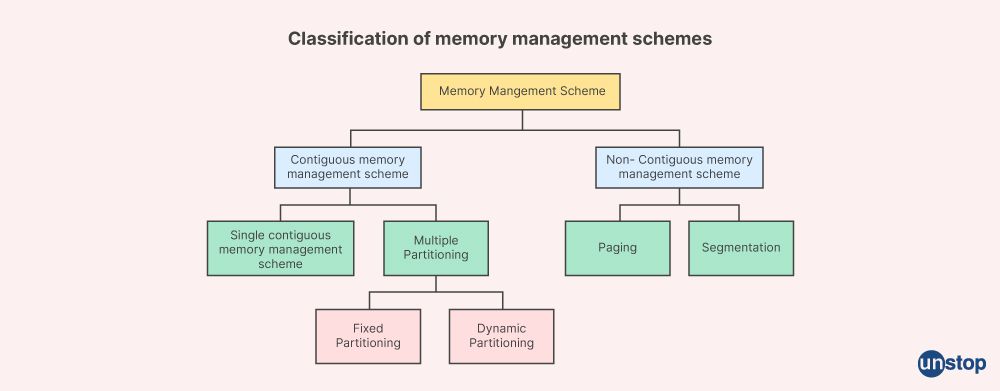
Q6. Explain the meaning of memory management.
Memory management is the control and coordination of computer memory. It involves allocating blocks of memory to different running programs to enable ways to dynamically allocate memory to programs upon their request and release it for reuse when no longer required. Memory management is important for the efficient utilization of memory.
Some features of memory management are:
- Main Memory: The crucial component of the computer utilized to store data is the memory. Because a computer system only has a very little quantity of main memory available, its efficient utilization is essential.
- Contiguous Memory Management Schemes: Space that is allocated utilizing contiguous memory management technique uses memory blocks that are adjacent or continuous with one another.
- Non-contiguous memory management: Memory blocks that are not next to one another or contiguous to one another are allocated utilizing non-contiguous memory management strategies.
Q7. Why is memory management necessary?
Memory management is needed because of the following reasons:
- Limited Memory: The amount of memory available in a computer system is limited, and many processes are competing for it.
- Optimizing Memory Usage: Memory management helps in placing the programs in memory in such a way that memory is utilized to its fullest extent.
- Efficient Resource Allocation: Memory management ensures that blocks of memory space are properly managed and allocated so that the operating system, applications, and other running processes have the memory they need to carry out their operations.
- Effective management: It involves keeping track of the memory locations in a computer system to determine if they are free or allocated and allocating the memory to various programs.
- Process Execution: A computer system's main goal is to run programs, and memory is utilized to store instructions and handle data processing.
Q8. Are interface and abstract classes the same?
No, they are not the same. The major difference between abstract class and interface are:
Interface
- An interface does not have a method body.
- There can only be abstract methods and static constants in an Interface.
- A constructor is not present in an interface.
- Multiple interfaces may be extended by one interface.
Abstract Class
- An abstract class can have a method body.
- Both abstract and non-abstract methods may be present in the abstract class.
- Only one class can be extended by an abstract class.
- An abstract class can have a constructor.

Q9. Tell some points of dissimilarities between a Compiler and an Interpreter.
The key difference between a compiler and an interpreter are:
Compiler:
- The compiler takes the entire program as input and converts the entire program into machine code before the program runs and has a faster execution time.
- It translates the entire source code in a single run and generates object code.
- It produces an output of low-level language, i.e., machine or assembly language.
- The compiler displays all errors after compilation and is less memory efficient.
Interpreter:
- The interpreter takes a single line of code as input and converts it into machine code during the program run, which means it does not entirely convert the program into machine code in one go.
- It translates the entire source code line by line and so it does not generate object code.
- It produces an output of comprehensible language.
- The interpreter displays errors of each line one by one and is more memory efficient.
Q10. What do you mean by a thread?
A thread is a collection of instructions that one program can execute independently. It is a quick process that can coexist with other program threads in the same program and share a common memory space. The employment of threads enables parallelism and boosts the program's performance,
and it also shows a path of execution.
Q11. How do you get rid of the trailing spaces in a string?
We can use the trim() method to get rid of trailing spaces in a string in JAVA. The String class in java.lang package contains the definition of the trim() function. It creates a new string object after eliminating all of the string's leading and trailing spaces.
Example:
String str = " Hello World ";
String trimmedStr = str.trim();
System.out.println(trimmedStr); // Output: "Hello World"
The strip() function in Python can also be used to eliminate both leading and trailing whitespace from a string. The rstrip() technique can be used to remove only trailing whitespace.
Example:
str = " Hello World "
trimmedStr = str.rstrip()
print(trimmedStr) # Output: " Hello World"
Q12. Explain the term synchronization.
Synchronization is the coordination of several processes or threads to work with each other. It is employed in concurrent programming to prevent deadlocks, race conditions, and other synchronization-related issues. Locks, semaphores, and monitors are examples of synchronization primitives that can be used to establish synchronization.
These primitives enable processes or threads to coordinate their operations in order to accomplish a shared objective. Synchronization mechanisms are used to make sure that just one thread or process may work on the crucial part at once.
Q13. Tell me some features of the DATA LINK LAYER.
The Data Link Layer is the second layer of the OSI model and is responsible for handling the moving of data into and out of a physical link in a network. Some of the characteristics of the Data Link Layer are:
- It deals with issues brought on by bit transmission errors.
- It makes sure that data moves at a rate that doesn't strain sending and receiving hardware.
- It enables the transmission of data to the network layer, which is Layer 3.
- It ensures an initial connection has been set up, divides output data into data frames, and handles the acknowledgments from a receiver that the data arrived successfully.
Q14. Explain the need for garbage collection in JAVA.
One of Java's most important features is garbage collection which controls how objects are allocated and released from memory automatically.
Java uses garbage collection for automatic memory reclamation during runtime. In another way, it is a means of getting rid of useless items. The thread, which, known as Garbage Collector (GC), is responsible for garbage collection. To make space, the GC searches for and monitors unused objects and then deletes them. A runtime OutOfMemoryError would occur if there were no garbage collections, and the heap will run out of memory.
Unlock endless job & internship opportunities!
Q15. Tell the name of the function in C and C++, which can be used in Garbage Collection.
Memory that has already been allocated using the malloc(), calloc(), or realloc() procedures are released using the free() function in the C programming language.
Using the delete() operator in C++, the memory that has previously been allocated using the new operator is released.
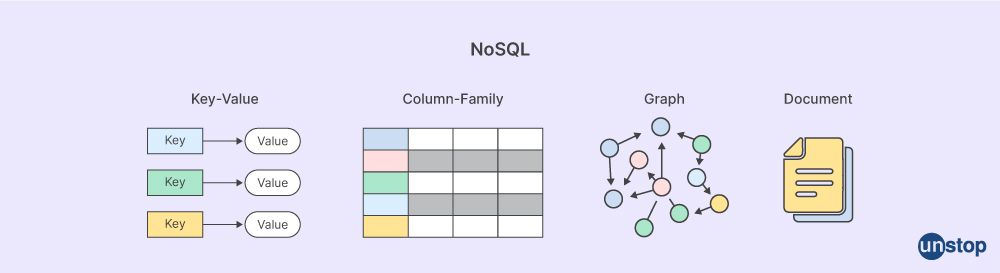
Q16. Explain NoSQL.
NoSQL is a method of managing databases that can handle many different types of data structures, including key-value, document, columnar, and graph formats. NoSQL databases aren't tabular like relational databases, so they store data in alternative ways. NoSQL databases can be classified as document, key-value, wide-column, or graph databases depending on their data models. They offer adaptable schemas and scale well under conditions of heavy data loads and user traffic. For distributed data repositories with enormous data storage requirements, a NoSQL database is mostly used.
Q17. Tell me the method name to join two tables in SQL.
We can join two tables in SQL by using INNER JOIN, LEFT JOIN, RIGHT JOIN, FULL JOIN, and CROSS JOIN.
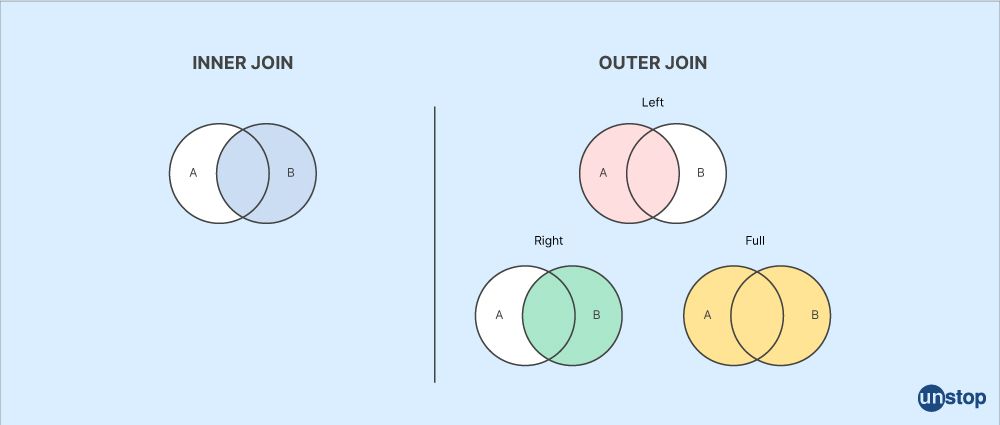
Example by using INNER JOIN:
SELECT column_name(s)
FROM table1
INNER JOIN table2
ON table1.column_name = table2.column_name;
Q18. Which Bitwise operator is used for checking whether a particular bit is on or off?
The bitwise AND operator (&) can be used to determine if a certain bit is on or off. The binary bitwise AND operator, operates on two operands and verifies the bits. If both bits are set to HIGH, it returns 1, and if either of the bit is set to LOW, it returns 0.
Example:
int num = 18; // binary 10010
int mask = 2; // binary 00010
if (num & mask) {
printf("The second bit is on.\n");
} else {
printf("The second bit is off.\n");
}
Q19. Are the string copy (strcpy) and the memory copy (memcpy) same?
No, they are not the same. The points of dissimilarities are:
Strcpy()
- Strcpy() copies the contents of one string into another.
- It copies characters until it reaches the null character '\0'.
- It does not need the specification of the destination buffer's size.
Memcpy()
- Memcpy() transfers a predetermined number of bytes from one memory region to another.
- It does not stop at null characters.
- The size of the target buffer must be specified when using the memcpy() function.
Q20. Describe Amortization.
Amortization is an accounting method used to spread out the expense of a long-term asset across the asset's estimated lifespan. The process of gradually writing off or excluding the cost of an asset or making periodic payments is known as amortization. Amortization expenses are calculated by factoring in the cost of long-term assets, such as computers and vehicles. Depreciation expenses, or amortization, show up on an organization's income statement. It is a non-cash expense; therefore, although there is no cash outflow, the asset's value is decreased.
Q21. Describe Securities Transaction Tax.
A tax known as the Securities Transaction Tax (STT) is imposed on each purchase and sale of shares listed on India's official stock exchanges. The investor is required to pay a little tax on the total amount given or received in exchange for shares under this type of turnover tax.
Q22. What is Alternative Minimum Tax?
Under the Alternative Minimum Tax (AMT), the taxpayers must determine their tax burden twice, first under the standards for ordinary income tax and again under the AMT regulations. A new set of guidelines are used to calculate the AMT in order to guarantee that some taxpayers pay at least a specific amount of income tax.
Q23. What is CARO 2003?
CARO 2003 stands for Companies (Auditor's Report) Order, 2003.
The government of India's Ministry of Corporate Affairs issued an order that specifies the topics that statutory auditors of firms must cover in their audit reports. CARO 2003 is subjected to every firm, including international companies as specified by Section 591 of the Companies Act of 1956.
Q24. Describe Long-Term Capital gains and Short-Term Capital gains.
Long-Term Capital gains
Long-term capital gains are profits made on assets held for more than one year.
Short-Term Capital gains
Short-term capital gains are profits made on assets held for one year or less. The tax on these capital assets is the same as the normal income tax.
Q25. Explain Capital Gain.
The profit made from the sale of an asset whose value has risen throughout the holding term is known as a capital gain and the property capital asset can either be tangible(like a car, or real estate) or intangible property(bonds and shares).
Q26. Describe Tax Refund.
The taxpayer receives a tax refund for any additional taxes paid to the government. When we as taxpayers have paid more taxes than we owe, we typically receive a refund.
Q27. Explain management audit.
A management audit is an unbiased, methodical investigation and evaluation of a company's entire operations and results. It is an evaluation of the managerial qualities of an organization.
Finding errors in management procedures and making suggestions for potential improvements are the major objectives of a management audit.
Q28. Describe Audit Control Procedures.
Audit control procedures are the strategies, processes, and methods that auditors use to gather trustworthy audit data and form their expert opinions regarding the efficacy of internal controls in an organisation.
Risk management, decision-making, financial and operational results of the firm, strategic and tactical planning, and other topics may all be covered by the audit.
Q30. Explain Cross-Functional Audits.
Cross-functional audits are a type of management audit that involves the review of managerial aspects across different departments or functions of an organization. It is a systematic examination of decisions and actions of the management to analyze the performance of different departments or functions
Cross-functional audits evaluate the effectiveness and suitability of controls by challenging underlying rules, procedures, and methods across different departments or functions.
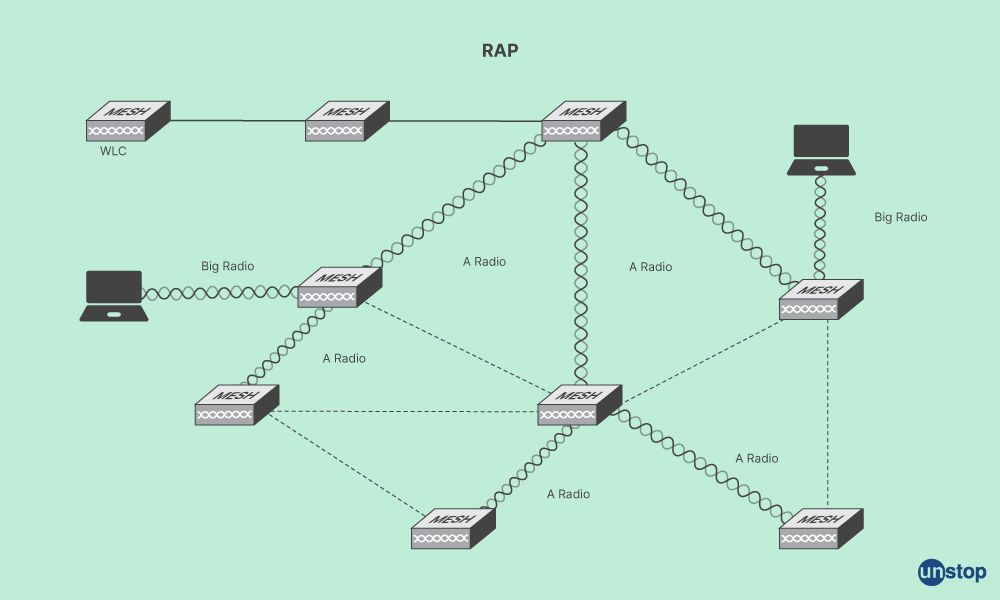
Q31. In multiple APs (in a mesh network), which protocol will allow multiple connections with redundant connections between the nodes?
The Adaptive Wireless Path Protocol (AWPP) is the protocol that enables several APs to connect with numerous redundant links between nodes in a mesh network. A mesh network's RAPs(Root Access Points) can interact with one another to find the best path to the wired network and then automatically selects the best path to the wired network because each AP in the mesh network runs in AWPP.
Q32. Can the initial size of an array be defined using constant values?
No, we cannot define an array’s initial size with constant values because the size of the array should be known at compile-time, so if we use a constant value for defining an array’s size then it cannot be changed at the runtime, which will limit the flexibility of the code.
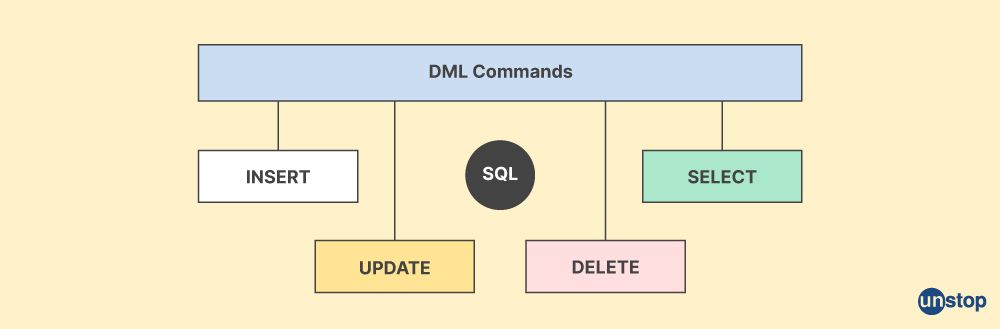
Q33. What is DML?
DML is a collection of languages that are used to manage and manipulate data in a relational database or relational model, which is a subset of SQL (Structured Query Language). We can insert, update, delete, and retrieve data from a database using DML commands like SELECT, UPDATE, INSERT INTO, and DELETE FROM, etc.
Example: INSERT INTO students (FirstName, MiddleNmae, RollNo) VALUES ('78', 'Paul', Joe');
Q34. What do you know about a process and a thread?
Process:
- A program that is running is referred to as a process.
- It is a function that the computer is carrying out.
- A process is separate from other processes and does not share memory.
- A process has the ability to produce other processes, also known as child processes.
Thread:
- A process segment is known as a thread which shows a path of execution.
- In concurrent programming, an execution unit is known as a thread.
- A thread in the same process with other threads does not isolate itself and shares common memory space with other threads.
- A process contains a thread, and numerous threads may run concurrently.
Q35. Describe the malloc() and calloc() function in C.
1. Malloc()(memory allocation function)
- Allocating a single block of memory involves the malloc() method.
- The malloc() function allocates a memory block with a garbage value, which indicates that the memory had not been initialized.
- It returns a pointer to the first byte of the allocated memory and allocates memory of the specified size in bytes.
SYNTAX of memory allocation function: ptr = (cast_type *) malloc(size);
2. Calloc()(contiguous allocation function)
- The calloc() function is used to allocate multiple blocks of memory space.
- It returns a pointer to the first byte of the memory that is allocated.
- The calloc() function when allocates the memory block, it is always initialized to zero.
SYNTAX of contiguous allocation function: ptr = (cast_type *) calloc(n, size);
Q36. Define a primary key and a foreign key.
Primary key
In a table, the primary key is a column or combination of columns that uniquely identifies each row. It guarantees that every row in the table has a special identification. A primary key cannot have a NULL value, and A table can have only one primary key.
Foreign key
A column or group of columns pointing to another table's primary key is referred to as a foreign key. It establishes a link between two tables and is used to enforce referential integrity. A foreign key can have NULL values as well as duplicate values, and a table can have multiple foreign keys.
Q37. Tell me about an exclusive lock and a shared lock.
Exclusive lock
An exclusive lock is a lock that is obtained to modify data. It prevents other transactions from accessing the locked resource until the lock is released. An exclusive lock can be imposed on a page or row only if there is no other exclusive lock imposed already on the target.
Shared lock
A shared lock is a lock that is obtained for a read-only operation. It allows multiple transactions to read the locked resource simultaneously and the objects that do not already have an exclusive lock applied to them can have a shared lock.
Q38. What is the use of locks?
Locks are needed in database management systems to ensure the isolation of property holds in transactions, prevent concurrent access, ensure data integrity, ensure transaction atomicity, and enforce transaction isolation.
Q39. Describe the term intercompany reconciliation.
The process of confirming transactions between many companies within the same parent corporation or same corporate umbrella is known as intercompany reconciliation. It guarantees the validity and accuracy of intercompany accounting records.
Intercompany transactions are important in the accounting process for every business. They enable the company to correctly and completely record and assess every type of financial activity.
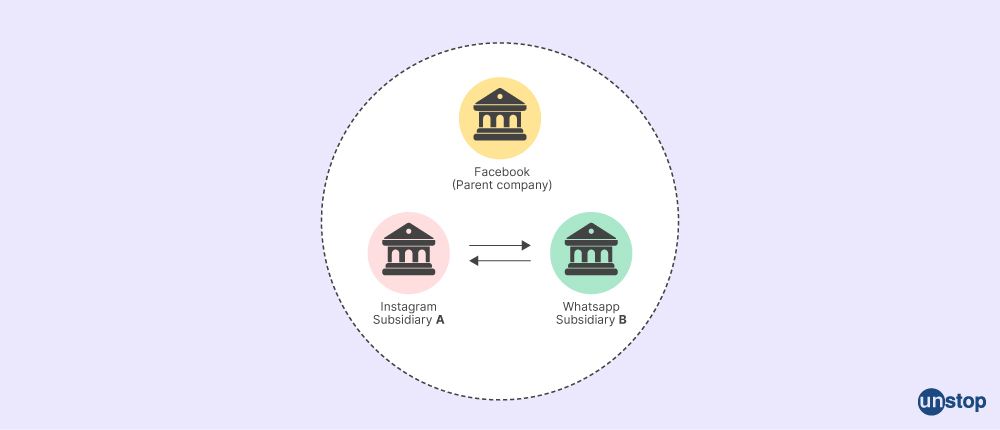
Q40. Describe the term impairment.
Impairment in accounting refers to a permanent decline in the value of a long-term intangible asset. This can happen when the cash flows or other benefits generated by an asset decline, as determined through a periodic assessment process. It can cause a major decline in the book value of a business. Impairment can occur due to multiple factors, such as increased competition, physical damage, etc.
Q41. Explain stored procedures.
Stored procedures are a type of code in SQL that can be stored for later use and can be used many times. Some benefits of stored procedures are:
- Better Performance: Stored procedures are compiled once and stored in executable form, so procedure calls are quick and efficient, which leads to improved performance.
- Scalability: Stored procedures increase scalability by enabling you to take advantage of the computing resources of the server
- Security: Stored procedures can be used to restrict access to data by allowing only authorized users to execute them.
Q42. Describe RDBMS.
RDBMS is a relational database management system. It was developed by E.F. Codd. It is a piece of software that lets us define, design, manage, and regulate access to relational databases. It is a kind of database management system (DBMS) that incorporates relational data architecture, and it typically includes an application programming interface for Structured Query Language (SQL).
Q43. What is performance testing?
Performance testing is a software testing method used to assess how well a system responds, is stable, reliable, scalable, and uses resources under a specific workload. Performance testing is mostly used to locate and fix software application performance issues.
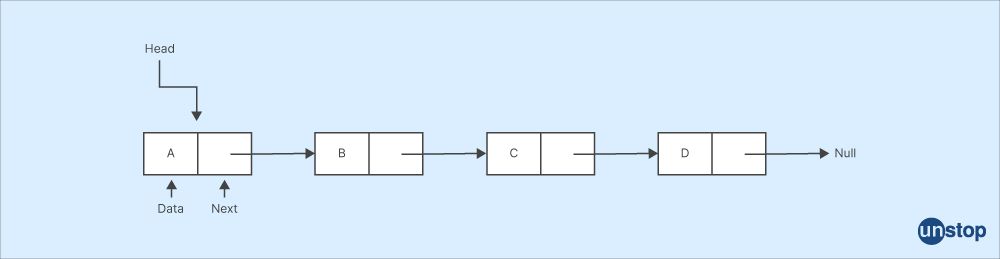
Q44. What is the singly-linked list?
A singly linked list is a kind of linked list that can only be traversed in one direction, from the first node (head) to the last node (tail). Each node in a singly linked list only links to the node after it in the list's sequence.
A succession of elements is stored using singly linked lists, where each element points to the adjacent element. They are helpful for dynamic data storage and manipulation when the size of the data is not known in advance.
EY Interview Questions for HR Round
Check out these sample HR questions for clearing your EY interview:
- Where do you see yourself in 5 years?
- Can you tell me about your previous experience?
- How can you manage a stressful situation?
- What is your approach to dealing with a challenging situation?
- Have you worked for a consulting services firm previously?
- Can you utilize people with energy in your team?
- I would like you to tell me about yourself.
- I'm curious about both your strengths and your weaknesses. Please elaborate.
- What do your close companions and coworkers have to say about you?
- How did you increase your knowledge during the past year? Share some steps did you take?
- Explain the distinction between a group and a team. What is teamwork for you?
- Describe the perfect business or workplace that you would work for.
About EY
EY's diversified teams establish confidence via assurance and assist customers in growing, transforming, and operating their businesses. EY teams explore better questions to uncover innovative answers to the difficult problems that are now affecting our world. It has over 700 offices located in 150 different countries and employs 250,000 people throughout the globe. It also offers tax consulting and advisory services to businesses like accounting firms in addition to providing assurance services (including financial audits). It is among the top professional services firms where most people would like to work.
We hope the above EY interview questions will take you closer to your dream job. For articles like this, stay tuned to Unstop!
I am a storyteller by nature. At Unstop, I tell stories ripe with promise and inspiration, and in life, I voice out the stories of our four-legged furry friends. Providing a prospect of a good life filled with equal opportunities to students and our pawsome buddies helps me sleep better at night. And for those rainy evenings, I turn to my colors.
Login to continue reading
And access exclusive content, personalized recommendations, and career-boosting opportunities.
Subscribe
to our newsletter
Blogs you need to hog!

This Is My First Hackathon, How Should I Prepare? (Tips & Hackathon Questions Inside)

10 Best C++ IDEs That Developers Mention The Most!

Advantages and Disadvantages of Cloud Computing That You Should Know!











Comments
Add comment